How to Choose the Right MFA Approach for Your Company?
What Is MFA?
Multi-factor authentication (MFA) is a user identity verification method that requires at least two different authentication factors, like a password and a one-time code. Passwords are a weak link in cybersecurity because 63% of people reuse them across accounts and devices. Additionally, 83% choose weak passwords like “guest” or “123456,” which hackers can easily guess or hack with a password-spraying attack. Once hackers get a user password, they can do a lot of malice. 23andMe genetic testing service had over 6.9 million user records stolen last year due to poor password practices.
MFA adds an extra layer of protection by forcing users to authenticate themselves using an extra method — a one-time password, mobile authentication app, or biometrics data. This extra step reduces the security risks of a breach if someone gains access to the user password.
How MFA Works
MFA asks users to prove their identity using one or more extra means from the following categories:
- Something you know (PIN or password)
- Something you are (Finger scan or Face ID)
- Something you have (Key fob, mobile device)
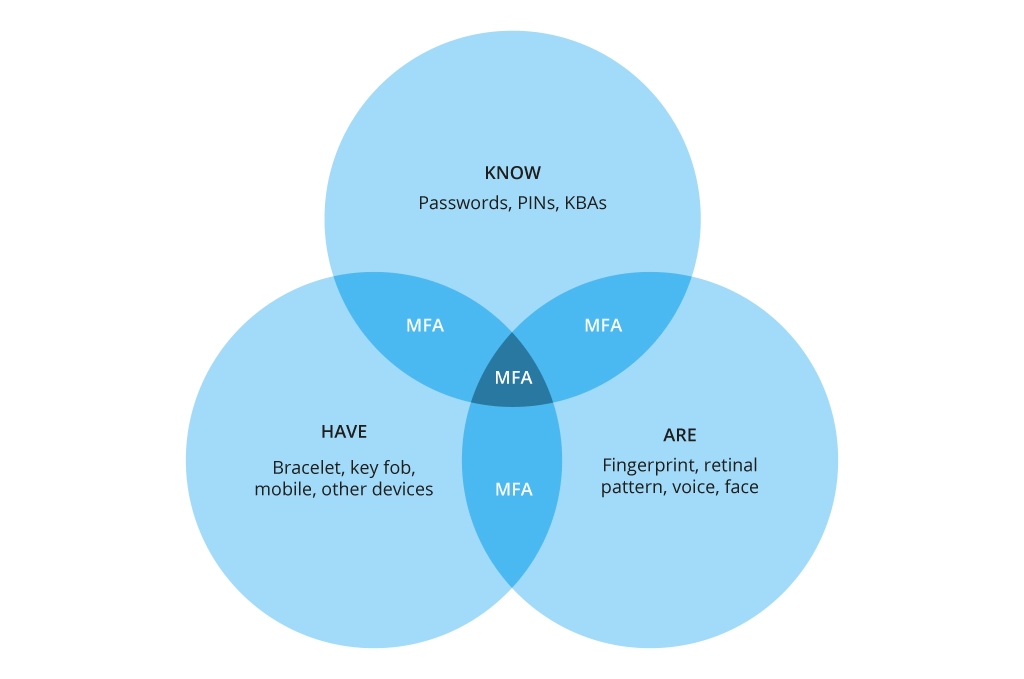
Companies may also use “location” (e.g., requiring the user to always use a VPN with a designated IP address or limiting login attempts from certain geographies) or “device type" (only allowing sign-ins from known, authorized corporate devices like laptops, corporate phones, etc.) as an extra security measure.
With MFA enabled, even if the hacker gets the user’s password, they can’t access the account without the second (and third) authentication factor, like a one-time password.
Common Types of MFA
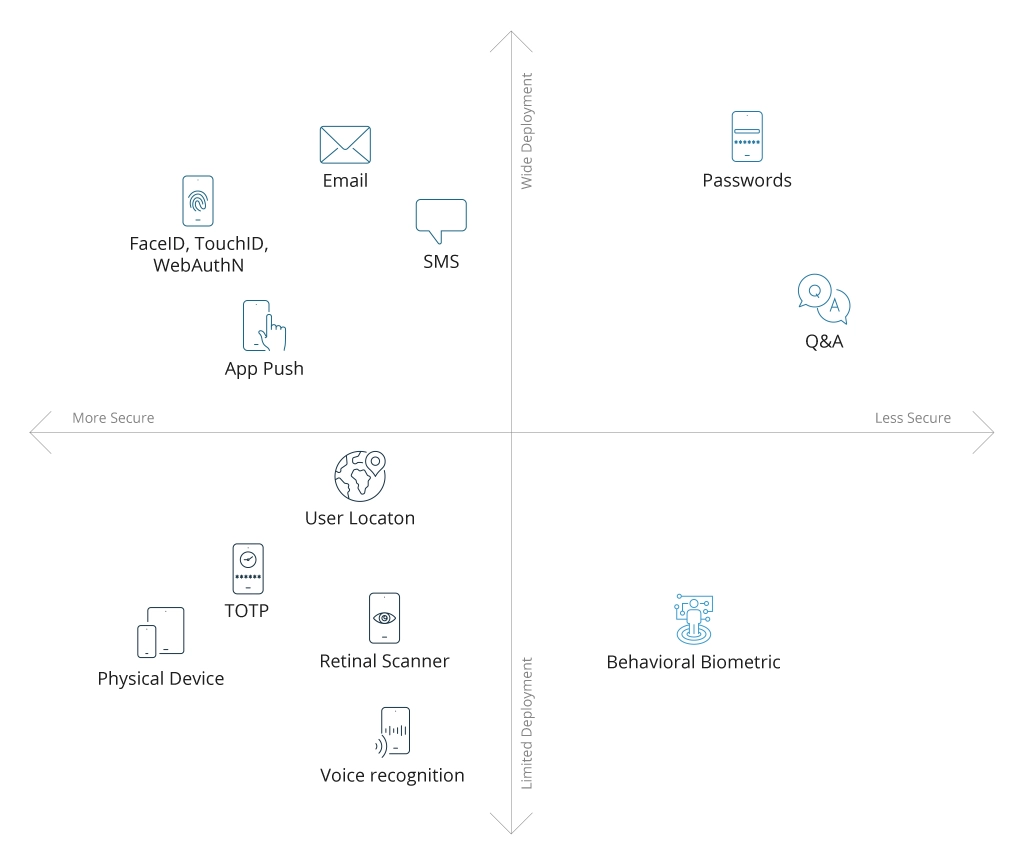
Many authentication tools and technologies are available, varying in convenience and security levels. For example, “What was your first pet name?” and a chip-based personal identity verification (PIV) card are both examples of MFA. The first is easier to implement but offers lower protection (hackers can still brute force it). The second option is more fool-proof but also more expensive and cumbersome.
Generally, the most used MFA types include:
- Time-based one-time password (TOTP)
- Tokens sent via SMS or email
- Security questions
- Hardware security key
- Biometric authentication
- Authenticator apps
- App push messages
- Magic links
- Social login
Common MFA Attack Vectors
As a recent memo from the CISA warns, not all MFA methods are equally secure. Text message tokens used to be popular, but all SMS transcriptions are unencrypted, making them easy for hackers to intercept. Text messages are also vulnerable to SS7 and SIM swap attacks. In-app push messages and token-based OTPs are prone to phishing.
The most common attack vectors on MFA include:
- MFA fatigue attacks aim to overwhelm users with authentication requests until they accept one by accident, granting the threat actor access to their account. These can be applied to push messages and OTP-based authentication.
- Man-in-the-middle attacks involve hackers intercepting a user request and rerouting the traffic to a malicious website, forcing users to input their MFA credentials and thus disclosing them. Hackers can also stage attacks that target the access tokens generated when users connect to an app.
- Token theft attacks compromise and replay stolen user-issued tokens to breach the corporate perimeter.
- Infrastructure vulnerabilities. Hackers may probe the corporate perimeter for outdated applications without modern authentication mechanisms and use these as an entry point.
Generally, authenticator apps are a top MFA method, offering high security without needing extra connectivity like in-app push messages. The best solutions use the FIDO/WebAuth authentication protocol, which is phishing-resistant. A unique, one-time authentication token is generated on the user's device (e.g., phone, laptop) or external hardware (e.g., a knob) connected via USB or NFC.
WebAuthn is already supported in major browsers, operating systems, and smartphones, and many vendors support FIDO2-compliant tokens, including Microsoft Entra, Okta, and Google Cloud, among others.
How to Choose the Most Appropriate MFA Methods
Your choice of MFA methods depends on four main factors: risk radar, IT infrastructure, regulatory requirements, and user experience.
Conduct a Risk Assessment
Multi-factor authentication (and your cybersecurity program at large) protects access to sensitive corporate data. Sensitive data includes users’ personally identifiable information (PII), financial records, and IP. Various applications in your ecosystem process this data. Different users have different levels of privilege for accessing sensitive information.
During a security assessment, our team creates an IT asset inventory, categorizes your data, and assigns risk levels. Based on this, we recommend MFA methods.
Most organizations use adaptive authentication — adjusting authentication requirements based on the action-related risks. For example, admin database users have the highest security controls, while a guest user with “view-only” access has lower authentication requirements.
Likewise, the best MFA tools automatically enforce policies based on user location, IP address, time of day, or signals from user behaviour analytics (UBA) tools (e.g., failed login attempts, new device, new location, etc.). Adaptive policies allow companies to maintain a user experience and lower technology costs without increasing cyber risk.
Analyze Existing Infrastructure
The second step is verifying the applicability of the selected authentication technologies for your infrastructure. Legacy applications may not support modern MFA methods. Integration can be complex due to technology fragmentation in the market.
When a major Oil & Gas company asked us to implement MFA, our team found that not all corporate applications had MFA support and direct integration with Microsoft Entra ID (former Azure Active Directory). The client wanted to implement MFA and passwordless authentication with adaptive security controls for different applications. We recommended FIDO2 tokens for Office 365 app and admin portal access and configured Windows Hello for Business for on-device two-factor authentication. We also implemented conditional access to adapt MFA policies for different scenarios.
Consider the total cost of ownership. MFA hardware offers greater security but has higher operating overheads. Off-the-shelf software MFA tools are cost-effective but may not provide the desired security or integrate well with your infrastructure. No matter the case, our cybersecurity team can propose effective hybrid scenarios, combining different MFA methods and technologies.
Check Regulatory Requirements
Authorities like the U.S. White House Office of Management and Budget (OMB), the Cybersecurity and Infrastructure Security Agency (CISA), and the National Institute of Standards and Technology (NIST) urge businesses to use phishing-resistant, passwordless authentication.
The ISO 27002:2022 standard recommends multi-factor authentication, smart access controls (smart cards), digital certificates, secure tokens, and biometric logins for secure authentication. Industry-specific regulations like HIPAA in healthcare, PCI-DSS, and the new FTC Safeguards Rule in finance mandate secure authentication methods.
Take Into Account User Experience
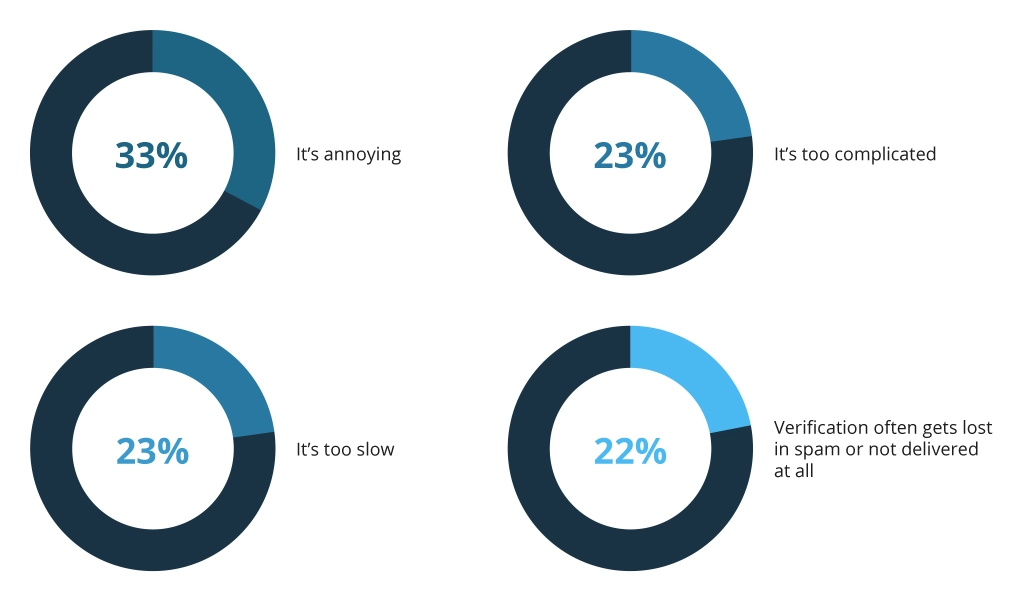
Cybersecurity measures often fail because users are reluctant to adopt them. Workers reuse passwords and customers fail to enable MFA by default because they find it inconvenient.
If a security measure is a nuisance, users will continuously ignore it, so you need to balance security and user experiences. Adaptive or conditional security policies are preferable since they eliminate redundant MFA checks for low-risk accounts and workplace scenarios.
Ongoing security awareness training is important to demonstrate the value of MFA tools and increase policy compliance. A quick white-hack demo from a cybersecurity professional showing how easy it is to take over a user’s account or access their payment method can persuade even the most reluctant adopters.
How to Implement MFA: Best Practices
To further streamline adoption, our team also recommends applying these fundamental best practices:
Know Your Infrastructure
The first step is to determine which systems and applications need MFA protection. Prime candidates are publicly exposed systems and internal applications storing sensitive company data.
Update IT asset management records to account for all IT systems — physical (on-premises servers and data centers) and virtual assets (cloud-based databases and apps). Assign risk scores and formalize authentication requirements.
Understand Your Constraints
The current IT infrastructure may limit your ability to implement certain MFA technologies. Legacy services may not support the selected MFA methods, and some on-premises apps may not integrate with modern cloud-based IAM systems.
On the pro side, security projects can accelerate IT portfolio optimization and harmonization. Our client, a large media company, used to rely on separate domains and infrastructures for different divisions. Implementing a new identity and access management solution with Microsoft Entra (Azure Active Directory) has helped them evolve to a modern hybrid IT infrastructure with a consolidated workload and optimized cost.
Consider other constraints like limited connectivity or device access. For example, if your workforce lacks corporate smartphones, using authentication apps may not be the best option. Similarly, field engineers may lack reliable 4G signal and struggle to receive OTPs for corporate service access. Check if the selected method supports all user requirements.
Set Up Adaptive MFA Controls
Conditional access policies are a simple and effective way to trigger MFA when needed. Instead of asking a user to confirm their identity after a period of inactivity, you can implement granular controls for different scenarios.
For instance, to access an internal corporate portal hosted on-premises, you may skip requesting MFA for users accessing from a corporate IP address from a known device. MFA may not be required for actions like checking account balances in a banking app or generating an account statement.
Tailor policies to user actions and behaviors. Require MFA for large transfers and after multiple failed logins. Choose an IAM solution for conditional policies. Admins should access a console for authentication processes and generate per-user and per-application reports.
Pair MFA with Other Security Methods
Offer various authentication methods to balance security and user experience. Effective combos include single-sign-on (SSO) systems for accessing multiple services after confirming identity with MFA. Enterprise SSO solutions also include user behavior analytics to adjust authentication based on activity.
Managed Device Services, such as where the vendor takes care of the endpoint provisioning, maintenance, device analytics, and security is another great option for ensuring homogenous security across the organization. For instance, Microsoft Intune allows security teams to manage accesses, privileges, device configurations, and app deployment to many corporate devices via a single interface. It also helps collect security analytics for better endpoint protection.
Organizations are adopting passwordless authentication as the “something you know” element of MFA. For example, Windows Hello combines PIN with biometrics for quick access to corporate services. Ping Identity Corporation offers out-of-the-box access to orchestrated SSO and MFA tools.
The adoption of the Zero Trust model also reduces the need for regular MFA checks by granting the user minimal privilege first and then expanding their rights automatically using UAB signals.
Final Tip: Review Security Policies Regularly
To create an effective cybersecurity model, leaders need to focus on both implementing and optimizing adopted policies. Astonishingly, 64% of organizations do not improve their password-based authentication controls even after experiencing a hack. Likewise, only 48% of employers explicitly oblige workers to use MFA, even if it is available.
The better news is that targeted investments in cybersecurity massively reduce the costs and complexity of maintaining high protection levels at all times. By adopting cloud IAM solutions, you can benefit from security defaults issued by the vendors. Security defaults are recommended policies and configurations to ensure protection against common identity threats.
When enabled, these are automatically scaled across all users, reducing the workload of administrators. However, to achieve a greater degree of security efficiency and automation, businesses must already have appropriate levels of infrastructure configurations and a higher degree of cybersecurity maturity — two areas where the Infopulse security team can advise your business.
![How to Choose MFA [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-how-to-choose-the-right-mfa-approach-for-your company.webp)



![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)



