How to Ensure Rock-Solid Security When Migrating Apps to the Cloud
Cloud migration is a hot trend right now, and stats by Grand View Research clearly prove as much. In 2022, the cloud migration market in the US alone was valued at $11.7 billion and is expected to grow at a CAGR of 25.9% by 2030 — increasing the worldwide demand for cloud migration services.
Enterprises all over the globe move to the cloud to get scalability, resource optimization, cost savings, and efficiency. However, it’s not a panacea in itself, and other factors should be paid heed to in order to achieve a truly successful implementation.
According to a Foundry survey, a majority of 850 IT leaders report facing security challenges when migrating to the cloud. 35% of the respondents deal with data privacy and security problems; 34% cite lack of security expertise as the key challenge; and 29% experience security compliance issues.
If you want to minimize the negative impact brought by security leaks or prevent it from happening altogether, you should make security your top priority when planning the migration. You can always opt for a cloud provider with a security-by-design infrastructure and other security features.
A good idea here is to engage an experienced cloud migration services provider who will provide you with comprehensive guidance on choosing the optimal cloud vendor for your specific business case while also bridging any lacking security expertise your team may have.
Key Security Features to Implement
With a number of security challenges related to cloud migration, choosing the right vendor is not something to be taken lightly. Here’s our list of security features you should pay particular attention to:
- Security-by-Design Infrastructure to lay the foundation for your protection.
- Continuous Infrastructure & Hardware Monitoring to be aware of all the threats.
- Backup and Recovery to keep your data intact.
- Security Standards Compliance to be in line with industry regulations.
- Continuous Updates and Innovation to stay one step ahead of cybercriminals.
- Corporate Network Segmentation to limit the impact of possible issues.
- Real-Time Analytics to find the data that really matters.
- Digital Forensics to strengthen your long-term defense.
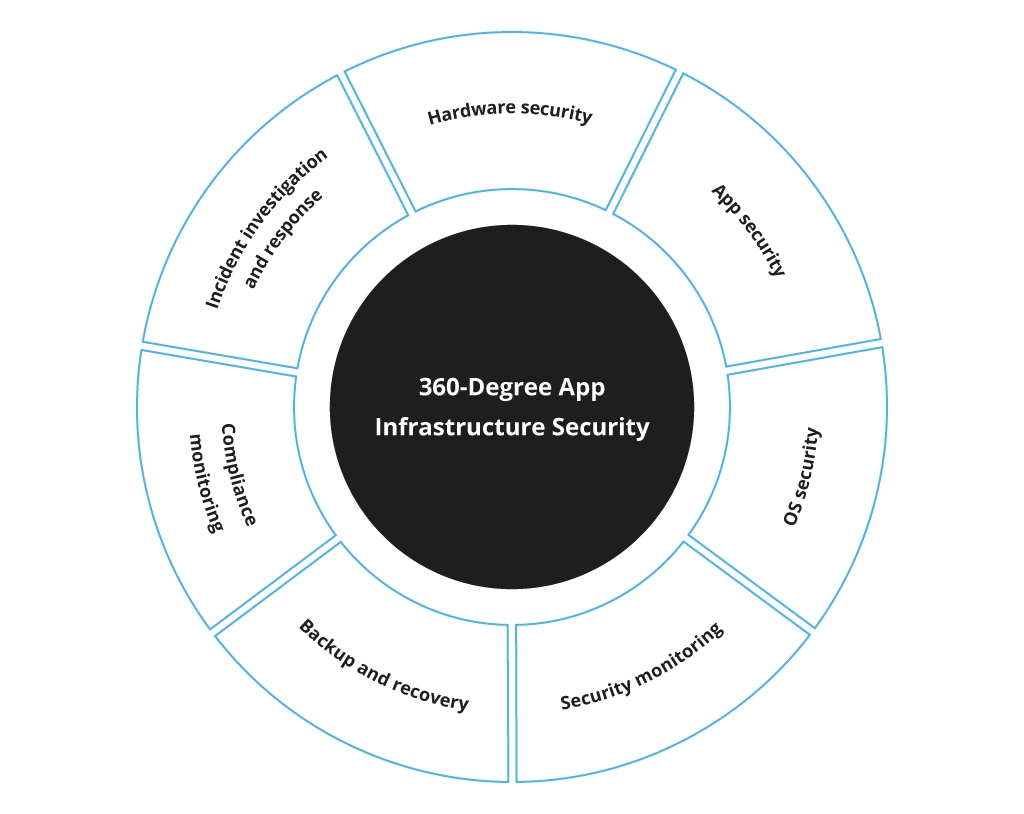
Security-by-Design Infrastructure
A security-by-design (SbD) approach is one of the essentials in building a rock-solid cloud infrastructure. Advanced risk management means that when you migrate your data and apps to the cloud, you can use the vendor’s rigorous security practices— including built-in encryption, real-time threat monitoring, phishing-resistant security keys, and layered security.
For example, Google Cloud offers SbD with built-in protection and encryption by default.
Azure leverages machine learning, behavioral analytics, and application-based intelligence as part of the Microsoft Intelligent Security Graph to quickly detect threats through a thorough analysis of multiple sources, including 18 billion Bing web pages, 400 billion emails, 1 billion Windows device updates, and 450 billion monthly authentications.
AWS provides powerful SbD capabilities for building a robust infrastructure, including logging, encryption, permissions, trust relationships, and more. With such an approach in place, you can also automate compliance.
To make the most of these security benefits, mind the sensitivity of the assets you plan to migrate and build your transition roadmap accordingly.
Continuous Infrastructure & Hardware Monitoring
Another key aspect of impeccable security is 24/7/365 monitoring of all the assets that might be prone to both internal and external breaches — from physical premises and networking equipment to custom security chips and low-level software stacks.
According to IBM’s data, in 2022, it took on average 277 days for an enterprise to detect and address a breach. By applying more thorough, in-depth monitoring, companies can expect faster detection and, as a result, less financial damage — shortening this period to 200 days or less can save around $1.12M.
To successfully implement infrastructure & hardware monitoring and, in turn, drive significant financial savings, you can employ a variety of tools and solutions, depending on your needs: from a simple Systems Manager Inventory to a full-fledged security operations center (SOC). Major cloud providers offer advanced resources to help execute the desired level of monitoring. For example, Microsoft Azure is protected by a 24x7 security team composed of over 3,500 cybersecurity experts. Amazon offers GuardDuty, a sophisticated threat detection mechanism that quickly reveals malicious activity and unauthorized behavior to protect AWS accounts.
Should you need to customize these tools to address your specific needs, a dedicated service provider like Infopulse is ready to assist you.
A case in point: Infopulse empowered a client to synchronize their security initiatives and streamline their security strategy by establishing a robust SOC. As a result, the client significantly reduced the risk of cyberattacks, detected and resolved over 500 security incidents monthly, enabled 24/7 monitoring, and got the utmost visibility into their security posture.
Backup and Recovery
Business continuity is one of the must-haves for any organization simply because the financial damage of downtime is extremely high.
The ITIC 2022 Security Report showed that for 91% of SMEs and large enterprises the hourly cost of downtime goes beyond $300,000 annually, with 44% of the respondents saying they lose between $1 to $5 million for every hour of downtime.
Moreover, no matter the industry or size of the enterprise, security breaches bring about an extremely negative impact on business continuity: 78% of the respondents report that data breaches constitute the key threat to the company’s data center, server, applications, cloud ecosystem reliability, and network edge.
If losses this huge might occur with just a short outage, imagine the risks when migrating your critical business assets to the cloud. That is why you should choose a cloud vendor with powerful backup and recovery capabilities.
For example, having the possibility to build backups in multiple geographic regions secures your assets and makes them resilient to potential zone and region failures in the cloud. Namely, AWS Global Infrastructure spans 99 Availability Zones in 31 regions, allowing organizations to deliver their services right to the customers’ doorsteps while ramping up system resiliency.
For their client, Azure provides scalable, highly customizable backup solutions which ensure an 80% reduction in average data recovery time with an impressive 97% rate of end-user productivity despite data loss.
A case in point: Infopulse helped a client with full-fledged cloud migration while ensuring rock-solid security and business continuity. The company enabled powerful risk management and 99.95% availability of IT services with minimized unplanned downtimes.
Stringent Security Standards Compliance
The more niche-specific security rules, regulations, standards, and requirements your cloud provider fulfills, the lower the risk of security breaches or outage becomes. In this context, compliance standards refer to the highest independent, internationally recognized audits and certifications concerning the security of employees, business processes, and technologies.
Top cloud vendors cover most of the required controls, including standards like PCI-DSS, HIPAA/HITECH, FedRAMP, GDPR, FIPS 140-2, and NIST 800-171. All you need to do is to tap into a variety of compliance-enabling offerings. For example, Azure Blueprints to create compliant environments or AWS Artifact to automate security and compliance reports.
If you need third-party validation of your security infrastructure, leverage a custom compliance management solution. Underpinned by this mechanism, you can thoroughly assess the current level of compliance with your products and processes as well as notably simplify the management of IT security, data privacy, and quality standards.
A case in point: Infopulse helped the second-largest alarm company in Europe to seamlessly migrate business systems to the cloud. The company revamped overall information security and notably improved compliance by restricting access to the personal information of end users.
Continuous Updates and Innovation
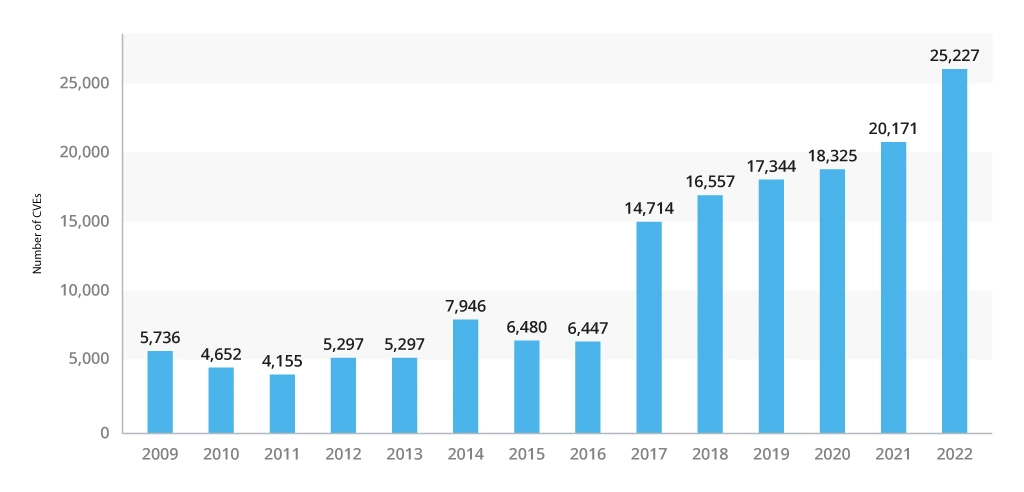
In 2022, there were more than 25,000 common IT security vulnerabilities and exposures (CVEs) reported, which is a record number to date. Between January and April 2023 alone, 7,489 vulnerabilities were detected.
These and other security stats clearly show the utmost demand for cloud-based security solutions with patches and software updates among key capabilities. Timely patches for critical vulnerabilities and regular updates across your infrastructure work best to defend your organization from serious breaches and zero-day threats.
Corporate Network Segmentation
Since cyber criminals usually target specific users in a corporate network via websites or emails, consider segmentation from user workstations as a necessary implementation step in the cloud. This way, users will only have the connectivity to perform their core competencies. Moreover, as workstations lack direct access to the corporate network, attackers will not reach the company’s data and software if a workstation is compromised.
Amazon offers the ability to create multiple network segments by using built-in security groups — each of them with custom communication mapping.
Powerful Real-Time Analytics
Another aspect you just cannot let slip through the cracks is ML-powered security analytics.
The stats show that companies with fully implemented AI and automation mechanisms can detect and address a security breach 74 days faster than those that don’t, all while saving $3.05 million in costs. Even those with partial deployment can notably fortify their security environment.
Indeed, through such cutting-edge mechanisms you can get in-depth insights into your security posture and mitigate the most sophisticated vulnerabilities. Besides, an experienced cloud security service provider will help minimize threats with ML-fueled security audits and risk assessments as well as run the simulated attacks needed for building a resilient security environment.
The above-mentioned GuardDuty by AWS, for example, can provide you with in-depth security findings for real-time visibility and timely remediation.
Azure’s threat detection tools rapidly spot anomalous database activities with potential threats and send reports directly to the administrator.
Digital Forensics
One more step that can significantly improve your cloud security is continuous incident monitoring. This way, you’ll be able to deeply analyze, report, and in turn remediate both internal and external attacks.
Also, think about developing all-encompassing incident response plans (IRPs) with advanced automation features to further strengthen your long-term defense. By continuously testing and enhancing your IRP, you can proactively detect cybersecurity weaknesses. Not only will this help shore up your security posture, but will also result in significant savings should a breach occur — in 2022, companies operating with an IR team and a regularly tested plan versus those who had neither, saved an average of $2.66 million when responding to a breach.
AWS offers a marketplace of logging and monitoring solutions that help detect the root cause of security incidents and the resources impacted, as well as quickly resolve investigations through custom metrics, powerful search capabilities, and machine learning.
Conclusion
As you can see, certain challenges are likely to arise when migrating your assets and business processes to the cloud. To mitigate these risks, make sure you choose an optimal provider and the most suitable cloud migration strategy.
A multi-year AWS and Microsoft partner and an expert in all things security, Infopulse has got your back in this respect. From comprehensive cloud consulting and strategy creation to full-fledged cloud migration and building a reliable SOC, we’re here to cover your specific needs.
![Security Guide for Cloud Migration [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-security-when-migrating-apps-to-the-cloud.webp)
![Security challenges [scheme 1]](/uploads/media/scheme-1-security-when-migrating-apps-to-the-cloud.webp)
![Cost of data breach [scheme 2]](/uploads/media/scheme-2-security-when-migrating-apps-to-the-cloud.webp)

![Top causes of server downtime [scheme 3]](/uploads/media/scheme-3-security-when-migrating-apps-to-the-cloud.webp)


![AWS migration strategy [thumbnail]](/uploads/media/thumbnail-280x222-aws-migration-strategy.webp)
![Common Cloud Migration Challenges [thumbnail]](/uploads/media/common-cloud-migration-challenges to-overcome with-cloud-managed-services-2023-02-22_280x222.webp)




