SMS Fraud Cases and Recommended Measures to Prevent Them
Nowadays, in the modern world of OTT (over-the-top) applications like WhatsApp, Viber, Telegram, etc., some people could think legacy SMS business to be on the verge of extinction. This is especially true for the younger generation that were born in the age of smart devices.
You may think so as well, however, it does not reflect the real situation.
In 2019 only, an SMS business generated more than 500 million USD according to the humblest estimates. Traffic volume at the end of the year exceeded 7 trillion messages, as stated in the Kaleido Intelligence and Mobilesquared SMS market research.
The research covers not only conventional P2P (person-to-person) traffic, but A2P (application-to-person) and P2A (person-to-application) messaging as well.
While P2P SMS is slightly going down by 8% a year, A2P traffic is growing steadily year after year by about 10% annually. Moreover, it is expected to increase further. Subscribers continue receiving different kinds of application notifications (from Facebook, Google, etc.), verification codes (two-factor authentication), messages from banks, including one-time-passwords (OTPs), advertisements, promotions, reminders, and so on and so forth.
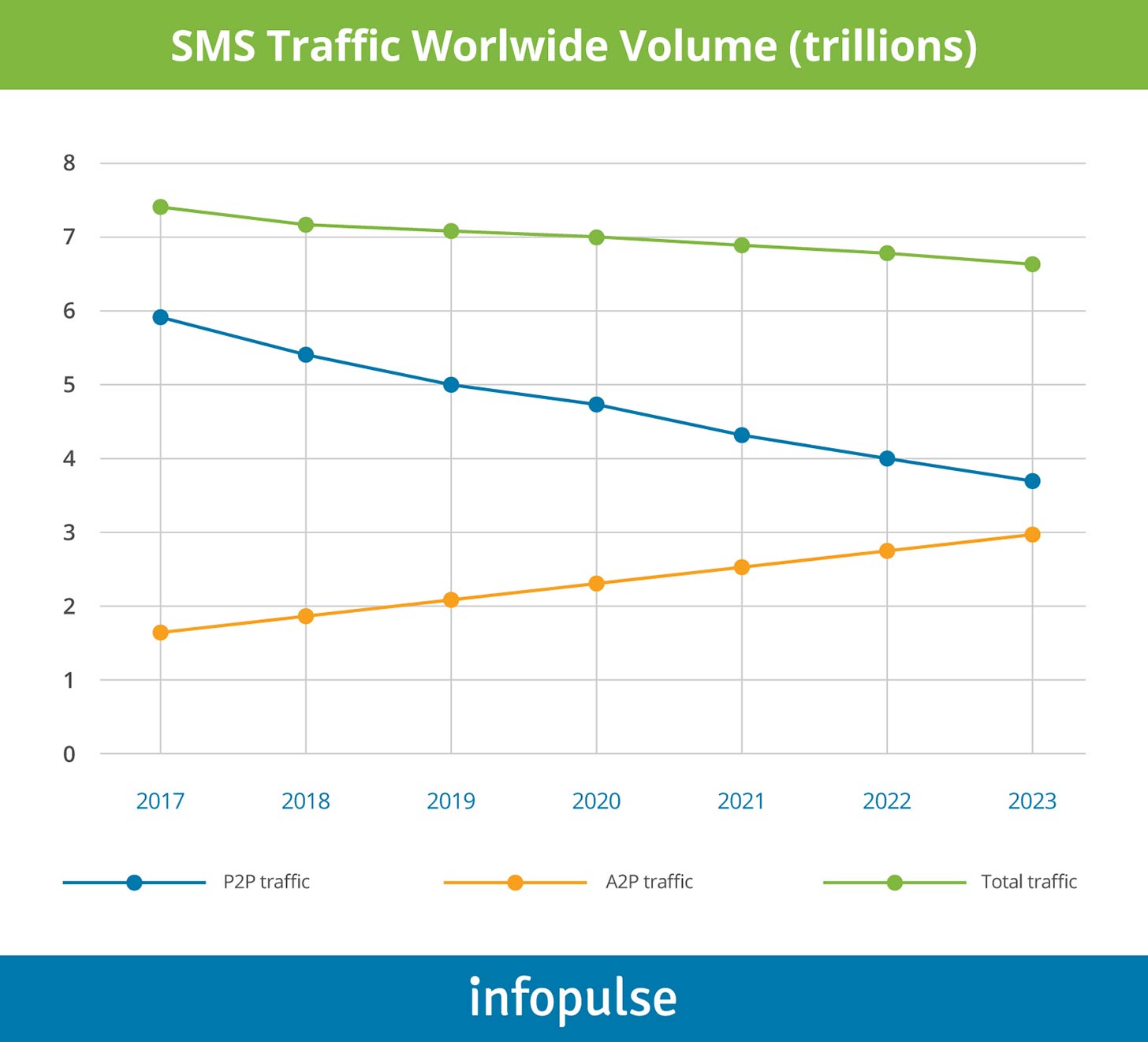
Today, SMS is more than a simple, instant communication platform; it is a scalable solution that can be automated and integrated with other business applications. This communication environment has undergone and stimulated many changes over its almost 30-year lifespan and is not likely to perish any time soon.
How SMS Fraud Threats Impact Subscribers and Operators
As mobile network operators (MNOs) open more and more SMS interconnection points and support new interfaces for SMS message submission from content providers and A2P services, they also provide fraudsters with new opportunities for targeting subscribers via the messaging service.
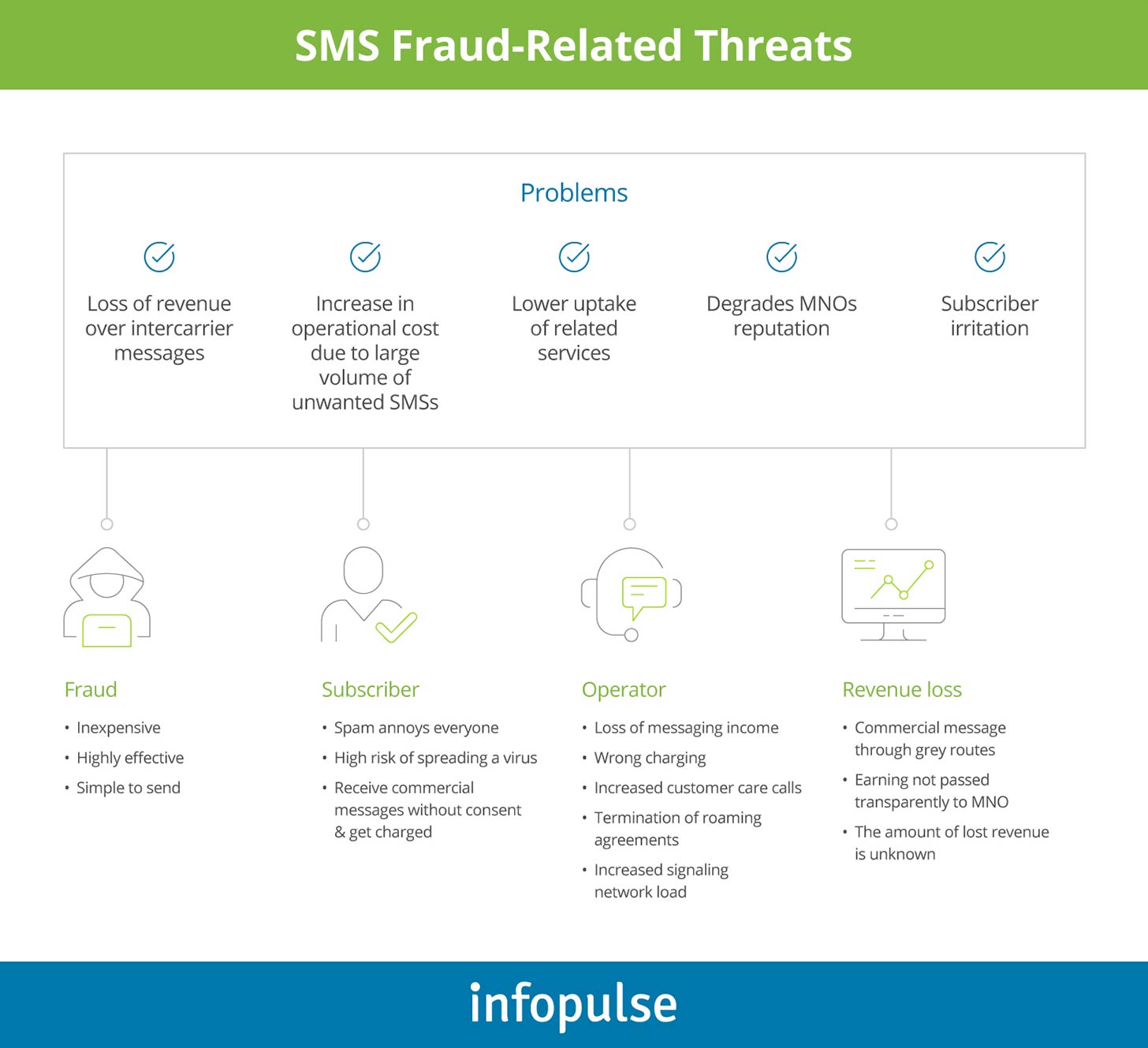
SMS fraud-related threats can be classified in different categories and can, at various levels, affect both operators and their subscribers.
Revenue Loss
Fraudsters can take advantage of technical gaps to send messages via home networks free of charge. Operators consequently suffer revenue losses due to the capacity usage of their messaging systems, and quite often even termination charges, which they pay when fraudulent messages are sent out of the home network. As the content of these messages is unregulated, the network operator may experience customer care issues and serious reputation losses.
Impact on User Experience
One common example of such threats is spam, which occurs when marketers use the SMS service to promote usually useless products and services to unwilling subscribers. Although spam may not represent direct revenue leakage, if the spammer pays for the SMS service, it can cause customer care problems. Moreover, uncontrolled spam in the home network may lead to significant customer churn.
Regulatory Penalties
SMS service can also be targeted by third parties to deliver undesirable content to the network or subscribers. Such content may be politically sensitive or considered immoral. Subscribers and national regulators tend to hold the network responsible for the nature of the content provided through their messaging services. Thereby, the responsibility for preventing such frauds lies with the operator that should ensure efficient mechanisms to control the content sent via their network.
When SMS attacks take place on a large scale, they can even congest the vital international SS7 signaling links of mobile network operators and compromise their valuable roaming business.
The Most Widespread and Well-Known SMS Fraud Cases
GT scanning (open SMSC seeking)
GT scanning refers to sending multiple mobile originated SMS (SMS-MO) to all Global Titles (GTs) addresses from one mobile operator in order to find unsecured SMS-Centers (SMSCs that do not control the A-number). Multiple forward short message (FSM) submits are received, generally from the same MSISDN (mobile subscriber integrated services digital number, or just a subscriber’s number) with the called SCCP address (signaling connection control part) and SMSC address incremented on each attempt. The easiest of these scans to spot are sequential in nature, scanning 10.000 GTs at a time. There can be no valid reason for such networks scanning other than locating unsecured SMSCs. With simpler computer integration with mobiles and SMS emulation software readily available, this type of activity is likely to be intensified.
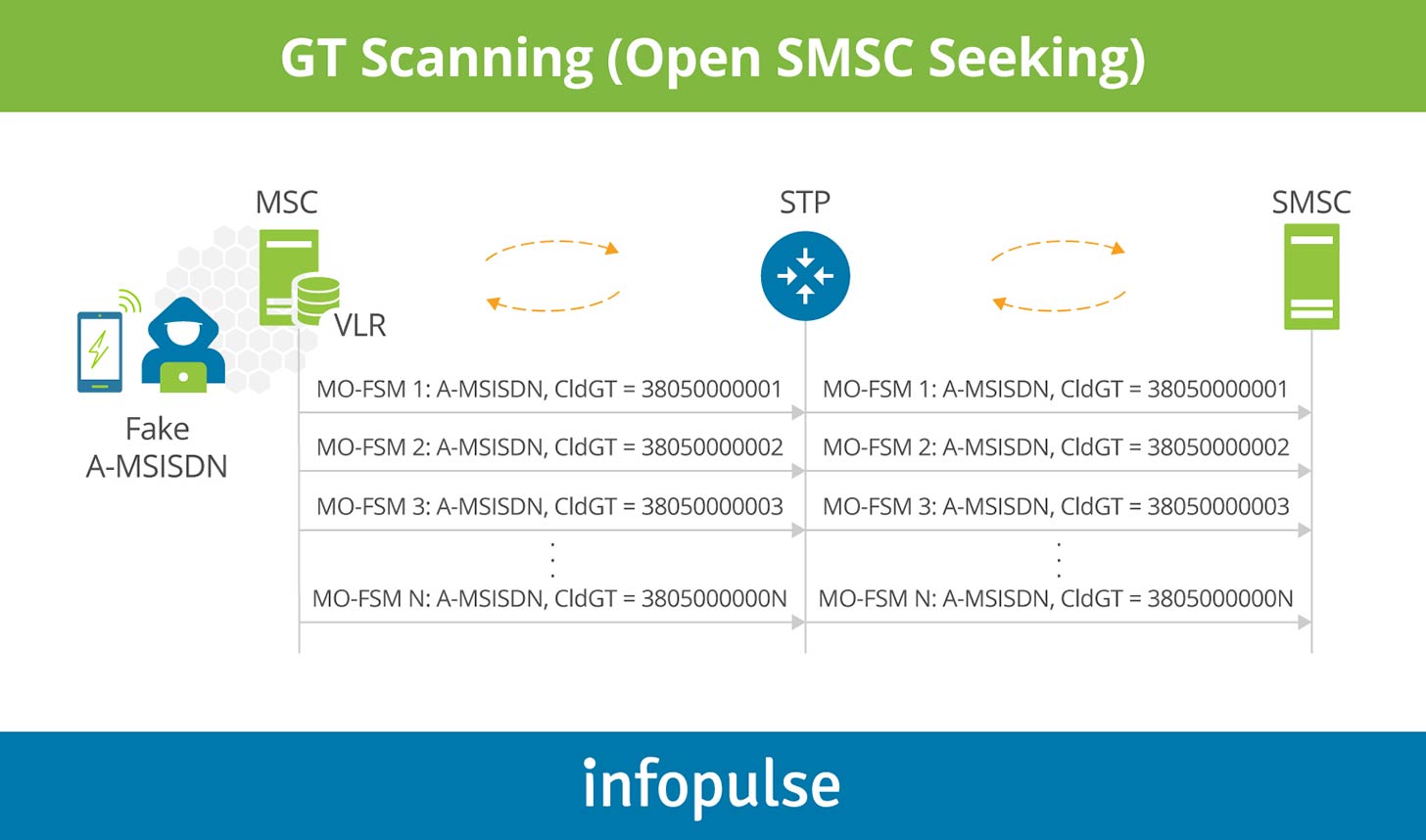
GT scanning is not significantly harmful by itself, however, it usually serves as a preparatory step for the next more dangerous attacks.
SMS spoofing
SMS Spoofing occurs when a sender manipulates the address information. It is often done in order to disguise a user that has roamed onto a foreign network and is submitting messages to the home network. Frequently, these messages are addressed to destinations outside the home network with the home SMSC essentially being “hijacked” to send messages to other networks. This is an unauthorized use of the home public land mobile network (HPLMN) SMSC by a third party. In this case, SMS-MO with a manipulated A-MSISDN (real or wrong) enters the HPMN from a foreign visitor location register (VLR with a real or wrong SCCP address).
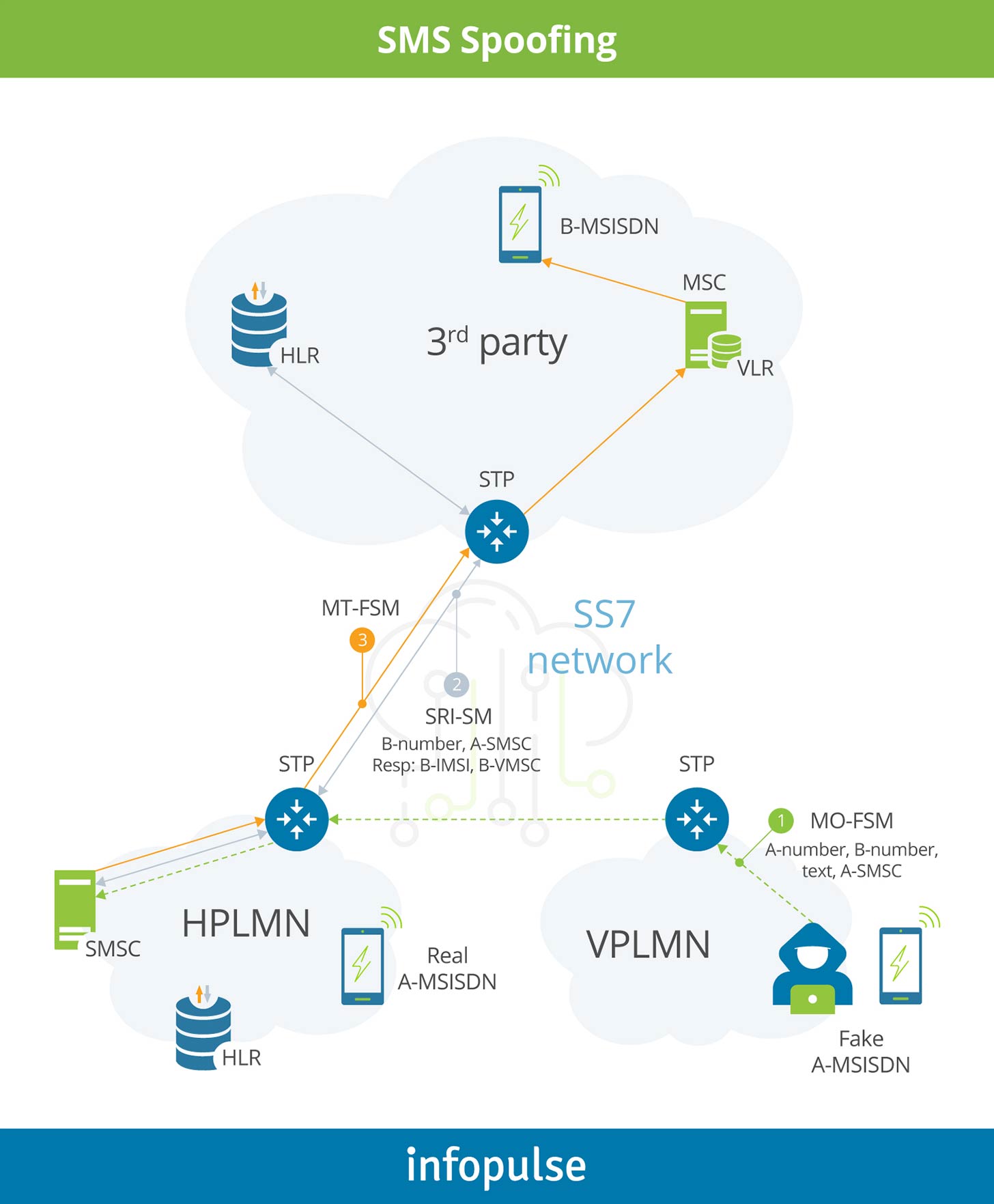
Such kinds of attacks allow fraudsters to use someone’s SMSC for their purposes.
For example, this way SMS aggregators can deliver huge amount of SMS A2P traffic to multiple destinations free of charge. While they receive payments from their customers, e.g. banks or OTTs like Google, Apple, Facebook, they do not compensate the traffic delivery. On the other hand, a hacked MNO might be charged by the destination operator based on the corresponding agreement (AA.19 – SMS Interworking Agreement).
Effective technique to address the attack
However, in most cases a properly configured SMS firewall, if present, can help prevent such issues.
Before delivering the incoming SMS-MO to the SMSC, an SMS firewall should perform an SRI-SM request (send routing information request) to the home location register (HLR) of the calling A-number. This way, the operator can verify whether the originating MSISDN is legitimate or not: HLR should respond with A-number’s IMSI and VMSC address.
If HLR replies with an error, e.g. unknown subscriber, the SMS-MO should be blocked.
Apart from that, the technique helps verify whether the caller’s location stored in the HLR matches the VMSC address the SMS-MO comes from. In case of a mismatch, the SMS-MO should be blocked.
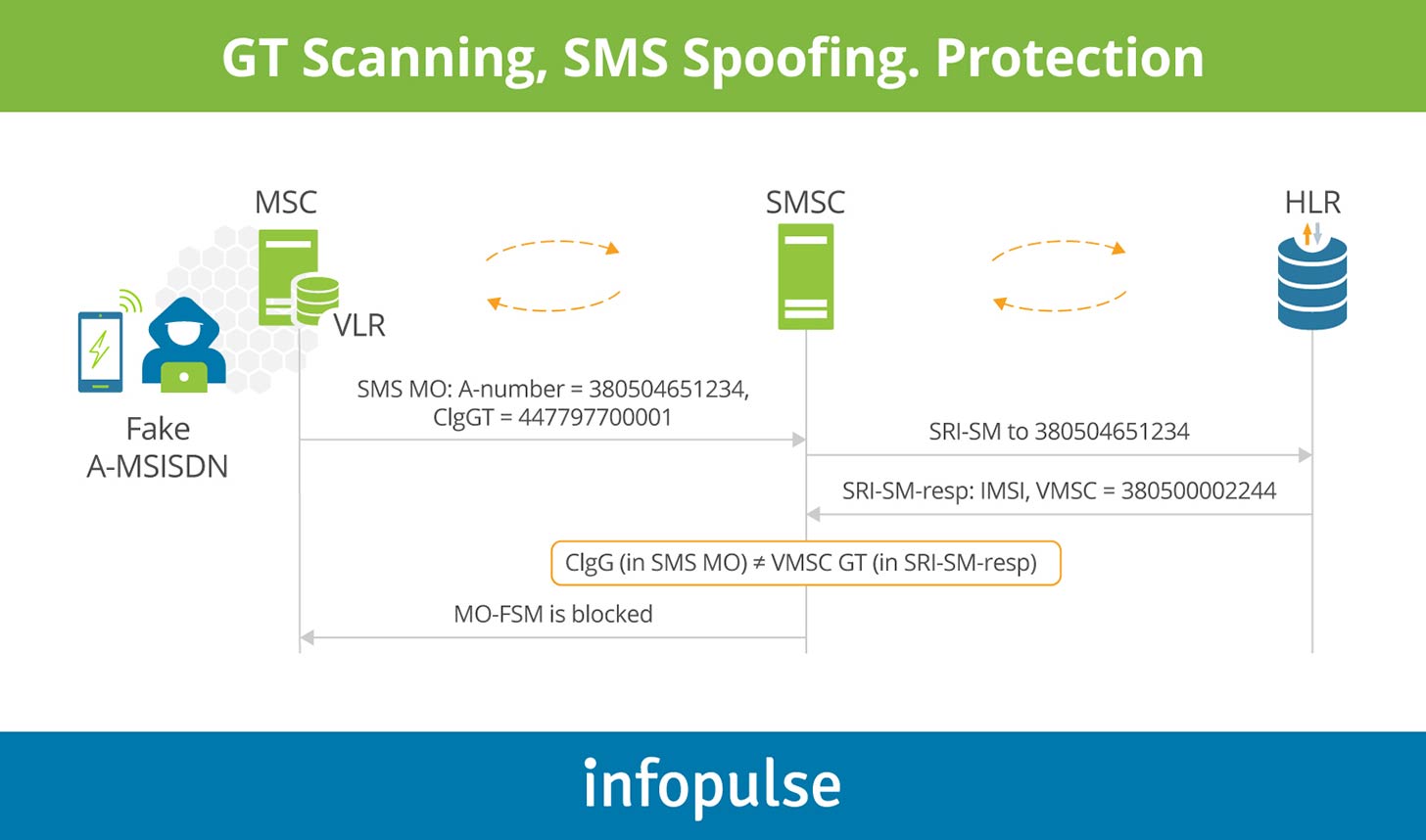
An SMS firewall can also have preconfigured counter-based filters. These filters block the A-number or the calling VMSC GT if there are too many transactions coming from the same A-number/VMSC address for a certain period (X seconds, Y minutes, Z hours, etc.).
SMS faking
In general, SMSC is used to send SMS-MT to a PLMN user but in a manner that conceals the true identity of the SMSC source. Typically, it is achieved by substituting a valid address with another PLMN address. When the faking technique is applied in conjunction with spam content, then the complaints are sent to the genuine PLMN. The normal delivery of SMS-MT contains two stages: the SMSC uses the destination MSISDN to address a MAP message SRI-SM (Send Routing Information for Short Message) to the HLR of that customer to find out whether the MSISDN is valid. If it can receive an SMS, the next step is to determine the current MSC that the destination user is registered on. The HLR responds to the SMSC with the corresponding information.
In the second phase, the SMSC sends the actual text of the message, including the sender’s ID, to the currently registered MSC and a MAP message MT-FSM (Mobile Terminated Forward Short Message). The MSC responds to confirm that the message was delivered in case of success, and generates a CDR containing all the relevant information, including the SMSC address.
In case of faking, the first part consists of the same steps as described above. However, the second part is modified so that the source address in the MAP message MT-FSM is changed, often to someone else’s SMSC address. The manipulation of the SMSC address may cause incorrect inter-PLMN SMS billing. Faking the source address in the SCCP calling GT and the Service Centre Address in the MAP message MT-FSM is impossible without considerable efforts. In other words, it does not happen by accident. It happens because in most cases it requires a software patch on the SMSC.
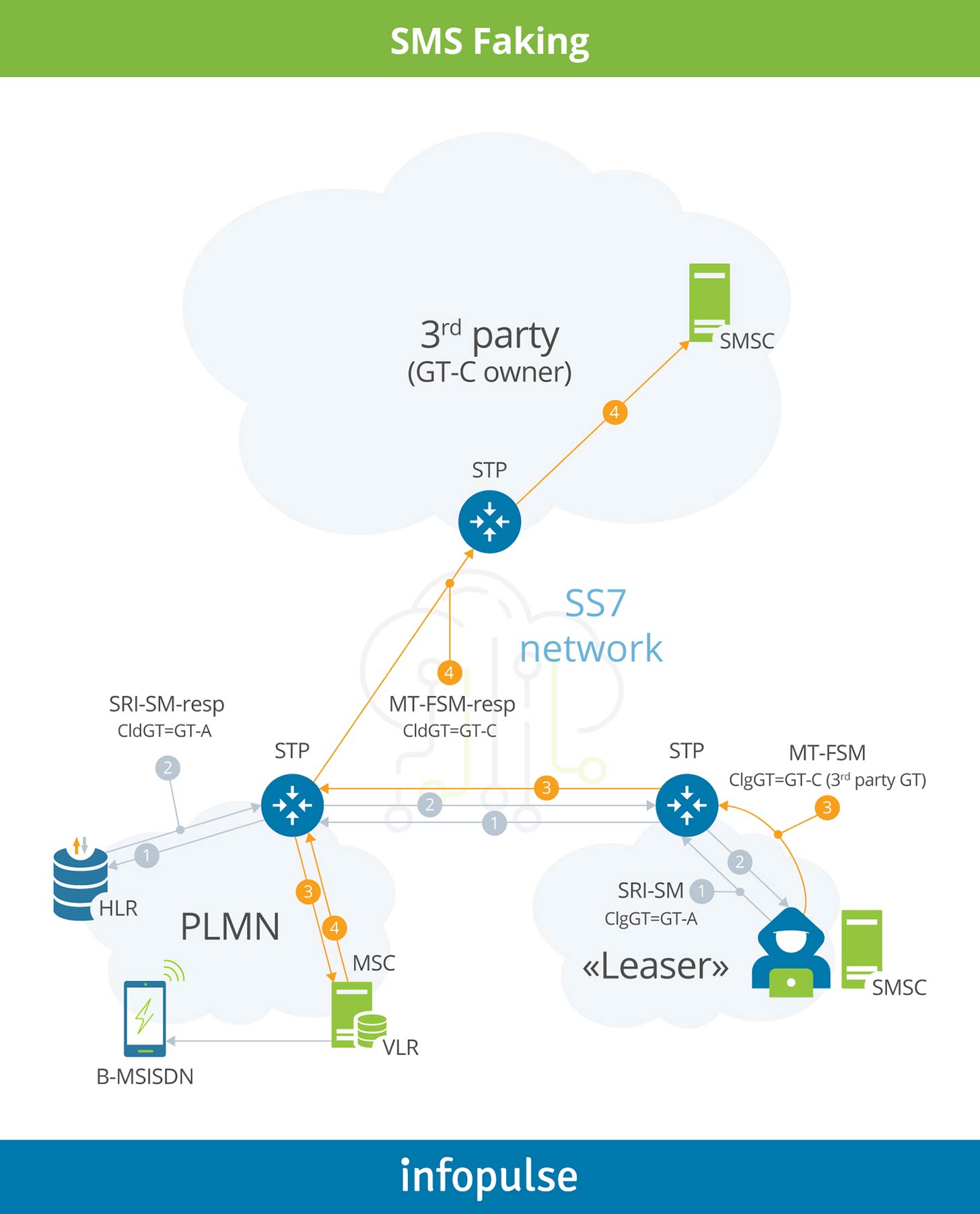
The easiest way to avoid such unsolicited traffic is to block single MT-FSMs. It means that the SMS firewall should block MT-FSM messages that come without preliminary SRI-SM requests from the same GT and SMSC address.
SMS leasing/sponsoring
Nowadays, mobile operators quite often lease their own GTs to a third party, most often SMS aggregators.
The reason behind it is cost reduction, typically utilized by smaller MNOs. As network subscribers become engaged in active conversation with their contacts around the globe, the number of sent and received P2P messages tends to be about equal. Hereby, an MNO does not need to sign multiple SMS interworking agreements with roaming partners to charge each other for the SMS traffic. Otherwise, the revenue would be almost the same as the cost.
Mutual forgiveness agreement
To address the situation, mobile operators often sign mutual forgiveness deals or have no official agreement in place at all. According to these arrangements, they do not charge each other for the incoming SMS traffic but continue invoicing their own subscribers. It helps save both money and time, as there are no invoices to be sent to the partners, no disputes, no investigations in case of data discrepancies, etc.
Many MNOs and SMS aggregators consider this situation as an opportunity.
To enable SMS leasing, an SMS aggregator X pays a certain amount of money to the operator Y for GT rental. These GTs are later used for free SMS traffic delivery to the networks that have mutual forgiveness SMS agreements with the operator Y.
The main difference between SMS faking and SMS sponsoring is that in the latter case, a GT owner knows that their GTs are being used by a third party. Moreover, it allows the operator to receive their profit as mentioned above.
Furthermore, an SMS aggregator X can provide his SS7 carriers with a notification letter, where MNO Y confirms that they allow aggregator X to use some of their GTs, and requests SS7 provider to adapt the routing accordingly. It means that the SS7 carrier will start routing the traffic of the leased GTs not to their real owner (operator Y) but to the temporary user – the aggregator X.
In order to block the P2P traffic coming from the leased GTs, operators’ SMS firewall can perform two main checks:
- Compare calling SCCP GT to MAP SMSC address. They should belong to the same network.
- Compare A-address to MAP SMSC address. They should belong to the same network as well.
For example, if subscriber 46708123456 (Sweden) sends a message to their friend or colleague, this message should normally go to the destination network from the SMSC address 46XXXXXXXXX (Sweden).
There might be exceptions, for instance when the source network uses an SMS hub solution. In this case, an official SMS hub GT/SMSC address should be whitelisted in the firewall.
If an operator wants to block all unsolicited A2P messages, then, apart from the checks above, they should also block alphanumeric sender IDs and short codes, namely A-numbers containing 6 digits or less. Content-based filters can also be fine-tuned to filter messages with particular keywords, key phrases or the same pattern, e.g. “You won a big prize! Call +XXXXXXXXXX to get more details”.
Counter-based filters described earlier might also be helpful.
Flooding
Flooding is a large number of messages sent to one or more destinations with the purpose of slowing down the operator network or jamming one or more mobile terminals. The sent messages may be valid or invalid. Flooding can be combined with spoofing or spamming.
An SMS firewall can filter out such traffic by detecting:
- Similar content;
- Same message type;
- Same calling SCCP address;
- Same origin MSISDN during a predefined time span (MO-FSM, MT-FSM).
IMSI harvesting
IMSI harvesting is usually a large number of single SRI-SMs sent to the HLR towards different MSISDNs to check their validity, availability and location. It often precedes SMS faking attacks.
Efficient countermeasures include counter-based filters that should block SRI-SMs coming from the same GT call or MAP SMSC address during a short period of time.
Conclusion
In this post, I tried to cover several popular widespread SMS fraud techniques that allow fraudsters and SMS providers to deliver messaging traffic free of charge. However, at the same time SMS firewall solutions improve day by day.
Fighting against fraudulent SMS traffic helps avoid subscriber’s dissatisfaction with the services and saves mobile operators’ reputation. On the other hand, by blocking grey routes, operators stimulate SMS aggregators to send useful A2P traffic (verification codes, bank transaction information) through the official paid routes and therefore increases revenue.
Infopulse can help you address SMS issues that cause significant revenue leakage and reinforce your telecom network by applying cutting-edge security practices and measures. Contact our telecom experts today!



![CX with Virtual Assistants in Telecom [thumbnail]](/uploads/media/280x222-how-to-improve-cx-in-telecom-with-virtual-assistants.webp)
![Power Apps Licensing Guide [thumbnail]](/uploads/media/thumbnail-280x222-power-apps-licensing-guide.webp)
![Expanding NOC into Service Monitoring [thumbnail]](/uploads/media/280x222-best-practices-of-expanding-telecom-noc.webp)
![Cloud-Native for Banking [thumbnail]](/uploads/media/cloud-native-solutions-for-banking_280x222.webp)
![Generative AI and Power BI [thumbnail]](/uploads/media/thumbnail-280x222-generative-AI-and-Power-BI-a-powerful.webp)
![Data Governance in Healthcare [thumbnail]](/uploads/media/blog-post-data-governance-in-healthcare_280x222.webp)
![Super Apps Review [thumbnail]](/uploads/media/thumbnail-280x222-introducing-Super-App-a-Better-Approach-to-All-in-One-Experience.webp)
![SAP Service Insight [thumbnail]](/uploads/media/Service Insight-Infopulse-SAP-Vendor-280x222.webp)
