Security in Telecom: 5 Current Cyber Threats and Solutions
The Main Types of Cyber Threats and Ways to Mitigate Them
SS7 and Diameter Signalling Threats
A number of core telecommunication services are still powered by flawed protocols such as SS7 (Signalling System No. 7) or Diameter. SS7 protocol, in particular, has become one of the central cyber threats to the banking industry since hackers can easily intercept 2FA authentication codes and drain users’ accounts.
Newer protocols such as SIP (Session Initiation Protocol) can also be extremely vulnerable to cyber threats without proper controls in place. For instance, in 2018 a group of attackers managed to stage a denial of service (DoS) attack on Cisco equipment through leveraging malformed SIP traffic.
However, implementing better signaling controls is proving to be a challenge for most telecoms due to the following:
- Overall complexity
- Privacy concerns
- Global title leasing
- Supply chain issues
- Network misconfigurations
- Traffic integrity
Granted, according to a report by the European Union for Cybersecurity, most telecoms have implemented the basic security measures for SS7 attacks:
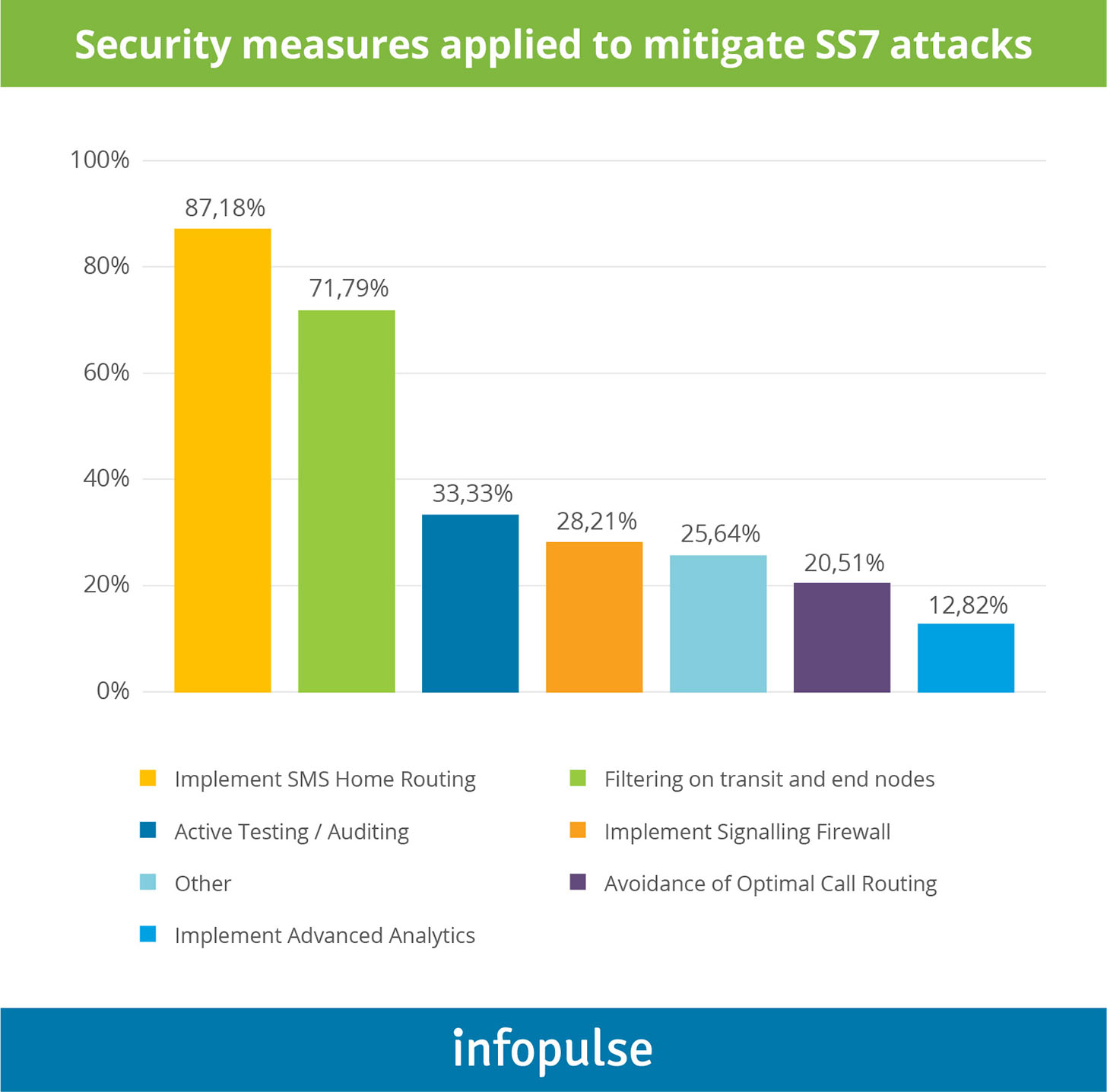
Cybersecurity Best Practices For SS7 and Diameter Protocols
- Exhaustive monitoring that covers all interconnect and outgoing traffic, as well as core network elements.
- Harden network nodes by implementing better firewall configuration rules.
- Conduct regular external network security assessments and penetration tests.
- Implement real-time anomaly detection systems to identify more advanced attacks and their prequels.
Also, keep an eye on updates from the Fraud and Security Group (FASG) work group organized by GSMA that is working on new end-to-end interconnect telecom security solutions for LTE and 5G networks.
SIP Hacking
Session Initiation Protocol (SIP), used in most voice-over-IP (VoIP) communications, is another prime target for malicious parties. Without proper telecom security system, hackers can easily tap into encrypter calls, distribute SIP malware and otherwise tamper with the VoIP services you are provisioning.
Here’s a list of cybersecurity threats that were common in 2019:
- SIP trunk hacking
- SIP toll fraud
- Eavesdropping
- Caller ID spoofing
- DDoS attacks on PBX systems
Utility suppliers in the US faced a series of VoIP attacks last year. An attacker was initially targeting 1,500 unique gateways tied to some 600 businesses, but later focused on a single company and, using a command-injection technique over HTTP, injected a malicious web shell into the company’s server outgoing directory. Granted, the hack was discovered in time before much damage had been done.
Best Practices for Protecting SIP Signalling
- Enforce strong encryption over your Transport Layer Security (TLS) and Real-Time Protocol (RTP) to protect all data transmissions.
- Implement anti-spoofing for SIP messages. Ensure that you have proper in-built mechanisms for challenging messages and authenticating SIP clients.
- Maintain strong Session Border Controller (SBC) controls that perform deep packet inspection of all SIP messages and prevent unauthorized SIP traffic.
DNS Attacks
DNS (Domain Name Security) attacks still remain a major sore point for telcos. What’s worse, the cost of such attacks is increasing year-over-year. As per Global DNS Threat Report, around 79% of the organizations faced DNS attacks in 2020. On average, the cost of a security incident was 924,000 USD. However, these stats are slightly better than a year before: the source’s report for 2019 indicates that 82% of companies experienced DNS attacks that amounted to 1.1 million USD on average.
Telecom and media became the most favored industries by attackers: averaged 11.4 attacks, with 8% incurring losses more than 5 million USD per attack. What this data is telling us is that most telecoms are completely unprepared for the latest cyber threats from this group. So, let’s brush up on the key security measures.
DNS Attack Prevention Best Practices
- Switch from a reactive to a proactive approach to cybersecurity. Start applying adaptive countermeasures.
- Implement real-time analytics for DNS transactions and gradually build up a behavioral threat detection suite, capable of detecting both known and emerging cyber threats and protect against data theft/leaks.
- Enhance your firewalls with ML-driven response policies on traffic to suspicious hostnames.
- Implement query monitoring and logging for all suspicious endpoints.
DDoS Attacks
Telcos are the prime target for DDoS attacks. As much as 65% of the global DDoS attacks in 2018 were aimed at communication services providers and the figure still remained high in 2020. Another recent report reveals that the following DDoS attacks are on the rise too:
- from February to September 2020, DDoS grew by half and was on average 98% higher than it was during the same period a year earlier. Furthermore, around 50 million DDoS attacks happened globally within a 12-month period.
- high-volume 50 Gpbs + attacks became a pressing issue for businesses lacking adequate protection.
- 59% of the total number of attacks were multi-vector incidents, which organizations are too weak to fight against.
- the most long-lasting DDoS attack was 5,698 minutes. This equals to 4 days of non-stop attacking. Notably, the key issue with DDoS incidents for the telecom sector is a ripple effect an attack of such magnitude can cause.
How Telcos Can Protect Against DDoS Attacks
- Set up robust Access control lists (ACL) – your first line of defense. Note, however, that ACL has a scaling issue. A rapid increase of temporary ACLs, built to resist a large-scale attack, can have a major performance impact on different router hardware and software, making the overall management rather challenging. Thus, it’s best to write several scripts for automatic router configuration and ACL management.
- Implement black hole scrubbing – a variation of the block hole filtering technique. In this case, the traffic is redirected to a different physical interface – a scrubbing center – that can weed out the good traffic from the malicious one. A number of software vendors offer such solutions.
- Real-time DDoS monitoring is a must. The best-of-breed tools are now powered with machine learning functionality, meaning their detection accuracy progressively increases over time.
IoT Network Security
In 2021, Gartner estimates that some 25 billion IoT devices will be connected to telecom networks. Accommodating such an increased volume of data is just one part of the challenge for telecom security though. Preventing unauthorized access, securing data transmissions and ensuring smooth monitoring of a much larger attack surface are the key security challenges for telcos.
Despite low adoption, IoT devices have already proven to present both internal and external threats to cybersecurity. First of all, the device itself can be exposed to various cyber threats and vulnerabilities due to manufacturing issues that might hinder a telecom security system. Secondly, misconfiguration and lack of proper security measures make an IoT device an easy entry-point to the entire network of devices, or worse – the supporting architecture. In short, most attackers will have an easier way of finding a leeway as the surface of attack increases.
Some of the common types of cybersecurity threats happening at network level are as follows:
- Network congestion
- RFIDs interference and spoofing
- Node jamming in WSN
- Eavesdropping attacks
- Sybil attacks
- DDoS attacks
- Routing attacks
Offering solid protection against these is a joint responsibility between network operators and IoT users.
IoT Cybersecurity Best Practices
GSMA has already developed a comprehensive IoT security assessment checklist for telcos, along with several supporting documents with security guidelines. Below are some of the key best practices the association proposes against common cybersecurity threats:
- Network operators should use UICC based mechanisms for the secure identification of IoT devices. You can also provide single sign-on services for devices but mind the security trade-offs.
- Enable secure authentication for all devices, networks and service platforms associated with an IoT Service.
- Offer data encryption services to IoT service providers to ensure high communication integrity and increase network resilience.
- Deploy private networks to support various IoT networks. These can be developed using Layer Two Tunnelling Protocol (L2TP) and secured with Internet Protocol Security (IPsec) as illustrated below:
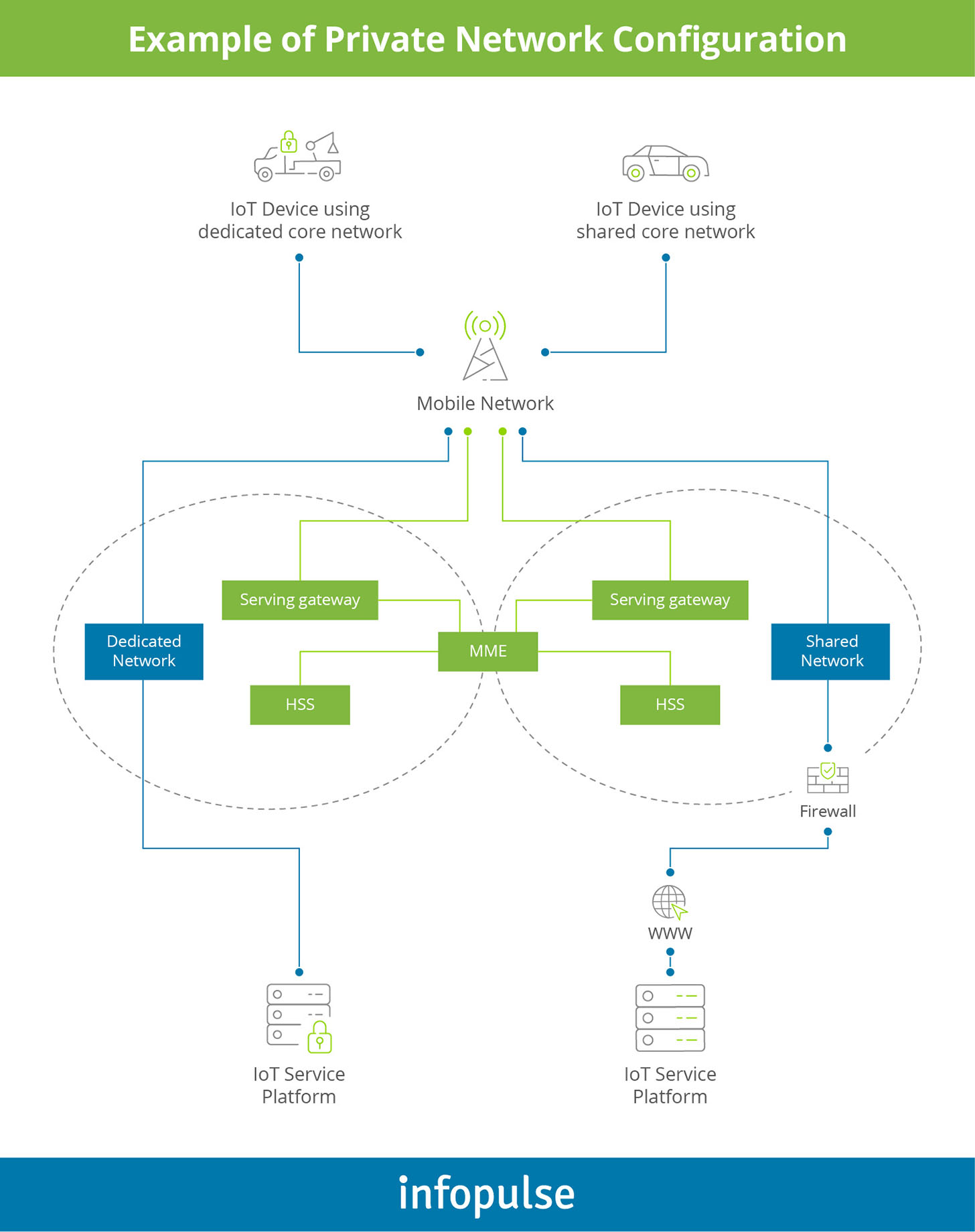
To Conclude
Telecom players have both an exciting and complex time ahead. On the one hand, the industry is undergoing major transformations, resulting in new revenue opportunities and value streams. On the other hand, an increased presence of new assets (such as IoT devices) and increased pressure on the old communication protocols enlarges the defense perimeter every telco needs to create.
Ultimately, to have strong and reliable telecom security mechanisms, you will need to switch from reactive security to proactive – one that relies on extensive monitoring and has predictive capabilities, powered by advanced analytics and AI. Conduct proper risk assessments for current systems, decentralize and automate the core security requirements with appropriate tools and run even deeper assessments for emerging technologies such as IoT, 5G, and NFV among others.
Having strong telecom expertise, Infopulse also provides a comprehensive scope of enterprise IT security services ranging from preliminary security assessments to comprehensive Security Operations Center (SOC) as a service. Let’s work together on strengthening your network resilience and future-proofing your operations against emerging threats!


![Pros and Cons of CEA [thumbnail]](/uploads/media/thumbnail-280x222-industrial-scale-of-controlled-agriEnvironment.webp)
![BPO in Telecom and BFSI [Thumbnail]](/uploads/media/thumbnail-280x222-ways-business-process-outsourcing-bpo-can-help-telecom-bfsi-and-other-industries-advance.webp)

![Power Platform for Manufacturing [Thumbnail]](/uploads/media/thumbnail-280x222-power-platform-for-manufacturing-companies-key-use-cases.webp)
![ServiceNow & Generative AI [thumbnail]](/uploads/media/thumbnail-280x222-servicenow-and-ai.webp)

![Data Analytics and AI Use Cases in Finance [Thumbnail]](/uploads/media/thumbnail-280x222-combining-data-analytics-and-ai-in-finance-benefits-and-use-cases.webp)
![AI in Telecom [Thumbnail]](/uploads/media/thumbnail-280x222-ai-in-telecom-network-optimization.webp)

![Data Analytics Use Cases in Banking [thumbnail]](/uploads/media/thumbnail-280x222-data-platform-for-banking.webp)