Caller Line Identification Spoofing & Robocall: 4 Mitigation Solutions
In 2023, imposter scams, often delivered via phone calls, accounted for a staggering $2.7 billion in losses, with a median loss of $1,480 per victim. Voice fraud scams often exploit Caller ID spoofing to appear legitimate, where callers impersonate trusted entities like banks, government agencies, or even family members.
The Ripple Effect: How Robocalls Burden Everyone
The epidemic of robocalls isn't just a consumer issue; it's a symptom of a wider cyber threat landscape that burdens telecom providers as well due to:
- Network Strain: Robocalls flood networks with automated calls, tying up resources and leading to congestion and decreased call quality for everyone.
- Cost Burden: Filtering robocalls, investigating complaints, and dealing with accidentally blocked legitimate calls all incur significant costs for telecom companies.
- Compliance Challenges: Regulatory bodies are enforcing stricter caller ID authentication protocols like STIR/SHAKEN to combat spoofing. Telecom providers must invest in technology and infrastructure to comply.
Fortunately, proactive measures can be taken to mitigate the robocall threat. However, to effectively mitigate this vulnerability, we must first understand the deceptive tactics employed by scammers. Let’s take a closer look at how they manipulate phone systems and exploit trust to commit fraud.
Understanding the Deceptive Tactics: Caller ID Spoofing and Robocalls
Caller ID spoofing is a technique where fraudsters manipulate the displayed phone number on a recipient's Caller ID. This deception allows them to impersonate trusted entities, such as banks, government agencies, or even a competitor's company number.
Originally intended for reminders or alerts, robocalls with pre-recorded messages are now increasingly used for spam, telemarketing, and scams. Their low cost and ease of mass distribution make them attractive for malicious actors. Robocalls often use spoofing to bypass spam filters and impersonate legitimate institutions, further escalating the risk.
How Spoofing Works
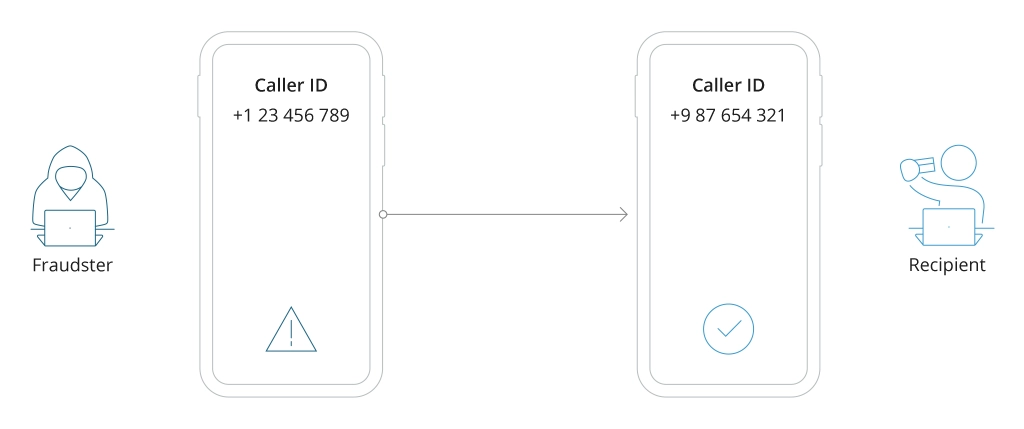
The problem is escalating further. The TNSI 2024 Robocall Investigation Report highlights the growing use of Generative AI to create realistic voice (and text) cloning scams, blurring the lines between legitimate calls and fraudulent attempts even more. Altogether, these techniques arm malicious actors with effective tools to commit fraud via phone calls.
Real-World Examples of Robocall Scams
- Impersonation Fraud. The scammers use spoofed numbers mimicking the bank's customer service line. They call bank consumers, claiming suspicious activity on their accounts. Panicked victims, believing it's their bank, reveal personal information and login credentials. News reports are full of stories of people losing thousands of dollars to these sophisticated call spoofing scams. This vulnerability highlights the importance of strong identity management practices. By implementing multi-factor authentication and avoiding sharing personal information over the phone, consumers can significantly reduce the risk of falling victim to these scams.
- Inter-carrier Wholesale Fraud or Call Stretching. This scam exploits a weakness in call routing. Call stretching scams involve hijacking international calls and keeping one party unknowingly connected to fake audio, inflating call duration on their phone bill for the scammer's financial gain. This hurts both consumers and legitimate telecom companies.
- Spam Operations. The call utilizes spoofing to bypass spam filters. Fraudsters mask their robocall numbers as local phone numbers, tricking recipients into answering calls that promote fake products or services. Not only does tactic flood the network with unwanted traffic, frustrating customers, but it can also be a deceptive attempt on the scammer’s part to sell low-quality goods or services.
Robocalls have become a significant challenge in the telecommunications industry. They are often used for legitimate purposes, such as public announcements and customer services, and robocall frauds undermine their value. The need for effective robocall mitigation solutions is critical to protect consumers and maintain trust in telecommunications systems.
Robocall Mitigation Solutions
Caller ID Authentication
The fight against robocalls has a new powerful tool: STIR/SHAKEN (Secure Telephony Identity Revisited/Signature-based Handling of Asserted information using toKENs). This suite of protocols disrupts robocall operations that rely on spoofed caller IDs by verifying the legitimacy of calls traveling over internet protocol (IP) networks.
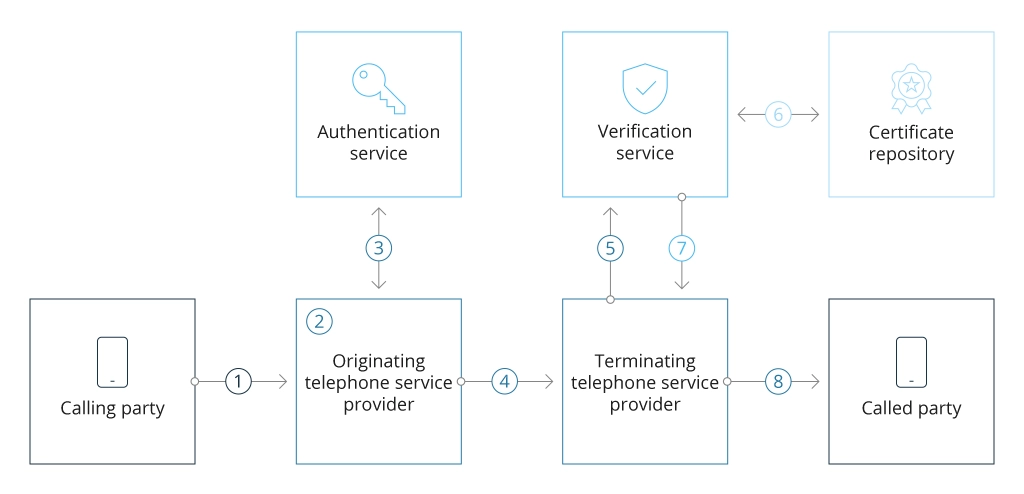
How STIR/SHAKEN works:
- Call Initiation: A call begins with a SIP INVITE message.
- Origin Validation: The caller's service provider checks the call source and number.
- Token Creation: An authentication service generates a unique token containing call details. This token is a signed JWT (JSON Web Token).
- Secure Transit: The token travels with the call through the network, its signature protecting it from tampering.
- Token Extraction: The recipient's service provider retrieves the token from the incoming call.
- Public Key Validation: The recipient's provider verifies the token using the caller's service provider's public key (retrieved from a central repository).
- Tamper Check: This verification ensures the call hasn't been tampered with.
- Call Presentation: If successful, the call is presented to the recipient with a verified caller ID status.
STIR/SHAKEN verifies calls in 3 levels:
- Level A (Full): Highest trust - Carrier confirms caller's identity and authorization for the number.
- Level B (Partial): Medium trust - Carrier verifies call origin, but not if the caller is authorized for the number.
- Level C (Gateway): Lowest trust - Carrier only verifies the call entered their network, not the source.
STIR/SHAKEN holds huge promise for combating robocalls. This protocol allows phone companies to authenticate caller identities, making it much harder for scammers to spoof legitimate phone numbers. Regulations like those mandated by the Federal Communications Commission (FCC) in the United States are pushing for its global adoption to ensure seamless operation across different phone networks.
However, bridging the gap between the traditional phone systems, which may not have built-in support for STIR/SHAKEN, and the newer IP-based networks, isn’t a simple task. On top of that, maintaining a secure and universally accessible repository of digital certificates for authentication presents another global challenge for the industry.
Despite these challenges, STIR/SHAKEN represents a foundational shift towards securing and authenticating caller identities in the digital age. Its widespread adoption is essential for a future free from the constant disruption of robocalls.
Real-Time Monitoring and Analysis
Telecom providers can identify and block robocalls in real-time by continuously monitoring call data and employing a multi-method approach:
- Data Collection: Every call generates data like caller ID, duration, time, and frequency.
- Real-time Analysis: This data is analyzed to identify suspicious patterns, such as high call volume from a single number or calls happening at unusual times.
- Network Behavior Analysis: Looking at how calls travel through the network can reveal red flags, like calls originating from unexpected locations or unusual call routing patterns.
Case in point: We teamed up with BICS to work on the FraudGuard platform and it has just won a Juniper Research award. This system uses a massive network of service providers to track and block scam calls, saving customers billions of dollars. Find out more about the project here.
Dynamic Blacklisting
Dynamic blacklisting acts like a continuously evolving shield, protecting your customers from unwanted robocalls. This system relies on a central database that stores phone numbers identified as originating robocalls. The database is constantly updated with information from multiple sources, such as:
- Telecom Providers: They share data on suspicious call patterns detected in their networks.
- Global Threat Intelligence: Industry-wide databases track known robocall operations and their phone numbers.
- User Reports: Consumers can report suspected robocalls, helping to identify new threats.
Customers can further personalize their protection with user control:
- User Blacklists: Add specific numbers to block unwanted callers beyond those identified by the central database.
- Whitelists: Ensure important numbers (e.g., doctor's office) are not accidentally blocked.
All in all, dynamic blacklisting is a viable tool for combating robocalls, but some considerations should be taken into account.
First, we need to effectively block robocalls while minimizing the risk of accidentally blocking legitimate calls (false positives). Second, data collection and sharing for blacklisting must comply with all relevant privacy regulations to ensure user trust. Finally, collaboration between phone companies and industry groups is essential. A comprehensive and effective database relies on this collaboration to identify a wider range of robocall threats.
AI and ML Algorithms
As you already know, the fight against robocalls relies heavily on data. AI and machine learning (ML) systems sift through a massive ocean of call details, caller behavior, and network data. This allows them to develop a keen eye for patterns indicative of robocalls.
Yet the battle lines are further blurred by the use of Generative AI technology by scammers. GenAI can be used to create synthetic voices that sound increasingly human-like, making it harder to distinguish them from real callers. However, AI-powered detection algorithms are also evolving to combat this tactic. By analyzing voice patterns, speech irregularities, and other subtle cues, these systems can identify even the most sophisticated AI-generated voices as non-human.
Types of data AI/ML algorithms analyze:
- Unusual Call Patterns: The frequency of calls, call duration, and even the time of day they arrive can all be red flags. Deviations from typical human calling behavior can signal a robocall attempt.
- Voice Analysis: Advanced AI can take things a step further. It can analyze the voice itself, differentiating between a human voice and a robotic one. This helps identify robocalls that try to mimic human speech.
- Script Recognition: AI doesn't just listen to the voice - it can also analyze the content of the call. By understanding the script, the system can identify common phrases or scams used by robocallers.
- Always on Alert: These systems work in real-time, constantly on the lookout for robocalls. This means they can stop new robocalls in their tracks before they even reach your phone.
Robocallers are clever, constantly developing new tricks. But AI can adapt too. By continuously updating algorithms, we can stay ahead of the curve. Combining AI with tools like STIR/SHAKEN creates a multi-layered defense, making it even harder for robocalls to get through.
Final Words and a Multi-Layered Approach
Robocalls leverage automation and low costs to bombard us with spam and scams. The good news is, we're not powerless. A multi-layered approach is emerging to combat this growing threat. By combining the solutions mentioned in the article, we can create a more robust defense against robocalls.


![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)



