A Definitive Guide to Telecom Security: SS7 Network Protocols
Regardless of what security assurances mobile network operators provide, plentiful evidence shows how vulnerable these systems may be. Currently, these networks are assailable to both active signalling attacks and to passive eavesdropping attacks.
A common misapprehension is that security offences are very complicated and expensive to perform and can be executed only by security intelligence agencies or the most sophisticated hackers. Many people consider a mobile communication network to be a system based on the most advanced technologies. However, this complex system is built on smaller subsystems that have different technological levels. The weakest link of one level may affect the security of the entire network.
For example, the process of placing voice calls in modern mobile networks is still based on SS7 (Signaling System No.7) technology. SS7 protocols date back to the 1970s when the concerns regarding signalling security were not as significant as today. At that time, safety protocols included the physical security of hosts and communication channels, making it impossible to obtain access to the SS7 network via a remote unauthorized host. Moreover, access to signalling would require much more effort and high-tech hardware.
What Made SS7 Network Vulnerable to Different Attacks
The growth of Internet technologies, in particular SIGTRAN, allowed migrating and adapting SS7 protocol layers to the IP world. This is when signalling security became a much more serious problem. The network became open to a wider audience with untrusted parties exploiting its capabilities for fraudulent activities. Security issues were also reported in Diameter, especially when the combination of SS7 and Diameter allowed getting all the information needed for the attack.
Even today, GSMA, telecom and private security companies are intensively working on viable solutions to address SS7 protocol vulnerabilities.
Fraudsters, mafia, and intelligence agencies are still undermining trust in mobile networks. Leading operator groups are securing themselves as the overall network has low security and lacks specific security measures (budget, awareness, slow deployment, etc.).
Moreover, attacks are rarely disclosed, publicized, and almost never penalized, merely giving attackers some discomfort, while they may be preparing for further attacks.
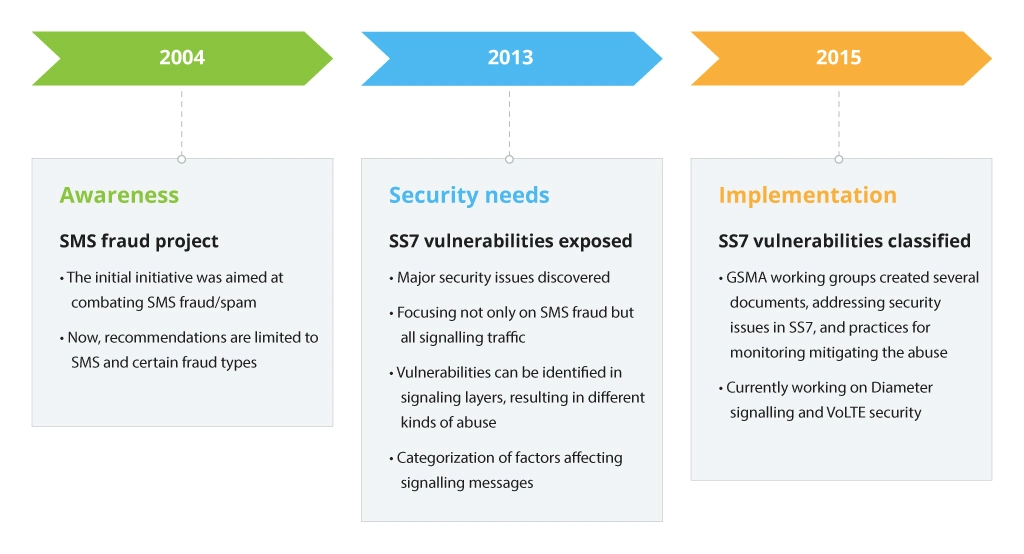
Again, security issues of the SS7 signalling network and its vulnerabilities are not a new topic – industry leaders have always been well aware of the risks. However, only in recent years, the problem has drawn more and more attention.
Now security researchers are working on proving how easy it would be for a knowledgeable attacker to commit different kinds of exploits using low-end equipment and with relatively simple means to get access to the global signalling network.
The abovementioned vulnerabilities can lead not only to revenue losses among mobile operators but also lay privacy and safety concerns among subscribers. Signalling security, focused on eliminating network protection weaknesses, should also help MNOs keep their brand reputation strong.
GSMA decided to address security concerns and multiple issues by creating dedicated groups of professionals, working on a new set of documents (FS.07, FS.11, FS.19, IR.82, etc.).
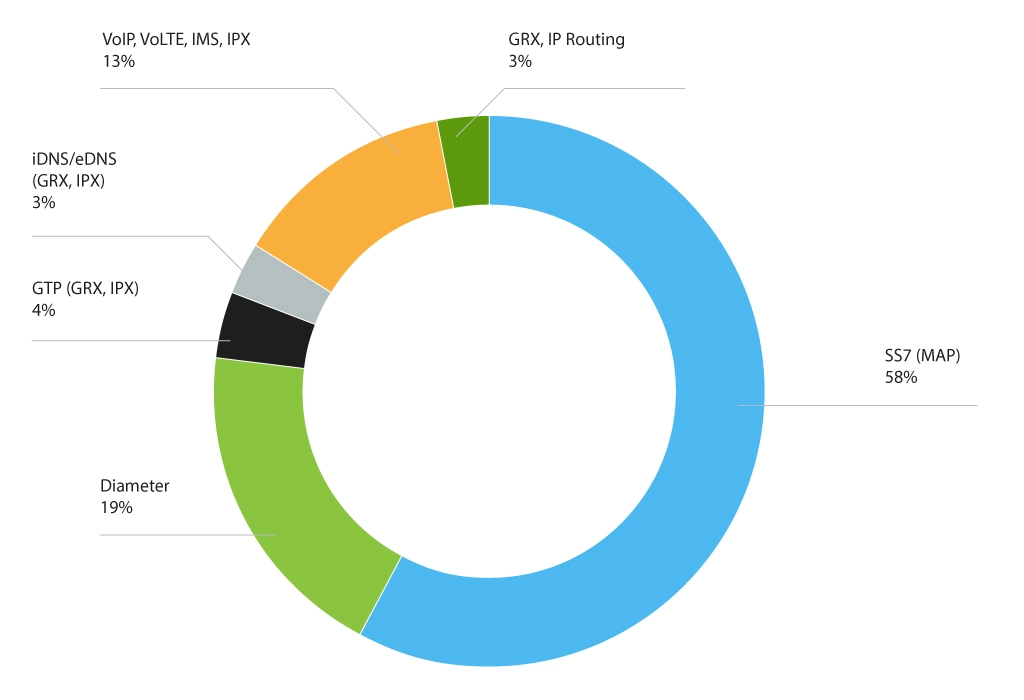
Signalling MAP Messages Categorization
When analysis and documents appeared, they further led to the introduction of signalling MAP messages categorization based on their functionality and use. Below are a few examples of such categories earlier described by GSMA.
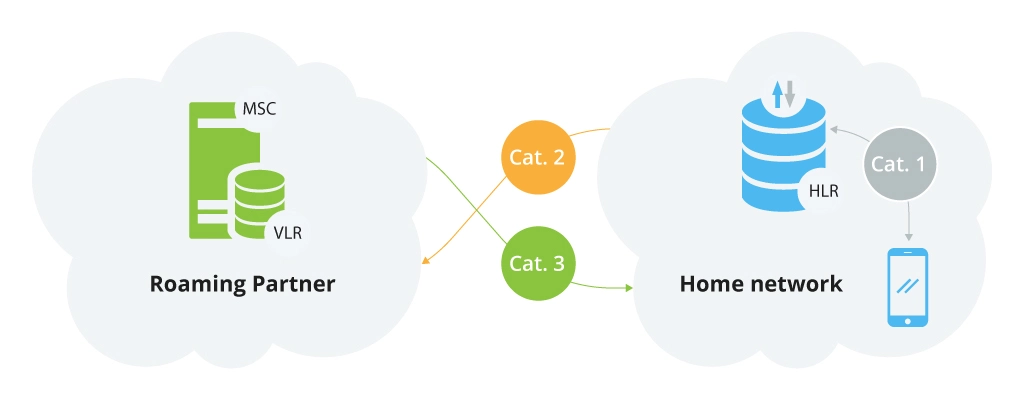
Category 1: Intra-PLMN messages
Intra-PLMN, prohibited messages that should only be received from within the same network.
These are unauthorised packets (listed in FS.11) and should not be sent between operators unless there is an explicit bilateral agreement between the operators to do so. Here are some of the packets:
- SRI (send routing information),
- SRI_GPRS (send routing information for GPRS),
- ATI (any time interrogation),
- ATM (any time modification),
- Send_USS_Req (send unstructured supplementary service request),
- Send_Identification, Send_Parameters, Send_IMSI, etc.
Category 2: Inter-PLMN messages and home network
Inter-PLMN messages must be received from the subscriber’s home network. In other words, Category 2 of MAP messages refers to those received by inbound roamers from their home network. This category embraces the following packets:
- PSI (provide subscriber info),
- PRN (provide roaming number),
- PSL (provide subscriber location),
- ISD (insert subscriber data),
- DSD (delete subscriber data),
- CL (cancel location), etc.
Category 3: Inter-PLMN messages and visited network
Inter-PLMN messages that must be received from the subscriber’s visited network. Category 3 messages are MAP packets, authorized to be delivered by interconnects between MNOs. It is regarded as suspicious/abnormal if these packets originate from a network that is not the subscriber’s last known location. As well as in Category 2, certain packets should only originate from a roaming partner of the home operator. The following packets should be monitored and analyzed:
Cat. 3.1: MAP messages with location validated by past/current VLR information:
- MO-FSM (mobile originating forward short message),
- Register_SS, Erase_SS (register or erase supplementary service),
- Activate_SS, Deactivate_SS (activate or deactivate supplementary service),
- Process_USS_Req (process unstructured supplementary service request), etc.
Cat. 3.2: MAP packets with location not validated by past/current VLR information:
- UL (update location),
- UL_GPRS (update GPRS location),
- SAI (send authentication request), etc.
Messages in Category 3.1 can be monitored by validating the past/current VLR address regarding the received packet.
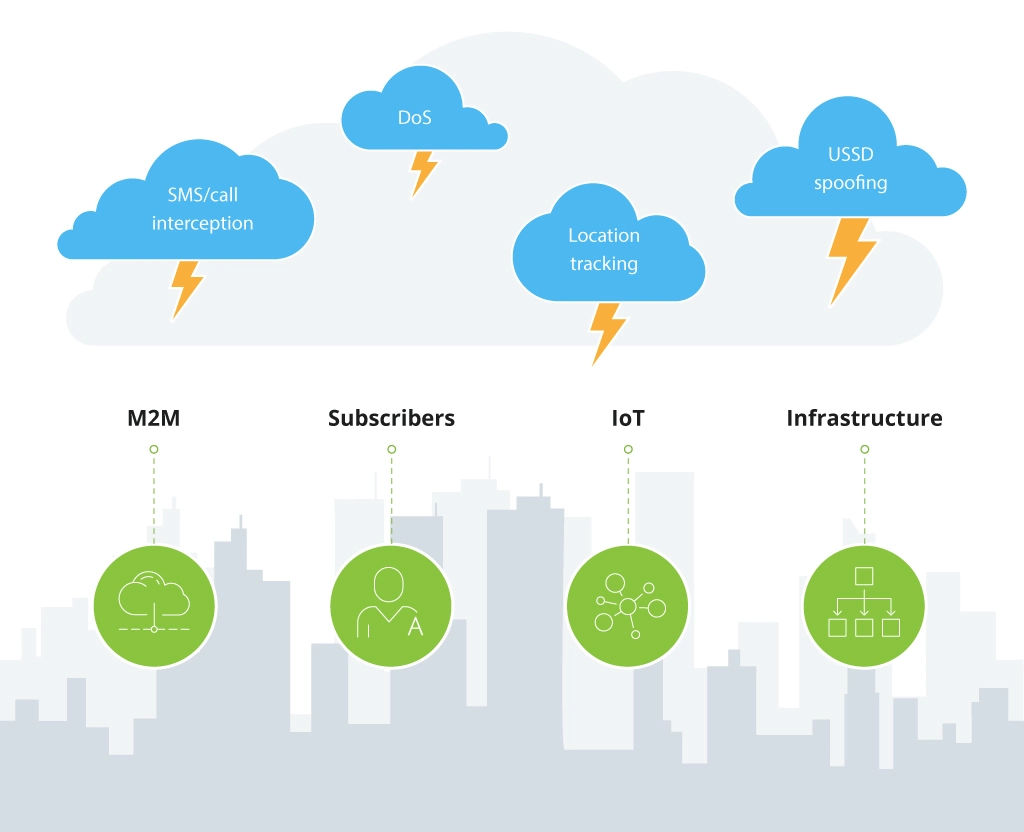
Main Types of SS7 Network Attacks
Fraudulent attacks over the signalling network can harm not only subscribers and mobile networks as a whole but also infrastructures (within one building or even the entire urban area), IoT and M2M ecosystems.
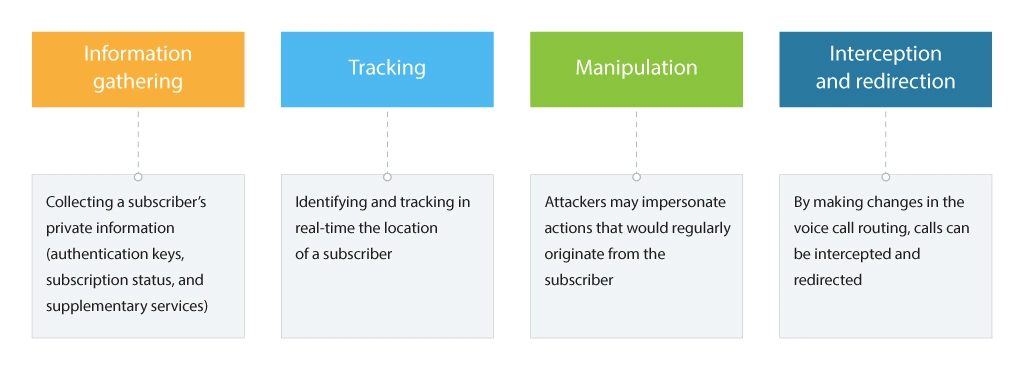
Information Gathering
This is often the primary step of the attack used to get to the subscriber information (IMSI, authentication keys, location by country/area/cell, call forwarding setup, etc.) and to identify network specifics (e.g., network topology).
Information gathering may pose less risk in terms of abuse, however, it’s the most crucial part that should be addressed in order to prevent any further service abuse. Even with the partial success of information gathering in SS7, the attacker may use this data in order to make more attacks on a subscriber’s profile through Diameter.
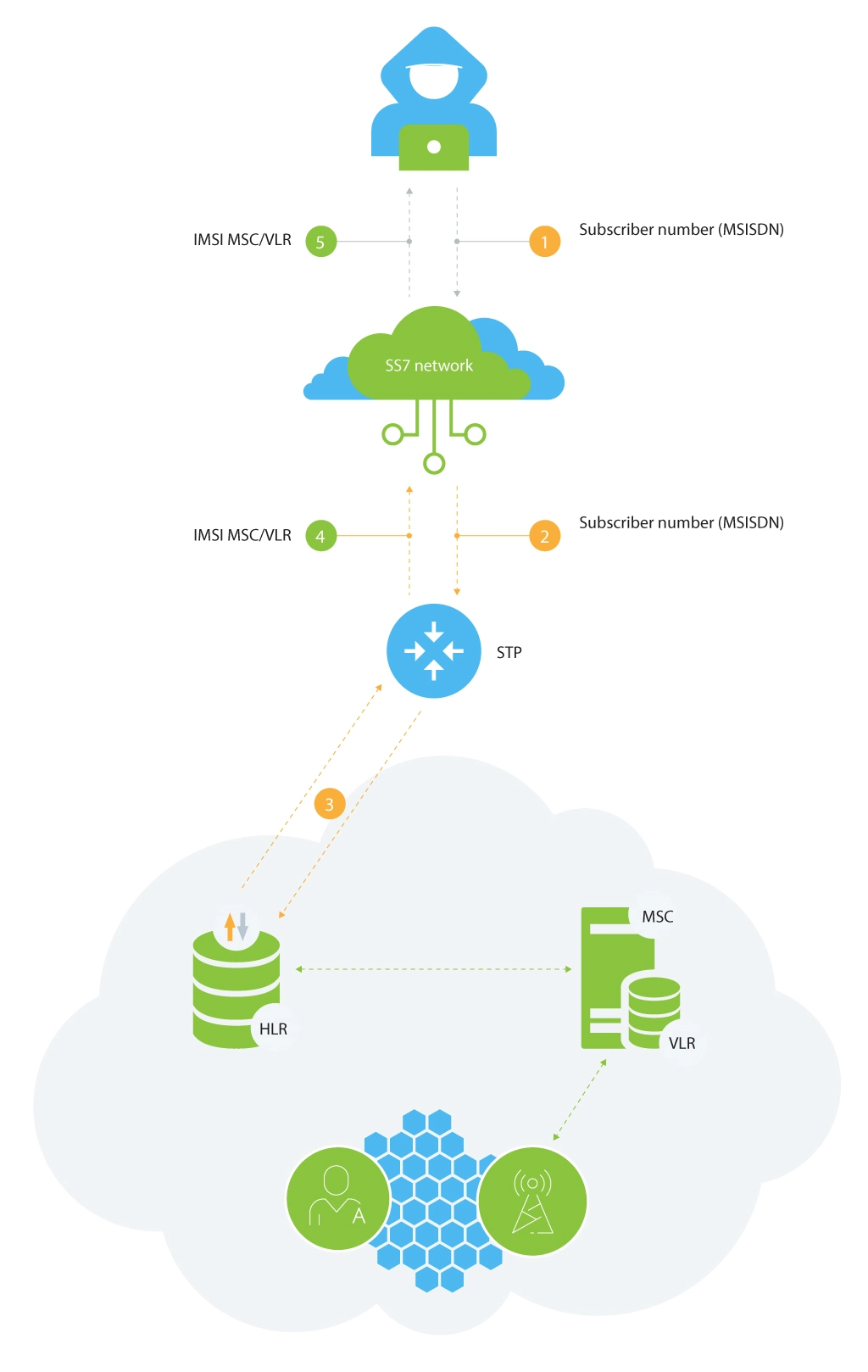
Such an attack can be executed by means of the following MAP messages:
- SendIMSI: request is sent to the subscriber’s number (usually known from the beginning), HLR responses with the subscriber’s IMSI;
- SRI: HLR replies with the subscriber’s IMSI, MSRN, and MSC (optional) and HLR (optional) addresses;
- SRI-SM (send routing information for SMS): HLR returns the subscriber’s IMSI and his MSC;
- SRI-LCS (send routing information for location services): HLR provides subscriber’s IMSI, LMSI (optional), MSC and SGSN (optional) addresses.
Location tracking
Although this type of attack is still part of the information gathering process, the focus shifts to tracking the subscriber’s current location. The attacker’s goal is to enable accurate global tracking service for mobile subscribers, ranging from a few kilometers to only hundreds of meters. While the compromised mobile network does not provide the exact location, the location area, and current cell information can be converted to the actual geo coordinates.
The location data can also be used to launch other attacks, which would compromise services or charging functionalities offered to subscribers. For this purpose, the following MAP packets are used:
- ATI (any time interrogation): this packet is sent to the subscriber’s HLR. In return, HLR provides the subscriber’s MSC/VLR address, LAC (location area code), CI (cell id), IMEI (optional), subscriber’s status (active, offline etc.), etc.
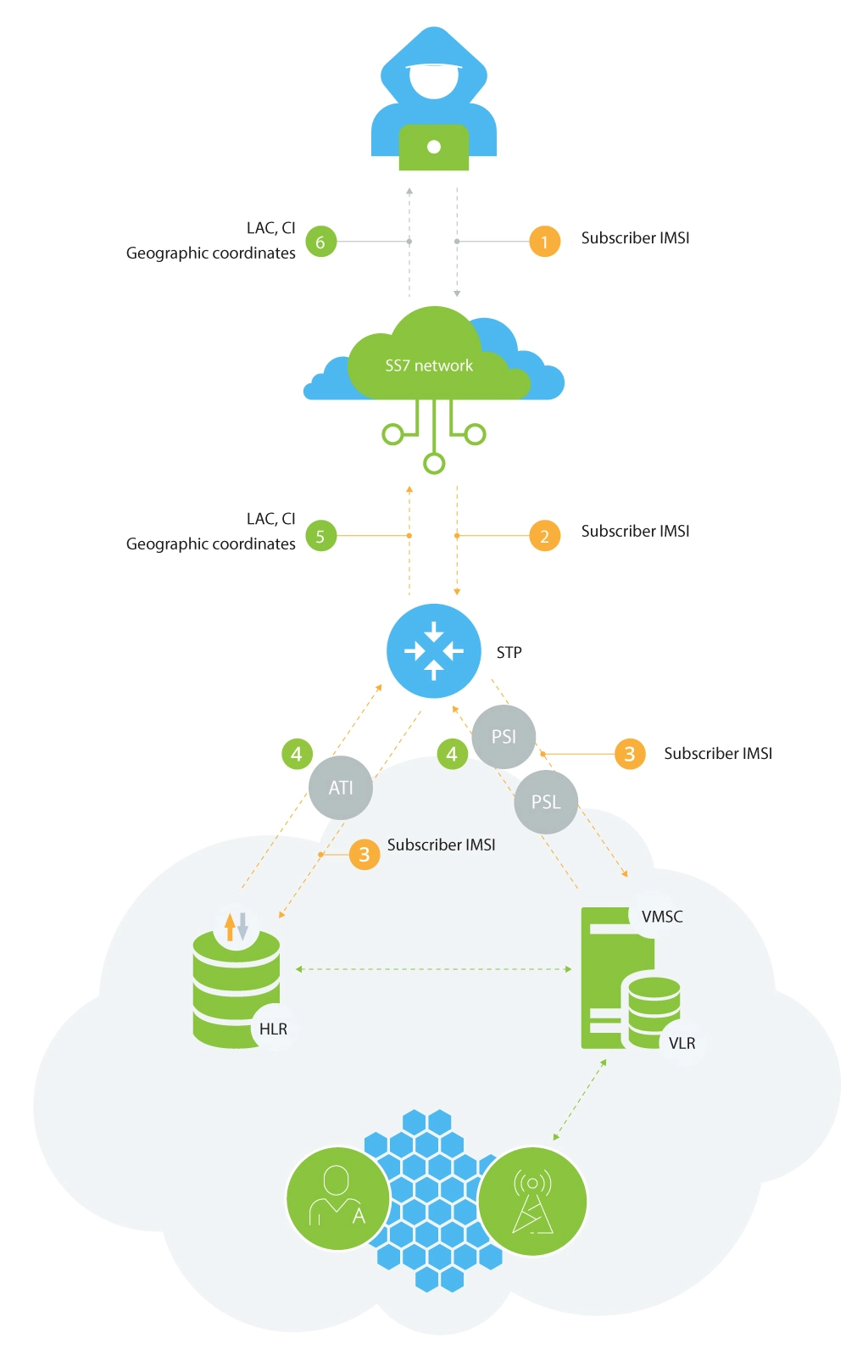
- PSI (provide subscriber info): the request is sent to the subscriber’s visited MSC (IMSI and MSC address should be known after the first phase – successful SRI, SRI for SM or SRI for LCS). MSC responds providing the subscriber’s LAC, Cell ID, IMEI (optional), status (active, offline, etc.) and the information about how relevant location data is (in minutes).
- PSL (provide subscriber location): the request is sent to the visited MSC, which opens access to the subscriber’s geographical coordinates.
Manipulation
Targeting at a specific subscriber, manipulation is aimed at modifying the profile of a subscriber in the current serving network VLR. In many cases, these attacks compromise charging facilities and at the same time, activate or deactivate additional subscriber services, which is typical only for the home network.
Quite often, networks do not detect such modifications. The reason is that, in most cases, access to the network is unlimited, which allows attackers to collect information and then change the subscriber data.
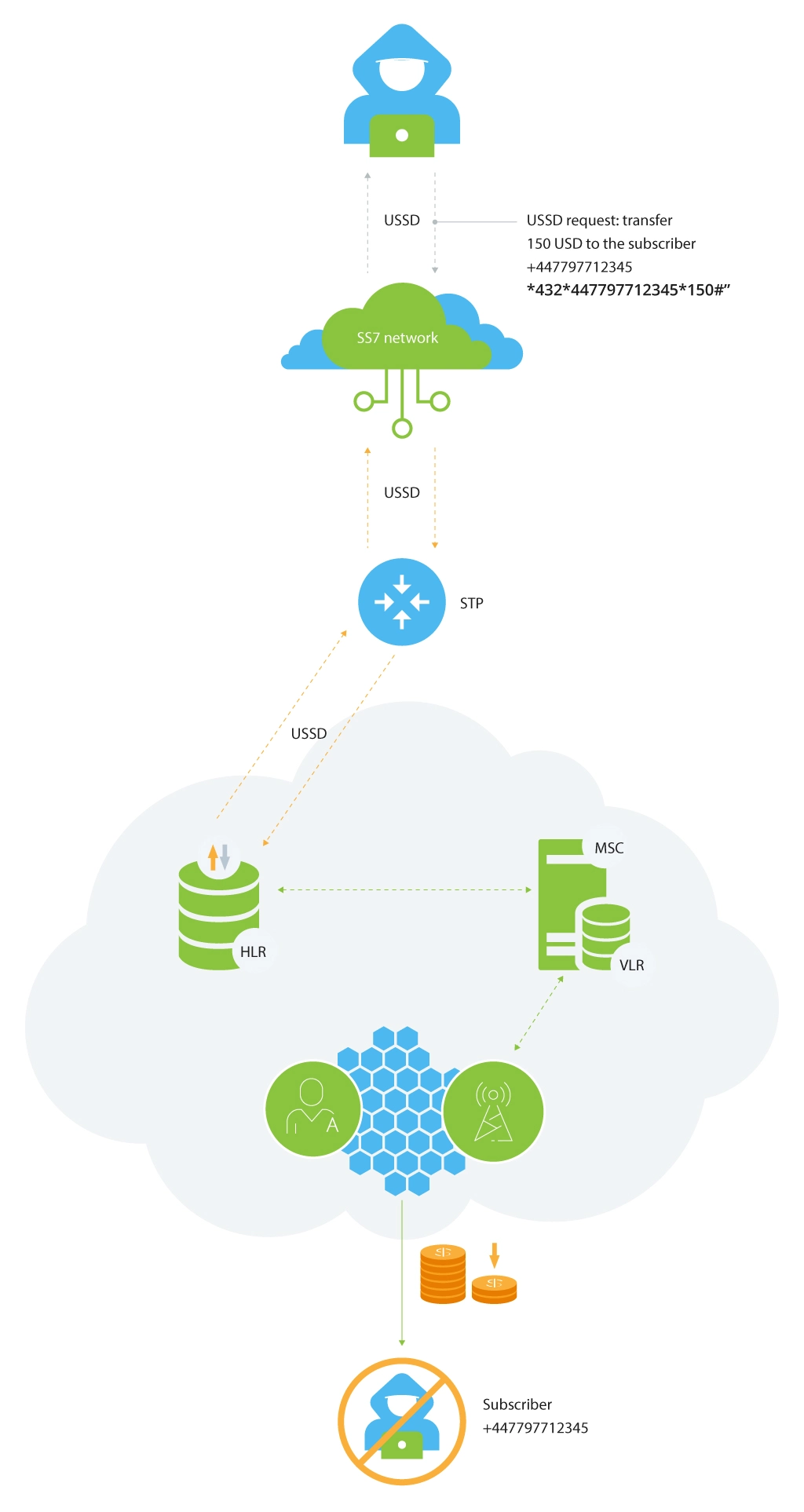
This attack means to send USSD requests straight to HLR under the guise of the victim. It’s also a good example of using a legitimate message with a USSD request sent from VLR to HLR. The initial data to compromise is a subscriber number, HLR address, and USSD string.
The worst scenario of this attack is when a request is sent to transfer money between the subscribers’ accounts.
This fraud attack may be performed by using Process-Unstructured-SS-Request packet leveraging the following data:
- Subscriber’s phone number, MSISDN (usually known from the beginning);
- HLR address (can be obtained as outlined in the information gathering section);
- USSD request structure (usually described on the service provider’s website with an open access).
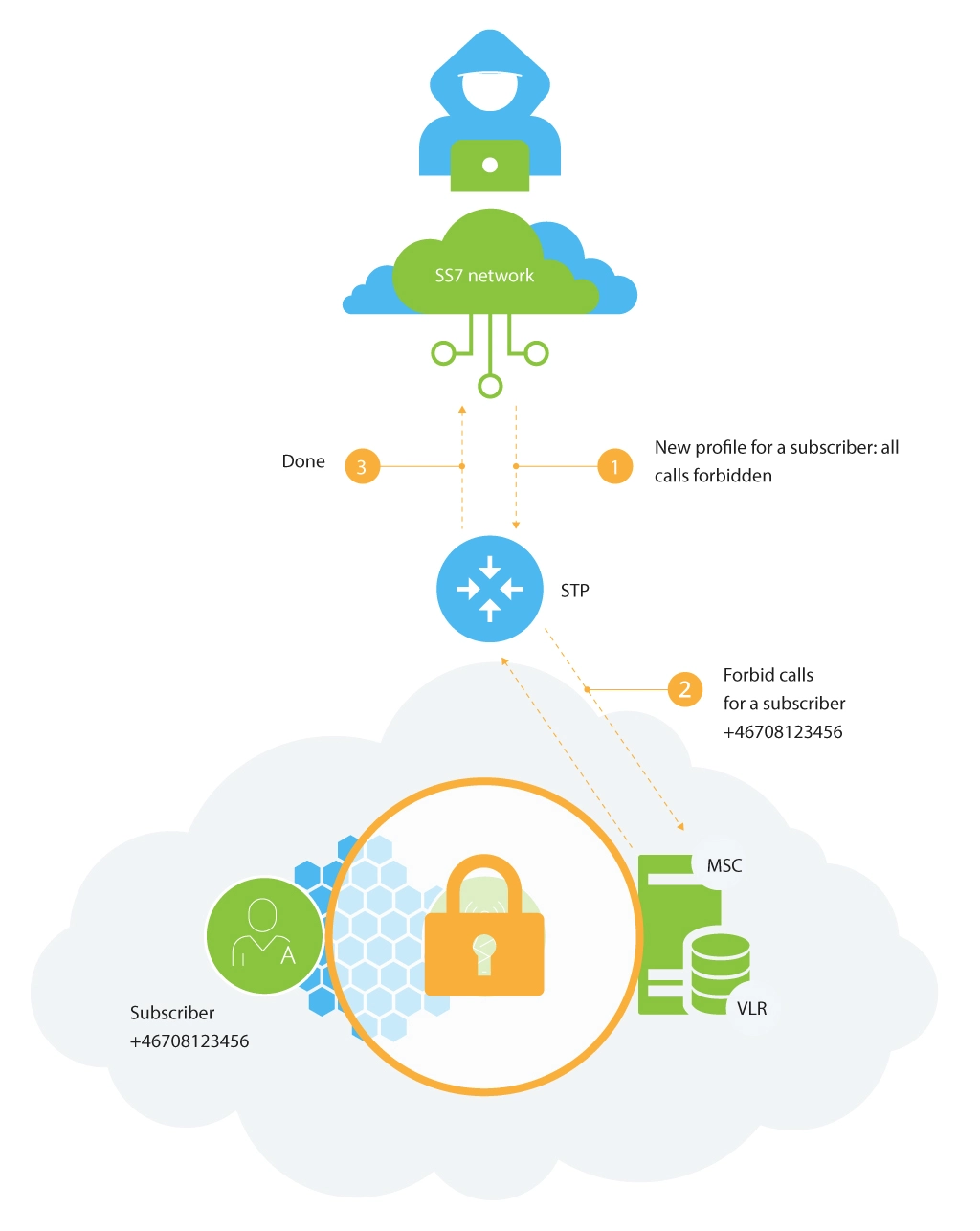
The goal of the attack is to spoof the network with fake subscriber profile data. When a subscriber registers on the network (MSC), his/her profile is copied from the HLR database to the VLR database. The profile contains information about active and inactive subscriber services, call forwarding parameters, the on-line billing platform address, etc. The attacker can send a fake subscriber profile to the VLR by enforcing a simple ISD (insert subscriber data) packet.
Traffic redirection/interception
With the information about a subscriber, attackers can send additional traffic using the compromised data and alter profile or routing parameters of the subscriber in order to intercept/redirect the traffic. Usually, these attacks are not very widespread but pose a high risk, since the identity of the subscriber is easily jeopardized. Moreover, it may result in major telecom and non-telecom abuse. Attackers may impersonate the subscriber and commit other fraudulent activities, promoting other types of security and financial fraud.
One of the common examples is the abuse of a roaming procedure. To perform the attack, records, and activities (voice calls, SMS, etc.) of a subscriber are forwarded to the fake network. With enough sophistication, these fake networks behave like regular ones when communicating with other signalling parties. More than that, without the detailed analysis of the traffic, it’s next to impossible to detect the attack.
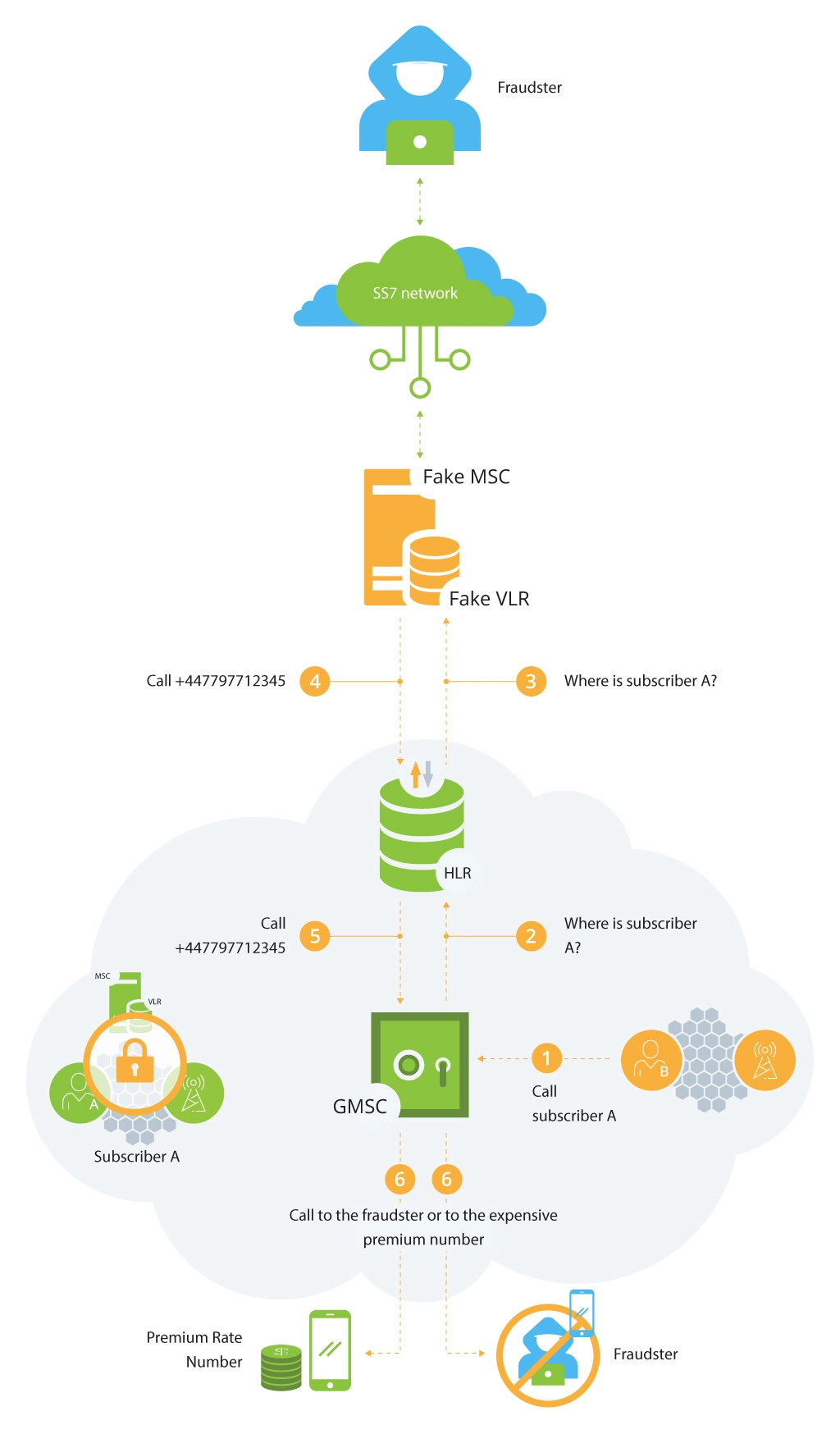
The attack can be achieved by redirecting the incoming call. The goal is to change the voice call routing and to redirect all incoming calls. When a call is terminated, the gateway MSC (GMSC) sends a request to the HLR to identify the MSC/VLR that currently serves the subscriber. This data serves for routing the call to the appropriate switch.
If the fraudster managed to register the subscriber (by using MAP message Location Update) in a fake MSC/VLR, the HLR will redirect the received request to this MSC/VLR, which in turn will send the Mobile Station Roaming Number (MSRN) to redirect the call. The HLR transfers this number to the GMSC, which redirects the call to the provided MSRN.
As a result, the attacker is able to redirect the incoming call to another number (in our particular case, to the number 447797712345 as described in the picture below).
This attack can cost you more if such calls are redirected to some expensive premium international numbers.
What Measures Should Be Applied
Stealing money, determining the subscriber location, tapping calls, and disrupting communication services are the results of exploited SS7 vulnerabilities. Such threats MNOs and their clients should still mitigate these days. With the Internet connection, mobile communication has become a preferred attack point for hackers looking to penetrate critical infrastructures of enterprises.
If mobile operators do not implement protection systems against SS7-based attacks, in the nearest future, the victims of such attacks will be not only public and private organizations but also entire nations.
To protect their SS7 networks, MNOs should apply the following measures:
- Analyze the provider’s hosts in the SS7 network;
- Control message filtering;
- Monitor the SS7 traffic;
- Examine the potential for attacks and fraud;
- Determine equipment configuration errors and vulnerabilities in protocols.
Final Point
This article is one of the series of posts on telecom security and we tried to shed light on the most common types of attacks, as well as measures mobile network operators should utilize to address multiple vulnerabilities and protect their network.
Infopulse can help you deal with SS7 issues with professional assistance of our telecom experts, who can help you strengthen your network by applying cutting-edge security practices and measures. Contact us today!


![Expanding NOC into Service Monitoring [thumbnail]](/uploads/media/280x222-best-practices-of-expanding-telecom-noc.webp)
![Cloud-Native for Banking [thumbnail]](/uploads/media/cloud-native-solutions-for-banking_280x222.webp)
![Generative AI and Power BI [thumbnail]](/uploads/media/thumbnail-280x222-generative-AI-and-Power-BI-a-powerful.webp)
![Data Governance in Healthcare [thumbnail]](/uploads/media/blog-post-data-governance-in-healthcare_280x222.webp)
![Super Apps Review [thumbnail]](/uploads/media/thumbnail-280x222-introducing-Super-App-a-Better-Approach-to-All-in-One-Experience.webp)
![SAP Service Insight [thumbnail]](/uploads/media/Service Insight-Infopulse-SAP-Vendor-280x222.webp)

![5G Network Holes [Thumbnail]](/uploads/media/280x222-how-to-detect-and-predict-5g-network-coverage-holes.webp)
![Carbon Management Challenges and Solutions [thumbnail]](/uploads/media/thumbnail-280x222-carbon-management-3-challenges-and-solutions-to-prepare-for-a-sustainable-future.webp)
![Automated Machine Data Collection for Manufacturing [Thumbnail]](/uploads/media/thumbnail-280x222-how-to-set-up-automated-machine-data-collection-for-manufacturing.webp)