Securing CI/CD Pipelines with Azure, AWS & On-premises DevSecOps
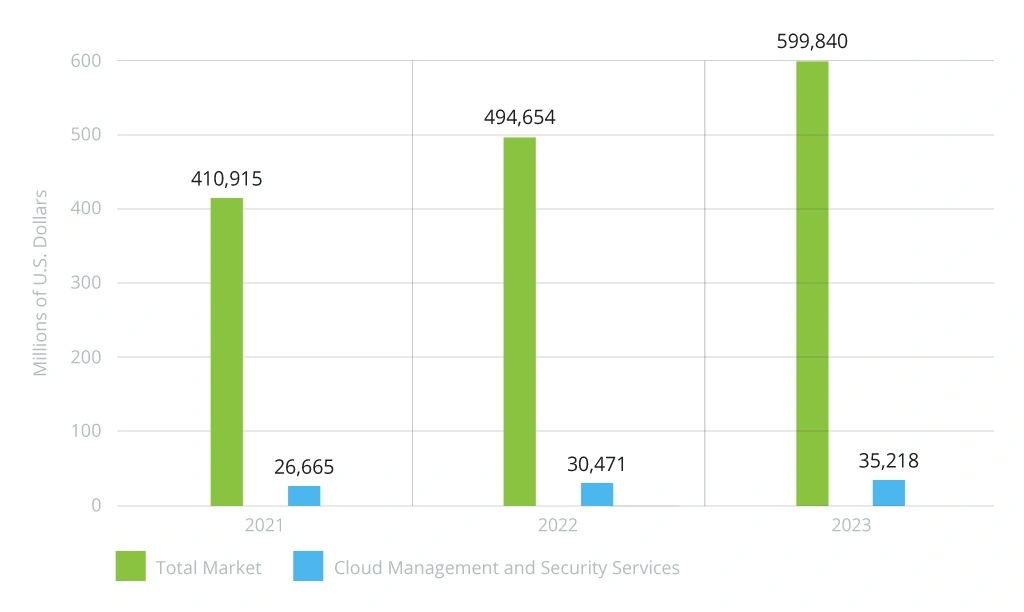
As Gartner’s VP of research states, “Cloud is the powerhouse that drives today’s digital organizations.” Indeed, the total spending for public cloud services, as per the source, is going to gain rapidly in the near future. Eventually, the share of security expenses is to surge, too:
If cloud solutions are only to bolster, would on-premises option become less popular? Today, we will explore the realm of DevSecOps build in the cloud, on-premises, and using the combination of the two – the hybrid setting. Together, we will try to find out what each option holds for businesses.
On-Premises vs Cloud: DevSecOps Snapshot
Though cloud solutions have been in vogue recently, some businesses still go for an on-premises option. The main reason behind their choice is the rules and regulations of certain business domains that are pretty strict and straightforward: they limit the options for IT infrastructure.
For example, government and public services as well as highly regulated banking and financial domains, usually choose this scenario. However, a substantial financial investment exists to build DevSecOps on-premises, including a payroll budget to select, buy, and maintain hardware. Let us not forget about the cost of the hardware itself.
In case of scaling, product managers plan for business growth and expansion, while architects need to estimate what kind and how much of hardware would be necessary to accommodate the projected development. If it is your own on-premises data center, you will require an extensive infrastructure – rooms with servers, lots of electrical services, cooling and air conditioning, as well as wiring works. Supporting this setup requires skilled experts and significant time and money the business has to invest in, since the company itself has to enable the uninterrupted performance of its own operations.
What can you expect with the on-premises alternative then – a cloud option? Unlike with an on-premises situation, uptime is guaranteed by the vendor who offers a cloud solution. In a nutshell, you do not have to ‘nurture’ cloud infrastructure with DevSecOps in AWS or DevSecOps in Azure.
With AWS DevSecOps, for example, you can connect components on demand: when your business grows, you can add more elements on the go, depending on your current needs. With time, you can pay for additional services like AWS CodeBuild service for continuous integration, using the ‘pay-as-you-go’, granular approach.
In contrast, Azure DevSecOps is more monolithic, heavy, and less of a “plug-and-work.” Usually, large businesses find it more suitable as they have versatile ecosystems that require complex solutions to meet their IT infrastructure requirements.
The bottom line is you can compare cloud vs on-premises DevSecOps as credit vs lease and choose the option that best fits your requirements.
If neither on-premises nor cloud suits your business needs 100%, you can always opt for hybrid setting. In such a way, you benefit from both environments. A hybrid infrastructure offers enough room to maintain your legacy servers hosted on-site and connect to cloud with zero disruptions to everyday operational work. You can easily do it by gradually integrating with a public cloud, while running business-critical operations on a private cloud.
DevSecOps on Azure: Creating Reliable Apps with Top-Grade Toolset
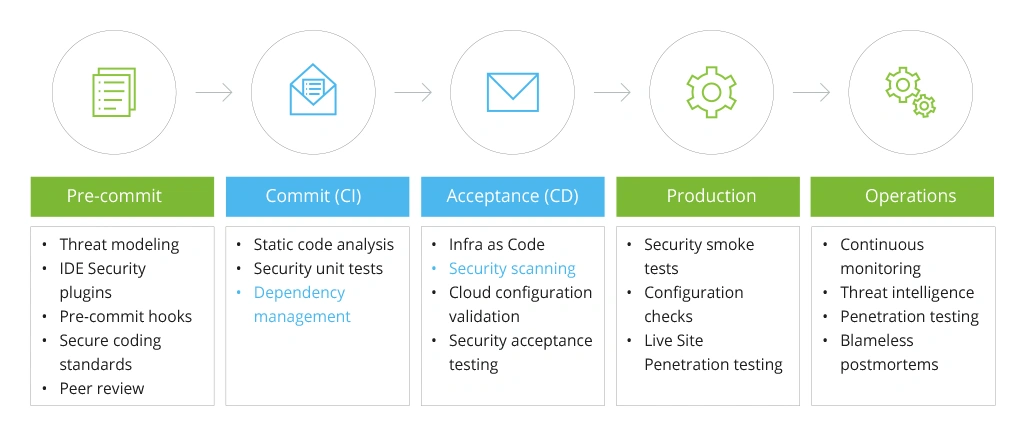
How to include security in the development process and enhance team ties through DevSecOps culture? Modern applications might seem like low-hanging fruit – a no-brainer for a knowledgeable professional.
However, with the evolution of cyber-attacks, embedding DevSecOps into the CI/CD pipeline is both an art and a science security architects must master. See how they are intertwined in the A-to-Z development process:
Implementing Security in DevOps
To make it less abstract, let us dive deep into Azure DevSecOps tools that enable proactive business practices:
Azure Pipelines
To create production-ready container images, Azure Pipelines would do the trick. With the comprehensive traceability of Azure Pipelines, developers can compile a code and pack it into a container with every commit (including further automatic deployment to a test environment). On top of that, the tool permits monitoring the commits, work items, and artifacts of every image to get a better understanding of your code.
Azure Container Registry
This tool with integrated security (Microsoft Defender for Cloud) is an engine behind more streamlined container lifecycle orchestration and management. As a registry of Docker and Open Container Initiative images, it helps developers manage this instrument across multiple geographical locations, automatically build and patch containers. Beyond that, Azure Container Registry serves as a function of task scheduling and base image updates.
Azure Kubernetes Service
Using Azure Kubernetes Service (AKS), you can employ Infrastructure-as-Code (IaC) solution to deploy cluster directly from CI/CD pipeline. Facilitating the deployment of managed Kubernetes clusters in Azure, AKS helps free developers and administrators from system health monitoring and support. Developers can also couple it with Azure Policy to ensure that operations are regulatory compliant, according to industry-specific or regional standards.
Key Vault
To keep your certificates, keys, and tokens safe, Azure offers organizations Key Vault. This instrument enhances the overall performance and helps you reach your desired objectives, offering lower latency with the cloud scale and its redundancy. The latter in terms of cloud guarantees that any component which fails, has an alternative within the architecture. In addition, you level up your data protection and boost regulatory compliance. As a result, you can securely store and manage sensitive information for which you want to have tight access control.
Azure AD
To masterfully manage identity and access control, nothing would work better than the ‘magic box’ of Azure Active Directory (AD). With the latter, you can authenticate users and apps with the existing business directory and rely on elevated security mechanisms, including multifactor authentication (MFA), Identity Protection, and atypical activity reports. Add the secret sauce of role-based access control in the mix to safeguard access to the Azure portal and resources.
Azure Monitor
If your specialists need to get real-time insights about your apps’ health, Azure Monitor comes in handy. Your DevSecOps team members can gather, decompose the relevant data, and make informed decisions based on telemetry collected in the cloud and on-prem. Through Azure Monitor, your technicians can elevate performance and quickly spot and mitigate any emerging problems in no time.
Defender for Cloud
Working for Azure, on-premises, and multi-cloud settings, this instrument supports Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP). Overall, Defender for Cloud has several functions including vulnerabilities detection and tracking, securing workloads from established security risks, and identifying and tackling threats to services and resources.
DevSecOps on AWS: Practical Tools
Further, we will be sharing some hands-on experience and DevSecOps tools our AWS engineers opt for.
GovCloud, Code Build & CodeCommit
To begin with, when using a public cloud for building a strong IT infrastructure, we can lower its risks and possibility of being compromised by moving part of the information to a particular AWS segment called GovCloud. For the record, the latter is similar to Azure Germany, as it is believed to be one of the safest solutions with GDPR compliance in focus.
With GovCloud, virtual infrastructure components are better protected. As a part of CI/CD, we need a place to store, build, and deploy it, for example, using AWS CodeCommit (similar to GitLab) and CodeBuild, respectively.
Static Code Analysis
All the info transferring from CodeCommit to CodeBuild is securely stored. Still, we can layer more security components on top of these two. We can do it by connecting SonarQube, which is responsible for ongoing code inspection based on the last push, branch, or feature introduction. Additionally, it is possible to check the interdependencies of a programming code and inspect the modules we connect.
CodeDeploy & the Green-Blue Strategy
This AWS component deals with code changes. When a developer pushes the code to SVN system/CodeCommit, CodeBuild creates a new software build, considering the recent changes. After the build is ready, it goes to production with the help of CodeDeploy. Further, the companies that want to increase the availability of their product use the Green-Blue deployment model.
The latter is a change management approach that step-by-step shifts user traffic from one product version to another while both are running in a production environment and being a backup for one another.
AWS Config & CloudTrail
For AWS access control alerts, these two DevSecOps instruments come in handy. If the entire infrastructure is built on AWS, it is easy to monitor its config-based condition, where any change in any config can be a warning sign of something going wrong. In such a case, a respective alert is sent, asking to sign off on and permit a change. Thus, CloudTrail is an instrument that logs all the changes: as any change in AWS is an interaction with API.
Identity and Access Management (IAM)
User accounts, especially their root types, are the most valuable assets in the AWS infrastructure. Therefore, to manage permissions to resources and services in a secure way you will need IAM. The service allows creating password policies, setting time and criteria for password changes as well as implementing two-factor authentication.
To benchmark your architectures against existing standards and spot the opportunities for improvement, it’s worth selecting the AWS Well-Architected framework that helps with business process optimization, reliability, enhanced productivity, better cost management, and ecosystem protection.
DevSecOps AWS vs. DevSecOps Azure
Both options have their own “marketplace,” which allows growing functionality, adding more components when necessary.
When it comes to an authorization system, for instance, there are Azure AD in Microsoft and IAM in AWS. Developers and administrators can use IAM to differentiate access to the cloud; it is more pragmatic as it allows mass users. Additionally, Linux-oriented AWS is more granular; it is mosaic-like building blocks, with which you can create a bigger picture. AD, in comparison, is larger and would suit organizations with complex hierarchies.
To Conclude
While each option has its own particularities, AWS DevSecOps best practices, Azure DevSecOps best practices, as well as the on-premises option are more about a holistic approach than one-size-fits-all thinking regarding security standards. Infopulse can assist you with the right choice of technology to enable security best practices. Reach out to our team and we will address any questions you may have!
![DevSecOps on Azure vs on AWS [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-dev-sec-ops-on-aws-vs-azure-vs-on-prem_1.webp)



![Cloud-Native for Banking [thumbnail]](/uploads/media/cloud-native-solutions-for-banking_280x222.webp)
![Generative AI and Power BI [thumbnail]](/uploads/media/thumbnail-280x222-generative-AI-and-Power-BI-a-powerful.webp)
![Cloud Native vs. Cloud Agnostic [thumbnail]](/uploads/media/thumbnail-280x222-cloud-agnostic-vs-cloud-native-architecture-which-approach-to-choose.webp)
![DevOps Adoption Challenges [thumbnail]](/uploads/media/thumbnail-280x222-7-devops-challenges-for-efficient-adoption.webp)
![Azure Monitor for SAP [thumbnail]](/uploads/media/thumbnail-280x222-azure-monitor-for-sap-solutions-an-overview.webp)
![Mortgages Module Flexcube [Thumbnail]](/uploads/media/thumbnail-280x222-Secrets-of-setting-up-a-mortgage-module-in-Oracle-FlexCube.webp)
![Digital Alignment Drivers [thumbnail]](/uploads/media/thumbnail-280x222-the-top-forces-driving-digital-alignment.webp)
![AWS vs. Azure Cloud Platform [Thumbnail]](/uploads/media/thumbnail-280x222-comparison-of-aws-vs-azure-when-each-cloud-platform-works-best.webp)
![Cloud-Native Maturity Model Assessment [thumbnail]](/uploads/media/thumbnail-280x222-what-Is-the-cloud-native-maturity-model-definition-and-assessment-criteria.webp)