The Key Role of Vulnerability Management and Penetration Testing in Business Protection
As online transactions continue to multiply, it has become imperative for finance companies to ensure the integrity of their systems. For example, there are already a few compliance regulations in place (like Payment Card Industry Data Security Standard (PCI DSS)) that subject financial organizations to perform regular vulnerability scanning and identify security vulnerabilities aimed at protecting data privacy of their customers. The objective is to detect and address any weaknesses or flaws in the systems before they can be exploited by cybercriminals.
For this, many organizations adopt some vulnerability management programs and solutions, and though 71% of surveyed companies already have some formal in-house programs, only 30% believe they are effective.
Today, we will focus on three essential components of such a vulnerability management program – vulnerability scanning, vulnerability assessment, and penetration testing that are poised to strengthen your organization's security posture with the right approach. Let’s look closer at how they complement each other and how you can add them to your cybersecurity strategy.
Vulnerability Management and Penetration Testing in Action
We have dedicated a series of our polished articles to delving into vulnerability assessment and penetration testing basics, methodologies, and best practices:
- "Setting Up an Effective Vulnerability Management Process"
- "Knowing When to Initiate Vulnerability Assessment and Penetration Testing"
- "Exploring Extreme Cases in Modern Penetration Testing"
- "Unveiling the Shades of Grey-Box Testing in Modern Penetration Testing"
- "From Routine to Art: Enhancing Your Penetration Testing Approach"
- "Beginner's Guide: Training and Practicing Buffer Overflow in Penetration Testing"
In this feature, let’s focus on the practical application of these security mechanisms. As an example, we will demonstrate how a financial institution should act when assessing the security of its online banking application.
Security Audit and Controlled Vulnerability Exploitation
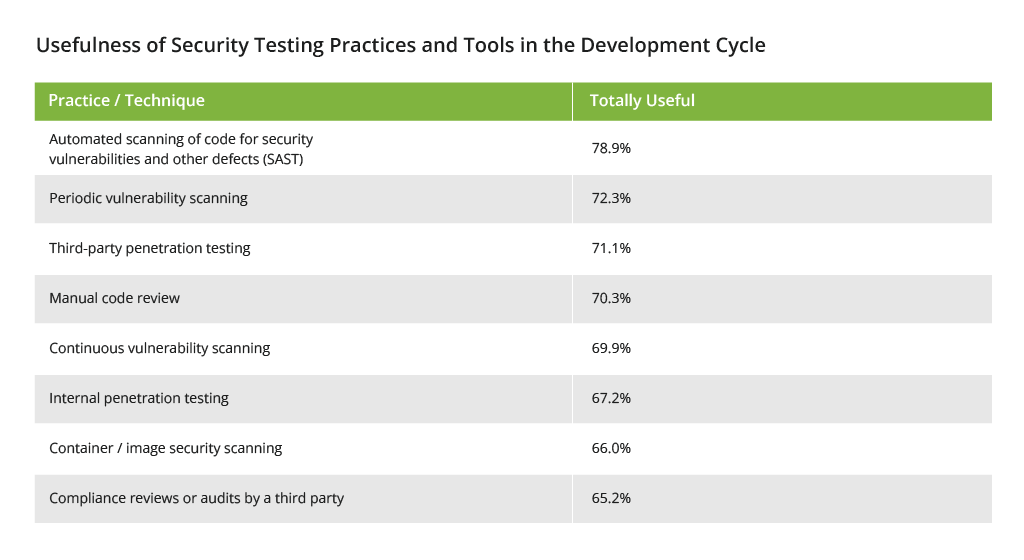
Safeguarding an organization's digital infrastructure against evolving threats requires a proactive and comprehensive approach to vulnerability management. Vulnerability scanning, vulnerability assessment, and penetration testing serve as critical components in this endeavor. Here’s how organizations evaluate the usefulness of such security practices:
By utilizing automated scanning tools, organizations can pinpoint vulnerabilities such as outdated software versions and weak passwords. By the way, automated vulnerability discovery (also scanning) already works well for 87% of organizations, helping them to safeguard both their on-premises and cloud infrastructure.
Moving beyond scanning, vulnerability assessment goes deeper into the identified vulnerabilities. Experts analyze and validate the severity of security loopholes, like the SQL injection, cross-site scripting (XSS), weak encryption algorithms, and inadequate access controls, to name a few. Through meticulous testing and analysis, the impact of an attack is demonstrated, providing insights into the risks an organization is currently facing. Penetration testing takes vulnerability assessment to the next level. Ethical and inventive hackers simulate real-world attacks and attempt to exploit the identified vulnerabilities.
A Sample Scenario: Security Assessment of a Banking Application
Let's explore a common scenario in the financial industry where a company seeks to evaluate the security of its banking app. To achieve this, a recommended approach involves a three-step process:
- Vulnerability scanning
- Vulnerability assessment
- Penetration testing
Vulnerability Scanning
The organization that wants to assess the security of its online banking application should conduct a vulnerability scan using automated scanning tools (Nessus, OpenVAS, QualysGuard, Rapid7 Nexpose, Acunetix). The scan helps identify potential vulnerabilities in the online banking application, such as outdated software versions, misconfigurations, and a myriad of other security flaws. The scan generates a report that lists the discovered vulnerabilities and their severity ratings.
We advise our clients to conduct routine in-house scanning with automated scanning tools before opting for a third party according to PCI DSS for CHD companies. This proactive approach allows for the identification of certain vulnerabilities that may be relatively minor in nature and can be resolved with the capabilities of scanning tools and general ‘housekeeping’.
These may include:
- Outdated software versions
- Weak passwords
- Misconfiguration
- Insecure permissions
- Missing security patches for libraries, etc.
Discovered vulnerability: SQL injection, for example. It can allow attackers to manipulate database queries with the goal of stealing sensitive and precious data, leading to financial and reputational losses.
The impact of SQL injection on your applications can be severe, including the following risks:
- Stolen Credentials: Attackers can exploit SQL injection to obtain credentials, allowing them to impersonate users and utilize their privileges within the system
- Accessed Databases: SQL injection allows attackers to gain unauthorized access to the sensitive data stored in your database servers, potentially exposing confidential information
- Altered Data: Attackers can maliciously alter or add new data to the accessed database, leading to data integrity issues and potentially compromising the accuracy and reliability of your data
- Deleted Data: SQL injection vulnerabilities can enable attackers to delete specific database records or even drop entire tables, causing data loss and disruption to your applications
- Lateral movement: In some cases, attackers can leverage SQL injection to access database servers with operating system privileges. This gives them the opportunity to exploit these permissions to further infiltrate other sensitive systems within your infrastructure.
Speaking of constant cyber risks, 24/7 monitoring and vulnerability scanning is prepackaged in our SOC (Security Operations Center) service. It is highly demanded by our clients, like a Swiss manufacturer, looking to strengthen their security posture.
Vulnerability Assessment
Building upon the vulnerability scan results, a team of experts should perform a vulnerability assessment to gain a deeper understanding of the identified vulnerabilities. Infopulse specialists are well-versed in security intricacies and equipped with advanced certifications in the Microsoft Threat Protection. They can conduct rigorous analysis to verify the accuracy and severity of the security loopholes.
In the case of SQLi, testers would try out various scenarios and techniques to identify the potential SQL injection points within the application. This may include:
- Sending particular input values – Testers create specific input values that have the potential to exploit SQL injection vulnerabilities, aimed at triggering unexpected behavior within the application's database interaction.
- Using different payloads – Security experts employ specialized inputs to exploit various SQL injection techniques, such as union-based, time-based, or error-based attacks. By systematically injecting these payloads, they uncover any vulnerable areas susceptible to SQLi.
- Analyzing application's responses – The application's responses are monitored and examined for any indications of SQL injection vulnerabilities. Anomalous behavior, error messages, or unexpected output can serve as telltale signs of potential SQL attack vectors.
Penetration Testing
Once the vulnerability assessment is complete, the organization proceeds with penetration testing. The importance of penetration testing is evident from the growth of the global market in this field, which was valued at US$1.4 billion in 2022 and projected to reach US$3.8 billion by 2030.
At this stage, creative ethical hackers simulate real-world attacks against the online banking application. They attempt to exploit the vulnerabilities identified in the previous steps by gaining unauthorized access or compromising sensitive data. Here's how Infopulse helped Bosch to conduct a comprehensive audit of their embedded solutions, including security assessment, threat and risk analysis, and penetration testing.
By exploiting the SQL injection vulnerability, the penetration tester aims to demonstrate the potential impact of an attack. This can include:
- Unauthorized data access and breach
- Data manipulation or destruction
- Account hijacking
- Denial of Service (DoS)
- Regulatory and legal consequences
- Financial and reputational losses
- Complete takeover of the application's backend database.
The penetration testing process is then thoroughly documented with taken steps, obtained results, any additional vulnerabilities or security weaknesses discovered during the pentest. Finally, ways to mitigate detected vulnerabilities are offered.
For 77% of organizations reporting is a must-have functionality in paid pentesting software. While 67% consider extensive threat libraries important, and 61% are looking for multi-vector testing capabilities.
In this simplified scenario (because vulnerabilities always travel in packs), we showed how the assessment helps in identifying and documenting the vulnerability, while penetration testing allows for real-world validation of its exploitability and the effectiveness of current security controls. Together, they provide valuable insights into the risk level and business impact posed by SQL injection and assist in developing appropriate mitigation strategies.
A case in point from our practice is a penetration testing project that we implemented for our client ING Bank Ukraine. Read the full business case here.
Security of Your Enterprise Is in Your Hands
There are no easy answers and blanket recommendations when it comes to vulnerability management. Besides interconnected digital landscape, organizations navigate their own complex systems like ERPs, CRMs, document management, collaboration tools, etc. that drive their operations.
One common misconception is that opting for well-known and established systems with millions of customers provides more safety and security to an organization. It’s true but only to some extent. Giants like SAP, Microsoft 365, and Salesforce are meticulous about the security and compliance of their products with regular patches and updates. But we all know that it takes two to tango. Businesses should take a proactive approach to manage potential vulnerabilities on their side.
For example, in SAP systems, weaknesses in access controls may result in unauthorized access to sensitive data and transactions. Meanwhile, organizations utilizing Microsoft 365 must be vigilant against weak passwords, phishing attacks, and insider threats that can lead to data breaches and unauthorized access to valuable resources. Similarly, Salesforce users should pay attention to issues such as insecure access controls, cross-site scripting vulnerabilities, and flaws in custom code that can expose customer data to unauthorized individuals.
Regular vulnerability assessments and vulnerability scanning can help identify potential weaknesses and security gaps in SAP, Microsoft 365, and Salesforce systems that are specific to your enterprise. To minimize the likelihood of attacks, organizations should implement strong security controls, such as:
- Robust access management mechanisms
- Regular system updates
- Comprehensive security training for employees.
However, to understand and successfully address the typical vulnerabilities associated with these systems, organizations first need to assess their security posture and understand how to best approach the defense of their critical assets and operations.
Conclusion
While vulnerability management is not without its challenges, organizations must embrace comprehensive security strategies. Simply relying on vulnerability assessment and penetration testing is insufficient. Instead, a holistic approach is needed, incorporating threat intelligence, employee training, secure coding practices, incident response planning, and regular security assessments. By adopting these measures, organizations fortify their defenses against emerging threats, adapt to changing attack vectors, and ensure the integrity of their data capital.





![Vulnerability Management [thumbnail]](/uploads/media/thumbnail-280x222-the-key-role-of-vulnerability-management.webp)
![Defender for IoT [thumbnail]](/uploads/media/thumbnail-280x222-how-to-ensure-Iot-and-ot-security98.webp)
![Security Stack [thumbnail]](/uploads/media/THUMBN~1.WEB)
![Vulnerability Management Process Setup [thumbnail]](/uploads/media/thumbnail-280x222-how-to-create-an-agile-vulnerability-management-process-best-practices.webp)
![AWS Security Hub Integrations [thumbnail]](/uploads/media/top-security-solutions-to-integrate-with-aws-security-hub-for-soc-280x222.webp)
![Building AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-enterprise-guide-to-building-your-aws-security-hub.webp)
![Why Use AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-why-use-aws-security-hub.webp)
![How to Centralize Enterprise Security System [thumbnail]](/uploads/media/thumbnail-280x222-how-to-centralize-enterprise-security-system.webp)





![Guide to Modern Penetration Testing [Part 3]: A Digital Adventure - Thumbnail](/uploads/media/guide-to-modern-penetration-testing-part-3-a-routine-or-genuine-art-280x222_1.webp)
![Guide to Modern Penetration Testing [Part 2]: Choose Your Box - Thumbnail](/uploads/media/guide-to-modern-penetration-testing-part-2-fifty-shades-of-grey-box-280x222_1.webp)
![Guide to Modern Penetration Testing [Part 1]: Two Extreme Cases - Thumbnail](/uploads/media/guide-to-modern-penetration-testing-part-1-two-extreme-cases-280x222_1.webp)