Understanding Enterprise Security Levels: Which Is Right for Your Business?
In this blog post, we will overview the building blocks of cybersecurity systems and how they form five core enterprise security levels. Consequently, we will share the best practices on how for elevating your security level, achieving ultimate cyber resilience, and leveraging your enterprise security solutions.
Key Pillars of a Cybersecurity System: Security Controls & Layers
What Is Enterprise Security?
Enterprise security is a holistic set of cybersecurity solutions, strategies, and policies that aims to protect an organization's digital assets and sensitive data. Part of this process involves implementing robust measures to prevent, detect, and respond to cyber threats. Enterprise security ensures business continuity and customer trust by safeguarding data integrity, availability, and confidentiality.
What Are Security Controls?
Security controls are specific techniques, policies, and tools that are implemented to safeguard the organization’s infrastructure and digital assets. Any countermeasure to reduce security risks can be considered a security control – from physical access cards to data loss prevention (DLP) tools or security awareness training sessions. Security controls fall into three primary categories:
- Physical – fences, locks, surveillance cameras, access control, and intrusion detection systems.
- Administrative – policies, guidelines, incident response processes, security education, and other activities related to personnel management.
- Technical – controls aimed at protecting the organization’s hardware and software, ranging from antiviruses and firewalls to SIEM/SOAR, threat intelligence, Security Operations Center (SOC), and other advanced security solutions.
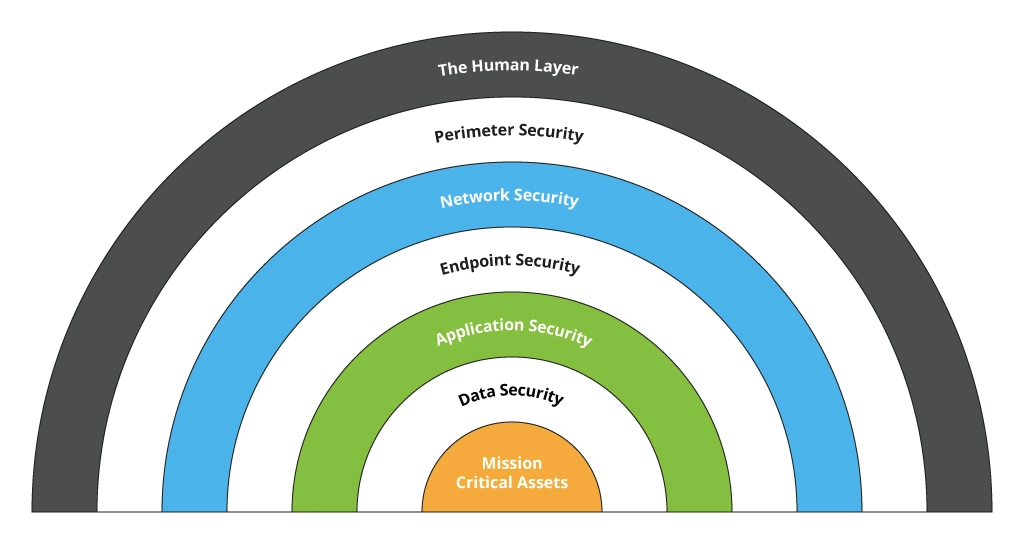
To mitigate risks and reduce the impact of cyberattacks, security controls must be applied across different layers – the major facets of an organization that can be jeopardized by different forms of cyber risks. This approach is known as “layered security” or defense-in-depth. The idea behind this approach is that when a vulnerability is exploited at one layer, the security controls on the next layers will slow and hinder the threat until its eliminated.
- Human layer – endangered by insider threats, human errors, and phishing attacks. Security controls to protect this layer typically include well-documented security policies and awareness training.
- Perimeter layer – ensures secure connectivity to the corporate network via routers and other devices. The perimeter is protected by firewalls, VPN, data encryption, and intrusion prevention tools.
- Network layer – often targeted by unauthorized access and DDoS attacks. To safeguard this layer, it’s essential to implement managed LAN/WLAN, access control solutions, next-gen firewalls, and network monitoring tools.
- Endpoint layer – all corporate devices that are targeted by malware, ransomware, and zero-day attacks. This layer is best protected with endpoint detection & response (EDR) solutions.
- Application layer – covers the security of applications and their access to the organization’s systems and data. To avoid broken authentication, injection attacks, and other threats this layer must be protected with continuous app patching, updates, access control (SSO/MFA), security monitoring, and penetration testing.
- Data layer – secures corporate data both in motion and at rest. The protection of this layer requires robust security controls across the application, endpoint, and network layers, as well as the implementation of data loss prevention tools, data classification, travel and sharing control, and data encryptions.
- Mission-critical assets – the final layer that is the primary target for the threat actors, as it stores the most valuable digital assets, such as user credentials, personal data, financial records, etc. In addition to counteractions from previous layers, mission-critical assets can be protected with coordinated incident response, data backup, and disaster recovery.
By analyzing what types of security controls are applied across each of the seven layers, you can identify the company’s level of security, which is the overall rate of your security maturity. The formula for achieving a higher level of security is simple – the more advanced security controls you apply across each layer, the higher the security level you will gain. Although the risk scenarios and attack vectors depend on the organization’s size, industry, services, and IT ecosystem, it’s imperative to determine and establish the minimum required level of security to minimize risks and sustain cyber resilience.
What Are the Levels of Enterprise Security?
Our experts have outlined five core security levels that are based on the National Institute of Standards and Technology (NIST) Cybersecurity Framework – a globally-recognized set of security standards and guidelines, as well as the Payment Card Industry Data Security Standard (PCI DSS) and cybersecurity policies and best practices from Microsoft. Each level is viewed from three perspectives – people, processes, and technology. Applying security controls across these three equally important domains is essential to safeguard any business from ever-evolving cyber threats.
Levels of Enterprise Security
Domains
People
Process
Technology
Entry Level
1. No dedicated security personnel
2. Lack of security awareness
1. All security activities occur ad-hoc
2. No strategic or mid-term security management plans
1. Absence of centralized security management
2. Lack of security visibility
Basic Level
1. Part-time or shared security personnel
2. Basic security education for non-IT personnel
1. Clear communications flow between the IT and security teams
2. Various security processes defined and documented
1. Security solutions not fine-tuned
2. Several infrastructure components are managed centrally
Challengers Level
1. Security team is not fully staffed
2. Ongoing security awareness training sessions
1. Defined security strategy
2. Corporate assets labeled and categorized
1. Centralized management of key security solutions and IT assets
2. Full security visibility over business-critical assets
Mature Level
1. Defined common security roles
2. Highly skilled and educated security teams
1. High coverage of security processes
2. Regular security assessments
1. Security risk assessment solutions and technologies implemented
2. Security solutions regularly fine-tuned with respect to the changing cyber landscape
Highly Secure Level
1. Red/Blue teaming with internal teams conducted
2. Bug-bounty program in place
1. Proactive approach to security management
2. Security best practices implemented and regularly reviewed
1. Implementation of next-gen security solutions
2. Multi-layered and multi-vendor security approach
How to Define the Minimum Required Level of Security?
Identify the Value of Your Mission-Critical Assets & Assess Risks
By evaluating the value of its data, an organization can accurately prioritize the required security controls. To illustrate the point – a small-scale е-commerce business is unlikely to be targeted by complex and costly zero-day threats, which means that aiming to reach the Highly Secure level is impractical. Yet, businesses that operate in highly-regulated industries and store large volumes of mission-critical assets and sensitive data, such as BFSI, healthcare, manufacturing, energy, and telecom, must obtain a Highly Secure, or at least a Mature security level.
After determining the value of your data, it’s also important to assess the associated business risks by answering the following questions – What if your mission-critical assets are lost, leaked, and corrupted? How will data loss affect your business continuity? Is there a data backup and a disaster recovery plan?
Once you have a clear picture of your assets and the related risks, it’s easier to predict the possible attack vectors and strengthen the protection across the most vulnerable security layers.
Define the Data Value/Breach Cost Correlation
One of the major cybersecurity postulates states that the cost of hacking into your company must be higher than the value of assets threat actors can receive in case of a successful breach. For example, the value of your data is $5 million, but it requires $6 million to breach your security system – in such a case, it’s pointless for cybercriminals to target your enterprise.
Unfortunately, this postulate is often ignored by companies that choose to cut down the security budget and neglect to apply security controls across multiple layers. This may have an adverse impact on one’s business, as there is a definite breach price for each asset, user, and ultimately the entire company. Depending on the attack vector, the price may range anywhere from less than $1 and up to $350,000+ or even millions of dollars. The most sophisticated full-chain persistence zero-day, zero-click attacks that subtly inflict malicious code into mobile devices cost up to $2,5 million, according to Zerodium – a world-leading bug bounty platform.
Security Breach Price per Attack Vector
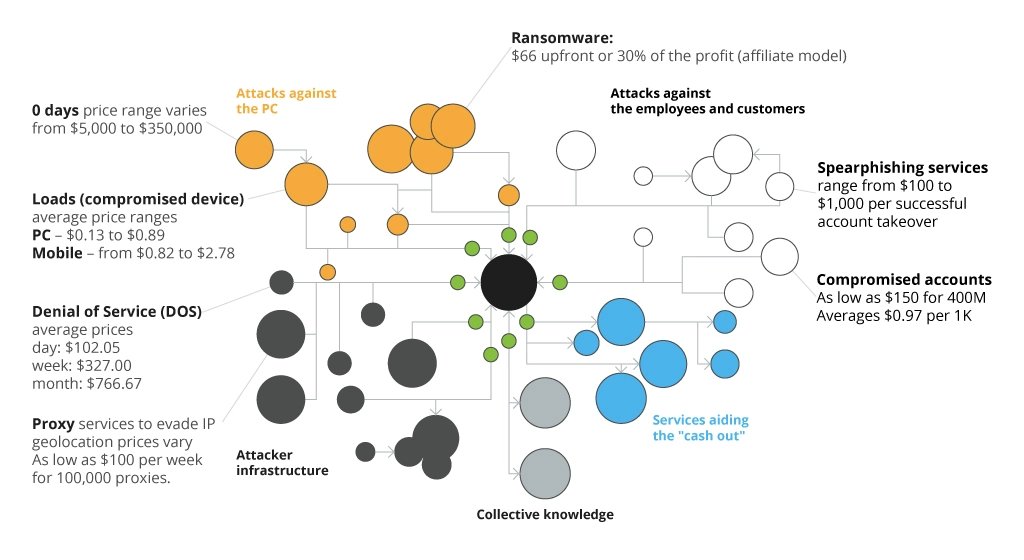
To maximize the breach costs for the attackers, you must accurately analyze the data value/breach cost correlation and invest in developing powerful security controls across all layers of your business. The best-case scenario is to build a system that can potentially be compromised only by complex zero-day threats, as they are the most expensive to execute.
Conduct a Security Assessment
The most reliable and efficient approach to defining both the current and minimum required security level is to conduct a security assessment that is intended to evaluate whether all administrative and technical security controls work correctly. By performing an end-to-end security assessment, you can gain a 360-degree view of your security posture, discover hidden vulnerabilities across your IT architecture, and identify missing security policies and processes. The insights gathered during the assessment can serve as the foundation for a security level enhancement roadmap.
Case in point: Discover how Infopulse helped Bosch Security & Safety Systems dramatically reduce business risks and optimize security costs with a holistic security audit.
Example of a Security Level Enhancement Roadmap
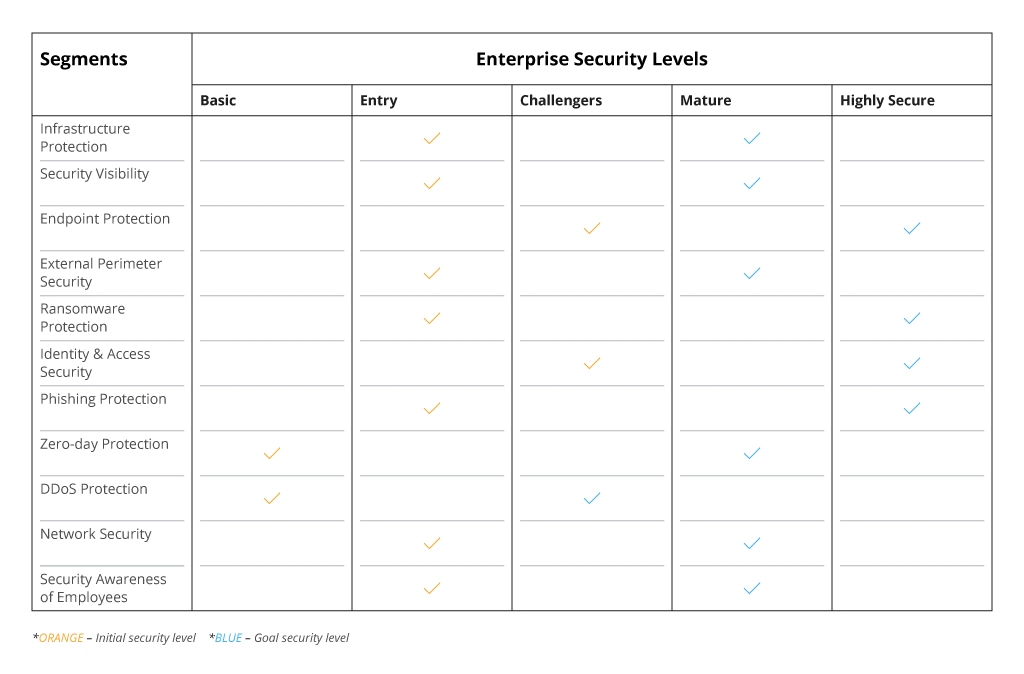
Organizations can design and implement dedicated roadmaps to elevate their security level. The best option is to build a tailored roadmap that is based on a specific business case (industry, data value, business needs, etc.), as well as the security assessment insights and custom threat modeling results. This is an optimal approach, as the required security level depends on the company’s size, services/products, business processes, and budget constraints, which makes reaching an entirely Highly Secure level across all segments rather challenging, or even unnecessary. The key goal is to move away from the Basic/Entry levels and build a blend of Challengers/Mature/Highly Secure levels that resonates with the company’s needs.
The table below demonstrates an example roadmap that Infopulse developed for a large-scale European manufacturer with presence in over 30 countries and 3,500+ employees. Yellow ticks indicate the client’s initial security level across different segments, and the green ones show the levels that we aimed to achieve.
Eventually, Infopulse helped the client switch from a primarily “Entry” level to a combination of Mature and Highly Secure levels and strengthen its security posture with a 24/7 SOC enhanced with a cloud-based SIEM/SOAR.
Security Level Enhancement Roadmap
Conclusion
The growing volume and complexity of cyberattacks pose a significant risk for SMBs and large enterprises, especially those with large volumes of mission-critical assets. If your security system is poorly protected, threat actors can detect and exploit vulnerabilities often with little to no effort and expense. By elevating your security level to a blend of Challengers/Mature you can keep the attackers at bay and avoid disastrous business risks. Moreover, by achieving a mostly or entirely Highly Secure level, you can transform your enterprise security software into a multi-layered cyber stronghold, capable of withstanding the never-ending swarm of cyberattacks, including even the most complex zero-day threats.
![Security Levels [main banner]](https://www.infopulse.com/uploads/media/banner-1920x528-levels-of-enterprise.webp)



![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)
![Security Stack [thumbnail]](/uploads/media/THUMBN~1.WEB)
![Security Guide for Cloud Migration [thumbnail]](/uploads/media/thumbnail-280x222-security-when-migrating-apps-to-the-cloud.webp)
![AWS Security Hub Integrations [thumbnail]](/uploads/media/top-security-solutions-to-integrate-with-aws-security-hub-for-soc-280x222.webp)
![Building AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-enterprise-guide-to-building-your-aws-security-hub.webp)
![How to Centralize Enterprise Security System [thumbnail]](/uploads/media/thumbnail-280x222-how-to-centralize-enterprise-security-system.webp)
![SOC Adoption Scenarios [thumbnail]](/uploads/media/three-ways-to-introduce-SOC-to-your-organization-280x222.webp)
![Guide to Security Automation [thumbnail]](/uploads/media/enterprise-guide-to-security-automation-280x222.webp)


