A Guide to Adopt Microsoft Sentinel for SAP
Increasing cybersecurity threats made ERP systems like SAP a prime target for threat actors. SAP security vulnerabilities have become a critical concern for enterprise decision-makers and senior security specialists, with an average cost of a SAP breach of $5 million per attack. This cost doesn’t include the cost of the reputational damage a security attack or breach might cause, yet it is often significant and prolonged.
Microsoft Sentinel is a robust SAP security tool that helps proactively detect and alert security threats. In this article, you will discover what advantages Microsoft Sentinel has over the native SAP security capabilities. Also, you will get a clear deployment roadmap for integrating the solution into your SAP environment.
How Does Microsoft Sentinel Improve SAP Security?
The SAP ecosystem is complex and challenging for security operations (SecOps) teams to monitor and address all potential and actual vulnerabilities effectively. The Microsoft Sentinel solution for SAP significantly widens capabilities for monitoring, detecting, and responding to suspicious activities and protecting all sensitive business data from sophisticated cyber attacks. Take a quick overview of what Microsoft Sentinel is in our dedicated adoption guide.
Benefits of Microsoft Sentinel for SAP
On the one hand, Microsoft Sentinel for SAP has a wide range of out-of-the-box logic and rules for security monitoring. On the other hand, this SAP security tool offers flexible customization capabilities to widen standard functionalities with custom scenarios and regulations. Additionally, it allows to collect valuable security information to perform threat analytics and threat hunting. Other benefits of Microsoft Sentinel for SAP include:
- Scalability with clear monthly operating costs: As the SAP environment scales to meet business needs, Microsoft Sentinel effortlessly scales alongside the growing volumes of security logs and events. Available license types allow precise and predictable budgeting based on the resources consumed.
- Simplified management with reduced labor: The latest Forrester study reveals that Microsoft Sentinel helped reduce labor effort for advanced/multitouch threat investigations by 80% during 1-3 years of use.
- Improved effectiveness: Microsoft Sentinel allows correlating data from different sources besides SAP data that helps create more flexible threat detection rules and detect a broader range of threats across the entire infrastructure. See how Infopulse helped improve the security posture of a Swiss manufacturer by implementing Microsoft Sentinel.
- Reduced maintenance effort: With reduced on-premises infrastructure and powerful storage automation capabilities, Microsoft Sentinel allows performing less maintenance and spending more time adding value to the business. Forrester reports 56% less maintenance efforts during the 1-3 years of Microsoft Sentinel use.
- Smarter and faster threat protection: Suspicious activities can be detected in the earliest stages, preventing the actual damage. Automating threat detection and reaction scenarios significantly saves time in processing threats and maintaining the required SAP security level.
A range of alternative solutions for SAP security monitoring is available on the market, including QRadar and Splunk, as the most popular ones. Compared with Microsoft Sentinel, the major disadvantage of QRadar is the lack of a ready-made data connector. It implies additional effort and challenges when ingesting SAP data. Compared to the alternatives, Microsoft Sentinel for SAP has broader native threat-hunting capabilities, allowing to identify potential threats easier for users.
SAP Security Capabilities
Integrated with SAP, Microsoft Sentinel seamlessly collects and correlates business and application logs from SAP systems, enabling proactive detection and response to potential threats. Among other strong features Microsoft Sentinel offers are:
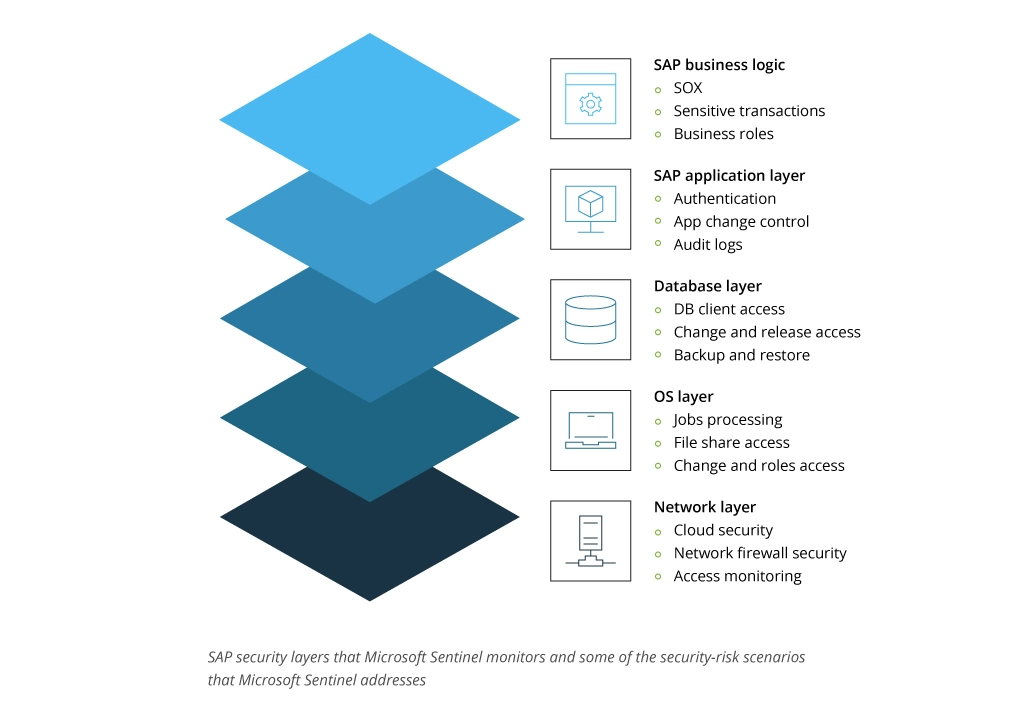
- Monitoring all SAP system layers: Gaining visibility across business logic, application, database, and operating system layers with integrated tools for suspicious activity investigation and threat detection.
- Detecting and automatically responding to threats: Activities like privilege escalation, unauthorized data modifications, sensitive transactions, and suspicious data downloads can be accurately detected and prevented.
- Correlating SAP activity with other signals: The system uses data correlation from all available sources and SAP infrastructure to detect SAP threats.
- Ability to customize based on your needs: Microsoft Sentinel allows to extend built-in security mechanisms by building custom threat detection solutions to monitor unique business risks.
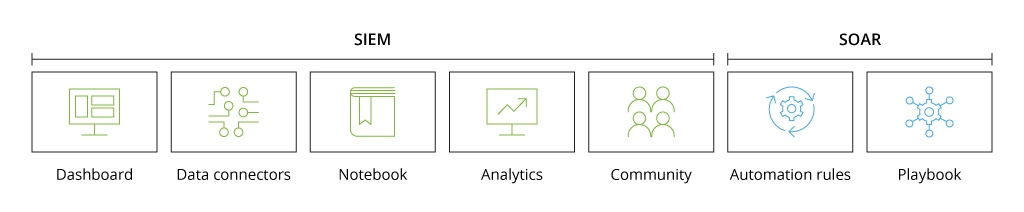
The solution includes the following components:
- The Microsoft Sentinel for SAP data connector for data ingestion. The data connector helps bring data from an SAP system to Microsoft Sentinel. It works as a Docker container installed on a virtual machine or a physical server. With a ready-made data connector, there is no need to build custom functionality to retrieve the SAP data from your ecosystem, significantly saving the implementation time.
- Analytics rules and watchlists to detect possible incidents and alert security respondents. There are various built-in rules available alongside the ability to create custom ones.
- Workbooks for interactive data visualization. Both pre-built workbook templates and custom workbook creation are available.
- Watchlists for customization of the built-in solution parameters.
- Playbooks for automating and simplifying the security orchestration.
Microsoft Sentinel for SAP is certified for SAP S/4HANA® Cloud, Private Edition RISE with SAP and SAP S/4 on-premises. It also enables integration with various enterprise-use products and platforms and provides customizable configurations to meet specific security monitoring needs. Advanced ML and AI capabilities help identify suspicious patterns based on previously defined threats.
Types of Threats Microsoft Sentinel for SAP Can Tackle
Microsoft Sentinel provides SAP security monitoring for all system layers, including SAP business logic, SAP application layer, database, and the operating system. Here are the main monitoring capabilities for each layer:
Compared to the native SAP security monitoring capabilities, Microsoft Sentinel gives more comprehensive visibility to potential threats by correlating data from different sources and allows investigating suspicious activities from the entire infrastructure, not limited only to the SAP layer. This SAP security tool ensures wide threat detection coverage, including the following types of threats:
- Suspicious privilege operations (critical authorization assignment, usage of break-glass users, unlocking a user and logging into it from the same IP address, etc.)
- Attempts to bypass SAP security mechanisms (unlocking blocked transactions, disabling audit logging, RFC (remote-function-call) execution of sensitive function, etc.)
- Backdoor creation (new ICF creation, user unlocking, accessing sensitive tables by RFC, etc.)
- Data exfiltration (spool takeover, multiple file downloads, dynamic RFC destination, etc.)
- Initial Access – Brute force (multiple logins from the same IP, SPNEGO Replay attack, etc.)
How Does Microsoft Sentinel Detect Threats inside SAP?
Let’s consider a sample of an attack scenario to understand the prevention capabilities of the Microsoft Sentinel SAP security tool:
- The threat actor wants to access SAP. They will most likely attempt to find some active user's login details using brute force. Sentinel will alert the system about this suspicious activity.
- If a password is found, the attacker will access SAP and check the available user permissions – what sources of sensitive information they can access and modify. Sentinel will alert the system if a user reviews more documents than it is typical for this account.
- The threat actor will try to extend available permissions to make more changes in the system and data. Microsoft Sentinel strongly controls permissions, so any attempts to modify rights will be detected and alerted upon.
- The next step of the threat actor is modifying some data, like changing an invoice amount for a partnering company or customer and pushing the invoice without confirmation. Again, Sentinel detects such activities and will notify about them.
This way, the attack will be alerted on each step. While Microsoft Sentinel is a typical SIEM system, its primary goal is threat control and monitoring. The response to alerts is the role of SOAR. Based on Sentinel’s alert, the following automation scenario for attack prevention can be implemented:
- Brute force: either blocking the attack actor's IP address or the end-point in case of using an employee computer.
- If the IP address changes, the attacker can still access SAP. When the system detects suspicious activity, this account can be blocked in SAP.
- Sometimes the attacker still has some options to continue their attack. After analyzing the points where they were previously blocked, they can enter the system from another account, avoiding those suspicious actions that have already led to alerting. Still, SOAR will be able to stop malicious activity when accessing documents or other files, which is not typical for this user’s common behavior patterns.
This is just an example of how Microsoft Sentinel capabilities help gain full transparency in detecting suspicious activity. Security monitoring in SAP is a part of customization task, as business processes and their value are specific for each enterprise. They need appropriate fine-tuning and customizations. Microsoft Sentinel allows writing custom rules and scenarios for detecting threats that help adjust cybersecurity monitoring to the needs of a specific infrastructure.
Microsoft Sentinel for SAP Deployment Roadmap
Microsoft Sentinel for SAP provides robust threat detection and monitoring capabilities. However, the cost-efficiency and deployment complexity highly depend on a deep understanding of the business logic and SAP security needs you want to address with its deployment. This deployment roadmap describes the process of integrating and configuring Microsoft Sentinel for SAP:
- Analyze the business needs for SAP security you want to cover with Microsoft Sentinel adoption.
- Identify specific use cases, i.e., processes and operations you need to control with your SAP security tool. The amount and complexity of use cases define the complexity of Microsoft Sentinel setup, license pricing, and maintenance effort.
- Identify the resources that the company owns and needs to protect (finances, human resources, etc.). Conduct threat modeling and risk assessment based on the steps 1 and 2.
- Verify the deployment prerequisites across the entire solution. This step includes verifying system prerequisites, Azure prerequisites, SAP prerequisites, and notes. It also includes creating a new SAP role to assign permissions to let the data connector connect to the SAP system and ingest data to Microsoft Sentinel.
- Prepare the SAP environment by deploying required CR files (change requests), import them into the SAP system, and create a user role with the required ABAP authorizations for the data connector.
- Integrate Microsoft Sentinel for SAP: deploy the data connector agent, deploy the security content, and choose whether to create a separate workspace for your SAP team or share the existing workspace based on your governance policies.
- Configure the solution by setting up the required watchlists, including SAP-Systems, SAP-Networks, SAP-Sensitive, and user master data watchlists, based on your SAP security tool needs.
- Clarify the roles for managing Microsoft Sentinel for SAP: The roles depend on your infrastructure and involve multiple roles to set up a responsible team. Administrators, security analysts, security and compliance analysts, and other IT technicians can be applied.
- Test Microsoft Sentinel for SAP before deploying into production to ensure the chosen configurations work correctly.
- Onboard the SOC team for effective Microsoft Sentinel management and monitoring.
Since Microsoft Sentinel for SAP is billed for the volume of data analyzed and stored in Azure Monitor Log Analytics, deciding which licensing and tier fits your organization can be challenging. Infopulse engineers perform the cost analysis in the pre-deployment stage to recommend a cost-efficient licensing plan according to the client’s specific infrastructure needs. In one of our latest projects, we validated Microsoft Sentinel capabilities for one of the European agriculture leaders and helped reduce licensing costs as part of the proposed solution.
Final Thoughts
Microsoft Sentinel significantly enhances SAP security management while reducing the effort, time, and cost of threat monitoring and response throughout all system layers. Successful and effective implementation highly relies on the following:
- Deep understanding of specific business needs and security challenges
- Proven expertise in deploying and adjusting Microsoft Sentinel for SAP
- High-quality team onboarding for further system management and maintenance.
At Infopulse, we help companies implement efficient SAP systems and enhance SAP security management with up-to-date SIEM & SOAR solutions, including Microsoft Sentinel. As certified Microsoft partners and service providers with 18+ years of practical experience, we are ready to help with all the steps of Microsoft Sentinel for SAP adoption to match all the specific requirements of your business.
![A Guide to Adopt Microsoft Sentinel for SAP [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-microsoft-sentinel-for-sap.webp)






![Security Stack [thumbnail]](/uploads/media/THUMBN~1.WEB)
![Microsoft Sentinel Test Cases [thumbnail]](/uploads/media/5-test-use-cases-of-ms-sentinel-implementation-280x222.webp)
![Microsoft Sentinel Adoption Guide [thumbnail]](/uploads/media/azure-sentinel-how-to-ensure-seamless-integration-and-optimize-your-soc-licensing-costs-280x222.webp)



![Why Implement SAP [thumbnail]](/uploads/media/thumbnail-280x222-why-do-companies-implement-sap-software.webp)
