Enterprise Guide to Security Automation: How to Select the Right Processes and Automate Them
Similarly, the size of the IT infrastructure portfolio businesses operate has expanded. From migrating critical data from on-premises to the cloud to establishing digital workplaces, leaders now have a longer defense perimeter to guard — but often not enough people to do so. To protect effectively all the company’s assets, the global security workforce needs to grow by 65% in the short-term perspective.
However, the crippling rates of cybercrime require immediate action. Many businesses are now considering security automation to complement their existing cybersecurity workforce and improve their security posture.
Security automation assumes methodical automation of common security actions — monitoring, assessments, and investigations — with the help of software solutions such as Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) tools, as well as other process automation solutions.
The purpose of security automation is to act as a force multiplier: streamline mundane repetitive security assessments and give your security people more headspace to investigate and remedy actual incidents.
3 Cases When Enterprises Choose to Automate Security
Rather than being a standalone solution, security automation is a collection of tools and best practices you employ across specific use cases. You can achieve end-to-end automation of certain security processes — or only automate one of its segments. In both cases, however, automation results in improved quality, efficiency, and cost of your cybersecurity defense.
We have identified three common security outcomes businesses want to achieve and a range of automation scenarios that can lead to these outcomes.
Outcome: Faster Response Time to Common Threats
The volume and vectors of attacks have grown more elaborate. However, businesses most often fall prey to the same types of simple attacks such as:
- Phishing emails
- Ransomware attacks
- DDoS attacks
- Botnet-based spam
- Malware distribution
- SQL injections
- Zero-day exploits
- Password brute force attacks
- Man-in-the-Middle (MitM) attacks
All of the above are relatively easy to orchestrate as cyber-offense tools are easily accessible. Plenty of “for-hire” services also operate at a low cost. Because of these factors, cyber-attacks have increased in volume and regularity. Most hackers today use a “spray and pray” approach — target as many victims in order to locate a “weak link”.
On the response side, each type of attack requires a specific multi-step security process for assessment and remediation. For example, to analyze a phishing attempt manually, a security specialist has to:
- Review the alert
- Extract URLs, IPs, domains, attachments, etc.
- Run a scan to verify documents/URLs.
- Escalate the ticket if malicious content was found.
- Determine if the user interacted with the asset.
- If the user’s security was breached, decide on the next steps.
When done manually, each of such assessments and subsequent remediation takes a lot of time and attention away from more complex (and likely threatening) issues.
For comparison, a SOAR platform can automatically assess the status of an incoming email and its contents — scan URL, assess host, investigate the connection, and so on — to classify its reputation in a matter of seconds. Such solutions can also scan over hundreds of alerts a security analyst faces daily, prioritize the most important issues, and apply auto-heading towards the regular ones.
Microsoft Sentinel — a dual SIEM/SOAR platform — is estimated to reduce over 79% in labor efforts spent on issue investigation. This further leads to an 80% reduction in mean-time-to-repair and up to $2.2 million in efficiency gains for enterprise-sized organizations.
Recommended security automation use cases:
- Prevention of mass-phishing
- Malicious communication blocking (internal and outbound)
- Malware blocking and prevention
- SIEM escalation
- Events risk scoring
Outcome: Improved Security Team Performance
Slow response time to common threats also stems from the overwhelming volume of alerts. Having more technical assets to guard, security analysts at the frontlines (L1/L2 specialists) often struggle with conflicting priorities.
A 2022 report by SonicWall states that over 78.4 million ransomware attacks took place in June 2021 alone. Throughout the year, the volumed of encrypted threats increased by 167% (to 10.4 million attacks) and cryptojacking spiked by 19% — to 97.1 million attacks. Thus, analysts are often bogged with multiple alerts and pressed to respond rapidly to multiple attack vectors.
Cisco survey further states that over 42% of cybersecurity specialists admit to suffering from alert fatigue. Among the overwhelmed teams, 93% have to deal with over 5,000 alerts per day. The overall dynamics of daily alert volumes are uneven as well.
Reported Number of Received Alerts
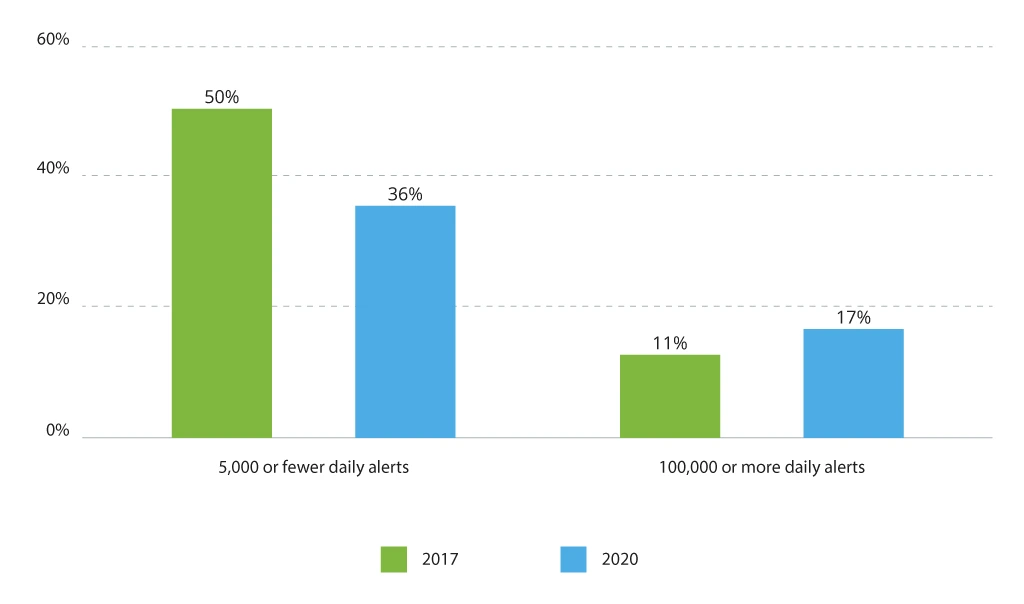
Security automation solutions can help curb the volume of alerts through smart triage and progressive escalation. You can codify policies to ensure that only the most crucial issues are escalated to senior security staff (L3 and above) who are on call. At the lower levels, automation can (and should be) employed towards repetitive, routine, and mundane tasks of lower priority that L1/L2 analysts cover.
Recommended security automation use cases:
- IP blacklisting
- Malicious accounts blocking
- User account unblocking
- Spam filtering
- Password reset
- User credential verification
- Quarantining devices
- Deleting or quarantining malware-infected files
- Endpoint analysis
Outcome: Streamlined SOC Operations
Security Operation Center (SOC) stands at the vanguard of preventive security. The unit’s job is to proactively identify weak areas and possible attack vectors and implement better protection mechanisms. Apart from infrastructure assessments, monitoring, and optimization, SOC specialists can also perform more sophisticated threat hunting, collect threat intelligence, and develop new security policies.
An integrated SOC and NOC team covers events/incidents monitoring, identification, and remediation across a wider set of assets — local and cloud-based infrastructure, networks, and edge devices.
It goes without saying that SOC teams cover a lot of assets and therefore have to receive security telemetry from different sources. In practice, however, many organizations struggle to achieve full visibility into their technical estate, which leaves them blind-sighted to possible attack vectors.
Low SOC maturity also often manifests in data silos and a lack of streamlined practices (playbooks) for responding to common events. Once again, without proper processes and tools, the team struggles to ensure a fast and consistent response.
Security automation can help coax clarity out of the process chaos that less mature SOC teams face. By methodically applying process automation and AI/ML capabilities of modern SIEM/SOAR solutions you can standardize your response scenarios to common and novel threats, improve the quality of incoming security intel, and introduce adaptive controls for all infrastructure.
As Anton Chuvakin, former Research VP and Distinguished Analyst at Gartner and current Security Solutions Strategy Specialist at Google Cloud, well noted:
Recommended security automation use cases:
- Automated incident detection
- Correlation rules improvement
- Data enrichment
- Role-based alerts triage
- Automated alert validation
- SLA policy monitoring
- Tickets prioritization and routing
- Security reporting automation
- Data lifecycle management
- Asset management
Common Blockers to Security Automation Implementation
An impressive 98% of companies plan to automate more of their cybersecurity processes this year. However, a significant gap often lies between aspiration and execution. Though cloud-based SIEM/SOAR solutions come with nearly effortless installation, especially when compared to legacy tools, the devil is often in the details.
Security process automation requires a deep understanding of the current infrastructure, available data sources, and correlation rules, signalling likely events. A lot of teams still have operational gaps in security — such that no tool can cover. By design, not all security processes are strong contenders for automation. Neither can certain SOC roles be fully replaced with tooling.
Our experience as a managed SOC provider has helped us to identify several common barriers to automation.
Insufficient Budget
Many organizations experience a “sunk cost fallacy” when it comes to retiring legacy SOAR/SIEM solutions. At the same time, many IT budgets are tied elsewhere. Gartner found that in 2020, security accounted for just 5.7% of the total IT spending in larger organizations. That is hardly enough. At the same time, high in-house SOC maintenance costs also deter smaller-to-mid-market companies from investing in security.
Soundly, you have alternatives. Cybersecurity tools like Microsoft Sentinel and various Microsoft Defender editions come with flexible pay-as-you-go or volume-based subscription costs. The monthly spending can be further optimized as well. You can also opt for alternative SOC adoption strategies — a managed SOC unit or “SOC-as-a-service” offering.
Irregular Events
Though many businesses are attacked by the same set of trite breach attempts, occasionally a more elaborate threat can emerge on the radar. Security automation solutions can alert of anomaly detection. Yet, you will then need threat intelligence experts to investigate its origins, impact, and perform remediation.
Similarly, if you operate a complex infrastructure of connected IoT/edge devices, your SOAR workflows will be more elaborate and unlikely suitable for end-to-end automation. Therefore, you should first attempt to automate monitoring and responses to regular security use cases. Then look into more advanced use cases.
Lack of Competency
With the cybersecurity talent shortage, many organizations do not have enough people on board to cope with the volume of security tasks. Less than half of companies employ a Chief Information Security Officer (CISO) — and 60% rely on IT, executive, or compliance teams for guidance in security matters. The lack of strong security leadership and domain expertise means that many security processes are ad-hoc, rather than documented, with both technical and operational gaps present.
In such cases, obtaining our external cybersecurity expertise for general advisory, as well as subsequent function establishment paired with service delivery, is the best plan of action.
Conclusions
Any type of automation — security or otherwise — should be implemented with careful planning. Indeed, modern SIEM/SOAR solutions can bring value to any security team. However, the ROI will strongly depend on how well you match the automation priorities to the teams’ needs, infrastructure size/type, and compliance requirements. Start with a shortlist of simple use cases — repetitive, low-value processes. Then work on consolidating your security reporting and data sources to enrich the incoming intel. Once this base is set, switch to the next collection of security processes, worth automating.
Contact Infopulse cybersecurity team to further discuss different strategies for security automation and approaches to managed services delivery.
![Guide to Security Automation [banner]](https://www.infopulse.com/uploads/media/enterprise-guide-to-security-automation-1920x528.webp)
![SOC eBook [promo banner]](/uploads/media/free-ebook-security-operations-center-soc-280x183.webp)

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


