A Look into Enterprise Cybersecurity: Curing the Ignorance

Seems like it was just some years ago, when hackers were still acting on their own. Lone wolves, guys next door – anyone could secretly be a hacker: one of your neighbors, your brother or your friend. While more and more tools become available for newbie hackers, allowing to easily getting confidential information (personal data, bank accounts, etc.), cyber crimes have grown in scale. Today’s cybercrimes moved from personal data thefts to industrial espionage and cyber terrorism, where foreign governments, organized groups, and big companies are involved. The contemporary world of cybercrime does not consist of a one-man show anymore but is a huge self-sufficient industry. Similar to a legal IT market, a black market for hackers now offers the full range of corporate cracking service packages, including access to a certain server, operating a navigation system with a botnet, DoS attacks on certain networks or hubs and a possibility to buy entire personal databases together with their passwords and accounts.
In March 2015, an independent cybersecurity consultant Marc Goodman hosted an interactive panel called “Future Crimes from the Digital Underworld” at SXSW 2015. According to Goodman’s forecasts, things are getting pretty serious . The danger continues to grow with every minute. As more and more devices become connected to the Internet, our living environment becomes completely hackable. According to Intel’s Internet of Things, we will have 200 billion internet-connected devices by 2020, resulting in 26 smart objects per capita worldwide. “Today all these computers are hackable, which means that the 21st century modern world, that we’re building, is a digital house of cards that can come crashing down at any moment. We need to protect it because right now we don’t have a backup plan”, says Goodman.
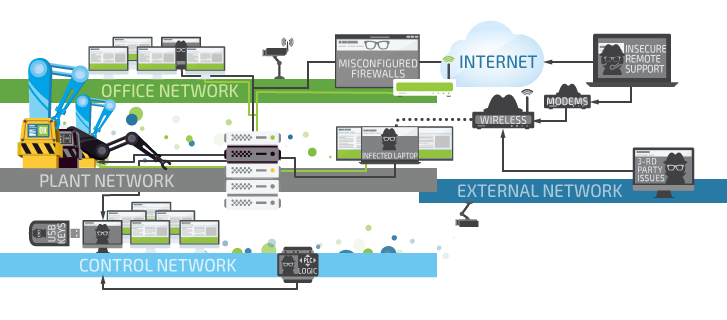
With the expanding digitalization of our world, risks for business continue to grow as well. Lots of companies remain unprotected. Experience shows that an exposed system is constantly scanned by potential attackers a couple dozen times a day. Advanced hacking attempts might reach up to five times a week. Thus, an unprotected system is vulnerable to an imminent cyber-attack. The main factor that determines the chances of the corporate data being hacked is a lack of a security system, which is aimed at protecting a specific business application. On the positive side, awareness and attention to cybersecurity have risen as well. A regular security kit, obviously, is not enough. The misunderstanding of cyber threats risks served a catalyst for the risk analysis correction. Potential threats are being analyzed and the possible negative consequences are properly evaluated. Microsoft pays up to $100,000 to anyone reporting the breaches in their systems (source). The 2016 U.S. national budget includes $14 billion for cybersecurity (source). Meanwhile, ICT companies continue to increase their security budgets. In the last year, Microsoft spent $1 billion on security only (source). Sounds like a tremendous amount at first, but even such expenses might fall short, as the total estimates of annual cybercrimes’ cost might reach $450 billion per McAfee reports. Many large companies were hacked over the past years: JP Morgan Chase, Sony, Adobe, eBay, TalkTalk etc. According to the 2014 Symantec research, five out of six interviewed companies have been attacked. What matters more, none of these researches is accurate enough as many cases are not reported or are even left unnoticed.
As the threat continues to grow, most corporations look for outsourced cybersecurity solutions. There are no issues with security solutions implementation: security specialists have tried-and-tested practices (risk analysis, a selection of security controls). There are ready solutions available on the IT market, which, together with organizational measures, make it possible to transform a huge problem with irreversible consequences into an unlikely risk. Still, in most cases, security systems are built from the ground up providing protection of the specific vulnerable information. Such system should include a complex of security events monitoring and penetration testing. This solution is normally an ‘eye-opener’ for business applications owners. After that, any doubts regarding a potential cyber-attack disappear completely.
Investing in data protection today is securing your business for tomorrow.

![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)





![Multi-Cloud Governance: Policies [thumbnail]](/uploads/media/thumbnail-280x222-multi-cloud- governance-policies-and-procedures.webp)
![Security Operations vs Security Development [thumbnail]](/uploads/media/thumbnail-280x222-how-to-strike-a-balance-between-security-operations.webp)
![Cloud WAF vs On-Premises WAF [Thumbnail]](/uploads/media/thumbnail-280x222-cloud-WAF-vs.-on-premises-WAF.webp)