NOC and SOC Integration for Telecom: Opportunities and Challenges
Security operations center (SOC) and network operations center (NOC) have long been two reliable bastions of corporate protection. As of recently, many telecoms are also looking to converge these two divisions.
A 2020 EMA study notes that over 90% of respondents plan to increase the collaboration between network and security teams. Among them, 63% have formalized collaboration plans. These contain guidelines on establishing shared standard operating procedures, collaborative workflows, and tighter toolkit integrations.
The same study also suggests that companies with tight SOC/NOC collaboration (or even full convergence into NSOC) have a better security posture and more effective network management processes.
Should your organization consider SOC/NOC integration as well? The answer depends on your overall SOC maturity and operational readiness for executing transformations. We further break down the benefits and challenges of establishing shared accountability and practices among the two units.
Why SOC/NOC Integration is Complex, but Necessary for Telecom
NOC is in charge of monitoring your networks and hardware devices (including nodes, firewalls, routers, and lately IoT devices). The team’s core duties include identification, response, and remediation of network incidents — ranging from power outages to technical failures and direct attacks. NOC is focused on maintaining high network uptime and undisrupted connectivity.
SOC in telecom is in charge of corporate cybersecurity. The team’s efforts are primarily focused on the transition from reactive to proactive response — that is ensuring your organization is well-prepared to resist any type of cyberattack or fraud. Their alert dashboards are configured to report on suspicious activities, anomalies, and other early patterns of security threats, malware, or harmful insider activity.
SOC teams can also venture into conducting network mapping as part of security risk assessments, as well as handling device protection — a turf shared with NOC.
In fact, at the lowest level, NOC and SOC analysts perform similar duties:
- Analyze and monitor events/incidents
- Perform triage and escalation
- Channel communication to the right departments
The difference is that NOC and SOC analysts rely on different types of tools and alerts to detect and investigate the incident. For example, a NOC analyst may use an SNMP/Syslog-based alerting system, which notifies them about downtime at some node. Based on that data and their experience, they will likely interpret it as a device outage event or equipment failure. At the same time, a SOC analyst, equipped with SIEM/SOAR tools and their respective knowledge may view the issue as a sign of compromised equipment.
Such differences in tools and views often result in operational inefficiencies. The two teams will work on investigating the same issue from two different angles without exchanging insights. This can increase the mean time to repair (MTTR) and lead to longer periods of disruption.
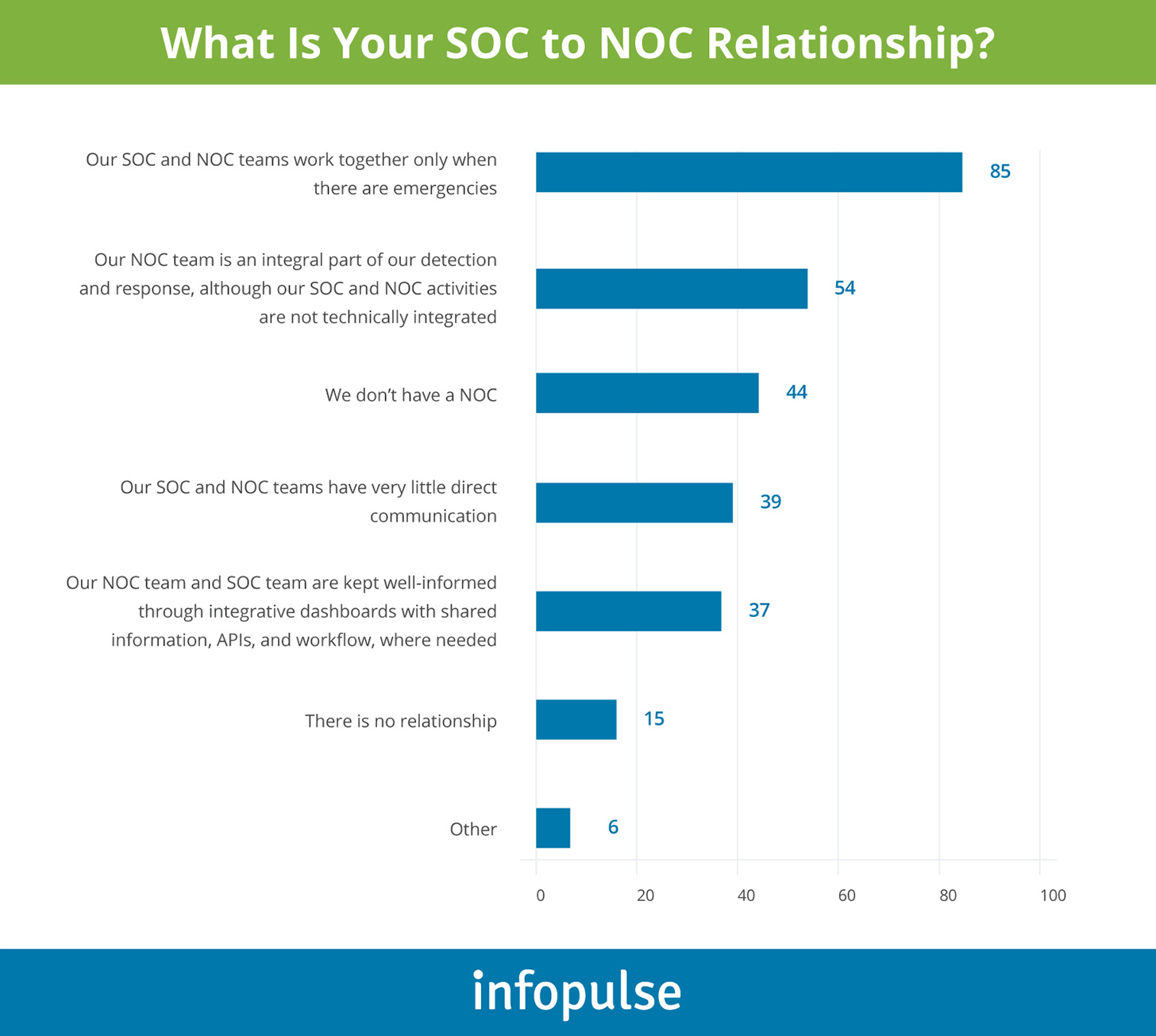
When NOC and SOC teams operate in silos, they resemble the folk from the “Blind Men and an Elephant” parable. Instead of seeing the issue holistically, each team only interacts with one of its presentations. Data from a SANS Institute Survey further reflects this sentiment:
The Benefits of SOC/NOC Integration
Though only 19% of organizations have strong NOC/SOC convergence in 2021, it is a worthwhile operational goal to aspire to.
The benefits of integrating SOC and NOC include:
- Better visibility, resulting in faster, more accurate issue identification and detection. By integrating security telematics with networking data, the two teams can become more efficient in issue triage, escalation, and resolution.
- Reduced talent gaps. Lack of skilled staff is the core barrier to effective SOC utilization, followed by “lack of automation and orchestration”. Establishing a shared Level 1 NSOC response could help you minimize the gaps in capacity. While tech alignment and progressive automation can make smaller units more efficient.
- Faster response time. With shared tools and workflows, integrated teams can react faster to critical issues and minimize the financial impacts of an incident.
- Lower total cost of ownership (TCO). In-house SOC maintenance costs for larger organizations can go north of seven figures. Similarly, a NOC unit also requires continuous investments in people, tools, and supporting technologies. By converging the two, you can trim your technical estate costs, automate or eliminate redundant processes, and re-assign people to more value-oriented tasks.
Ultimately, integrated SOC/NOC teams drive both better security outcomes and higher network performance.
How to Approach SOC/NOC Integration
At present, SOC and NOC teams are often divided on the scope of responsibilities, means of collaboration, and avenues for intel exchanges. As IDC report suggests such disjoint efforts create a flurry of issues within teams such as:
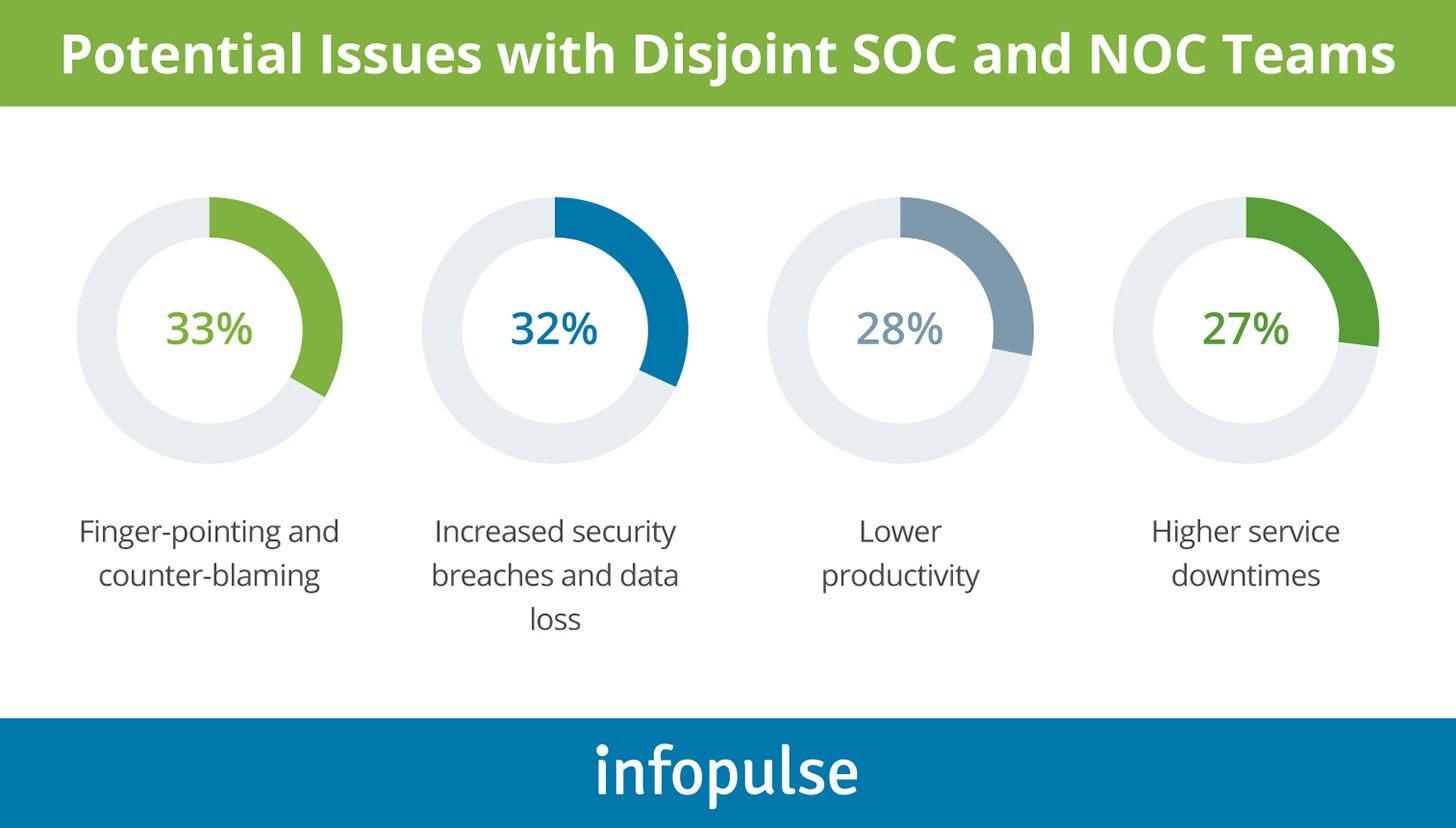
To prevent the above, SOC/NOC convergence should be orchestrated on two levels:
- Technology integration — consolidating information aggregation. Then enabling distribution across integrated dashboards and tools for issue resolution, as well as adding integrated ticketing.
- Operational integration — establishing common practices for a first-level response, improving issue cross-correlation, adding more collaborative workflows and joint standard operating procedures.
To deliver on the above objectives, telecom leaders should address the following barriers.
1. Contain the Diversity of Toolkits
Over 64% of enterprises rely on 4 to 10 tools to monitor and troubleshoot their networks. Separately, 40% of companies use 10-25 security tools, and 30% have cybersecurity toolkits with up to 50 items.
Clearly, the costs of maintaining such diverse portfolios are significant. What many leaders do not realize is that some of these tools may have overlapping functionality. Trimming that thicket could result in lower TCO without any losses in visibility or security coverage.
Therefore, we always recommend conducting a tool inventory first and mapping every tool to a specific business need (or system). For telecoms, this task may be a challenging one for several reasons.
First, off-the-shelf monitoring and troubleshooting solutions are often domain-specific (e.g., supporting only voice or SMS analysis). On the other hand, some vendors offer comprehensive solutions, covering the full spectrum of telecom network and cybersecurity needs (often through value-added services). Replacing several “mono” solutions with a more comprehensive option can drive a substantial reduction in total cost of ownership.
Another option is “right-sizing” a proprietary platform or open-source tool through customization. For example, Splunk software platform comes with pre-installed tools for implementing over 50 telecom-specific features. You can use it as a base for further customization.
The biggest challenge at this stage, however, is mapping how different monitoring and networking systems should work together to provide NOC/SOC teams with the data they need.
2. Balance IT versus Security
Due to the lack of collaboration and clarity in ownership, security and network operations, teams often engage in a “tug of war”. This results in weaker security, higher downtime, and even preventable exposure to incidents.
Why does this happen? Often NOC and SOC teams lack a fundamental understanding of each other’s roles, further magnified by conflicting objectives set by the management. When there are no shared operational procedures, task prioritization, and coordination between ITOps and SecOps, both domains suffer.
That is why you should clearly map the areas of joint and separate responsibilities. Then strengthen these through policies on triage, escalation, and coordination.
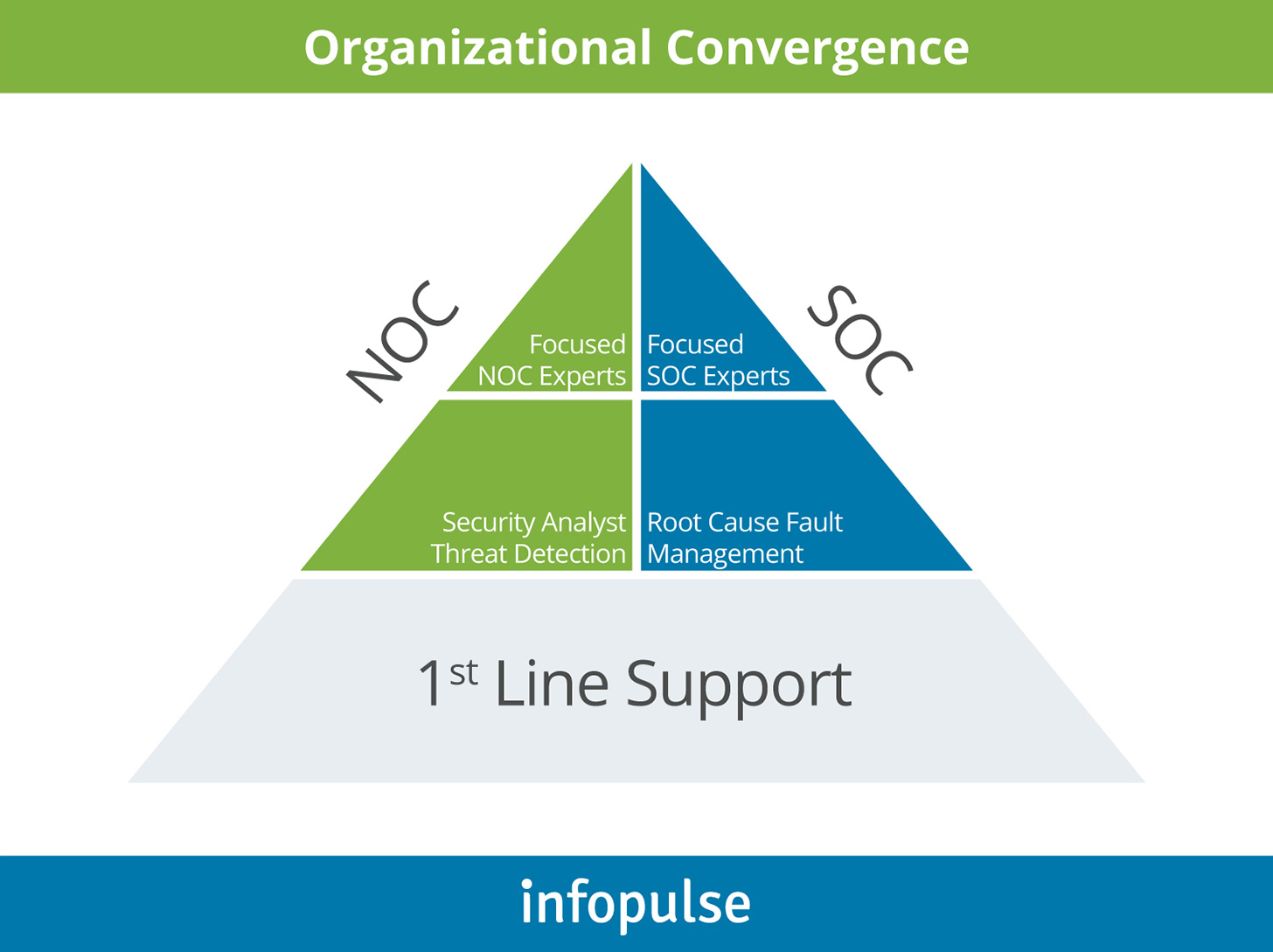
Organizational Convergence
Generally, Level 1 NOC and SOC analysts will have the largest overlap in duties as both are responsible for 24/7 monitoring, alerts/incidents triage, and escalation.
At Level 2, each teams’ expertise becomes more prolific. SOC focuses more on security analysis and threat detection, whereas NOC specialists drill down to the root cause of the performance issues and perform fault management. Yet, proactive information exchanges should also take place to ensure rapid rerouting and a joint response to critical issues.
At Level 3, convergence will be the lowest. Both NOC and SOC should retain domain subject matter experts, who can expertly address and resolve specialized network issues and security incidents.
3. Right-Size Each Team
Historically, telecoms placed greater emphasis on NOC operations. However, the rising rates and sophistication of telecom fraud, malware, and direct exploits strengthen the need to increase the size of the security unit(s).
Endpoint security, in particular, is an area where greater security coverage is needed. Why? Because up to 80% of endpoint security attacks exploit the same top 10 or 20 patchable vulnerabilities. Yet, without proper security visibility, your Ops teams may not be up-to-speed on when the update should be released or conflicted to execute it. Since operations are more concerned with preventing operational disruptions and network downtime, the teams may delay patching.
In fact, 81% of teams admit deferring critical updates with 56% saying that they were unaware of the security consequences of such a decision. Those consequences can be dire as practice shows: the 2017 Equifax data breach was eventually traced to a vulnerability for which a patch was available.
Such cybersecurity negligence can be prevented when you have enough people with the security acumen and respective powers to continuously enforce, enhance, and update best practices for all units.
To Conclude
For long enough, SOC and NOC had unhealthy power dynamics. Reconciliation is well overdue. However, many telecom companies postpone this decision. In most cases, the reluctance stems from constrained access to security talent, as well as the technological complexity of achieving convergence.
To overcome both, many leaders opt for managed security services providers (MSSPs). The advantage here is that such teams are often experienced in a diverse stack of technologies and varied monitoring tools. Respectively, they can conduct an initial assessment, advise on the necessary scope of improvement, and provide converged NSOC operations.



![CX with Virtual Assistants in Telecom [thumbnail]](/uploads/media/280x222-how-to-improve-cx-in-telecom-with-virtual-assistants.webp)
![Power Apps Licensing Guide [thumbnail]](/uploads/media/thumbnail-280x222-power-apps-licensing-guide.webp)
![Expanding NOC into Service Monitoring [thumbnail]](/uploads/media/280x222-best-practices-of-expanding-telecom-noc.webp)
![Cloud-Native for Banking [thumbnail]](/uploads/media/cloud-native-solutions-for-banking_280x222.webp)
![Generative AI and Power BI [thumbnail]](/uploads/media/thumbnail-280x222-generative-AI-and-Power-BI-a-powerful.webp)
![Data Governance in Healthcare [thumbnail]](/uploads/media/blog-post-data-governance-in-healthcare_280x222.webp)
![Super Apps Review [thumbnail]](/uploads/media/thumbnail-280x222-introducing-Super-App-a-Better-Approach-to-All-in-One-Experience.webp)
![SAP Service Insight [thumbnail]](/uploads/media/Service Insight-Infopulse-SAP-Vendor-280x222.webp)
