How to Enable all Three Zero Trust Principles within Azure AD
Soundly, organizations are not on their own in their battle for security. Solutions such as Azure Active Directory (AD) by Microsoft provide a range of necessary capabilities for implementing the Zero Trust security model — arguably, the best type of protection your business can establish today.
What is Zero Trust?
The Zero Trust approach to cybersecurity entails denying all access to resources on the network until the request passes a verification. In other words, every request is viewed as “guilty unless proven otherwise”.
Three principles of the Zero Trust security model:
- Verify explicitly: Authenticate and authorize requests using multiple data points.
- Grant least privileged access: Extend just-in-time and just-enough-access to users; create risk-based, adaptive policies for different groups.
- Assume a breach: Segment accesses, verify encryptions, and use threat detection tools to continuously monitor the perimeter.
Think of a zero trust model as your office building. Most people can step into the lobby, but then all visitors will need to introduce themselves and get authorization for accessing certain floors, rooms, and so on. You do not let a stranger poke into any office they want because anything can happen.
Likewise, it is essential to understand what happens behind your corporate firewall. Apart from knowing the “visitors”, you also need to ensure that they have the right type of access, privilege, and protection.
Why Azure AD for Zero Trust
Azure Active Directory is an identity-as-a-service (IDaaS) and access management solution, offering single-sign-on (SSO) capabilities for on-premises and cloud apps for all users in your ecosystem. Unlike standard SSOs, Azure AD also doubles as a security policy management solution. It allows the implementation of adaptive controls, automated monitoring, and visibility for different user groups.
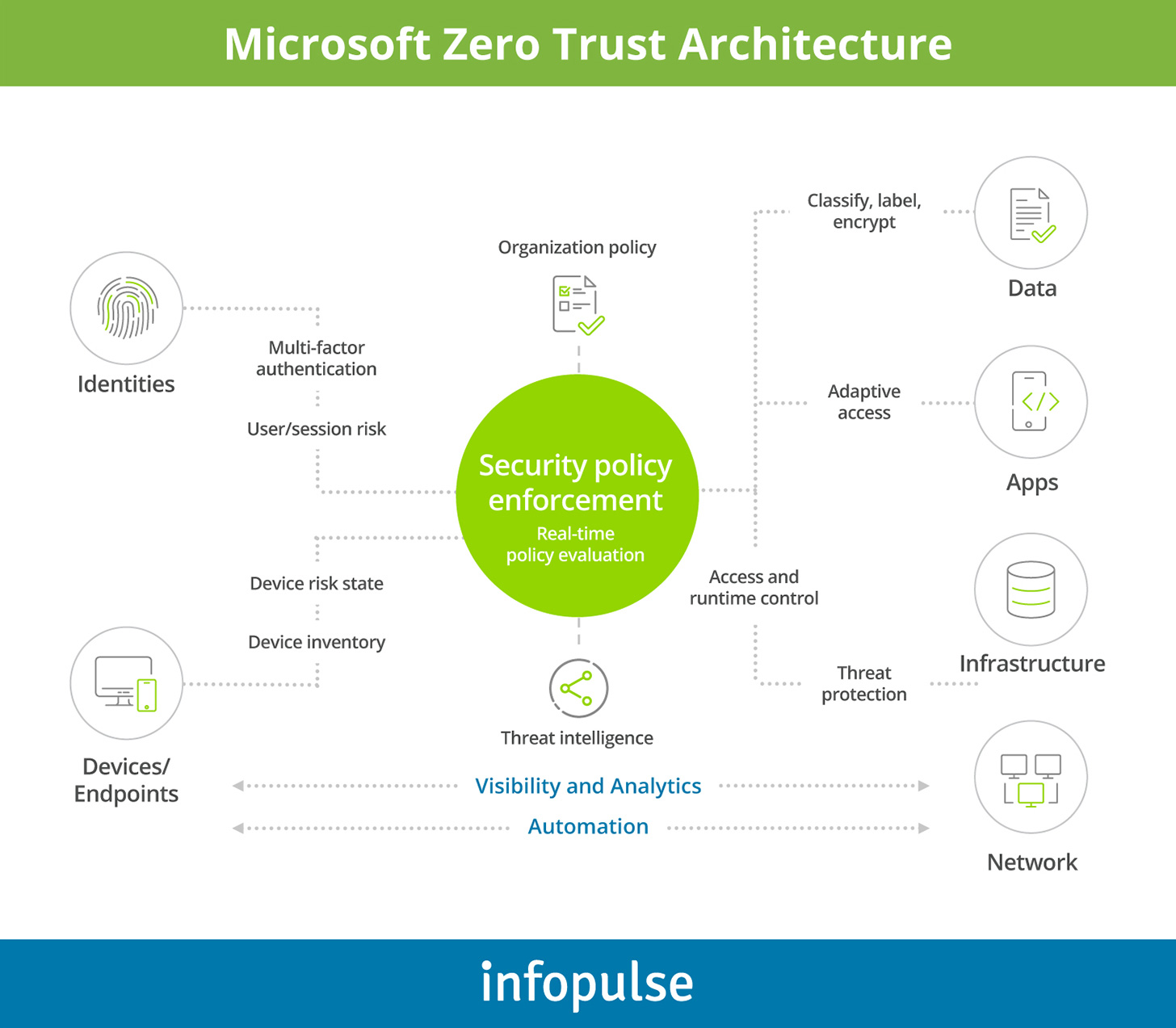
Azure AD features:
- Centralized application management
- Strong customer authentication (SCA)
- Conditional access
- Device management
- Guest user policies
- Identity governance and protection
- Privileged identity management (PIM)
- Advanced reporting and monitoring capabilities
The above controls allow your security teams to implement flexible, condition-based user access policies, provision timely access to the necessary apps/data, and automate detection and remediation of compromised identities. According to a Forrester study, Azure AD users experienced:
- 75% reduction in password reset requests with an estimated savings of $684k per year.
- $2.1 million over three years in estimated risk reduction through lower chances of a data breach.
- An average payback period of 6 months and over $15.9 million in perceived value within three years after adoption.
Moreover, the adoption of Azure AD leads to a number of unquantifiable user benefits as one of our customers, a large pharma company, reported. These include higher user productivity, improved access to corporate data, and better collaboration.
4 Steps towards Enabling Zero Trust Approach with Azure AD
Microsoft has been continuously re-aligning Azure AD capabilities with the principles of zero trust based on such security frameworks as NIST SP 800-207, OMB TIC 3.0, and CISA CDM.
Despite being highly technical, Azure AD remains intuitive in usage and non-disruptive in implementation. Here is how to get started with Azure AD:
Step 1: Connect all users, groups, devices to AD. Implement authentication options that make the most sense for your organization. For convenience, you can also use Azure AD Connect to create the optimal topology and configurations.
Step 2: Integrate all corporate applications with Azure AD. AD provides SSO capabilities, meaning that users do not need to maintain (or leave) copies of their credentials in other applications. Instead, they can rely on Azure AD at all times. Prior to transitioning, be sure to switch off other IAM engines (if you have any) as these may interfere with AD performance.
Azure AD supports the following types of integrations:
- OAuth2.0 or SAML
- Kerberos and Form-based authentication applications that can be integrated via Azure AD Application Proxy
Azure also has a number of pre-built integrations for legacy applications including:
- Akamai Enterprise Application Access (EAA)
- Citrix Application Delivery Controller (ADC)
- F5 Big-IP APM
- Pulse Secure Virtual Traffic Manager (VTM)
- Kemp
Step 3: Automate user identities distribution to your apps. After consolidating all user identities in Azure AD, you can set up the automatic distribution of these to different cloud apps. You can also implement custom business rules for different SaaS apps and effectively scale user identity management across cloud and hybrid environments.
Step 4: Organize logging and reporting. Azure AD collects and assesses security signals to determine the best course of action. Ensure that you are collecting necessary log data for audits to better understand your users’ working patterns and detect potential risks at the onset. Azure AD data can be then integrated with Azure Sentinel — the company’s security information and event manager (SIEM) platform.
Implementing Three Zero Trust Cyber Security Principles with Azure AD
Azure AD provides a robust toolkit for implementing Zero Trust security principles. However, it is your job to determine the optimal architecture pattern and implement respective controls. Based on Microsoft best practices, our cybersecurity team recommends the following steps.
Enacting the Principle of Least Privilege on AD
Azure AD has two main features for enabling the first principle of Zero Trust: time-limited access and role-based access control.
First, consider the premises of your Conditional Access policy. Devise a set of if-then scenarios for authentication and verification for different user groups. Remember: your goal is twofold — secure corporate data without hindering user productivity.
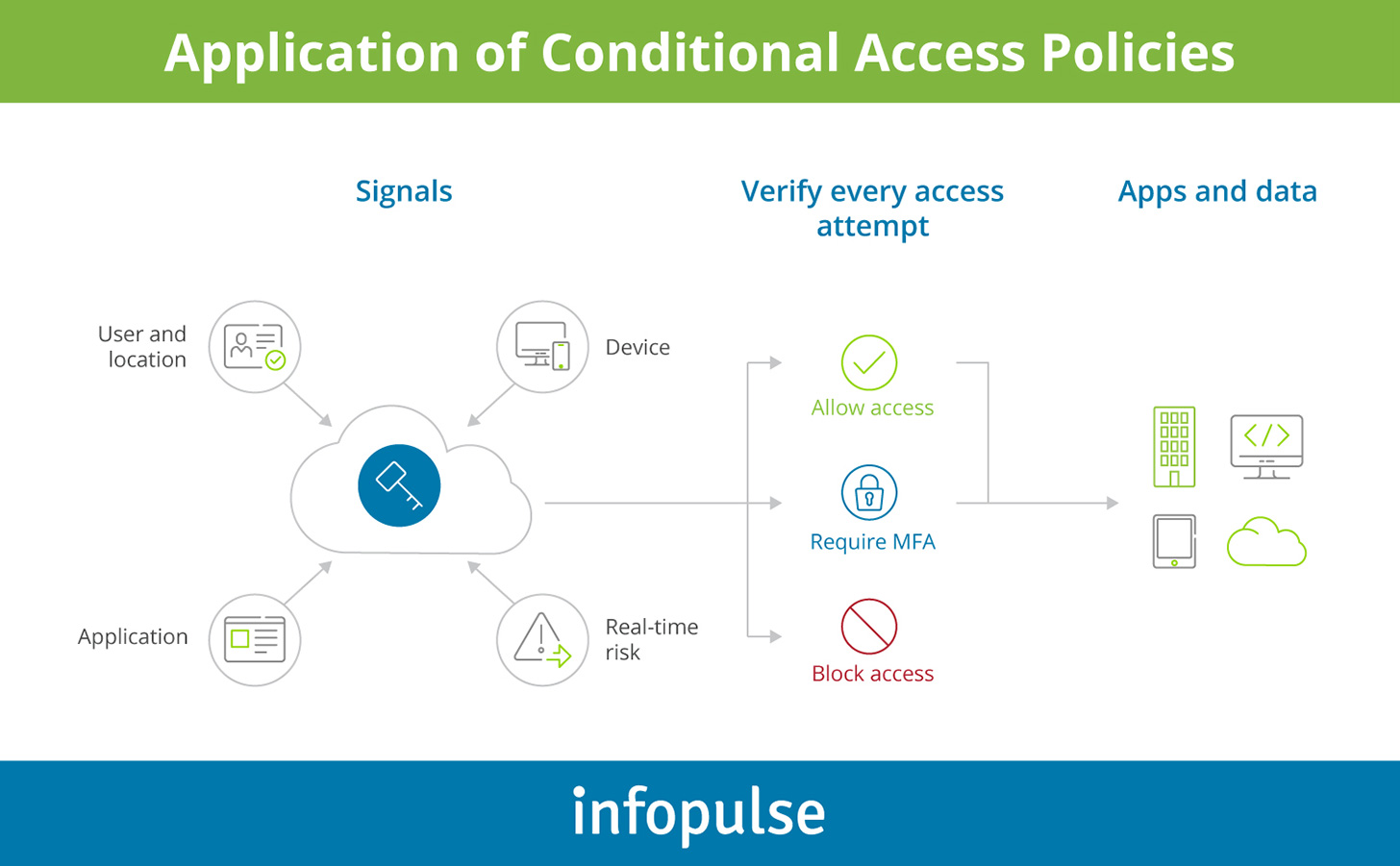
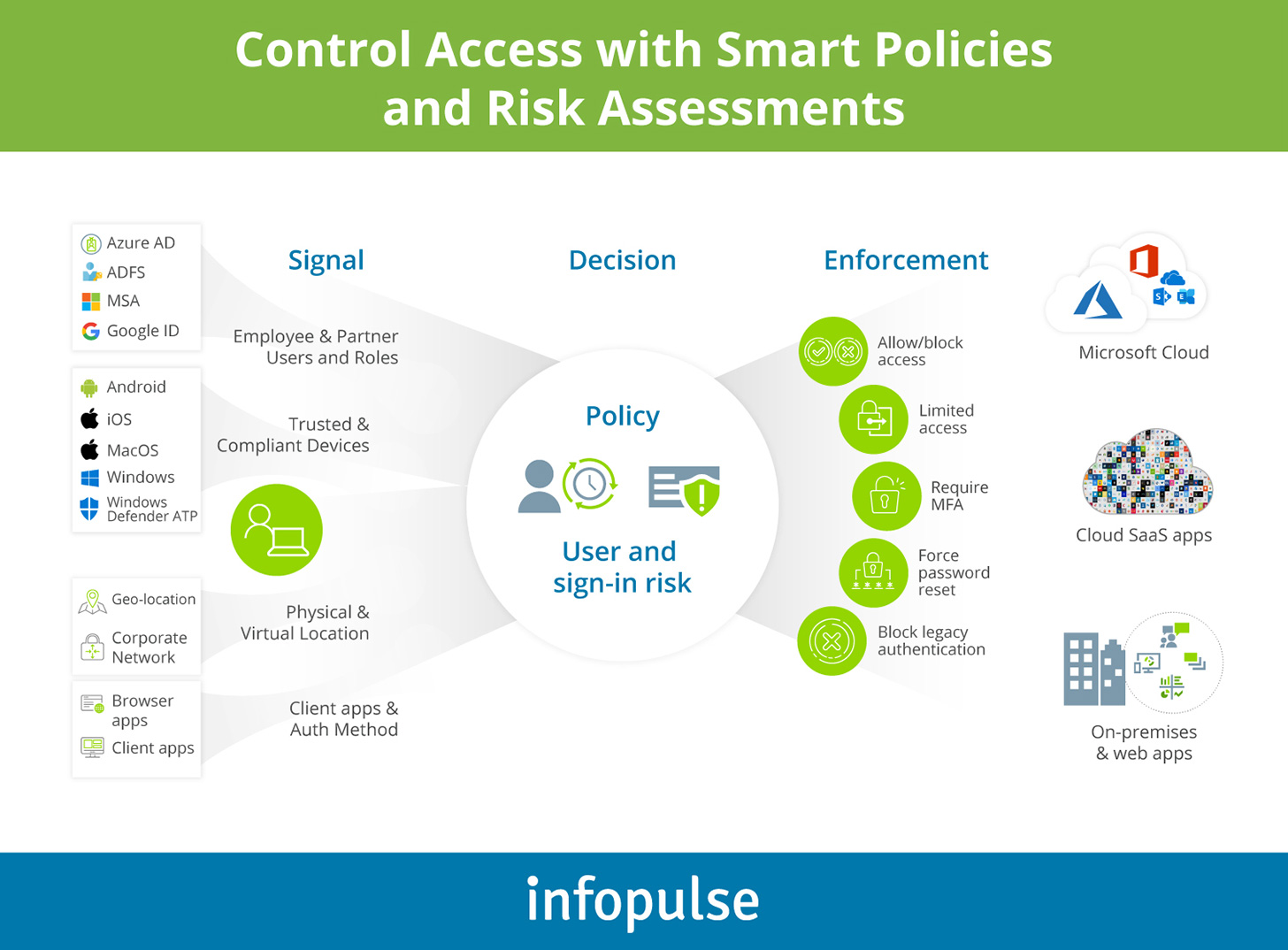
Next, determine which user roles require privileged access. Unlike traditional network security solutions, Azure AD replaces the network security perimeter with an identity layer. Respectively, roles with the most privilege gain nearly universal control. Use Azure AD Privileged Identity Management (PIM) tool to configure the optimal policies for the next types of roles:
- Global Administrator
- Privileged Role Administrator
- Exchange Administrator
- SharePoint Administrator
Turn on multi-factor authentication (MFA) for each role. Then use Azure AD Identity Protection service to assess and monitor for potential vulnerabilities.
For all user roles, review and restrict user consent to applications. This step helps minimize the chances of accidental or malicious exposure of your corporate data to third-party providers.
If you are on the Azure AD Premium P2 plan, take advantage of the entitlement management feature. It allows you to create time-bound access packages for specific user groups (e.g., a team) for faster distribution. Alternatively, you can opt for self-service group management and self-service application access.
Enacting the principle of explicit verification on AD
The second principle of Zero Trust prompts encompassing verification of users, based on different signals.
Start with the basics — implement MFA for all unknown users, attempting to sign in from an unknown device or location.
Next, enable Azure AD Join or AD Hybrid Join — a service that allows linking corporate devices with a respective Azure AD identity for better monitoring and control.
Afterward, enable Microsoft Intune — a service for securing users’ corporate mobile devices and exercising remote updates and control over them.
Finally, consider transitioning to passwordless credentials. Passwords have long been the weakest link in corporate security. A strong password policy is hard to enforce among users, while password reset costs leave a sizable dent in your IT budget. Additionally, passwords are prone to spoofing, phishing, and social engineering. Azure AD supports passwordless phone sign-ins, FIDO2-compliant security keys, and biometrics-based authentication for Windows users.
Enacting the Principle of Assuming a Breach on AD
Human errors, not targeted attacks, are the cause of corporate data breaches in 88% of organizations. Azure AD provides stellar capabilities for minimizing the chances of human errors, while also protecting your assets from external attacks.
Implement Azure AD Password Protection as the first security baseline for on-premises and cloud applications. This service prohibits creating weak passwords, plus allows you to create custom password policies and add lists of banned passwords (known compromised credentials).
As an extra step, you can also consider blocking legacy authentication via Conditional Access. Doing so prevents access from applications that use POP, SMTP, IMAP, and MAPI protocols, known to be incompatible with MFA.
Extend Azure AD Identity Protection to all users to benefit from automated monitoring and reporting on anomalies, suspicious sign-in attempts, and early signs of compromised accounts.
Larger enterprises with global staff can also benefit from enabling restricted access to SharePoint and Exchange online apps. In such a case, a user, attempting access from an unknown device or location, can gain access to the requested resource but remain limited in their actions.
Companies relying on SaaS applications should also consider integrating Conditional Access with Microsoft Cloud App Security (MCAS) to monitor user behavior in connected applications and enforce the necessary policies. Similarly, MCAS can be integrated with AD Identity Protection to gain more visibility into user’s actions post-authentication in the SaaS app to receive more security signals.
Finally, tools such as Azure Advanced Threat Protection (ATP) and Microsoft Defender ATP allow you to broaden your perimeter even further. Azure ATP helps collect security signals from on-premises apps, whereas Microsoft Defender ATP provides intel about Windows machine health. The two services supply extra intel for your SOC team to analyze and act upon it.
To Conclude
Azure AD is one of the first IAM solutions to offer multi-vector protection for cloud-based and on-premises business apps, easily extendable across all assets within your ecosystem. Even more importantly, Azure AD provides unprecedented levels of downstream and upstream visibility that help security teams understand normal user behavior and common attack vectors. Last, but not least, Azure AD helps enact the principles of zero trust security without hindering the end-user experience.
If you want learn more about the full scope of Microsoft security solutions, download our eBook on Innovative Approaches to Cybersecurity. Or if you have a specific question about Microsoft Azure AD and Zero Trust model implementations, contact Infopulse security team directly!

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


