Data Protection as a Business Driver: Key Benefits and Best Practices
Data security has always been an everlasting issue for organizations, and this year is no exception. In 2023, data breaches cost an average of $4.45 million globally, which constitutes a 15% increase over the last three years. As a result of this, 51% of companies plan to expand their security budgets.
Every organization that collects, processes, and stores sensitive data to some extent, is not immune to data loss, theft, misuse, or corruption. That is why there is a harsh necessity for data protection. What makes up a good data protection investment? How can a solid strategy save you millions of dollars? What are the steps for the successful implementation of protection practices? Read on to find the answers.
What is Data Protection?
Sometimes such notions as data protection, data privacy, and data security are used interchangeably, but there is a clear difference between them. Data privacy defines who has access to personal health information (PHI) and personally identifiable information (PII), while data protection represents a set of strategies, processes, practices, and tools to safeguard that information in the event of data loss or damage.
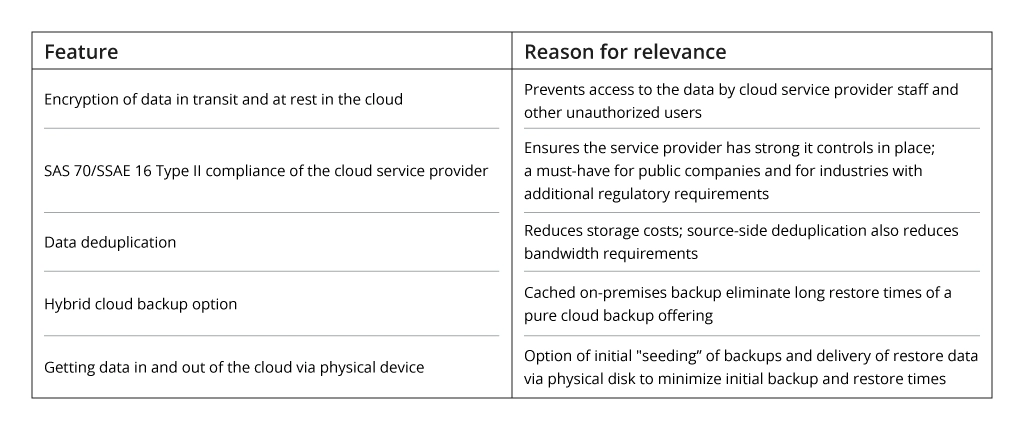
Conversely, data security is aimed at protecting from unauthorized access not just personal data, but all types of information despite its origin and owner, whether it is a physical person, a legal entity, or a corporation. Organizational policies and procedures, hardware and storage devices, administrative access controls, enterprise-grade software applications — data security covers these key components. Here is a comparative table to better explain how data protection differs from data security.
.webp)
The key principles of data protection are stipulated by the General Data Protection Regulation (GDPR), which defines standards for data collection and processing and imposes the toughest obligations and fines for their violation. This EU’s data protection law was enforced in 2018 and since then has changed the way personal data should be treated not only in Europe but also around the world. The need to safeguard consumer data came to the limelight and many countries (the U.S., Canada, Japan, South Korea, etc.) updated their archaic data privacy acts/laws trying to mirror GDPR’s key principles:
- Transparency: companies are open about all their data practices, i.e., individuals should be aware to what extent and how their data is collected, processed, and shared
- Collection and purpose limitation: personal information must be gathered in a limited manner; with an individual’s knowledge and consent; and the purpose of data gathering and disclosure must be specified at the time of collection
- Integrity and confidentiality: data controllers are allowed to use the data provided they ensure appropriate security safeguards and confidentiality
- Data minimization: personal information processing and storing should be limited to a closely related purpose and period of time
- Storage limitation: personally identifiable information (PII) is only kept as long as is necessary, within established time limits
- Accuracy: controllers ensure that an individual’s data is accurate, relevant, and up-to-date
- Accountability: all data protection principles should be in strict compliance with the GDPR and DPC
Data Protection as an Evergreen Trend
Poor data protection does not only negatively affect a company’s reputation and bottom line, but also hampers efficiency and productivity. For example, a report by Evidon found that 70% of the surveyed site operators had been affected by third-party marketing techs running on their website without knowing that. This led to serious performance glitches for 80% of websites and 57% feared they might have to deal with data leaks.
Another reason why data protection is also of such great importance is the introduction of multiple privacy laws and regulations that are obligatory to comply with, including:

As enforcement of data protection laws increases and shows no signs of abating, companies should also attain data protection certifications that are relevant to their business. Some of the most essential ones are:
- CIPT: Certified Information Privacy Technologist
- CIPP/E Certification: Certified Information Privacy Professionals, Europe
- CDPP: Certified Data Privacy Professional
- HCISPP: HealthCare Information Security and Privacy Practitioner
- CDPSE: Certified Data Privacy Solutions Engineer
These rules, laws, and regulations stipulate specific practices companies should adopt to ensure data privacy. One of them is implementing a data protection management system (DPMS). Such a solution comprises legal and operational requirements for data protection and automatically manages them to ensure full compliance. The advantages of using a DPMS include protecting valuable personal information around business transactions and financial statements. This means increased confidence in consumers who purchase or use other services online, and in turn boost revenue.
How to Protect Data: Top Practices and Solutions
Now that we have delved into what data protection is and why it is important, let’s discuss the most useful data protection management practices.
Data Loss Prevention Solutions
Named shortly DLP, data loss prevention solutions are built to identify, monitor, and secure sensitive personal data from theft, loss, and other invasive forms of contact. In essence, such systems prevent breaches by continuously scanning and analyzing data at rest, in use, and in motion across email, cloud storage, network file shares, and endpoints. When a potential threat is discovered, instant alerts are generated and sent to IT administrators, while files with the most critical data are blocked.
DLP solutions also activate automated tagging to classify data according to specific risk scores, restrict end devices from viewing and complying specific data, as well as permit data sharing only among trusted devices.
To develop a comprehensive approach to data loss prevention, we recommend building SOC as one of the most effective approaches to data protection.
For example, the use of a robust Security Operations Center (SOC) helped a Swiss manufacturer identify main data risks, establish a data protection strategy, implement and perform continuous monitoring of data protection status, and incident response. As a result, the client notably reduced the risk of data breaches and cyberattacks, detected and resolved 500+ security incidents on a monthly basis, and enabled 24/7 vulnerability scanning across multiple branches.
Encryption Techniques
A report by Statista states that during the first quarter of 2023, over 6 million unencrypted data records were compromised worldwide due to data breaches. Poor encryption also leads to lengthy recovery timelines after the data is leaked, as much as 287 days or even more. Moreover, enterprises could save an average of $1.4 million in ransomware payments for each attack by reinforcing their encryption practices.
It is recommendable to encrypt all data, while they are both at rest and in transit. The algorithms used to encrypt data include AES, RSA, Triple DES, and Twofish. They perform differently depending on the data type and infrastructure, so be sure to choose the optimal one to serve your needs. An adept data protection services provider will help you accomplish this as well as implement the best encryption practices. These include:
- Full disk encryption (FDE) encrypts the entire content of a device at the hardware or software level to prevent unauthorized access. A user can unlock the device with a password, a PIN, or a biometric authentication
- File-level encryption (FLE) safeguards individual files or folders, providing more granular control over data access. You can integrate FLE practices in your access control policy for more efficiency
- Protocols such as HTTPS, SSL, TLS, and SSH encrypt data in transit by creating a secure channel between the data sender and receiver
- Virtual private networks (VPNs) protect data in motion across multiple devices or networks by leveraging encryption, authentication, and tunneling protocols.
Regular Check or Verification of Access Rights
It’s essential to build a process that will allow monitoring users' roles and rights, how often he uses them, and how they are related to his work. This would also allow revoking access to specific infrastructure objects when such access is no longer needed (e.g., a user has changed the position within the company), or the access is no longer compatible with the user’s position, or his privileges have increased.
Revocation of access rights is a crucial measure to exclude broken access permissions that often lead to information leaks, especially when it comes to insiders.
In this case, the reason behind such data leakage is not the choice of solutions but improper organization of access management process.
Data Backups
Stats say that 97% of ransomware attacks are focused on infecting primary systems and backup repositories. It stands to reason that implementing an effective backup strategy at your enterprise is of great importance. This includes a 3-2-1 strategy: storing at least three data copies on at least two different storages (in a separate physical disk, in the cloud) — one of them off-site.
Among other practices: increasing backup frequency, aligning backups to service-level demands, and making the most of cloud backups.
A case in point: Infopulse helped a Nordic software development company reinforce the security posture for their transportation services client through the powerful mechanisms of round-the-clock threat detection and data backup & recovery. Timely security issues resolution with 24/7 L3 support helped the company notably increase end-customer satisfaction.
Disaster Recovery as a Service
According to the IT Outage Impact Study by LogicMonitor, 96% of IT decision makers worldwide dealt with at least one outage in the last three years. Moreover, organizations with frequent outages suffer from 16x higher costs than those with less downtime. These stats make it clear that a robust disaster recovery strategy is a must-have in today’s business climate.
For this, we recommend implementing Disaster Recovery as a Service (DRaaS). It is a cloud-based model that enables enterprises to back up its entire data centers, systems, and IT infrastructure in a third-party cloud environment and restore them in case of a disaster. In a managed DRaaS, a third-party vendor takes full responsibility for continuous data replication, maintenance of a disaster recovery environment, and an organization’s normal operation renewal — sparing you the effort and money for establishing and provisioning your own off-site environment.
Copy Data Management
When preparing backups, enterprise applications might create multiple copies of the same data. These redundant copies reduce storage space and negatively impact network performance, in turn, making it burdensome to further restore mission-critical data.
A copy data management (CDM) approach can help you eliminate unnecessary duplication of the production data through virtualization. By automatically erasing extra copies, you can speed up application release cycles, enhance productivity, and slash maintenance and storage costs, as well as ensure greater compliance.
Looking for more innovative approaches to ensure the stellar security of your data and further enable the digital transformation of your organization? Check out our free ebook!
Conclusion
Data protection is quite a complicated process that requires detailed planning, expert implementation, and substantial financing. One wrong move — you damage your reputation, experience outage, and lose money. That is why it seems reasonable to outsource this huge amount of work to an experienced security expert and focus more on your key business processes. Such a third-party company will provide a full IT audit, build a tailored data protection strategy, implement the most effective security tools and practices, and provide continuous support.
![Main Benefits and Best Practices of Data Protection [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-data-protection.webp)

.webp)

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


