DDoS and DNS Attacks: Common Security Questions Answered for Businesses
What is a DDoS Attack?
DDoS (distributed denial-of-service) attack is a targeted action aimed at overwhelming a server, network, IoT gadget, service, or its surrounding tech infrastructure by directing high volumes of traffic towards the target. The end goal is to boggle the exploited system’s operations until it becomes inoperable.
Compared to other types of cyberthreats, DDoS attacks are easier and cheaper to orchestrate. Dark Web Price Index 2020 indicates that a 1-hour DDoS attack can cost as low as $10. On top of that, a lot of basic DDoS attacks are generated by amateurs who use variations of publicly available Mirai botnet code. To some extent, this is the reason behind the growing volume of DDoS attacks today. According to NetScout report:
- Some 8.4 million DDoS attacks took place in 2019. That’s 670,000 attacks per month or 23,000 attacks per day.
- Telecom security is suffering in particular. DDoS attacks on mobile operations increased by 64% in 2019 and the growth remains as steady in 2020. In addition, the frequency of attacks on satellite communications jumped by 295%.
- The costs of DDoS attacks are also rising: small businesses could lose $120,000 on average from a single attack, whereas for enterprises the costs can surpass $2 million.
Considering their popularity, DDoS attacks often become the first critical indicator for businesses, signifying that their network security needs hardening.
How Does a DDoS Attack Work?
Here’s what happens during a DDoS attack:
- The end goal of a hacker is to overwhelm their target with incoming traffic.
- To accomplish that, they use a botnet – a network of devices (computers or IoTs), infected by malware.
- Once the botnet is active (created or purchased), the attacker sends remote instructions to each bot to launch the attack on a selected target.
- Then, each bot starts sending multiple requests to the target’s IP address at a fast rate to overwhelm their networking resources.
- As a result, your application becomes unavailable as it cannot handle the traffic load.
Since each bot is hard to distinguish from a legitimate device sending normal traffic, identifying the early signs of DDoS attacks can be challenging.
Common DDoS Attacks Types
While the basic mechanism of the DDoS attack stays the same, individual attacks can vary in the level of sophistication, depending on which layer of the Open Systems Interconnection (OSI) model they target, as represented on the infographics below.
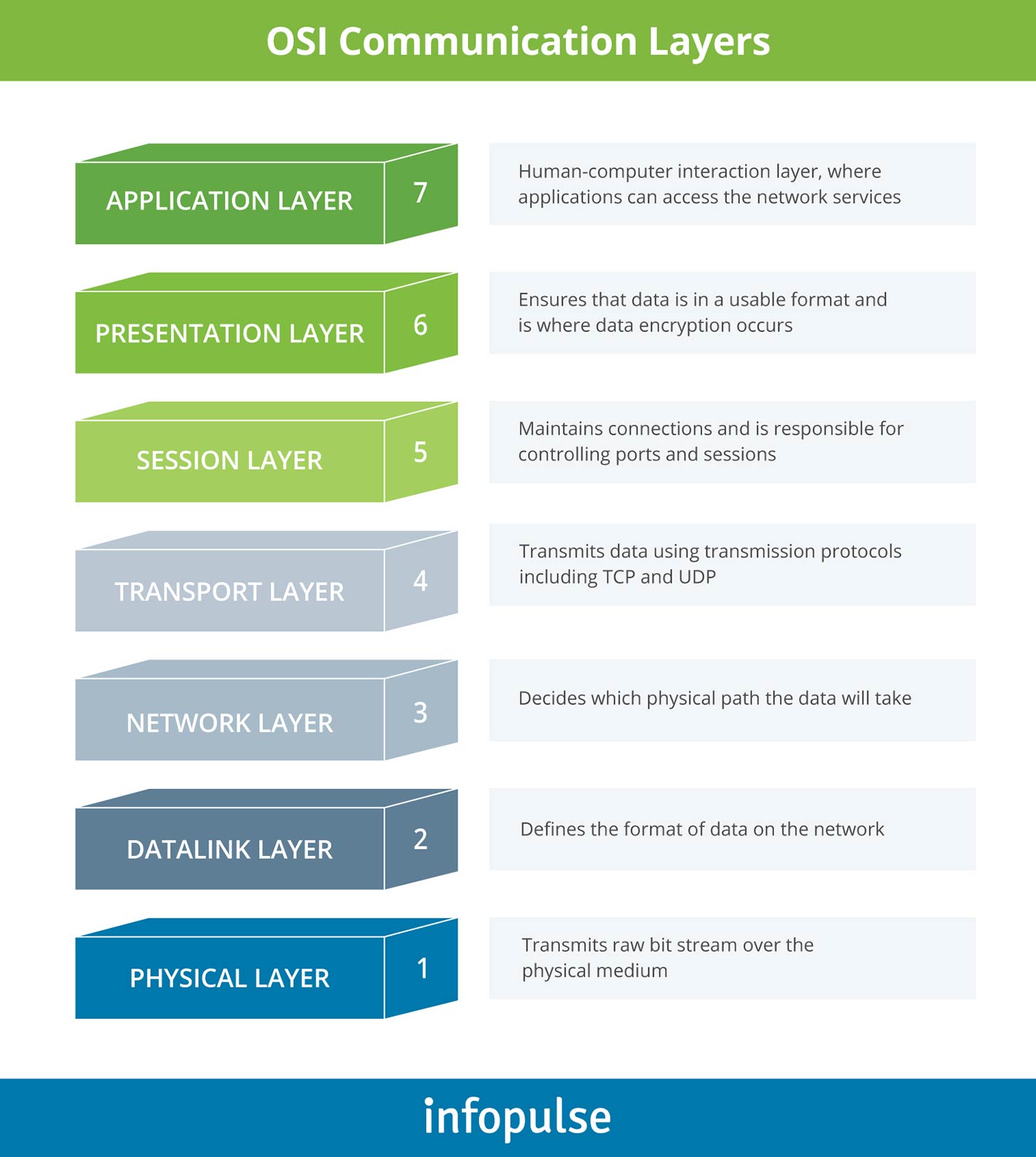
Let’s review some of the most common attack types.
Application Layer (Layer 7) attacks are targeted at overwhelming the layer, responsible for generating web pages on the server and delivering them in response to HTTP requests. The end goal is to deluge the server with a huge volume of requests per second. This type of attacks includes:
- Attacks targeting Windows, Apache, or OpenBSD vulnerabilities;
- GET/POST flood attack types;
- Low-and-slow attacks.
Protocol attacks leverage weaknesses in Layer 3 and Layer 4. Also known as state-exhaustion attacks, these malicious acts are aimed at over-consuming server resources and/or intermediate communication equipment resources such as firewalls and load balancers. Common types of attacks are:
- SYN floods;
- Ping of Death;
- Smurf DDoS;
- Fragmented packet attacks.
Volume-based attacks attempt to saturate the bandwidth by sending large volumes of data to the target using a botnet. Popular attack types are:
- DNS amplification;
- UDP floods;
- ICMP floods;
- Other types of spoofed-packet floods.
Multi-vector DDoS Attacks feature multiple attack pathways, targeted at different layers of the protocol stack, to create an even greater sense of overwhelm and disperse DDoS attack prevention efforts that are thrown against them.
How to Stop a DDoS Attack?
Stopping a DDoS attack in its tracks is more challenging than preventing it from happening. However, if your systems are under ceasefire, our cybersecurity specialists recommend deploying the following response tactics:
- Implement bandwidth overprovisioning to win extra minutes once the attack has started.
- Create a blackhole routing mechanism to funnel malicious traffic.
- Or set up a redundant network architecture to roll-over fast.
- Activate rate limiting on your router to prevent servers from further overwhelm.
- Report a DDoS attack to your ISP/Host so that they can immediately block the malicious traffic/packets. Every provider has specific instructions on how to report a DDoS attack in progress.
How to Prevent a DDoS attack?
The best method of DDoS attack protection is proactive prevention. Remember: there are many amateurs among attackers and their actions can be easily counteracted with the appropriate IT infrastructure protection mechanisms in place. In particular:
- Ensure that you have properly configured firewalls and/or Access Control Lists (ACLs) to monitor what traffic enters your applications.
- Set up Load Balancers, content filtering, DNS resolution centers, and Content Distribution Networks (CDNs) to better handle the incoming traffic load.
- Introduce a packet capture mechanism to monitor and analyze incoming transfers. Modern tools can be configured to check specific fields in the packet (e.g., destination IP, length, protocol, etc.) against baseline measures to identify early signs of DDoS.
- Fully restrict direct web traffic from penetrating sensitive parts of your infrastructure (e.g., database servers).
- Implement continuous traffic monitoring with advanced technologies for anomaly detection.
- Perform regular network security assessments to further strengthen your security posture, using the latest best practices.
What is a DNS Attack?
A DNS attack targets the availability and/or stability of a network’s Domain Name System (DNS) service to subvert the answers it is providing. In short, hackers attempt to deviate the incoming traffic from a legit resource towards a malicious property.
Since DNS is the underlying component for processing all Internet requests, DNS server attacks are rather frequent. According to the Global DNS Threat Report 2019:
- Per year, a company faces 9 DNS attacks on average – 34% more than the year before.
- One in five businesses lost over $1 million per DNS attack due to app downtime, business downtime, and compromised services.
- Along with financial losses, 26% of companies lost brand equity.
As the data further shows, DNS attacks today are nowhere close to losing popularity. On the contrary, their level of frequency and sophistication keeps expanding.
The Most Common DNS Attack Types
Over the years, hackers have found different ways of tampering with the DNS records and exploiting flaws in the implementation of the DNS protocol among businesses. These actions result in the following types of attacks:
- DNS tunneling assumes the usage of other protocols such as SSH, TCP, or HTTP to tunnel through DNS queries and responses. The goal is to pass malware to or siphon sensitive information from your systems in a bypass of most firewalls.
- DNS spoofing (also known as cache poisoning) is an attack staged to inject spoofed DNS data into a DNS resolver’s cache so that it returns an incorrect IP address for a domain. In essence, the hackers attempt to re-route traffic from the correct website to a malicious property to steal sensitive user information or distribute malware. Such DNS security attacks are particularly harmful as when left undetected, they can have a long-term impact on your operations.
- DNS hijacking follows a similar attack pattern as the previous hack. The difference is that the attacker goes after the website’s DNS record on the nameserver, instead of the resolver’s cache. Their goal is to redirect queries to another domain name server by using malware or by performing unauthorized modifications of a DNS server.
- Phantom domain attack is aimed at orchestrating a denial-of-service event. The attacker creates a hub of malicious ‘phantom’ domain servers. Then, the resolver receives a huge volume of requests for these domains. Since they are programmed for a slow-to-no response, the resolver becomes bogged down and eventually, inoperative.
- Random subdomain attack is another sub-type of DNS flood attack, aimed at overwhelming the domain’s nameserver. To accomplish that, the hacker sends multiple DNS queries for several random sub-domains of a legitimate target website.
How to Prevent DNS Attacks
Similar to DDoS, DNS security should be proactive rather than reactive since most attacks come as a direct result of business negligence. To mitigate the risks, you should implement the following DNS security best practices:
- Conduct regular DNS audits. Ensure that your main DNS server is properly configured, in line with the latest recommendations from your provider. Regularly review your DNS zone to locate the abandoned test (sub)domains that may contain potential loopholes vulnerable to an attack. There are plenty of DNS security tools on the market that auto-scan all A, CNAME, and MX records, plus audit public zones, records, and IPs.
- Consider enabling DNSSEC. DNS Security Extensions is a newer security protocol that addresses inherent security limitations in DNS systems. It was designed to introduce a special digital signing policy across all layers of DNS that helps ensure its validity during the DNS lookup process. DNSSEC can help you protect the most sensitive data and definitions stored in the DNS and prevent data exfiltration performed via DNS – a common mechanism that attackers leverage. Ask your TLD to provide you with DNSSEC specific requirements and set it up manually. Also, most managed DNS security solutions offer a simple one-click setup.
- Configure Access Control Lists that will specify which hosts can perform specific DNS tasks. This will limit the potential of external intrusions.
- Regularly update the DNS servers. If you are running your DNS servers, make sure that the installed OS is up-to-date, and all the latest security patches are applied.
- Disable DNS recursion. Some servers (Bind, Linux) have DNS recursion enabled by default. If that’s the case, your DNS server actually allows third-party hosts to query the name servers without any limitations. This, in turn, opens the floodgate for DNS poisoning attacks. So, it’s best to disable this feature unless you need your DNS servers to receive recursive queries.
To Conclude
Most DDoS and DNS attacks can be prevented with basic DNS cybersecurity measures that most modern web providers already have in place. However, if you are running large-scale digital operations and provide services over the web, treating DNS security as an afterthought can end up being a costly mistake, especially if you become the target of the attack.
Contact Infopulse cybersecurity specialists to receive a quick consultation on how you can improve your corporate security posture and become fully protected against all types of DDoS/DNS attacks.

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


