How to Create Secure Identity Infrastructure in Azure Cloud
The same Akamai survey suggests that while 100% of organizations have experienced credit stuffing attacks in the past 12 months, only 30% have sufficient solutions to stop attacks. That’s problematic, especially in the wake of remote work, when more and more sensitive data is traveling in and out of the cloud.
Granted, when it comes to Microsoft Azure security, you already have a diverse range of tools for ensuring that no user account can be easily compromised or hacked. However, Azure cloud data security is a shared responsibility. While Microsoft ensures the topmost security of the underlying platform infrastructure, it’s your job to set up custom security facets for your organization, pertaining to identity management and access control.
In this post, we provide a step-by-step framework for enabling a security-tight, but user-friendly identity management process with the help of Azure Active Directory (AD).
How to create secure identity infrastructure in Microsoft Azure in 5 steps:
- Implement Centralized Identity Management
- Enable Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
- Proactively Manage User Access
- Actively Monitor Your Security State
- Automate the Common Monitoring and Management Task
Let's review each of the steps in more detail.
1. Implement Centralized Identity Management
If you rely on hybrid environments (e.g., your on-premises data center is extended to Azure cloud), your first step towards Azure protection should be enabling integrated identity management. After integrating on-prem and cloud directories, you can manage all user accounts from a single place, plus provide users with a common identity for accessing both environments. This, in turn, reduces password management costs. Given that almost 50% of IT help desk costs are associated with password resets, the savings of a Single Sign-On (SSO) solution can be significant.
Best Practices:
- Designate one Azure AD instance to all corporate accounts (on-prem & cloud-based).
- Use Azure AD Connect to enable synchronization between your cloud and on-premises directories.
- When it comes to high-privilege accounts that you already have in your Active Directory instance, don’t change the default Azure AD Connect configuration fileting them out. Or else, such accounts might meddle in the on-premises assets.
- Enable password hash synchronization — a feature that helps protect against credential stuffing attacks. This config is particularly valuable as it helps check if users have used the same email/password combo on other services (non-connected to Azure AD), and prevent them from using the same credentials if these have already been compromised.
- Embed Azure AD into all your newly developed business applications for extra security.
2. Enable Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
Single sign-on (SSO) reduces the reliance on multiple passwords and, thus, increases overall Azure cloud security. Instead of asking your business users to maintain multiple passwords for their Salesforce, Microsoft 365, Google apps, and other accounts, you can set up seamless and secure access to all of them via Azure AD. Considering that an average enterprise has over 900 applications with only 28% being integrated, users are forced to store a lot of passwords (and oftentimes re-use the weak ones). This can lead to security incidents and costly data breaches.
The benefit of using Azure AD is that many business applications already have pre-integrated SSO connections with it. On top of that, you can find SSO connectors for some 3,000 applications on Azure Marketplace.
You can choose one of two approaches to enable SSO on Azure:
- Federated SSO. In this case, Azure AD authenticates users with their Azure AD account. This method is available for all applications, supporting the following protocols – SAML 2.0, WS-Federation, or OpenID Connect.
- Password-based SSO. When using this type of authentication, users are asked to provide a username/password combo to the application during their first access. For all the subsequent logins, Azure AD will supply the login credentials to the connected app.
More information on the benefits of each SSO method can be found in this Microsoft guide.
Multi-factor authentication (MFA) is another strong security facet we always recommend implementing as a part of the cloud security strategy.
MFA is an intermediary measure that can help stop unsolicited login attempts, especially from compromised accounts, by asking the user to provide a second form of authentication for accessing their accounts. Azure provides an array of user-friendly authentication methods such as:
- One-time text or voice passwords
- Software token OTPs
- Microsoft authenticator
- Windows Hello
- FIDO2 security keys (in preview).
According to Microsoft, corporate accounts are 99.9% less likely to get hacked with MFA enabled.
Conditional Access in Azure Active Directory
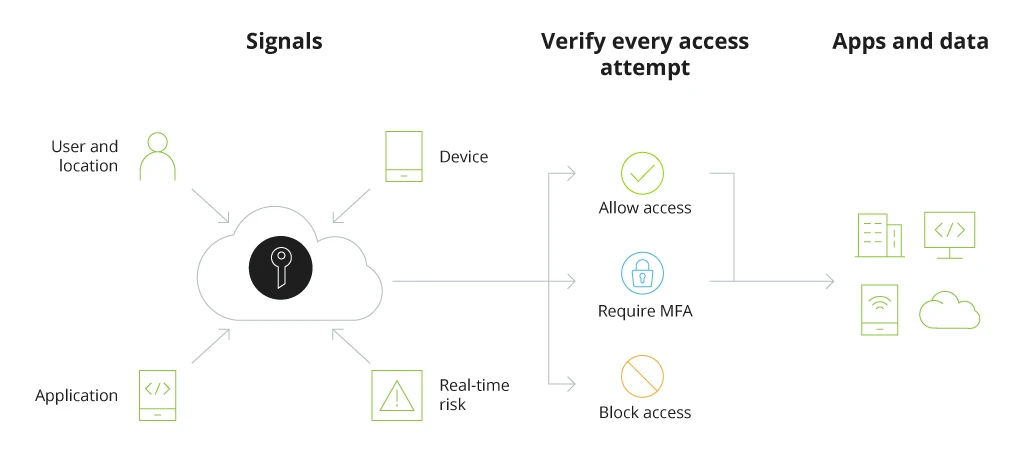
With SSO and MFA enabled, you reduce your company’s reliance on passwords and, subsequently, the risks of brute force breaches due to weak passwords.
3. Proactively Manage User Access
Having complete visibility into different user roles and permissions is essential to implementing proper security controls. Azure role-based access control (Azure RBAC) is an authorization service, designated for implementing granular access management of Azure resources.
Consider implementing this service for all staff members.
When it comes to line-of-business leaders, Azure AD Identity Governance is a service we recommend implementing. A comprehensive solution for managing roles, data, and resources access, Azure AD Identity Governance enables a single pane of glass view into all your employees’ activity and permissions for easy audit and monitoring without placing a strain on their productivity. Running in the background, the app allows you to perform the following tasks across all users, services, and applications, running on-premises, and in the cloud:
- Govern the identity lifecycle
- Govern access lifecycle
- Secure privileged access for administration
Through one convenient interface, your security team can monitor which users have access to which resources and how they are using that access.
Privileged Identity Management (PIM) is another facet of Azure identity protection worth leveraging to safeguard the most sensitive data within your company. The service lets you smartly manage access to certain resources and operations in Azure AD, Azure, Microsoft 365, and other SaaS apps. The role of this service is to act as a controller for providing just-in-time privileged access to restricted resources to LOBs who need it, along with monitoring that access usage and automatically terminating it.
Some of the main PIM features include:
- Provisioning of time-bound access to certain Azure AD and Azure resources;
- Approval management for activating privileged roles;
- Auto-MFA initiation for activating any role;
- Convenient access reviews for managing roles access;
- Quick history download for audits.
PIM is especially important for larger Azure instances as was the case with our client — Metinvest Group. As part of a large-scale digital transformation project, implemented together with Metinvest Digital and encompassing migration of two on-premises data centers (with 680 servers) and some 80,000+ business users, the Infopulse team performed advanced Azure AD configurations for effective management of user roles and permissions. Read the complete case study.
Bonus tip: Azure Information Protection (AIP) is a handy cloud-based labeling service for discovering, classifying, and protecting various documents and business communication. It further extends the labeling functionality offered by Microsoft 365 and enables the support of additional file types, as well as protects File Explorer and PowerShell.
4. Actively Monitor Your Security State
After you are done with the initial setup, check your Azure AD identity secure score — a measure between 1 and 223, indicating how well your infrastructure complies with Microsoft’s security recommendations.
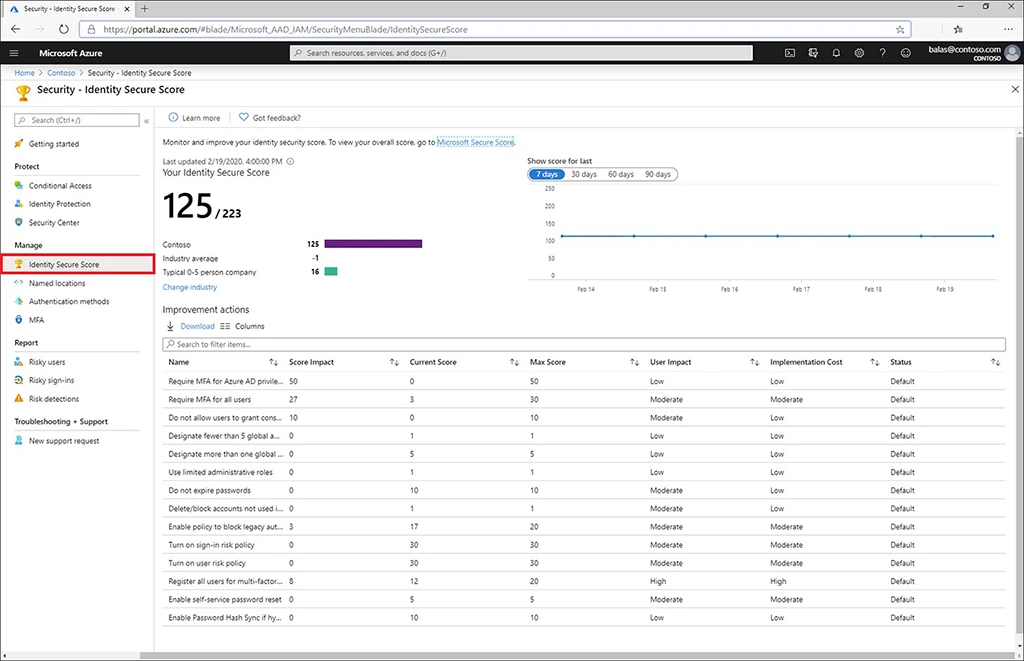
The dashboard shows how well you have coped with various tasks and lets you plan further implements by filtering them by cost and user impact.
As the next step of your Microsoft Azure information protection plan, enable identity risk monitoring using Azure AD Identity Protection. This ML-based tool helps you automate the detection and mitigation of common identity-based risks and capture relevant data around them for further investigation. By means of Microsoft Intelligent Security Graph, which analyzes over 6,5 trillion signals per day to identify suspicious behavior patterns, these findings are then translated into alerts and mitigation suggestions for Microsoft Identity Protection users.
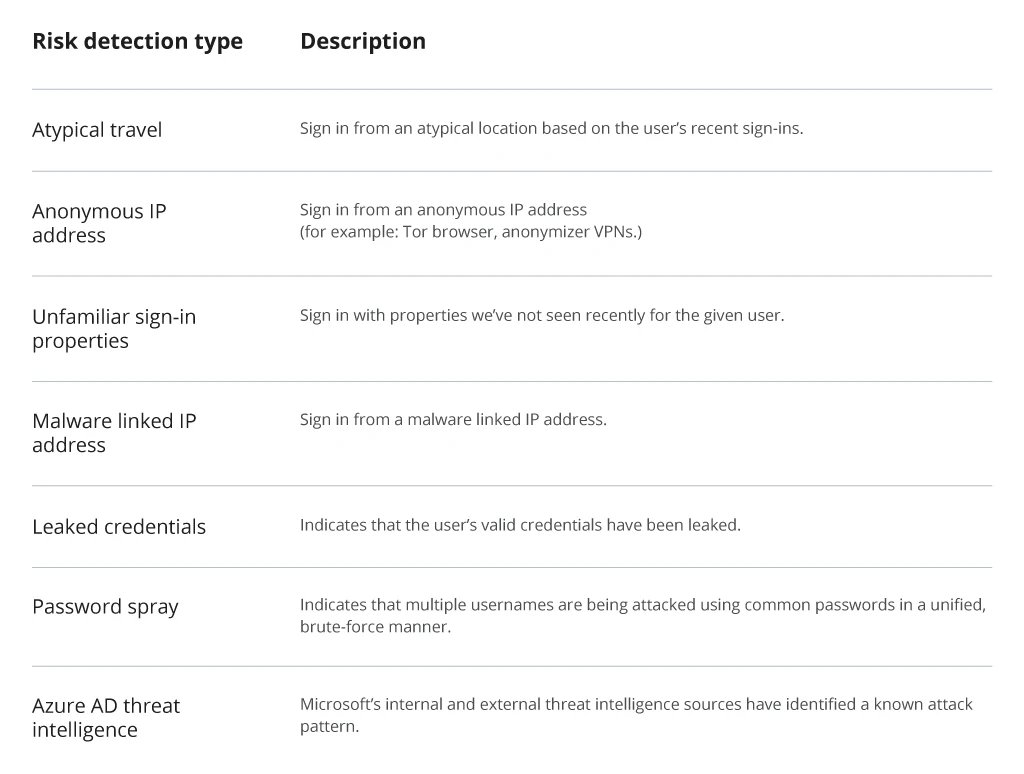
Some of the common risks the tool can detect are as follows:
Common Risks to Detect with Azure AD Identity Protection
Finally, make sure that you are continuously auditing accesses provided to various SaaS apps so that no third-party product attempts to overstep the granted permissions.
5. Automate the Common Monitoring and Management Task
For larger enterprises, effective identity management and security automation is a solid way to realize further TCO savings from Azure migration.
As already mentioned, Azure AD Identity Protection is a stellar service for automating risk monitoring and taking advantage of Microsoft’s state-of-the-art machine learning algorithms, powering threat detection within this tool. With the help of this service, you can set up automated threat responses to common attack vectors. For example:
- Roll-out new user risk policies in real-time to remedy compromised accounts.
- Implement SSO policies in real-time to stall suspicious sign-in attempts.
Also, to reduce the volume of menial work your IT service desk has to deal with you can integrate Microsoft Graph with Azure AD identity management and other services. This will help you to automate workflows such as:
- Employee onboarding/termination
- Profile maintenance
- Licenses deployment.
Lastly, many common identity management workflows can also be automated with the Azure Automation service.
To Conclude
User credentials have always been an attractive target for malicious parties. With the rise of remote work and rapid cloudification, hackers have become even more determined to access corporate systems as the rewards of doing so have majorly increased. Businesses should stay vigilant and proactive regarding their identity management and monitoring practices. Otherwise, they risk becoming another item in the growing list of recent password-related breaches.
Infopulse, a Microsoft Solutions Partner, Azure Expert MSP with multiple Microsoft Azure specializations, CSP Tier 1 for the EU and CIS, and a Forrester-recommended vendor for Microsoft Azure Services, would be delighted to further consult you on Azure Cloud security.







![Multi-Cloud Governance: Policies [thumbnail]](/uploads/media/thumbnail-280x222-multi-cloud- governance-policies-and-procedures.webp)
![Security Operations vs Security Development [thumbnail]](/uploads/media/thumbnail-280x222-how-to-strike-a-balance-between-security-operations.webp)
![Cloud WAF vs On-Premises WAF [Thumbnail]](/uploads/media/thumbnail-280x222-cloud-WAF-vs.-on-premises-WAF.webp)
![Data Storage Security [thumbnail]](/uploads/media/thumbnail-280x222-data-storage-security.webp)