What is SOC? Types, Benefits and Security Challenges It Can Tackle
It follows that SOC (security operations center) has moved to the front line for consideration among enterprises. Is SOC the security solution your business needs? The following post should help you understand main roles of SOC and how it empowers business continuity.
What is SOC?
Security Operations Center (SOC) is a dedicated business unit, operating under a set of defined procedures and employing technology to continuously monitor, analyze, respond, and prevent cybersecurity incidents.
Acting as a hub, SOC teams take full control over the pre-established security operating procedures (SOPs) to ensure full coverage of the corporate’s technical environment and infrastructure, as well as ensuring compliance with the regulatory standards. SOC teams are responsible for monitoring the company’s infrastructure, networks, connected devices, and all data exchanges happening between them.
Apart from assuming the “watch guard” role, SOC services providers also perform regular assessments of the company’s overall security posture and suggest further improvements in response to emerging threats.
Enterprise SOC responsibilities include:
- Proactive security monitoring
- Incident management plan development and execution
- Threat response and remediation
- Log management
- Alert prioritization, management, and response
- Root cause analysis
- Vulnerability management and assessments
- Infrastructure and network hardening
In essence, SOC teams establish the protocol for preventive security maintenance and act accordingly. Proactive detection and cybersecurity incident response mechanisms should already be in place prior to the establishment of the SOC cybersecurity unit.
To understand whether your organization is ready for SOC, determine what technological and workflow/process capabilities are already realized.
Types of SOC Operations by Maturity Levels
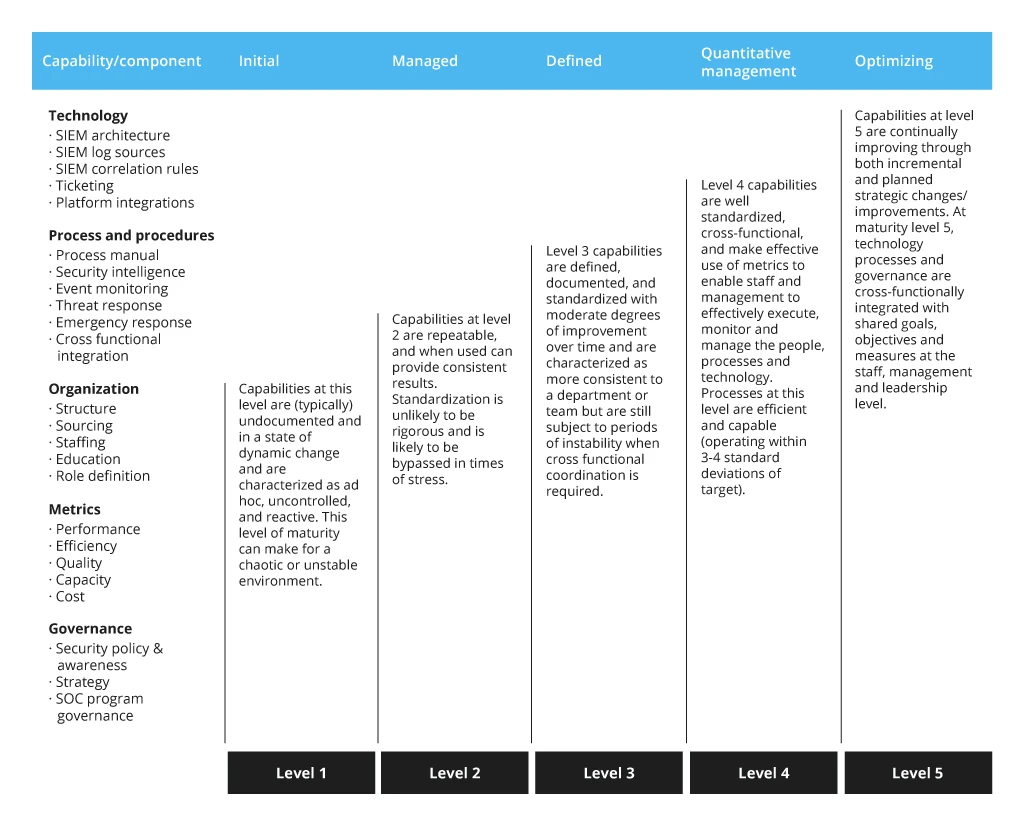
To rightsize the scope of IT cybersecurity services, Infopulse begins each engagement with an in-depth audit of the customer’s IT infrastructure, security processes, and technical capabilities.
In terms of cybersecurity maturity, organizations vary between Level 1 and Level 5 depending on the above factors.
Level 1
At ground level, companies already have the following security controls in place:
- Baseline security monitoring and response, dictated by compliance requirements
- Ad hoc log data collection and management
- Entry-level endpoint detection response
- No formal incident response and management plans
Such companies have the minimum necessary security requirements covered. However, they aren’t in a good shape to effectively respond to targeted attacks and remain vulnerable to insider breaches.
In most cases, low maturity stems from the lack of people and domain expertise for establishing effective threat detection, prioritization, and management.
Level 2
At this stage, businesses rely on manual and proactive threat response, yet standardization is lacking. This often results in sporadic security coverage and prolonged response to security incidents.
At Level 2 companies already have:
- Established security event centralization capabilities
- Reactive threat intelligence workflows
- Entry-level analytics capabilities
- Automated alert prioritization
- Manual vulnerability assessment
The above results in a higher degree of security. However, the company has capabilities to detect major threats, rather than identify early signs of breach or exposure. Security teams still have blind spots, especially when it comes to sophisticated attacks. Visibility into both internal and external threats is moderate.
Level 3
Level 3 organizations rely on documented, consistent security best practices and also leverage security tools to streamline repetitive chores.
The range of capabilities includes:
- Formalized monitoring process
- Analytics-based threat intelligence
- Established incident management and response plans
- A wider range of threat detection capabilities
- Proactive threat identification
- Automated workflows for threat investigation
SOC solutions and teams can be effectively established at this point to drive further operational improvements in terms of visibility, hardening, and proactive monitoring. Level 3 organizations are in a good position to detect incidents early but they may require a longer time to respond due to somewhat lacking cross-functional coordination abilities.
Level 4
Level 4 organizations can decisively respond to an array of security incidents thanks to a well-documented response process, backed by automated threat detection, investigation, and analytics tools.
The following security facets are in place:
- Consolidated log data and security event centralization
- Server, endpoint, and network forensics
- Mature threat detection and response processes
- Machine learning solutions for anomaly detection
- A high degree of standard workflow automation
- KPI/SLA-based performance capabilities
Level 4 organizations can rapidly handle emerging threats at the onset stage and effectively collaborate across the board to drive company-wide security improvements. Such businesses are also likely to have 24/7 physical SOC teams or rely on a SOC as a service provider.
Level 5
Security is a company-wide endeavor, actively supported by all stakeholders. Level 5 organizations assumed a proactive stance on threat management and security. They have:
- Corporate-wide agenda for ensuring certain levels of security and driving continuous improvement
- 24/7 security monitoring, prevention, and detection systems in place
- Proactive capabilities to identify and mitigate vulnerabilities
- Mature SIEM architecture and supporting SOC technologies for maximizing their staff’s efficiency.
Typically, Level 5 organizations operate in regulated industries — finance, telecom, and healthcare among others — and their aspirations to security excellence are also driven by regulatory and compliance requirements. They are also a prime target for cybercriminals but have the resilience to withstand targeted attacks and stay one step ahead of emerging threats.
The Benefits of SOC
Given that 56% of enterprises receive over 1,000+ daily security alerts, it is safe to assume that the main benefit of SOC as a business function is to enable a more effective, rapid, and formalized response to those events.
Beyond that, the establishment of SOC also results in the following benefits:
- Continuous protection; a higher degree of business continuity
- Unified and centralized responses to threats, based on SOPs/compliance requirements
- Faster investigation and remediation of vulnerabilities and security issues
- Deep-level analysis of the threat landscape and reporting on findings
- Continuous improvements in the security posture
The indirect benefits of SOC (and mature cybersecurity in general) also include:
- Improved compliance
- Lower chances of breaches
- Undisrupted service levels
- Higher brand reputation
Building a Business Case for SOC Adoption
SOC generates the most benefits for businesses at Level 3 to 5. If your organization is still at a lower level of cybersecurity maturity, it is worth considering cybersecurity consulting services first to prioritize subsequent strategic initiatives and technology investments.
Prior to putting plans for establishing SOC operations, business leaders should evaluate their cybersecurity maturity levels and build their business case based on those findings.
Assess the Current Cybersecurity Maturity Levels
SOC operations are complex. Not every type of business needs a dedicated SOC team since staunch cyber protection can be established via alternative means such as:
- Centralized identity management and single sign-on
- SIEM systems implementation (e.g., Azure Sentinel)
- Network security implementation (Anti-DDoS, IPS, IDS, Proxy, SSL, Wireless)
- Traffic monitoring solutions (e.g., Azure Traffic Manager)
Businesses that can gain the most benefits out of SOC should already have:
- Established critical IT infrastructure protection
- Baseline event monitoring and logging
- Threat detection, prevention, and monitoring capabilities
- Sufficient cybersecurity acumen to distinguish between the reactive and proactive approaches to security and the need of deploying each option at the right time.
Determine the Functions You Need
Depending on your industry, the position on the maturity spectrum, and in-house talent, your needs for different SOC technology solutions and processes may vary.
The five essential functions of SOC include:
- Security threat monitoring — Which tools and workflows do you have in place? Do your operations require 24/7 monitoring? Can you identify your current blind spots?
- Security incident management — Are there any business, regulatory, or compliance requirements that need to be met? Are you bound by customer SLAs? Do you have established metrics for monitoring the team’s efficiency?
- Personnel recruitment and retaining — On average, companies require 8 months to hire and train an in-house SOC analyst. Are you considering alternative service arrangements such as outsourcing or contracting with a managed services provider?
- Process development and optimization — Do you have documented operational processes and SOPs? What about workflows and operational playbooks? Documentation is key to driving subsequent improvements.
- Emerging threat strategy — What is your strategy for tackling novel threats? Do you plan to invest in a new analytics and monitoring technology to facilitate discovery? How do you plan to ensure that your cybersecurity practices remain up to date?
Estimate Your Capacity Requirements
The two common operational scenarios are in-house and virtual SOCs. The latter can be organized as outstaffing, managed team, or “SOC as a service” solution. Each option has its merit and certain constraints.
In-house operations may seem like the simplest option. However, lack of existing expertise for setting up the operations, plus recruiting challenges can extend the SOC establishment timeline. In-house operations also require a separate budget. On average, enterprises spend $2.86 million annually on maintaining an in-house SOC.
Delegating SOC maintenance to a managed services provider reduces the setup timeline and provides access to the missing expertise. For that reason, over 50% of businesses choose to partially or completely outsource their SOC. Infopulse also has the capacity and skillset to help businesses build a SOC center or support existing operations.
Conclusion
SOC is a strategic security “asset”, protecting businesses against known and emerging threats. Gaining the capabilities to proactively identify threats and vulnerabilities at a nascent stage is particularly crucial for enterprises in regulated industries, where a breach leads to hefty compliance fees and brand damage.
At the same time, SOC is more than just an IT function, it is a consolidated set of company-wide operational practices for driving continuous improvements. Given the SOC’s far-reaching implications, establishing such a unit is challenging.
Contact Infopulse security specialists to receive a preliminary consultation on your cybersecurity maturity levels and guidance on the subsequent steps in SOC adoption.


![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)





![Multi-Cloud Governance: Policies [thumbnail]](/uploads/media/thumbnail-280x222-multi-cloud- governance-policies-and-procedures.webp)
![Security Operations vs Security Development [thumbnail]](/uploads/media/thumbnail-280x222-how-to-strike-a-balance-between-security-operations.webp)
![Cloud WAF vs On-Premises WAF [Thumbnail]](/uploads/media/thumbnail-280x222-cloud-WAF-vs.-on-premises-WAF.webp)