How to Scale Your Asset Management Solution
As new assets enter the perimeter, software asset management (SAM) teams often struggle to keep up. Over three-quarters of Flexera survey respondents say that dealing with new environments such as SaaS, cloud, and containers is challenging for them. At the same time, 70% of SAM teams lack qualified human resources, which stalls the process of implementing new asset management best practices.
In this post, we talk about signs that your company needs to scale up your enterprise asset management solution and provide a resource-effective framework for doing so.
3 Scenarios When You Need to Rethink Your Asset Management
Your company has already set up the baseline IT asset management process and established essential vulnerability management practices. This means you are covered, right? Hold that thought.
IT asset management is a lifecycle process, requiring ongoing diligence. Adoption of new environments (e.g., in a public cloud), purchases of new software licenses (e.g., PaaS products), or shifts to new software development practices (e.g., double down on containerization) require a refresh of your asset management process.
Likewise, growth in employee headcount or applications in production requires more computing capacities such as virtual machines (VMs), integrated development requirements, and other CPU and memory resources. These must be properly inventoried and monitored too.
Therefore, our Infrastructure Management team always recommends re-evaluating your asset management process in the following three scenarios.
Recent M&A Activity
Mermer and acquisition (M&A) activity comes with a host of IT jobs to be done — from data consolidation to system integration and homogenization. Eventually, you end up with a wider IT estate, often with redundant IT infrastructure components and duplicate licenses.
The matters often get extremely complex when the acquired company had immature asset management practices (i.e., used an Excel spreadsheet for tracking). In such cases, you will have to create a new inventory of acquired assets, then properly tag them, and incorporate them into the established asset management framework. The faster you complete this process, the less budget you will waste on excess resources.
Multi-Cloud Adoption
Multi-cloud strategy has many perks: improved scalability, reduced operational risks, better compliance, and the ability to combine the best-of-breed providers. So no wonder that 98% of enterprises intend to or already use at least two cloud infrastructure providers, of which 31% use four or more.
The key challenge of embracing the multi-cloud (or even cloud-agnostic) strategy is ongoing infrastructure management. Interoperability among cloud services providers (CSPs) remains somewhat bounded, especially regarding asset monitoring. For example, AWS offers ample, scalable monitoring tools for its environment. So do Azure and Google Cloud Platform for their respective environments. Yet, consolidating assets and monitoring data from multiple cloud environments requires the creation of separate custom dashboards and the usage of third-party tools if you wish to obtain consolidated insights from numerous accounts and regions.
Cloud Computing Cost Optimization
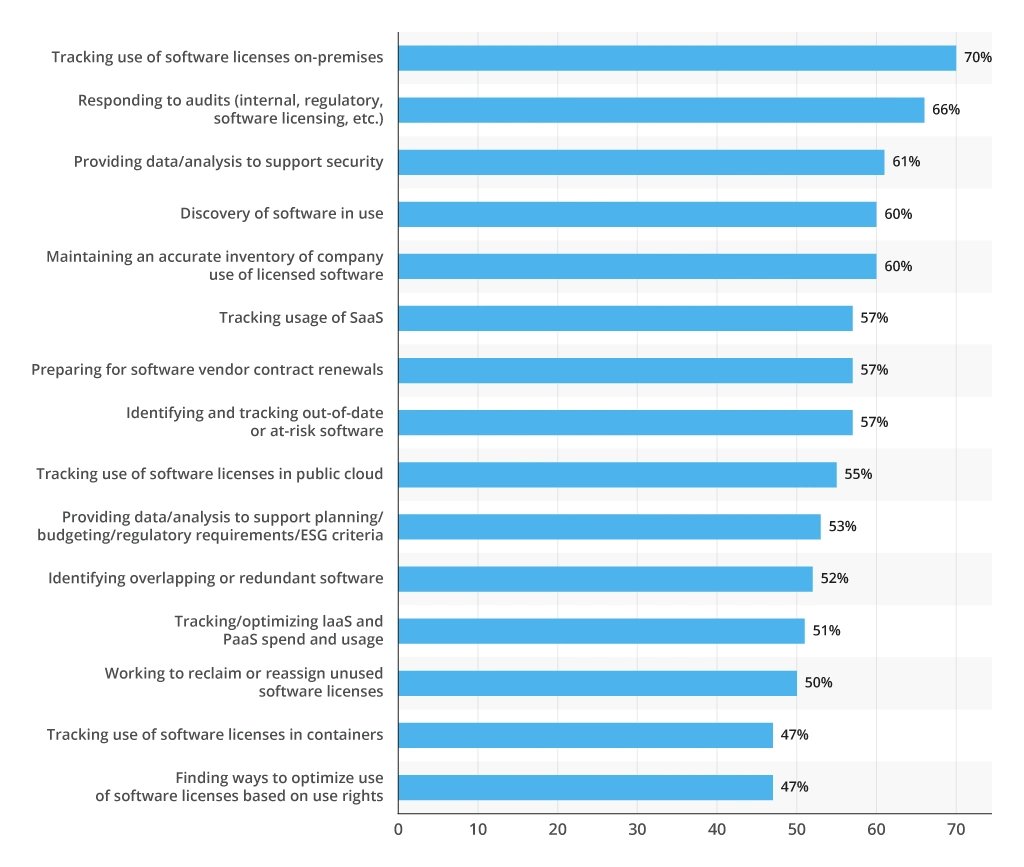
Whether you are using multiple CSPs or a single provider, cloud license monitoring can be a tedious process. CSPs use a range of billing models — from fixed-price licenses and user seats to pay-as-you-go — for different types of assets. A poorly selected license balloons the operating bill along with underused and unused software licenses, which 50% of SAM teams aim to reclaim.
If you are constantly surprised by a large cloud bill and cannot properly attribute spending to different cost centers, it is a clear sign that your asset management practices need a refresh.
How to Approach Enterprise Asset Management Scaling
If any of the above scenarios ring a bell, there is new audit work to be done. Although being labor-intensive, timely audits can harness major cost savings and help improve corporate security posture and compliance.
The better news: Technical audits and asset management in general can be a streamlined activity when backed by mature information technology asset management (ITAM) practices.
Here is how to improve your asset management process to achieve virtually limitless scalability.
Start With an Audit
A well-structured, up-to-date inventory of all assets is the backbone of effective ITAM. If there have been any major changes in your IT portfolio lately, update your asset inventory.
A good SAM audit includes the following activities:
- Inventory of all installed apps
- All existing cloud licenses
- Active SaaS/IaaS/PaaS subscriptions
Your goal is to create a unified system for inventory detailing e.g., by asset objective, asset type, or assigned cost center. For larger organizations, a multi-branch tree works best. The next step is to record all the assets, using the assumed convention. The new inventory must also reflect recent policy changes in asset management for different teams (e.g., new usage caps for on-demand instances).
The outcome of an audit is an updated inventory where you can see all assets, categorized by tenant, billing type, owner/administrator, with clear dependencies between different IT systems.
Implement Tagging and Naming Conventions
Well-structured asset metadata is the second critical element of scalable asset management. Unsystematic naming or tagging practices do not only hinder asset visibility but also limit scalability since you cannot implement automated categorization and effective filtering.
It pays to remember the following asset tagging best practices:
- Create standardized asset categories (e.g., business app, VM, server) and types (e.g., on-premises, AWS, Azure).
- Establish naming conventions. Most organizations go with an alphanumeric system, which codifies the asset type and designation.
- Use descriptive tags to provide extra contextual information. Tags should be short and contain only information that is useful at a glance.
- Include ownership information to better attribute costs and forward requests.
Your asset naming convention should be built in a top-to-bottom hierarchy, with a descriptive prefix as the top element for search and categorization. Ensure that there are no duplicate names and add rules that prohibit using the same names.
The outcome: A tree structure hierarchy, promoting consistent, unique naming and easy asset discovery.
Update Your RBAC Model
Role-based access control (RBAC) combines IT privileges to make access management easier. In other words, different types of roles automatically receive standardized permissions for accessing a set of designated assets.
Manual access management for each user is time-consuming and leads to mistakes. As a result, your enterprise may be dealing with orphaned accounts or privilege creep — a build-up of excessive permissions on certain user accounts. The latter poses major cybersecurity risks.
RBAC helps streamline user and rights management, while also ensuring proper usage of allocated assets (e.g., you restrict access to new instance creation only to senior engineers). In this way, you can not only better control asset usage but also minimize cyber risk exposure and optimize operating costs.
Based on your asset inventory and corporate IT policies, create a standardized set of user roles. Roles are usually based on various user attributes such as:
- Office
- Department
- Position
- Seniority level.
One user can hold multiple roles at a time if that is required by their job. Modern IAM solutions such as Azure Identity Management help streamline this process.
Refresh Your Asset Monitoring Setup
The last step in improving your asset management process is implementing across-the-board monitoring.
Set up new dashboards or update existing ones to include newly added assets. Create detailed filters, based on tags and names and aggregated views for convenience.
A common mistake we often observe during asset management scaling is excessive monitoring. In simpler terms: companies want to track every minuscule change without having a good reason for doing so. Such a penchant for observability can result in jumbo-sized visual dashboards, where truly important information gets concealed by insignificant details.
Remember: the goal of IT infrastructure monitoring is to alert the teams about important events such as
- Performance issues
- Resource over-use
- Vulnerabilities discovery
- SLA breaches.
Select a limited number of use cases for asset monitoring. For example, “Understanding cloud licensing costs for all AWS assets” is a solid use case, but “Having all IT assets parameters visible from a dashboard” is not. Before you set up another dashboard view, always ask this simple question: Why do we need this data? If you cannot come up with a legitimate reason, drop that idea.
Last but not least, take another look at your asset monitoring tools. For cloud monitoring, Azure Lighthouse and AWS Control Tower are the optimal choices. Each service supports multi-tenant asset management and monitoring; promotes streamlined resource governance and automation.
To Conclude
Effective asset management is harder to set up than it is to scale. As long as your company is proactive about asset discovery, diligent with inventory upkeep, and practices unified resource tagging, you will be in a good place to accommodate scale.
The above-described approach lets you achieve a virtually limitless scalability potential where new asset discovery is largely automated and governed by unified policies.
![Asset Management Solution [main banner]](https://www.infopulse.com/uploads/media/banner-1920x528-how-to-scale-an-enterprise-asset-management-solution.webp)


![Vulnerability Management [thumbnail]](/uploads/media/thumbnail-280x222-the-key-role-of-vulnerability-management.webp)
![Cloud Cost Optimization [thumbnail]](/uploads/media/thumbnail-280x222-cost-optimization-in-cloud-licensing.webp)
![Azure Arc [thumbnail]](/uploads/media/thumbnail-280x222-azure-arc-multi-cloud-management.webp)
![Vulnerability Management Process Setup [thumbnail]](/uploads/media/thumbnail-280x222-how-to-create-an-agile-vulnerability-management-process-best-practices.webp)
![Cryptojacking and how to prevent it [thumbnail]](/uploads/media/thumbnail-280x222-what-is-cryptojacking.webp)
![Asset Management in AWS [thumbnail]](/uploads/media/thumbnail-280x222-how-to-enable-effective-asset-management-in-your-was-environment.webp)
![What Is ITAM [thumbnail]](/uploads/media/thumbnail-280x222-what-is-it-asset-management-and-how-to-build-one.webp)



