Enterprise IT Security: How to Reorganize and Centralize Your Cybersecurity System
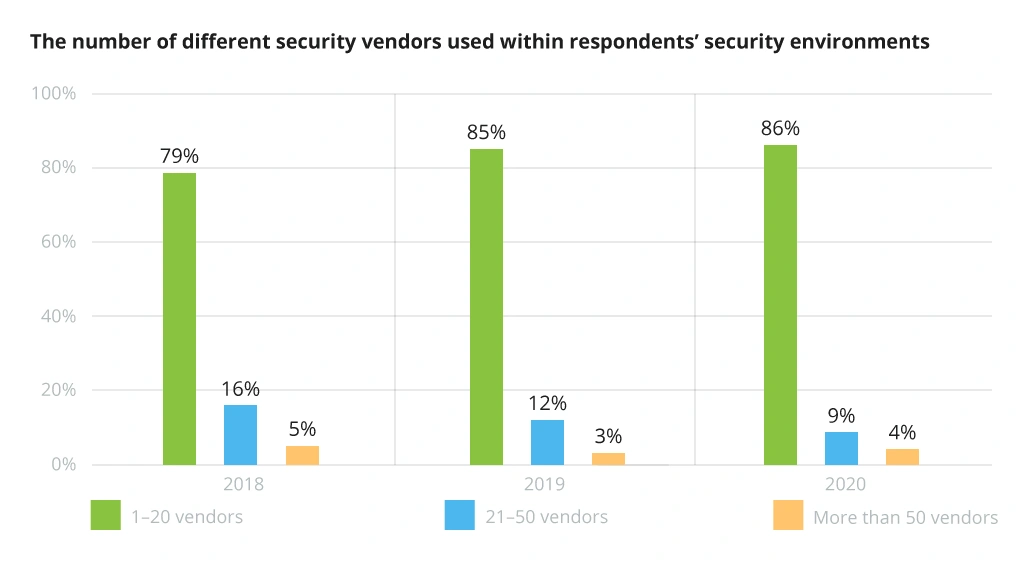
Businesses tend to add new products to their existing IT ecosystems mostly as new needs arise. Consequently, many enterprises end up with a collection of specialized tools for distinct niche purposes, varying data types, and operations being not as efficient as expected. Almost every company activity, from marketing to information security, exhibits this pattern. However, with 86% of organizations using IT security solutions provided by between one and twenty vendors, and only 13% using more than twenty, the tendency to minimize complexity through vendor consolidation continues.
The Trend Toward Vendor Consolidation
The fact is that an array of diversified solutions makes it difficult to monitor the systems, gather and analyze data, and manage the landscape. This is especially true when it comes to cybersecurity, where the stakes are high and the potential for data breaches is all too real. To cope with these challenges, organizations need to adopt a holistic approach to security that considers the whole variety of solutions in use. This implies having a clear understanding of the systems and data flows while being able to monitor and manage them effectively. It also requires having the proper tools and processes in place to collect and analyze data as well as to identify and respond to security threats.
In this article, we will explore what key components of designing an enterprise IT security system are and what tools you can use to reorganize it.
Why Is Centralized Management an Essential Security Measure?
Data breaches and cyberthreats have become so commonplace that it’s almost hard to imagine our digital lives without them.
Currently, the world is undergoing a tremendous cyberwar on a global scale. Over the past few years, there have been numerous high-profile data breaches, cyberattacks, and even multifaceted cyberattack campaigns. It is not just companies with sensitive user data that are being hit; even game developers like Fortnite, streaming services like Twitch, and fashion retailers like Guess have all become victims of data attacks.
When it comes to a decentralized IT security system, it has several disadvantages:
- First, it is less secure since there is no single point of control. As a result, coordination of security efforts can be difficult, which makes it easier for attackers to exploit vulnerabilities.
- Second, decentralized security systems are more complex and difficult to manage because each component must be configured and maintained separately. This can lead to a breakdown in communication and coordination among various security efforts, making it more difficult to respond to security threats.
- Another weak point is that there are often multiple experts responsible for security, each worth the cost, usually making such systems more expensive to maintain.
As many enterprises today are liable for various types of sensitive data, they need to make sure that this data is properly secured. The centralization of an enterprise security landscape is one of the most frequently used approaches to data protection. By bringing all your different security systems under a single umbrella, you can ensure they are consistently monitored and maintained. In addition, you also gain better insight into how your security solutions perform over time. This data then allows you to detect and deal with potential problems early on before they lead to bigger issues.
Centralizing Your Security System: Steps to Take
To rearrange your enterprise security, it is necessary to develop a strategy, determine the technologies, and the optimal way to organize your network. Here is a list of steps you can take to reorganize and centralize your company's security system.
1. Comprehensive audit: defining your security maturity and establishing the strategic goal
The first step in improving the organization's security posture is to assess your security maturity. This requires defining your organization's current security status and the necessary improvements. Once you have a clear understanding of your organization's security maturity, you can establish a strategic goal for improvement, considering that it should be specific, measurable, achievable, relevant, and time-bound. By setting a clear objective, you ensure that your enterprise is making progress toward improving its security posture.
Case in point. When conducting an independent comprehensive security audit for Bosch, Infopulse created client-specific engagement standards and technical security assessment specifications. Only after the client approved the security assessment strategy, we implemented the project that also included penetration tests and detailed technical security analysis of basic security management solutions and embedded software.
Our end-to-end security assessment services helped define the maturity of another organization's security system. The client is a leading international provider of manufacturing equipment and related services. We provided an assessment of their security program and identified gaps that needed to be addressed, based on a review of policies, risk assessments, and existing controls. This analysis revealed areas where the security posture was underdeveloped and also highlighted areas where security controls were not being enforced as intended. The results then were used to create a security risk matrix that would show which risks are ranked the highest or pose the greatest threat to the organization based on their severity and the likelihood of affecting the client.
The following section provides a more in-depth summary of the risk assessment process.
2. Threat modeling and risk matrix creation
The next stage of reconsidering your security landscape is to use threat modeling and risk assessment to define your security requirements, namely to identify potential threats and vulnerabilities and assess the associated risks . All this will allow you to design a complete security strategy that is tailored to your organization's needs.
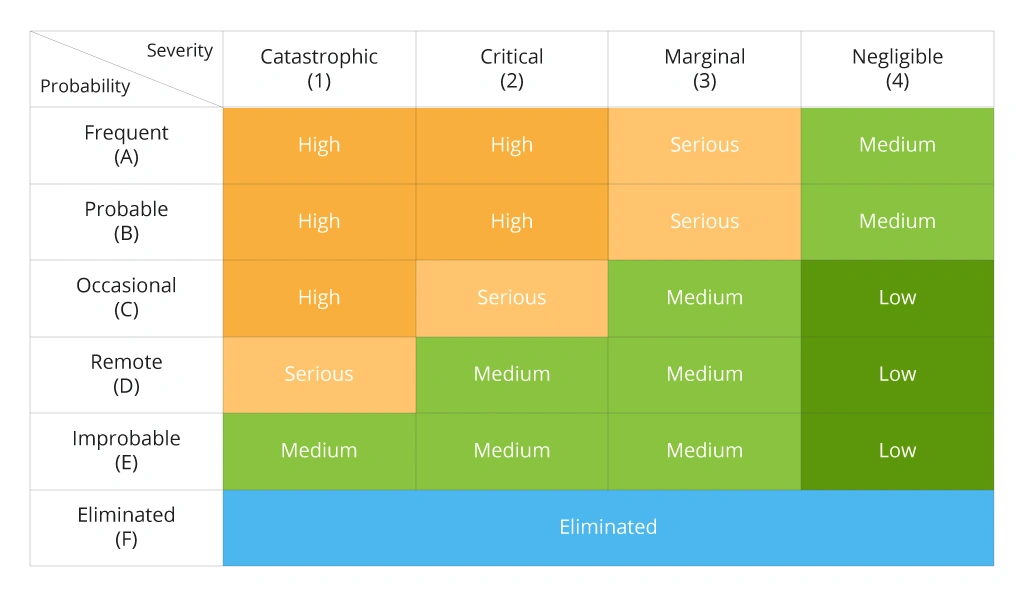
Creating a risk matrix can help you visualize and compare the potential risks to your enterprise. As a result, you will be able to identify possible security risks and develop viable strategies to mitigate them.
There is a variety of methods that can be used for threat modeling. The most common approach uses diagrams to visualize the system and identify potential threats. Other options include listing all potential threats and then prioritizing them based on the likelihood and potential impact or using a structured approach such as the STRIDE method.
Example of the Risk Assessment Matrix
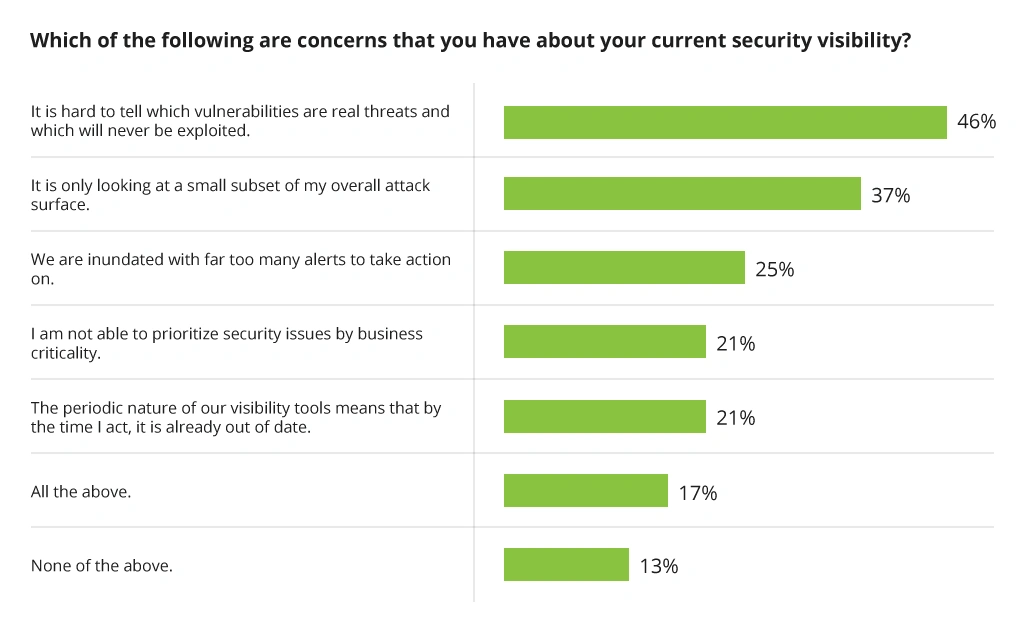
According to a cybersecurity posture report, 46% of all security specialists are unable to distinguish effectively between vulnerabilities that represent real threats and those that are unlikely to be exploited. This underscores the importance of threat modeling, which can help organizations measure and prioritize vulnerabilities based on their potential impact. The lack of security visibility leads to ineffective threat mitigation strategies and leaves organizations vulnerable to serious attacks.
Cybersecurity Visibility Challenges
When using threat models and risk assessments to define your security requirements, it is important to consider the security operations center (SOC) as part of the equation. Since SOC is responsible for monitoring and responding to security incidents, it plays a vital role in protecting organization’s assets.
3. Implementing core security solutions and security controls
When it comes to choosing the best-fitting security solutions and security controls for an enterprise, it is important to consider the specific needs and threats that the enterprise faces. That is why the previous stage — threat modeling — is significant, as it allows you to choose the appropriate tools. Since not all organizations have the same security needs, it is necessary to adjust the chosen solutions and controls to a particular enterprise.
Implementing security tools can be a complex and daunting task, but it is a critical part of protecting an organization from security threats when designing an enterprise security system. With accurate planning and implementation, enterprises can significantly lower their vulnerability to security threats.
The following components are essential for an effective security system:
1. Endpoint detection and response (EDR). Organizations today are under constant attack from sophisticated cyber adversaries. To defend against these threats, they need to continuously monitor endpoint activity and quickly identify and respond to potential threats. This is where EDR solutions come in.
EDR functions are designed to detect and respond to malicious activities on a network endpoint device, such as a laptop, desktop, server, or mobile device. EDR solutions typically work by collecting data from various systems and network events and then analyzing that data to look for patterns that may indicate a malicious activity. If such activity is detected, the EDR solution can take various actions to respond, such as blocking suspicious activity and generating an alert.
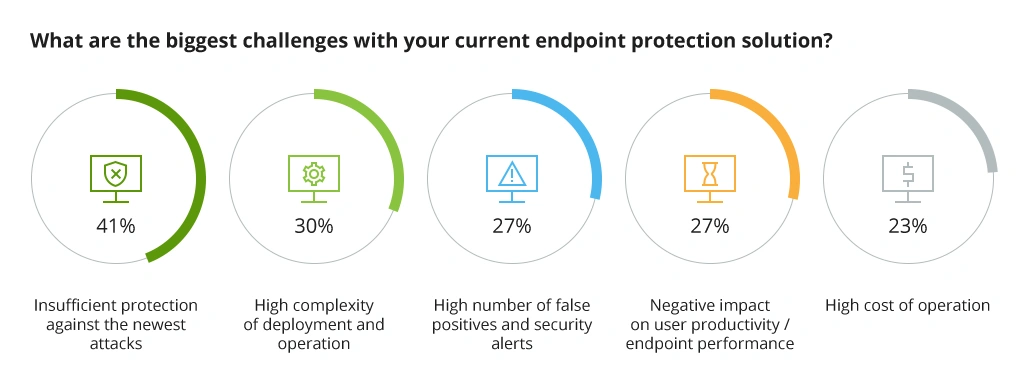
The endpoint is the network's most susceptible point because it is where data enters and exits, including malware and other security threats. Therefore, protecting endpoints is crucial, especially when devices are outside the corporate network and the complexity of attacks scales up daily. 41% of surveyed security specialists reported protection from the newest attacks as their biggest challenge with their current endpoint security setup.
Key Endpoint Security Challenges
2. Multifactor authentication (MFA) is an intermediate solution that can prevent unauthorized login attempts, particularly from compromised accounts, by requiring the user to provide a second form of authentication for account access. Today’s businesses need to put in place the necessary infrastructure to support multifactor authentication, for example, install the required hardware and configure systems accordingly to the use of multiple authentication factors.
For instance, Azure AD Multi-Factor Authentication is a great way to add an extra layer of security to your Azure AD account, as it makes it far more difficult for hackers to access it. Additionally, it can prevent phishing attacks by requiring both your password and a second factor of authentication to log in.
3. Vulnerability scanning. Vulnerability scanning helps to identify potential security risks and vulnerabilities in the enterprise security system. By conducting regular vulnerability scans, organizations can detect and fix security issues before they are exploited by attackers. This procedure also allows organizations to track the progress of their security improvement efforts over time.
To make scanning effective, security specialists refer to databases of known vulnerabilities, which are constantly updated. When a scanning solution identifies a potential vulnerability, it reports it to the user — who can then decide whether to fix it.
4. Security information and event management (SIEM) system can be a critical part of implementing core security solutions for an enterprise. SIEM provides real-time visibility into all the activity on the network, allowing security analysts to identify and investigate potential threats. Additionally, SIEM can be used to comply with various security regulations, such as PCI DSS, HIPAA, etc.
5. Security Operations Center (SOC). Implementing SOC allows enterprises to improve their overall security posture by centralizing the management of cybersecurity operations. The primary objective of a SOC is to provide 24/7 monitoring and analysis of all IT security threats, vulnerabilities, and events that affect the organization's networks, systems, or applications.
4. Leveraging the data via dashboard and analytics
The final step of centralizing a security system is to implement a dashboard — an interface through which you can see all general and statistical information on incidents and their dynamics. This allows planning actions in terms of the development of security infrastructure. A dashboard is a valuable tool for keeping track of progress and ensuring that everyone is on the same page.
As a result of centralizing data from different sources in one place, the dashboard enables a security specialist to promptly analyze the current state of the system in a single location; hence, it helps to discover problems and risks in a timely manner. More importantly, it displays information concisely, so it is easy to understand, which also facilitates the assessment of the situation by specialists.
Overall, clearly seeing the big picture of what is happening with incidents in your company helps to make better decisions about where to allocate resources.
Final Thoughts
A centralized enterprise security system considerably simplifies the administration of various cybersecurity solutions within an organization. As a result, your company receives the solid threat protection of endpoints that is particularly vital during remote work. Besides this, developing an enterprise security system also provides access to visibility and analytics, which allows your enterprise to set long-term strategic goals.
Today's relentless cyber attacks necessitate a well-coordinated, meticulously managed, and adaptable security posture. A consolidated approach to security can protect the enterprise from external threats.
Entirely unifying and centralizing security management is a prevalent strategy for fighting the flood of vulnerabilities and those seeking to benefit from them. In today's tremendously varied and complex IT enterprise settings, CIOs must rethink their approach to running their security posture to meet risk management and regulatory compliance duties with consistency.
If you are looking for effective security solutions, contact us to learn more about the ways to keep your corporate data safe.
![How to Centralize Enterprise Security System [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-how-to-centralize-enterprise-security-system.webp)



![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


