Five Signs Your Organization Needs AWS Security Hub
What Is AWS Security Hub?
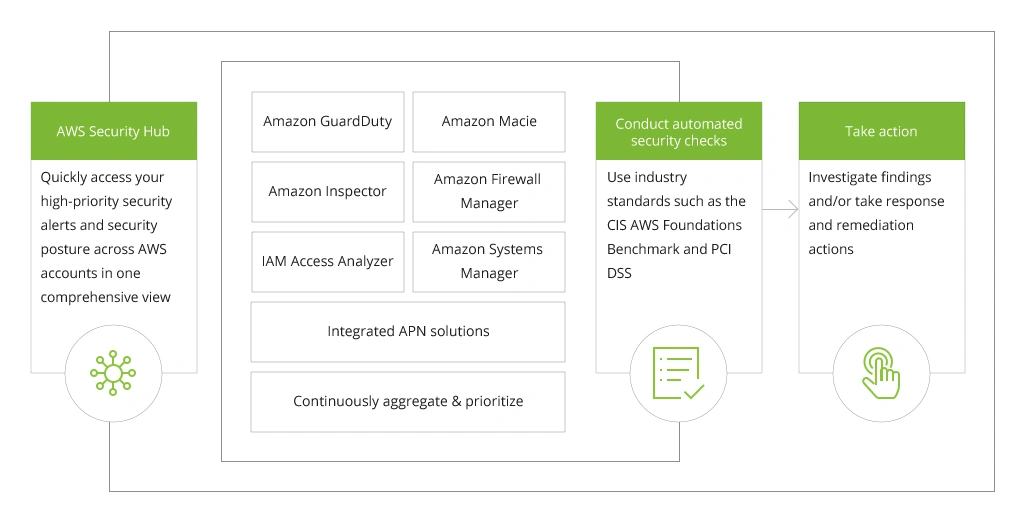
AWS Security Hub is a cloud-based security management service, which takes the role of a central place that provides a comprehensive view of your security posture and allows you to identify and prioritize areas for improvement. As a result, it helps you to protect Amazon Web Services (AWS) resources and accounts from potential threats.
How the AWS Security Hub Works?
Security Hub integrates with many other services in the AWS family of tools and services. It consolidates findings from AWS Identity and Access Management (IAM), Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS WAF and Firewall Manager, as well as information from third-party security solutions, all into a single view in the AWS Console.
Benefits of AWS Security Hub
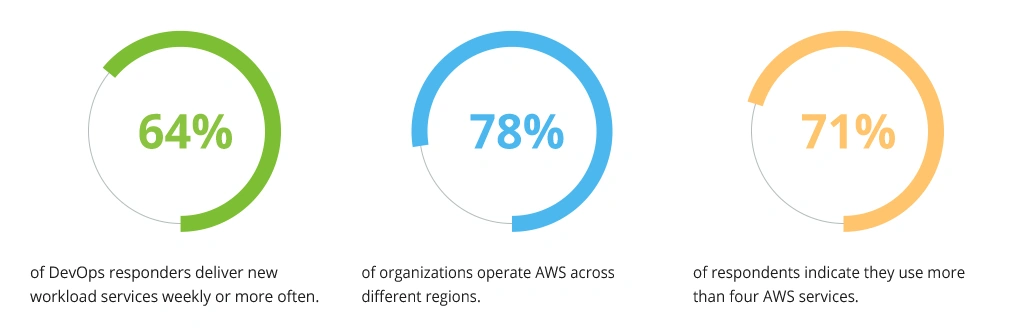
As digital transformation progresses, AWS becomes an ever-more-important component of it. Organizations deploy new workloads frequently, utilize deployments in many regions, and rely on multiple AWS services, as revealed by the survey.
AWS Usage Across Companies
Such figures are driven by the range of advantages the services offer, including the top-tier approach to security designed to accommodate organizations with various needs. Available as a standalone service or as part of the AWS Managed Services portfolio, AWS Security Hub provides proactive monitoring, assessment, and remediation capabilities to help your organization meet compliance requirements across all workloads in your account. Let’s look further into the benefits of using AWS Security Hub.
Quickly Assessing Compliance with Security Best Practices
As stated before, AWS Security Hub consolidates security-related information into a single spot. This reduces response time as you can timely identify which component is failing and take immediate action to resolve the issue.
With AWS Security Hub, you can:
- View the overall security state of all your accounts in one place — and drill down into each account to see how it is affected by any specific threat;
- Identify compromised accounts by comparing the predicted risk of an account with its actual risk score;
- Reduce false positives by filtering out a known good behavior (such as normal user activity) that might otherwise trigger alerts.
Improving Security Posture
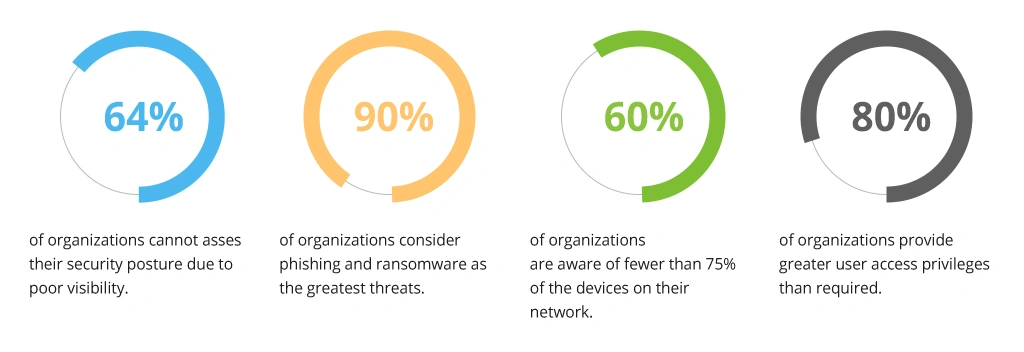
According to the 2020 State of Enterprise Security Posture Report, cybersecurity teams are having trouble keeping track of threats, endpoints, access rights, and other crucial security controls needed for a strong cybersecurity posture.
- 64% of organizations lack confidence in the current level of their security posture because of poor visibility.
- 90% of organizations believe that phishing and ransomware pose the greatest threats to their organization, while just 50% have adequate visibility into these challenges.
- 60% of organizations are aware of fewer than 75% of the devices on their network. It is difficult to strengthen the security perimeter due to this lack of asset awareness.
- 80% of organizations provide greater access privileges than are required for users to perform their tasks, with 17% claiming that most users have excessive privileges.
State of Enterprise Security Posture
AWS Security Hub provides organizations with just the right set of tools to diminish the informational disarray and achieve the desired level of transparency and visibility into their IT infrastructure. At the same time, it reduces the risk to expose companies’ assets by elevating security practices through automated threat detection and investigation.
Reducing Human Error by Automating Security Tasks
One of the core values of Security Hub is reducing the amount of human error in your security operations. It automates many of the tasks security analysts would otherwise have to do manually. For example, Security Hub can automatically run security checks and generate reports on your AWS environment. This can help free up your security team so that they can focus on more strategic tasks, all the while reducing human error and alarm fatigue among the personnel.
Automation within Security Hub allows avoiding costly breaches or malicious activities: for instance, if an employee accidentally clicks on an attachment that contains malware without being aware of it (or because they were tricked into opening it), this could result in an attack that compromises sensitive data stored within their organization's systems. In such cases, AWS Security Hub can automatically detect an attack against your data by collecting information about activities occurring across multiple services at once and analyzing them against known patterns associated with cyberattacks like phishing emails or malware installations).
Providing Easier Collaboration
AWS Security Hub simplifies the distribution of security-related information among your specialists. Your team members can join the security center with just a few clicks, and they will be able to access all the security information you have gathered. This facilitates the resolution of security issues and ensures that everyone is on the same page regarding safety.
Signs you need AWS Security Hub for Your Organization
There are various indicators that the AWS Security Hub is something your company needs to implement. They largely depend on your organization's requirements, but there are also some common scenarios where this service will be useful.
1. Your organization has a geographically distributed infrastructure
If your company operates in multiple regions and uses multiple AWS accounts, you can use AWS Security Hub to gather security data from all of your accounts, giving you a comprehensive view of your organization’s overall security posture. Managing everything from a single place saves time and money compared to having a different hub for each location.
2. You do not have CISO in your organization
When an organization lacks a chief information security officer (CISO) to manage its infrastructure, it can use the Security Hub to get a security perspective on the entire landscape in one place. This allows the organization to see the situation from a bird's-eye view and determine the best course of action. A Security Hub can also be used to establish guidelines for management and create an agenda for immediate tasks.
3. Your organization has to follow security standards
Security Hub is an excellent tool to standardize your security policies and procedures. It provides you with a central place to manage all your security information, which ensures that everyone in your organization follows the same security procedures.
Using AWS Security Hub, you can stay in compliance with the applicable regulations and standards that govern your business, such as PCI DSS, HIPAA, GDPR, and ISO 27001.
4. Your organization has experienced a rapid growth
AWS provides a great way to level out your infrastructure from the perspective of an information security analyst. When your company's infrastructure expands rapidly, it can be difficult to keep up with the security needs of all the new locations. However, with the AWS Security Hub, you can effortlessly monitor and manage security for multiple accounts.
5. Your day-to-day tasks consume too much time
If day-to-day security tasks take far too much time and attention, AWS Security Hub is an effective approach to automating those tasks while also helping you to detect potential issues at scale. Using AWS Security Hub, you can automatically respond to vulnerabilities that are discovered by continuously monitoring your apps for potential problems using a set of monitoring rules. You can also use AWS Security Hub to detect threats that may not be visible enough by using machine learning models and streamline the process with workflow templates.
How to Select Data to Feed to AWS Security Hub
AWS Security Hub is a powerful tool for security analysis and monitoring, but it can only be as effective as the data that is fed into it. When selecting data to source for Security Hub, it is important to consider the types of data that will be most useful for the types of analysis you wish to perform.
For instance, if you are interested in identifying potential security threats, you have to select data sources that provide information that could be indicative of malicious activity. This might include data from your network security logs, web server logs, application logs, and so on.
On the other hand, if you are primarily interested in compliance monitoring, you can select data sources that provide information regarding compliance, like AWS Artifact, audit logs, Access Control Lists (ACLs), and so on.
AWS Security Hub collects data from different services, integrated third-party products, and from the following AWS services:
- AWS CloudTrail
- Amazon VPC Flow Logs
- Amazon CloudWatch Events
- AWS Systems Manager (together with Data Sync Manager)
- AWS Config Rules (including changes to IAM roles)
AWS Security Hub can be provisioned with just a few clicks from the CloudFormation template provided by AWS. The best way to get started using this application is by learning how it works so that you can customize its settings for better use within your organization's environment.
How to Customize AWS Security Hub
Besides keeping your AWS environment secure, AWS Security Hub can be customized to fit your specific needs. By leveraging the power of machine learning algorithms, the service can automatically recommend AWS Security Hub best practices for improving security across your account's most important services.
You can also tailor these recommendations based on different roles within your organization or individual preferences — for example, by tightening permissions for one group while loosening them for another so they can access sensitive data without compromising its availability within the organization.
You can set up rules to detect and investigate incidents, then receive notifications when suspicious activity occurs.
Here are some tips on how to customize the AWS Security Hub:
- Identify the security risks that are specific to your AWS environment. This can include risks related to your industry, geographic location, or company size.
- Choose the AWS Security Hub features that will help mitigate these risks. For example, you might enable integration with third-party security tools, enable real-time monitoring, or set up alerts for suspicious activity.
- Configure the AWS Security Hub settings to match your company's security policies. This can involve specifying which users have access to the tool, what kinds of activity they can see, and how long data is retained.
By following these steps, you can ensure that AWS Security Hub is tailored to your company's specific needs and risks. This will help you keep your AWS environment safe and secure.
To Conclude
As you can see, the AWS Security Hub is an extremely valuable tool. It can help you stay on top of your security and make sure you are protected from variable threats within your environment. The ability to customize it to meet your needs makes it even more useful.
If you are looking for a single view of your AWS environment security and compliance, Security Hub is the right solution for you. With real-time dashboards, automated alerts, and easy access to reports on all your AWS resources, it helps you identify issues faster without having to leave the AWS console.
![Why Use AWS Security Hub [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-why-use-aws-security-hub.webp)

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


