What Is IT Asset Management and How to Build a Strong Process for Your Business
IT technologies have proven time and sizable benefits for businesses. However, without a strong IT asset management process, your IT infrastructure can progressively transform from a competitive advantage into a financial and security liability.
What Is IT Asset Management?
IT asset management (ITAM) is a structured process for maintaining an account of all technology assets through standard lifecycle policies. An IT asset management plan maximizes the value of technology investments, existing architecture, and sourcing decisions by accurately accounting for operational costs and risks.
ITAM Lifecycle
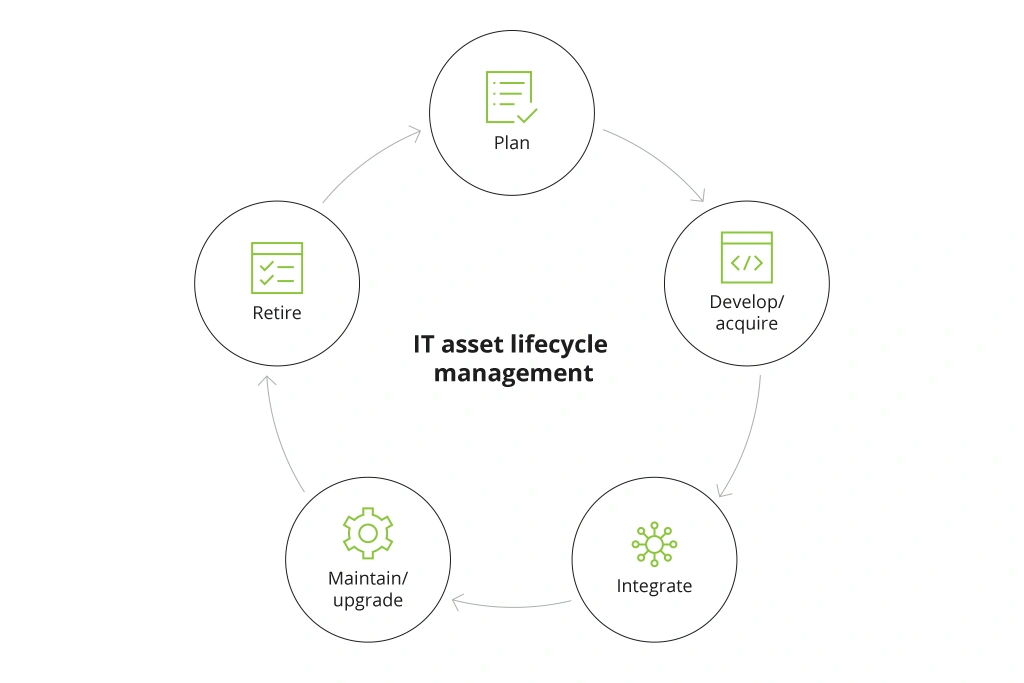
Key IT Asset Management Principles
The first principle of effective ITAM is: “Know Your Infrastructure”. You need to understand what assets your organization holds and determine the optimal approaches to controlling them.
Unlike physical, IT assets are often more complex to map and define. On the surface level, most count one business application as an asset, but that is a narrow view. Each application has a “hidden layer” of supporting infrastructure, ranging from a hosting destination (e.g., a local server) and networking endpoints to API-based integrations with other systems.
Conditionally, we can separate IT assets into two groups:
- Physical assets — on-premises servers, data centers, networks, routers, etc.
- Virtual assets — corporate website and application(s), cloud-based databases, CRM, etc.
Next, you can identify all the components of an IT asset by analyzing it through three dimensions:
- Infrastructure includes all the supporting local, cloud, or hybrid infrastructure elements, associated with a certain asset (and proper cost/security controls, implemented for them).
- Operating systems — outdated OS versions or subpar configurations can also be a source of risk for IT assets, operating on them.
- Applications (proprietary and SaaS) — unlike custom apps, SaaS/IaaS solutions do not require manual patching or security updates. However, you need to implement proper security configurations and access management rights to prevent breaches or data leakage.
The second key principle of ITAM: “Know the IT Owner”. For each IT asset, you need to understand who is in charge of
- Procuring, using, and maintaining an IT asset
- Administering the said application
In most cases, these can be several different people since lines of business now account for 56% of all company app ownership and management.
Once you have correctly determined the asset size and owner, you can complete the final categorization step — determine the value of your IT asset.
Each IT asset should be protected according to its perceived value. For instance, building a complex line of defense for an isolated application that contains non-sensitive data does not make much economic sense. However, adding extra safeguards for an on-premises database, holding customer personally identifiable information (PII) or corporate financial records is a sound step.
Benefits of Cloud-Based IT Asset Management Process
The above asset assessment process may initially sound too complex, but the payoffs of implementing an up-to-date, cloud-based ITAM process are significant.
Counter Shadow IT
Shadow IT is an umbrella term for all the technology applications deployed by employees directly without the authorization or knowledge of the IT department.
On average, the number of SaaS apps running on corporate networks is three times greater than what IT departments are aware of. Even if the size and scope of shadow IT can appear negligible (e.g., an employee, installing a spell-checking browser add-on), its impact on corporate cybersecurity can be significant. Almost 70% of tech leaders view shadow IT as a security concern.
IT asset management helps establish a better purview into the known and previously unaccounted assets, plus counter unauthorized app usage. Additionally, an in-depth audit can help you establish what tools your teams actually lack and create new procurement requests for your IT service desk.
Improve IT Visibility and Optimize Spending
Understanding which IT assets you own, where they are located, and how much they cost to operate is another key element of effective ITAM. Since the cloud made extra resource provisioning a matter of several clicks, organizations increasingly struggle to contain the growing cloud bill.
As much as 30% of cloud computing resources regularly get wasted due to suboptimal workload allocation, poor data management practices, and lack of streamlined procurement.
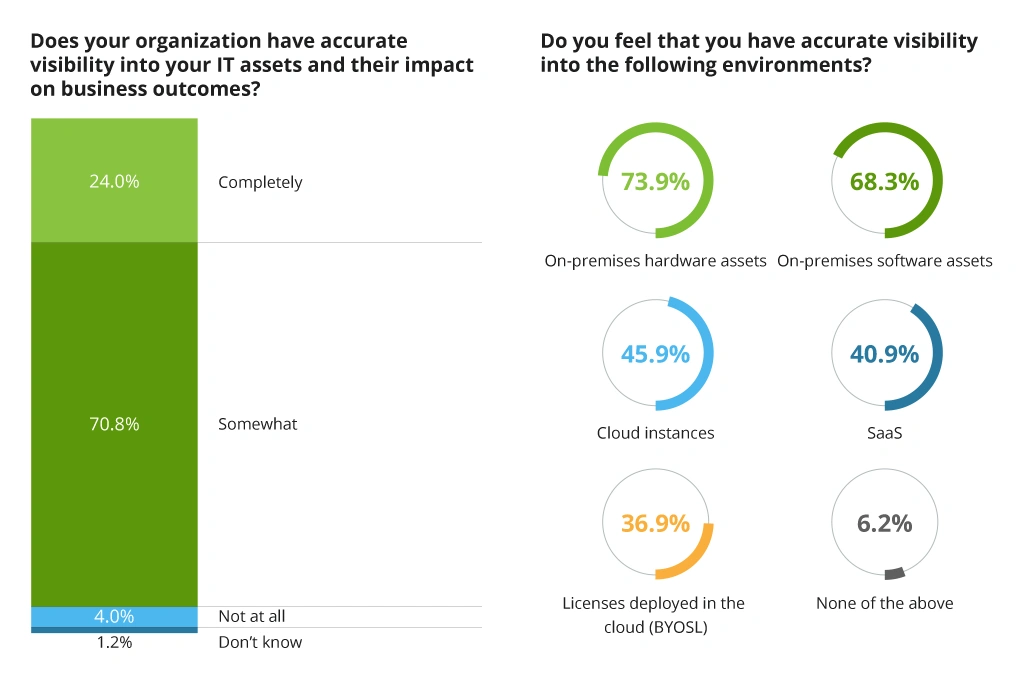
At the same time, leaders also struggle to understand which resources are already available due to low visibility into the current IT ecosystem.
Organizations' Visibility Into IT Assets and Environments
Modern IT asset management software can progressively scan your environments and bring forward underutilized resources, cases of inadequate workload allocation, and draw attention to other areas for cost- and operational optimizations.
Reduce Human Factor Security Risks
About a third of employees (36%) admit to having made a security-impacting mistake at work. The growing volume of malware and phishing attacks also makes companies more critically exposed. The danger of such incidents often lies in the fact that one overlooked IT asset with expired security credentials can serve as a leeway into a wider system penetration.
SANS report found that most insider security threats result from lacking visibility into baseline normal user behavior as well as poor access management of user accounts. Given that insider threats can cost enterprises $11.45 million on average, they should not be taken lightly. By proactively improving visibility and employee security policy management with ITAM, organizations can bolster their security.
How to Create an IT Asset Management Process
Cost optimization and risk mitigation are the two intrinsically linked components of digital asset management.
In the current business climate, most companies remain in cost-containment mode, seeking to optimize spending without undermining the short-term ROI of ongoing digital transformations. That said: the rapid shift to digital workplaces and cloud-first operations has left many organizations with underused on-premises resources, unaccounted virtual machines (VMs), and under-the-radar business applications. For instance, less than 45% of company SaaS applications are being used on a regular basis. Clearly, there is a lot of money left on the table.
At the same time, companies are forced to move fast and deploy new use cases and applications at cruising speed. Every new application requires proper underlying infrastructure to support everything from storage capacity to data protection and cybersecurity. When time is an issue, decisions are made in a rush, leading to improper infrastructure configurations, security gaps, and suboptimal resource usage (e.g., commissioning a new cloud instance versus using an idle server).
Finally, as much as 50% of corporate data remains on-premises. Oftentimes, this is the most sensitive and valuable corporate intel that requires utmost cybersecurity protection. With the growing size and complexity of overall IT infrastructure, administrators often struggle to ensure its proper protection against both insider and outsider threats.
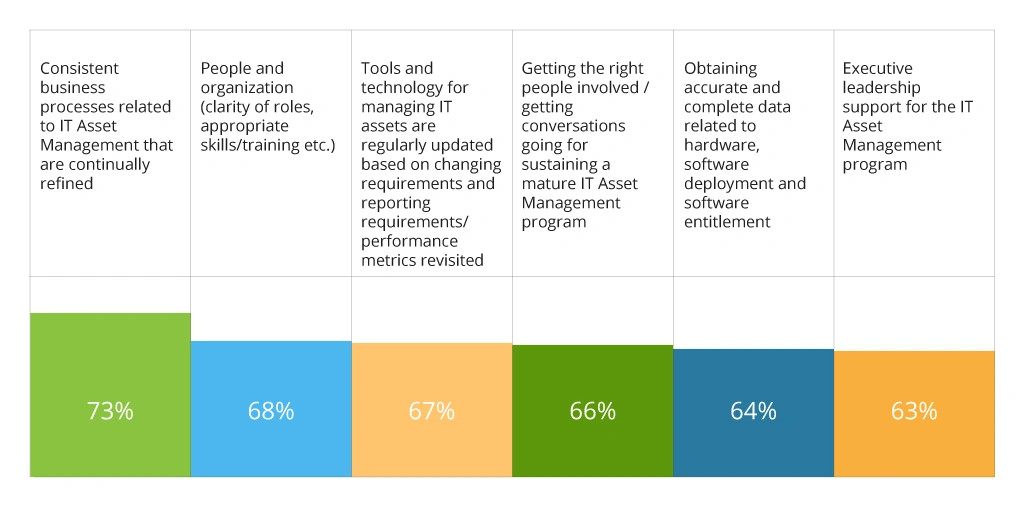
Given the above, it makes sense why 84% of CIOs believe that they lack a truly effective ITAM strategy in their organization due to inept business processes, people and organization issues, and missing IT asset management software.
Pain Point in Organizational ITAM Programs
The better news is that the challenges above can be proactively addressed and resolved as our cybersecurity consultants explain in this section.
Conduct an Asset Discovery
Without a comprehensive inventory of all IT assets, you cannot establish a proper management cadence. Hence, your first goal is to locate and tag all the infrastructure elements you have. Then determine how to harmonize your portfolio to improve its cost performance and security standing.
At Infopulse, we suggest collecting the following intel about your assets:
- Current active assets
- Parameters and properties of assets
- Historical data about assets
- Asset's state from security and compliance point of view
To gain this data, our consultants employ active (scanning, mapping) and passive (through analysis of collected events, configurations, state tables) objects discovery methods.
For such audits, we recommend using AWS asset management tools such as AWS Systems Manager Inventory to automatically collect metadata from all your cloud deployments. Using built-in platform tools, you can easily query this data to identify performance or configuration issues that differ from your corporate policies. Running regular scans can help you proactively contain costs and minimize cases of under-utilized resources.
Define Assets Value and Criticality
As discussed earlier, different IT assets need different degrees of protection. Investing in more cybersecurity tools and safeguards do not always translate to better security outcomes. On the contrary, security tooling sprawl can become another source of vulnerability since your teams will likely struggle to implement standardized controls across the board. Gartner found that security control failures were the number one cited cyber risk in Q1 2021.
The optimal way to prevent such a scenario is to define asset value and criticality prior to making any further decisions. Understand which security and cost controls are available and verify their current state of implementation. Then decide if extra security controls are truly warranted by stacking the TCO of the new security solution versus the cost of experiencing/containing a risk.
When designing our internal asset management policy, Infopulse used a three-criteria matrix for evaluating each asset. We asked the line of business (LOB) leaders to first map each asset by perceived value (high, medium, low). Next, the cybersecurity team marked each asset as local versus externally exposed (where the latter requires greater protection) — and established each asset’s interconnection with other systems (greater connectivity expands the risk radar. For various types of infrastructure, we have designed a series of asset management policies and additional security protocols.
Tag Your Assets
To ensure the “Know Your IT Owner” principle, you should create a clear labeling system where each asset has:
- Assigned properties
- Related/interconnected IT systems
- Current IT owner and administrator (if different)
The easiest way to do the above is by creating a standardized resource tagging system in AWS and a mirror version for all on-premises resources.
A tag should communicate the server’s primary designation, plus provide an easy way for identifying its primary purpose and affiliation with a certain project or department. Your naming parameters and tagging taxonomy should be standardized across the board.
Separately, take time to create internal documentation, explaining the status and value of each asset, its ownership, and recommended configurations. Incomplete or non-existent technical documentation is a sign of an immature ITSM process.
Create a Change Management Process
At the end of your asset audit, you would likely end up with a collection of assets requiring updates, deprecation, or changes in configuration. The obvious question is: Who should be in charge of applying the fixes now and in the future?
Your change management process has to specify that. Once you figure out the ownership status for each asset, you can create standard ITSM workflows for asset management and maintenance — and escalate issues to the right person.
In this case, your ITAM system acts as a single source of truth that supplies different LOBs and IT personnel with information about discovered vulnerabilities, configuration issues, or wasteful resource usage practices.
Schedule Regular Audits
IT asset management is a lifecycle process. By the time you are done with the first round of optimizations, a new sprawl may start emerging in some far corner. Legacy software and servers also require more frequent patching — and new technology investments will also affect the state of your IT ecosystem. To maintain equilibrium, you need to perform regular audits every 12 to 18 months.
To Conclude
IT asset management is a “housekeeping” activity: it might not sound initially exciting, but its value cannot be underestimated. Without ITAM, your organization will not be able to excel in other areas of IT services management. More importantly, lax attitudes towards IT assets result not just in budget waste, but also heightened security measures and compliance risks. A streamlined ITAM process established once continues to protect your business for years to come.
![What Is ITAM [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-what-is-it-asset-management-and-how-to-build-one.webp)

![Expanding NOC into Service Monitoring [thumbnail]](/uploads/media/280x222-best-practices-of-expanding-telecom-noc.webp)
![Cloud-Native for Banking [thumbnail]](/uploads/media/cloud-native-solutions-for-banking_280x222.webp)
![Data Governance in Healthcare [thumbnail]](/uploads/media/blog-post-data-governance-in-healthcare_280x222.webp)
![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![ServiceNow and Third-Party Integrations [thumbnail]](/uploads/media/thumbnail-280x222-how-to-integrate-service-now-and-third-party-systems.webp)
![5G Network Holes [Thumbnail]](/uploads/media/280x222-how-to-detect-and-predict-5g-network-coverage-holes.webp)
![DevOps Adoption Challenges [thumbnail]](/uploads/media/thumbnail-280x222-7-devops-challenges-for-efficient-adoption.webp)
![How to Reduce Churn in Telecom [thumbnail]](/uploads/media/thumbnail-280x222-how-to-reduce-churn-in-telecom-6-practical-strategies-for-telco-managers.webp)
![Automated Machine Data Collection for Manufacturing [Thumbnail]](/uploads/media/thumbnail-280x222-how-to-set-up-automated-machine-data-collection-for-manufacturing.webp)
![Azure Monitor for SAP [thumbnail]](/uploads/media/thumbnail-280x222-azure-monitor-for-sap-solutions-an-overview.webp)