4 Qualities of an Efficient Security Operations Center for Telecom
To effectively balance the increased security pressure with the introduction of new IT initiatives, a growing cohort of telcos are putting plans to establish security operation centers (SOCs).
This is our second post in the ongoing SOC series, complimentary of an upcoming eBook on SOC adoption.
SOC Meaning in Telecom
SOC stands for Security Operations Center — a dedicated cybersecurity unit, empowered by cybersecurity tools, lean IT security processes, and operational templates to stand at the vanguard of threat monitoring, detection, and prevention.
Unlike traditional security departments at telecom, SOC teams are focused on proactive security measures — monitoring, detection, prevention, and system hardening — rather than reactive remediation of direct attacks and potential breaches.
An operationally efficient SOC is the result of strong people and well-defined processes.
What Assets SOC Team Protect in the Telecom Industry
The telecom industry is prone to multiple risks, emerging at different operational endpoints — data sharing with partners, mobile customer data collection and exchanges, and payment processing among others.
The vast operational spectrum makes the industry an attractive target for malicious hackers. Some of the common cybersecurity threats that became more prolific in telecom over the past several years include:
- SS7 and Diameter Signaling Threats
- DNS Attacks
- DDoS Attacks
- Attacks on IoT Networks
In addition to that, telcos are actively pressured by regulators to maintain top security standards. Minor breaches can lead to hefty fines and ongoing scrutiny for regulators.
The role of a SOC security unit is to primarily ensure visibility and control over all aspects of the telecom operations:
- Networks
- Cloud environments
- On-premises systems
- Mobile devices
Security operations center tools should be incorporated to monitor all the endpoints, servers, and applications within the organization, plus traffic exchanges with third-party services and partners. Best-in-class SOC technologies enable security specialists to proactively collect security intelligence and use it to fill in the blind spots in security.
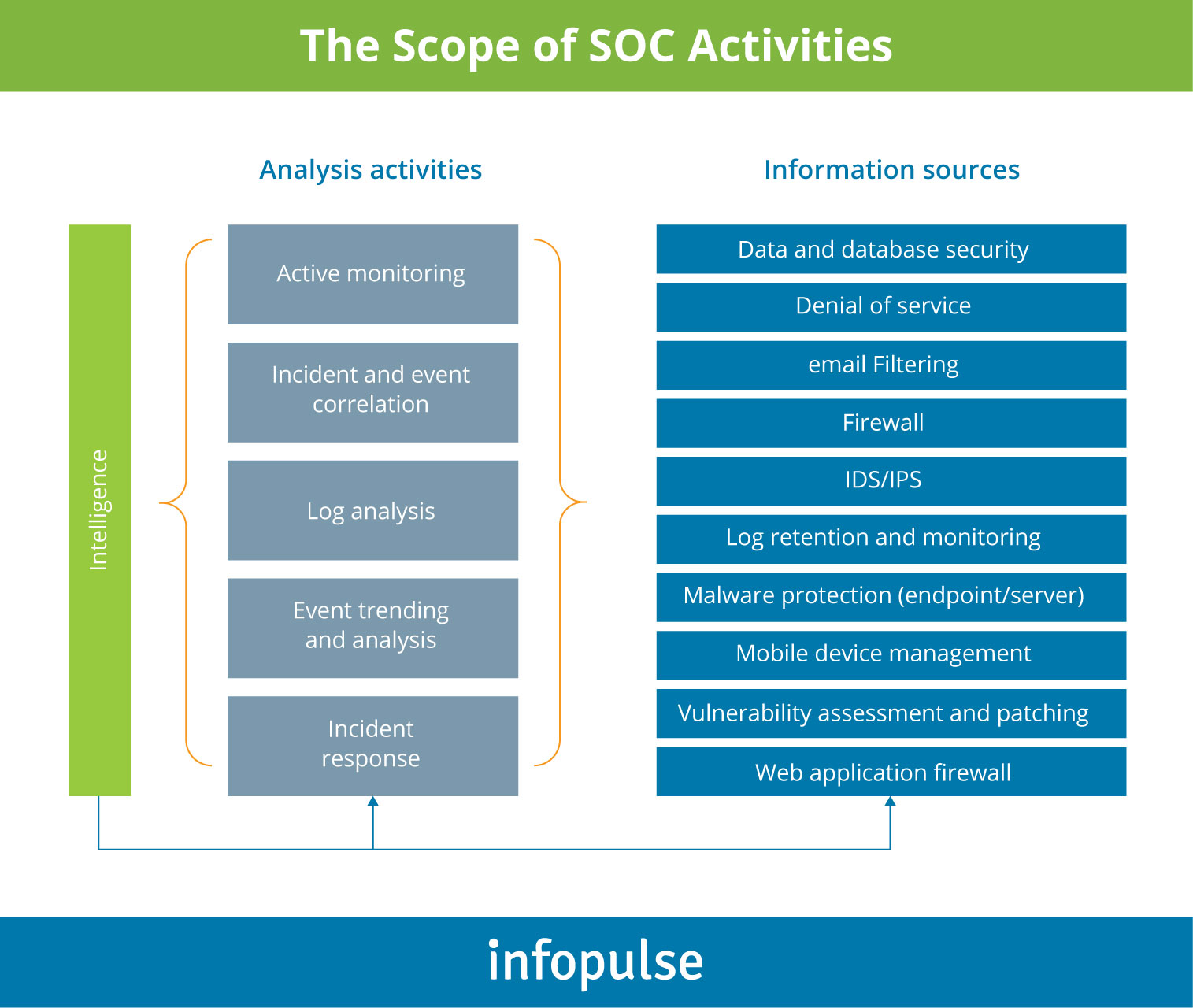
SOC engineers in telecom are also focused on addressing industry-specific vulnerabilities and preventing fraud. In particular, some common security tasks include:
- Ensure that access and use of networks and services is restricted to authorized users only
- GSM network protection against unsolicited access and unauthorized operations
- Maintain security policies in line with the ITU-T security standards
- Put down and execute security plans for SS7 network protection
- Monitor, investigate and mitigate cases of telecom fraud
- Establish protection against man-in-the-middle attacks (e.g. those using IMSI catchers)
- Prevent subscriber location and personal information disclosures
SS7 network protection, in particular, is a core area of focus for SOC teams. Being a legacy protocol, SS7 has several vulnerabilities malicious parties can exploit.
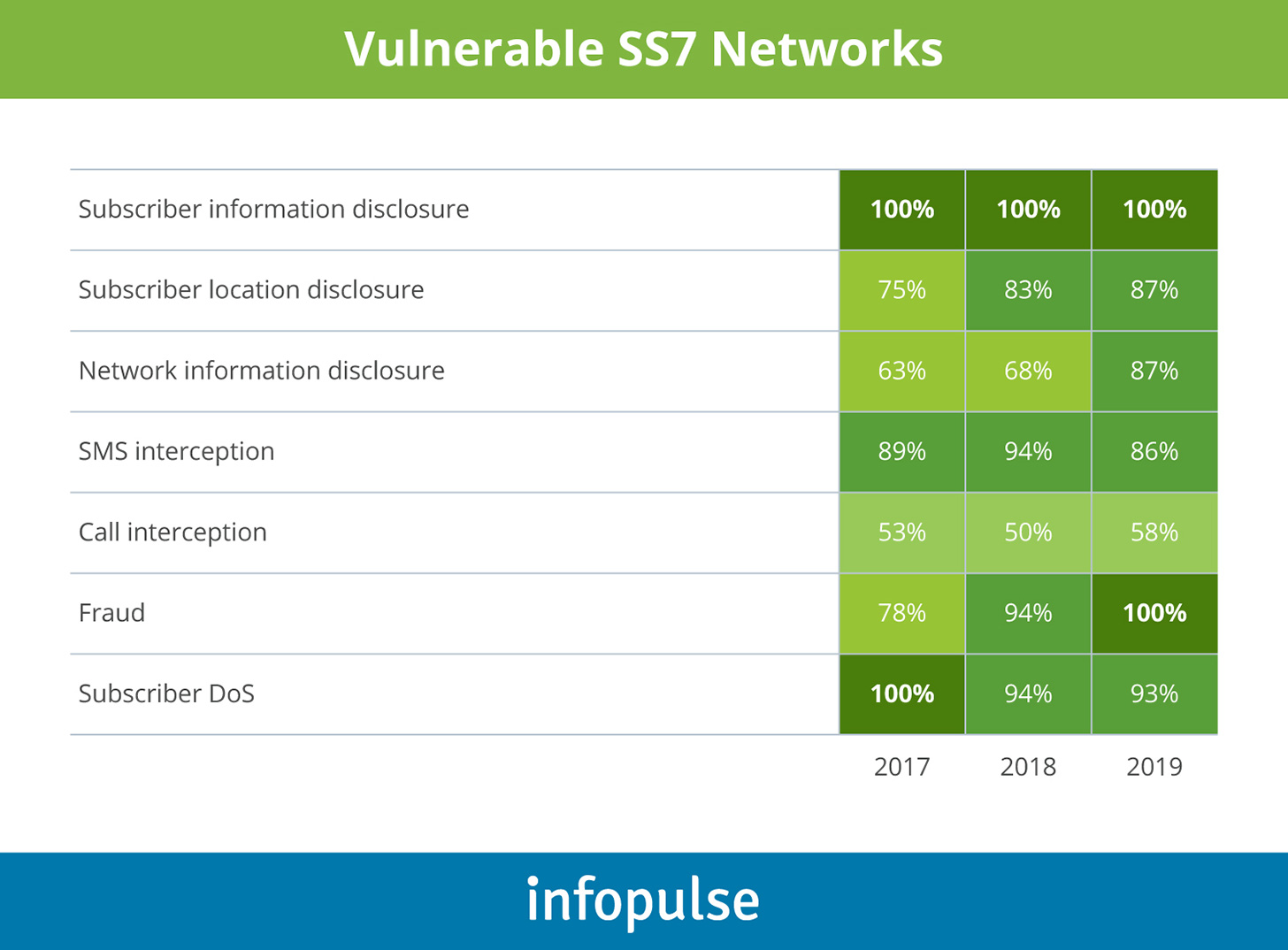
The better news, however, is that the abovementioned vulnerabilities can be effectively resolved with SS7 firewall and proper network equipment configurations, as well as signaling traffic filtering and blocking systems.
In addition, larger telecoms may also want to consider implementing extra protection against common types of telecom fraud — call and text hijacking, IRSF, PBX hacking, roaming fraud and more. Specifically, a SOC team can help establish a proper Identity management (IdM) process for all the entities within the ecosystem (service providers, subscribers, network devices, software applications, plus implement a fraud detection system that will identify any deviations in the behaviors of tracked IDs.
4 Attributes of an Effective Security Operations Center for Telecom
Aging protocols, growing volumes of data, mounting regulatory pressure, and overall vector of greater digitization have significantly expanded the size and strength of the security perimeter telcos need to build. Operators are now expected to operate under “privacy by design” protocols, with customer data protection prioritized. The requirements further extend to protecting all metadata exchanges happening within the telecom ecosystem.
With an increasing list of security jobs to be done, many telecom leaders are considering the creation of an in-house SOC center or partnerships with a SOC as a service provider. Regardless of which approaches to SOC adoption you settle for, be sure to leverage the following security operations center best practices for team setup and management.
1. Optimal Staffing Levels
The cybersecurity skills gap is reaching a tipping point. In 2020, over 3.1 million in-house security roles were left unfilled globally, which led to increased exposure to threats. In the short-term perspective, the gap is projected to widen further.

SOC software can compensate for slight shortages and a greater level of automation can lead to enhanced team productivity and performance. Yet, most telecoms cannot solely rely on SIEM (security information and event management) and SOAR (security orchestration, automation, and response) tools alone if they want to ensure robust security coverage.
Depending on the size of your operations, you should plan to hire specialists for at least three roles, as described below.
SOC Security Analyst
A cybersecurity specialist with strong analytical skills, who will be in charge of security monitoring, events analysis, and threat detection.
Skillset
- Sysadmin skills (Linux/macOS/Windows)
- Coding skills (Python, Ruby, PHP, C#, Java, etc.)
- Analytical skills (domain knowledge, expert overview of current lay of land in security)
- Cybersecurity security skills and certifications (e.g. CISSP, GCIA / GCIH)
- Coding skills (Python, Ruby, PHP, C#, Java, etc)
- Sysadmin skills (Linux/Mac/Windows)
Core responsibilities
- Review security scans, vulnerability assessments, and reviews
- Set up, configure, and manage SOC cybersecurity tools
- Review alerts and prioritize them by relevancy/urgency
- Provide Tier-1 support and escalate issues to Tier 2 / Incident Response
- Report on findings and emerging security trends, provide suggestions to further strengthen security
Security Specialists
Security Specialists have more hands-on responsibilities. They are at the front line of incident investigation, response, and prevention. Their skillset is similar to SOC analysts, but typically they have more years of security experience, plus complimentary penetration testing or white-hacking skills.
Core responsibilities:
- Review and act upon tickets, submitted by Analysts
- Develop and execute incident management plans
- Use the threat intelligence to assess the scope of the incident and investigate exposure
- Collect and analyze data on all security events to suggest new security measures.
- Respond to detected threats and provide remediation
Threat Investigators
Also called threat hunters or forensic investigators, such specialists do not wait for an attack to happen. Instead, they proactively probe the current setup for effectiveness, model different attack scenarios, and work out new measures for protection. They are experts in penetration testing, plus feel comfortable with different BI and data visualization tools.
Core responsibilities:
- Perform assess discovery and vulnerability assessments
- Test the systems against emerging threats by modeling attacks
- Conduct penetration tests to identify weak areas in your systems
- Provide recommendations for improving security processes and security operations center software optimization.
SOC Manager
For SOC, the managerial duties are similar to other departments — recruit, train, mentor, and assess the staff. SOC managers are the prime point of contact for business stakeholders. They also assist with SOC compliance reporting, support security audits, facilitate communication with other departments, and report on the SOC performance.
2. Comprehensive Staffing Schedule
Having appropriate coverage is essential when setting up an SOC. Telecom companies often require 24/7 SOC operations, which, in turn, means a larger bench of staff with a reasonable rotation schedule.
McAfee proposes the following sample schedule for SOC teams where A stands for the morning shift and the after-hours shift Monday to Friday, and B represents the afternoon shift in the SOC center and the pager shift over the weekends.
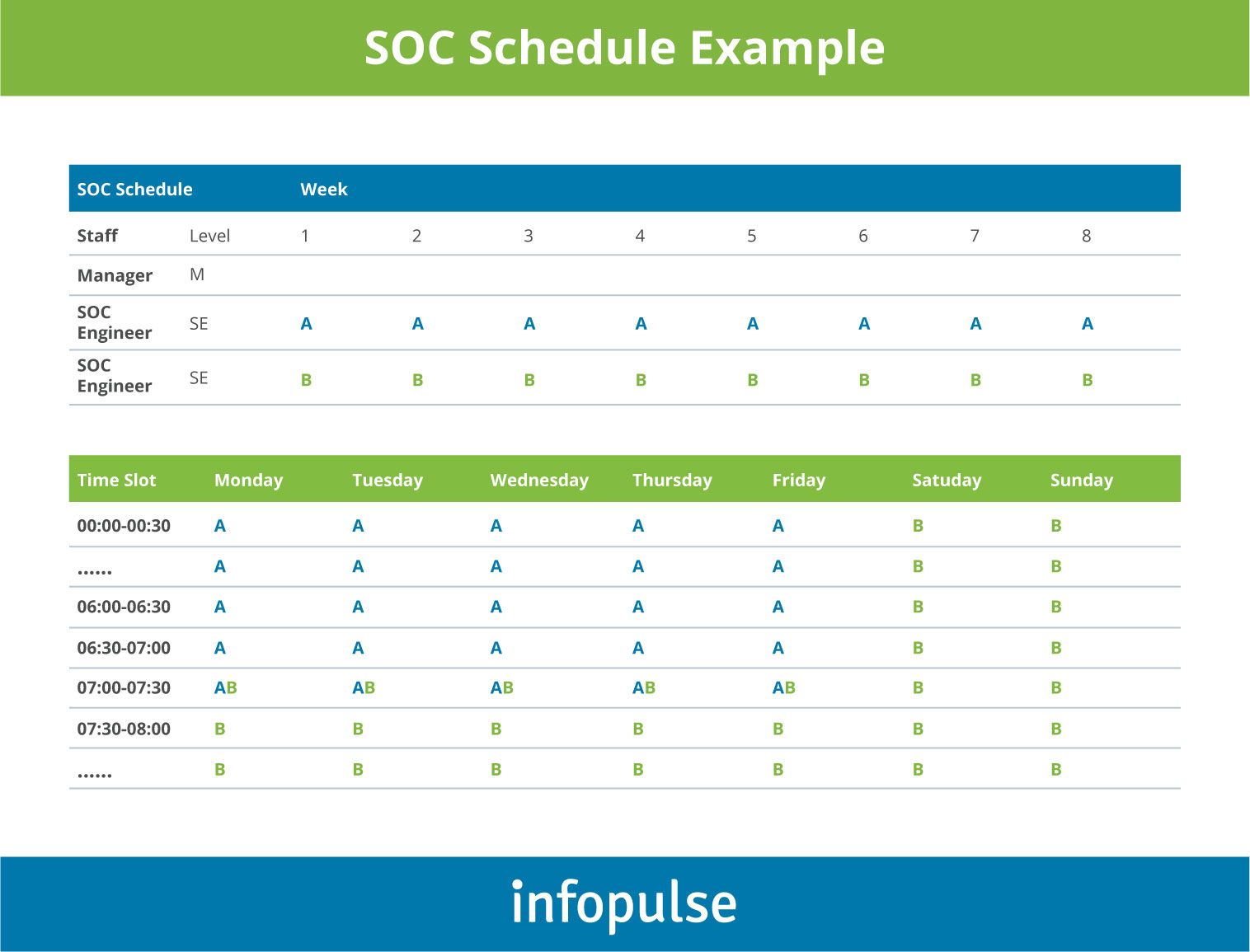
Remember: you have to keep your schedules realistic or else you risk losing some of your best talents. Cybersecurity specialists are often overworked with 31% reporting overwhelming workload.
3. Deep Domain Knowledge and Regular Upskilling
In addition to being familiar with security best practices, SOC teams in telecom also need to understand the industry intricacies related to compliance and customer data security.
A great SOC specialist for telecom should be familiar with:
- ICT security standards
- Security architecture for systems providing end-to-end communications (e.g. ITU-T X.805 architecture)
- SS7 network security best practices
- Information security management frameworks for telecom
- Public key and privilege management infrastructure
- Protection of directory information
- Best authentication protocols
- Telecom application security (VoIP, IPTV, etc)
- Local and international compliance requirements
- The current state of the threat landscape
- Common types of telecom fraud and remediation techniques
Besides hiring people with the fitting expertise, also make sure that you provide regular on-the-job training to junior personnel. According to a 2020 report by Devo, 67% of high-performing SOCs have an active skills development and training program in place.
Should you invest in cybersecurity certifications for your teams? Typically, those are handy to select candidates during hiring. However, the importance (and relevance) of certifications somewhat increases when it comes to day-to-day work, as cybersecurity specialists report:
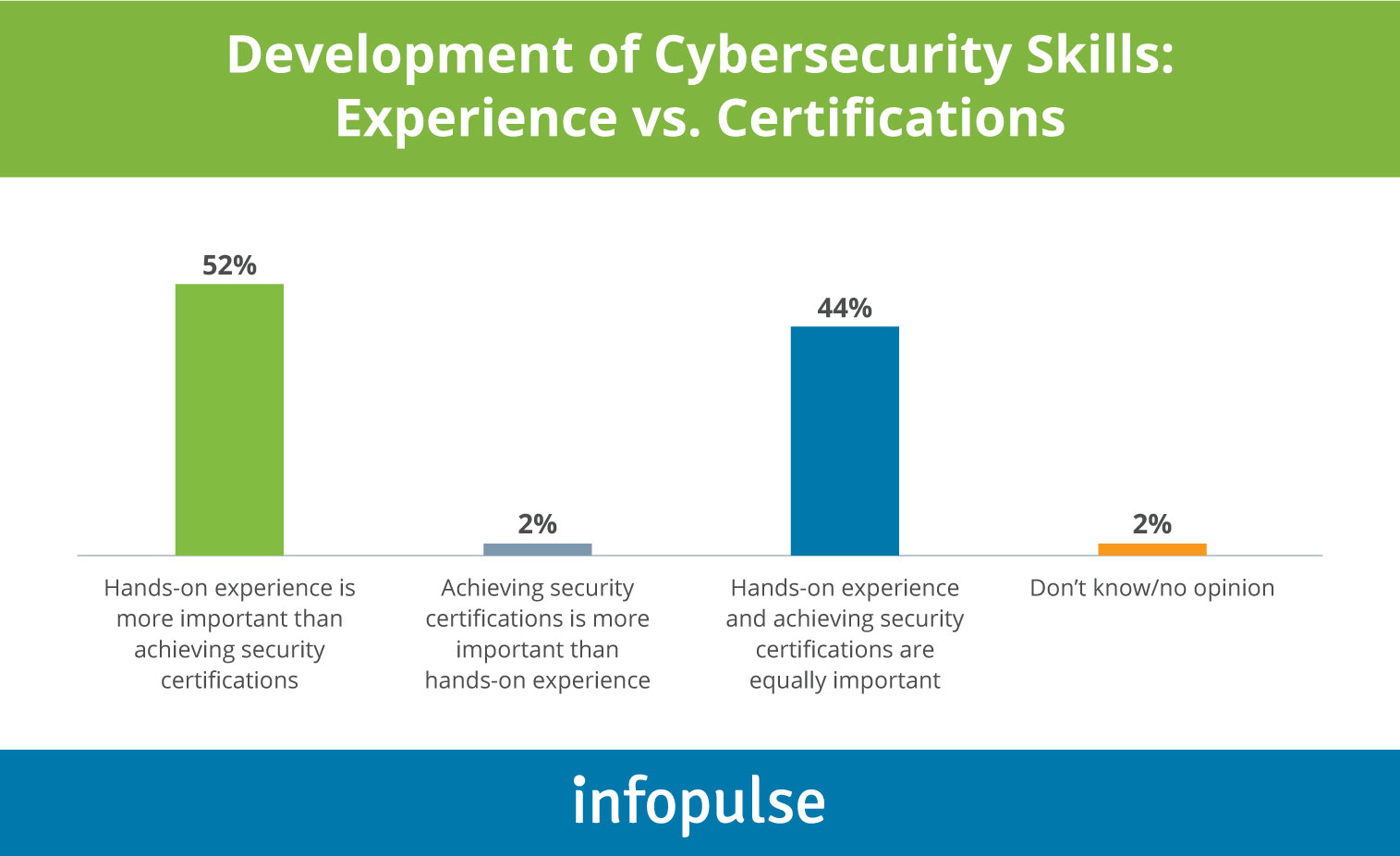
4. Strong Operational Procedures
SOC is a hub where all security information flows to monitoring and assessment. Without strong operational procedures and standardization, event management can become sporadic and ineffective, while the SOC team members themselves struggle with overwork. Efficient SOC teams operate by playbooks and standard operating procedures that clearly describe how all incidents should be monitored, assessed, investigated, mitigated, and reported.
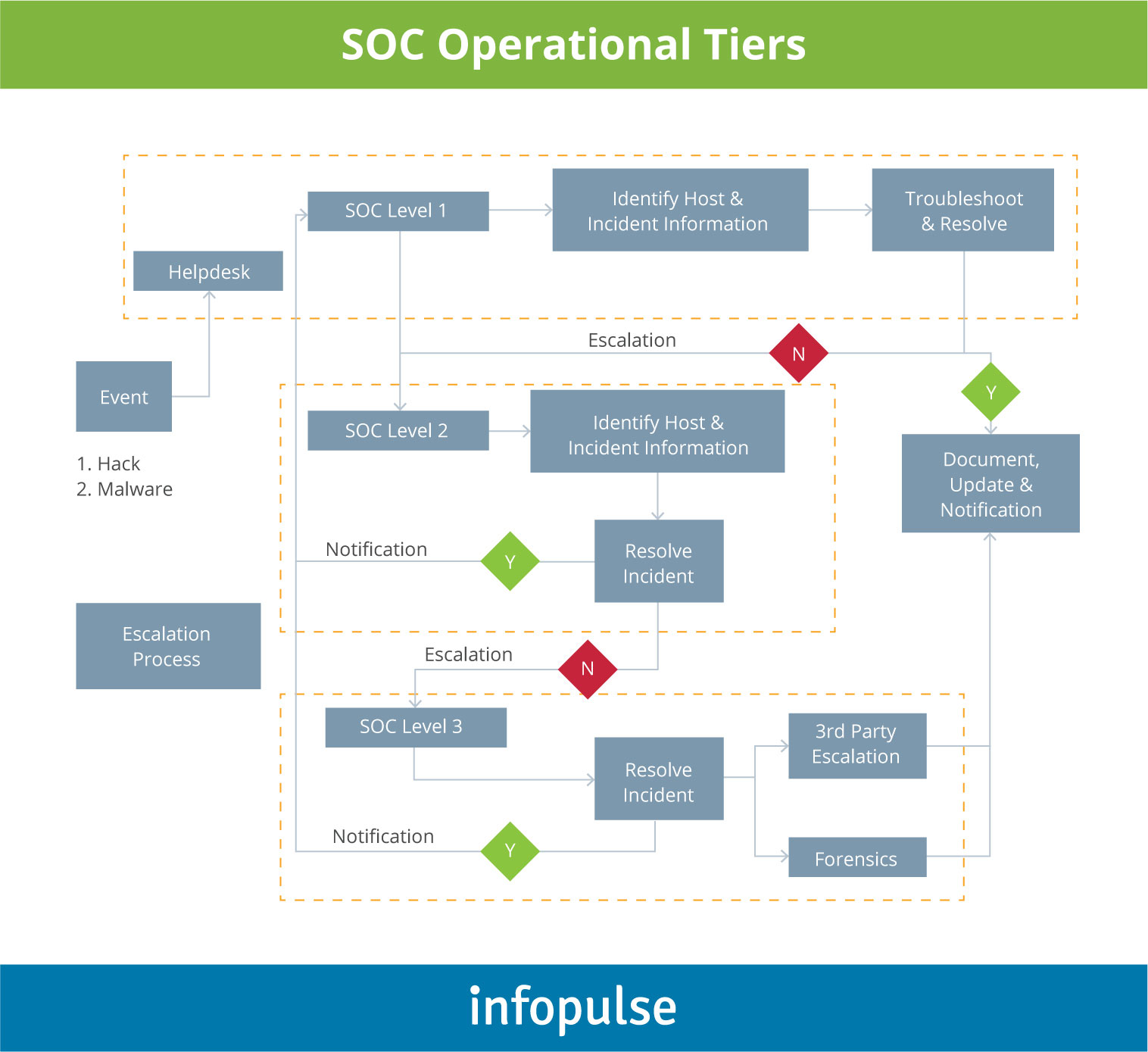
At the very basic level, the security operation center should be broken down to:
- Level 1: SOC analyst and junior personal providing Level 1 support to end-users.
- Level 2: Security specialists that are responsible for incident management, remediation, and reporting.
- Level 3: Threat analysts and managers, responsible for investigations, systems hardening, and shaping the overall vector of the security program.
Each level should have specific SOPs, the bounded scope of responsibilities, and clear escalation procedures as illustrated in the chart by McAfee below:
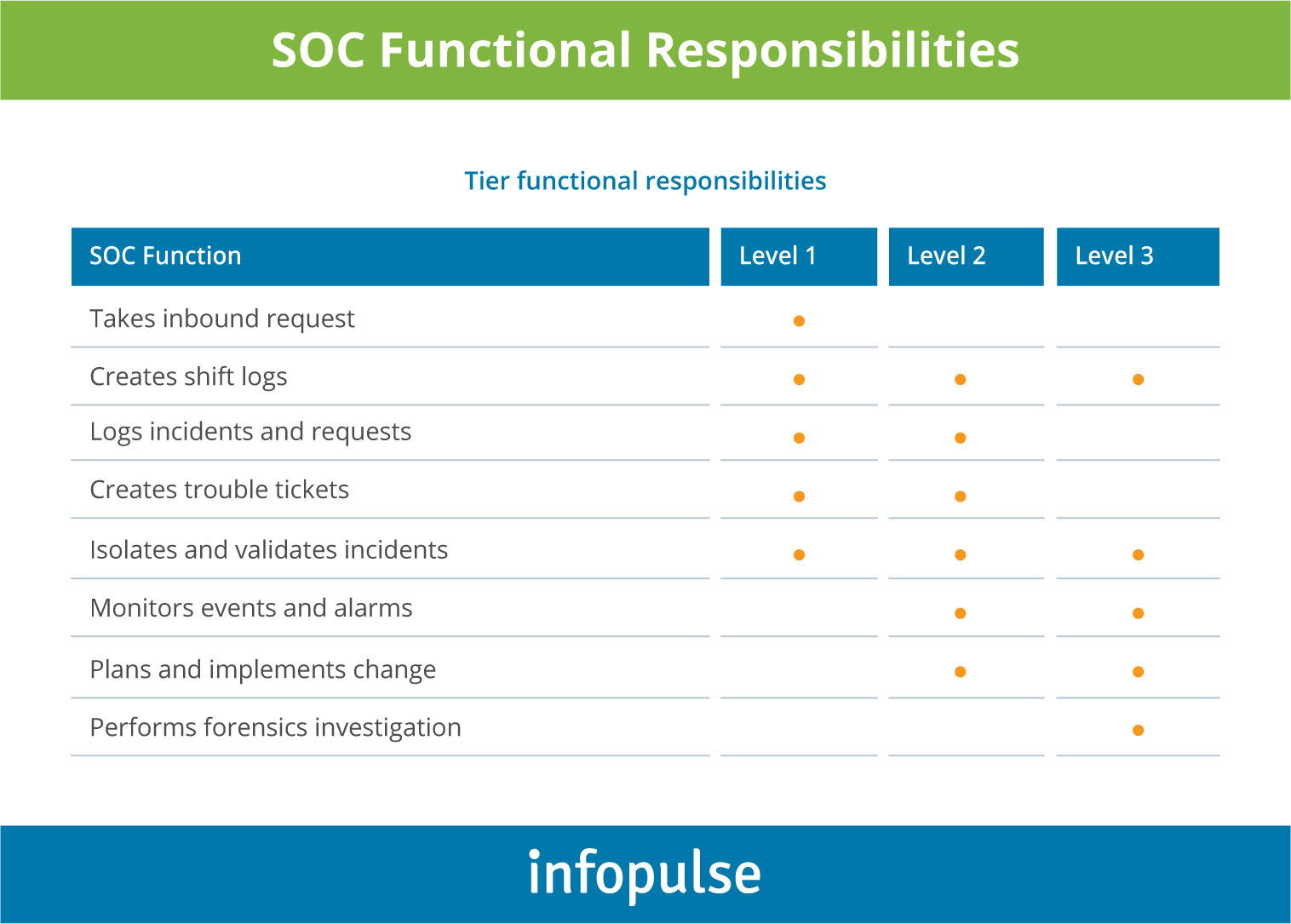
Document functional responsibilities for each operational tier to prevent overlaps and suboptimal work distribution.
(also McAfee)
Separately, establish incident escalation procedures for different types of tickets. In particular, every SOC specialist needs to understand:
- Which resources they have to assist with the resolution and how to access them
- How and when to add status updates
- What to do if there’s no response from the customer who opened the ticket
- What information to include in the incident records before escalation
- How to set the optimal priority level
- Where to reroute the most critical issues
- What to do in case of no resolution, etc.
Ultimately, SOC managers should strive to build the level of operations where results are consistent and predictive, low-value processes are automated, and overall SOC operations are well aligned with the business objectives of the telecom company.
To Conclude: SOC Efficiency Strongly Correlates with SOC Maturity
SOC is more about establishing the appropriate security processes, rather than haphazardly adopting the latest-gen SOC software or investing in top-tier security talent.
Leaders, responsible for setting up and maintaining SOC operations, should keep the overall ITSM best practices in mind and use them to attain more homogenous, consistent, and predictive SOC service levels.
Define the core functions and areas of responsibility for each role and SOC level. Set performance benchmarks and KPIs in line with the overall business requirements. Keep your SOC teams informed on the planned changes in the enterprise systems and emerging requirements from other departments. Over 35% of security specialists admit they feel stressed to find new IT initiatives that have been started by other teams without any security oversight.
Ensure that your teams are well staffed and equipped with the SOC software they need to do their best job. In particular, evaluate if your personnel has proper tools for asset discovery, vulnerability assessment, intrusion detection, pen testing, SIEM and SOAR solutions.
To learn more about establishing SOC operations, contact our security department for a personalized consultation.


![Pros and Cons of CEA [thumbnail]](/uploads/media/thumbnail-280x222-industrial-scale-of-controlled-agriEnvironment.webp)
![BPO in Telecom and BFSI [Thumbnail]](/uploads/media/thumbnail-280x222-ways-business-process-outsourcing-bpo-can-help-telecom-bfsi-and-other-industries-advance.webp)

![Power Platform for Manufacturing [Thumbnail]](/uploads/media/thumbnail-280x222-power-platform-for-manufacturing-companies-key-use-cases.webp)
![ServiceNow & Generative AI [thumbnail]](/uploads/media/thumbnail-280x222-servicenow-and-ai.webp)

![Data Analytics and AI Use Cases in Finance [Thumbnail]](/uploads/media/thumbnail-280x222-combining-data-analytics-and-ai-in-finance-benefits-and-use-cases.webp)
![AI in Telecom [Thumbnail]](/uploads/media/thumbnail-280x222-ai-in-telecom-network-optimization.webp)

![Data Analytics Use Cases in Banking [thumbnail]](/uploads/media/thumbnail-280x222-data-platform-for-banking.webp)