5 Test Use Cases of Microsoft Sentinel to Implement SIEM and SOAR
SIEM and SOAR Converged: Their Mutual Benefits for Businesses
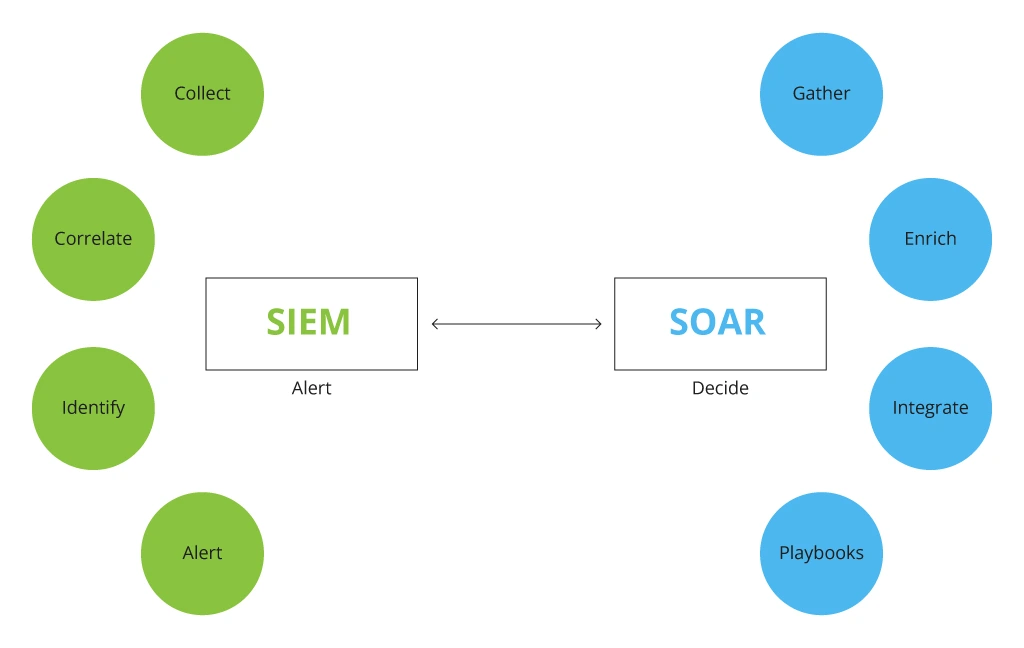
When SOAR appeared on the horizon in 2015, ten years after SIEM’s ascend, many mistakenly considered SOAR as the next evolution step to replace the tool. However, functioning in synergy, these solutions become a vital part of incident resolution management. While SIEM is a threat data collector and analyzer, SOAR operates on the SIEM’s analyzed intel, prioritizing and handling threats, taking a load of ever-growing routine tasks off a SOC team. Operating together, these tools can help not only to resolve but also prevent incidents from happening.
How SIEM and SOAR Work Together
It is the automation of repetitive manual tasks that SOAR adds to SIEM capabilities, allowing it to connect data from various systems and achieve higher visibility of security alerts. Abbreviation of SOAR covers three technologies – SIRP, SOA, and TIP.
Read more about their capabilities in a related blog article by Infopulse “SIEM & SOAR Tools: A Gentle Guide to Selecting the Right Solution”.
Both SIEM and SOAR systems can function autonomously. However, it is their convergence – where SIEM’s job finishes, SOAR picks up – that empowers SOC teams with:
- Streamlined alert management processes – 54% of cybersecurity pros say that SIEM triage is now among the key SOAR use cases
- Accelerated threat discovery and enhanced threat intelligence (57% choose SOAR to enable effective threat intelligence program)
- Reduced mean time to resolution – 70% consider this as the main reason to invest in modern SOAR/SIEM solutions
- Less overhead due to automated repetitive manual tasks performed by SOC.
Microsoft Sentinel as a Response to Traditional SIEM Limitations
In one of the latest SIEM surveys, 96% of decision-makers say that their threat detection has strengthened, however, only 15% are completely satisfied with their security posture after the SIEM adoption. The need for SOAR companionship came mostly from the limitations of a traditional SIEM:
- Excessive alerts made 24% of security specialists leave high-priority alerts unnoticed while spending too much time and resources on false-positive alerts.
- Almost 50% observe slow querying that most often stems from a reliance on their legacy tech stack and traditional SIEM’s on-premises infrastructure.
- Inability to scale operations in a legacy SIEM with the growth of data ingestion volumes.
- Operational overhead (33%) and allocation of high-value labor to routine administrative and maintenance tasks, both sprouting from insufficient automation.
To overcome those limitations, many security teams lean towards the implementation of SaaS solutions, like Microsoft Sentinel, that already combines both SIEM and SOAR functionalities, enriched with AI and numerous Microsoft and non-Microsoft connectors. In 2020, Forrester studied the economic impact of Microsoft Sentinel on those companies that switched from their traditional on-premises SIEM solution to an all-in-one cloud-native SIEM and SOAR solution. For the surveyed companies, having a modern Microsoft Sentinel was 48% more cost-effective than their legacy SIEM.
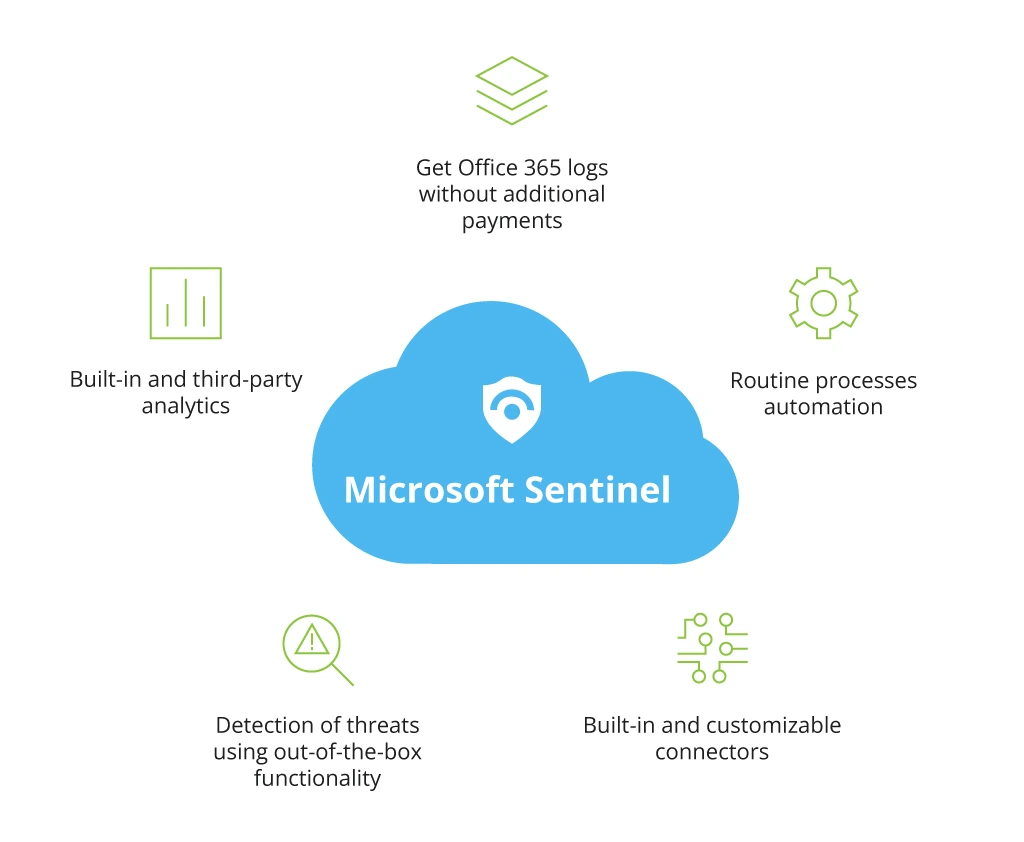
A case in point: when Infopulse helped a client, one of the largest supermarket chains, to decide on a suitable SIEM/SOAR solution that had to meet their security management requirements, our experts made a detailed assessment and comparison of Microsoft Sentinel’s cloud-native capabilities with the available hybrid solutions. Microsoft Sentinel demonstrated more advantages due to its tight integration with other cloud services and its cloud-based security powered by machine learning analytics. When using Microsoft Sentinel as a SIEM/SOAR system, the client can minimize the total cost of ownership of SOAR that does not require a license as a dedicated solution or payments until automation activities are completed.
Comparing Microsoft Sentinel with a Traditional Hybrid/On-Prem Solution
Functionality
Microsoft Sentinel
Traditional SIEM
Software as a Service (SaaS) model allows for unlimited service productivity
✔
—/✔
Optimized pricing model with a pay-per-use feature
✔
—
Integration with Cloud Access Security Broker
✔
—/✔
Built-in integration with Office 365 (Exchange, SharePoint, OneDrive, Teams)
✔
—
Ability to get logs from external network devices (raw network traffic)
✔
✔
Analysis of large amounts of data with minimal delay
✔
—/✔
Higher Teams protection due to the out-of-the-box capabilities of Microsoft Sentinel
✔
—
Unloading SIEM data from the SOAR interface
✔
—/✔
Managing Microsoft Sentinel in a multitenancy environment for SOC, acting as a service
✔
—
Reporting with Power BI for data visualization
✔
$x2
Windows Virtual Desktop Monitoring
✔
—
If you are already considering Microsoft Sentinel implementation, then you should check some best practices for the flawless adoption in our other blog article “Microsoft Sentinel: How to Ensure Seamless Integration and Optimize Your SOC Licensing Costs”.
Five Test Use Cases of Microsoft Sentinel
Another best practice we recommend following is performing test use cases to assess and validate the capabilities of Microsoft Sentinel for your business and define the most winning scenario of the solution implementation into the existing cybersecurity system. For example, Infopulse developed four test cases for a major agricultural company to validate the effectiveness of the solution in regard to their business demands and demonstrate Microsoft Sentinel’s advantages as a single SIEM/SOAR solution. Among them are many automation options for repetitive tasks, decreased license costs, and a roadmap for further integration with the client’s cybersecurity system.
In this blog post, we have gathered the most common test use cases that allow showing Microsoft Sentinel’s SIEM and SOAR capabilities as a cloud-native solution and ways to implement them.
1. Multiple Password Resets by User
This test scenario suggests steps needed to automate password resets or MFA requests when a user account is suspected to be compromised. With Microsoft Sentinel’s SOAR capabilities, it is easier to fully automate common activities needed to rapidly react to unauthorized access.
Actions needed to run a test
Recommendations for implementation
- Collect an extended number of Active Directory logs (Sign-in activity)
- Configure an analytic rule Distributed Password cracking attempts in Azure AD
- Configure an analytic rule Multiple Password Reset by user
- Set security incident notifications when the user account is compromised
- Configure a policy Conditional Access (User risk, Sign-in risk)
- Set up automated actions for a possibly compromised user account with Logic Apps:
- Account lockout
- Force change of a user account password
- Force logoff of all user sessions and enable MFA for another sign-in Conditional Access (User risk, Sign-in risk
2. Detection of Events Based on Indicators of Compromise
Indicators of compromise (IoCs) are forensic intel, the evidence security specialists gather to detect malicious activities that can lead to possible security attacks, data breaches, or other threats compromising the security of existing IT infrastructure. Testing IoCs inclusion into a Microsoft SIEM/SOAR system will most likely demonstrate its potential to act rapidly upon threats and enable remediation scenarios.
Actions needed to run a test
Recommendations for implementation
- Connect public IoCs (a threat intelligence feed)
- Add own IoCs
- Create a KQL-request to detect inclusion of IoCs in the received logs from Cisco ASA
- Set up notifications about potential incidents related to access to a malicious IP address
- Choose public IoCs and order subscriptions to them
- Develop classification of own IoCs
- Configure own IoCs
- Enable SOAR capabilities to respond to any activity from a malicious IP address
3. Identifying Non-Typical Activities of Privileged Accounts
Timely detecting potential threats or abnormal behavior patterns of privileged users whose essential role is to administer the company’s IT infrastructure, software, and critical business systems can help avert critical sensitive data loss and system breaches.
Actions needed to run a test
Recommendations for implementation
- Collect an extended set of Azure Activity logs
- Configure an analytic rule Administrative actions
- Set notifications about the administrative actions on portal.azure.com as an information incident, forming a list of all administrative actions once a day
- Configure a role-based access model to Azure RBAC resources
- Implement a procedure of reviewing access rights Access Review
- Use administrative accounts with limited access rights
- Implement Just In-time Access (JIA) and Just Enough Access (JEA)
- Consider using Azure AD Entitlement Manager
- Create the Logic App notification for a Global Administrator to be informed when administrative accounts are suspected to be compromised
4. Identify Potentially Malicious Scenarios of Using Microsoft Teams
While digital collaboration and communication have become the most requested trends these years, 75% of organizations have deployed Microsoft Teams without integrating security practices. Even more, only 25% actually removed guest users, while the rest faced the risk of being exposed to potential threats not doing so. Obviously, organizations must automate some routine activities like the external users automatic removal not to deal with security incidents in the future.
This use case focuses on testing how Microsoft Sentinel manages the security of digital collaboration in Microsoft Teams, specifically the ability to connect safely with external users.
Actions needed to run a test
Recommendations for implementation
- Collect an extended set of Office 365 logs
- Parse received logs for Microsoft Teams
- Set up Logic Apps to collect logs through Office 365 Management Activity API
- Enable graphic visualization sharing of Microsoft Teams users with external users
- Configure such analytic rules as:
- One user can delete multiple teams
- Adding users to Teams from external organizations
- Ability to add external users to Teams and then remove them
- Creating Owner for multiple teams
- Adding a chatbot or integrating a new application into Teams
- Enable the collaboration of Microsoft Teams users with external users
- Set up the process of sending notifications about security incidents to the existing ITSM system, Exchange, or a Teams channel
5. Identifying Dangerous Activities with Files on SharePoint / OneDrive Coming from New IP Addresses
This test scenario allows assessing Microsoft Sentinel’s SIEM/SOAR ability to check and ensure the security of SharePoint / OneDrive data received from new IP addresses.
Actions needed to run a test
Recommendations for implementation
- Collect an extended set of Office 365 logs
- Parse received logs for SharePoint / OneDrive
- Configure Logic Apps for collecting logs through Office 365 Management Activity API
- Configure the analytic ruleSharePointFileOperation via previously unseen IPs
- Set up a process of sending notifications about security incidents to the existing ITSM system, Exchange, or a Teams channel
Conclusion
While SIEM and SOAR are quite different in their purposes, they perfectly complement each other and can be implemented as part of a single solution such as Microsoft Sentinel that allows using the best of both worlds. When comparing this solution with the traditional SIEM system, you can see how many gaps the latter may have in regard to costs and operational capabilities. Before implementing Microsoft Sentinel, you can check its validity by applying the specific test use cases that we describe in this article. And if you are ready for getting started with a consolidated SIEM and SOAR solution, please check a dedicated Microsoft Sentinel service we offer together with our profound expertise in this solution implementation.
![Microsoft Sentinel Test Cases [banner]](https://www.infopulse.com/uploads/media/5-test-use-cases-of-ms-sentinel-implementation-1920x528.webp)

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


