SIP Hacking: Ways to Protect Your VoIP Services
Seamless scaling, lower implementation costs, and the rising demand among end-customers make Voice over IP (VoIP) services an attractive new business avenue for telecoms. So much so that by 2025, the global VoIP industry is expected to reach $55 billion.
While the benefits of VoIP adoption are certainly attractive, they are somewhat offset by the increased cybersecurity risks this new technology poses. Legacy on-premises systems required physical access for hacking, whereas VoIP devices and networks can be compromised remotely. In 2017, nearly 46% of all fraudulent calls in the world were made using VoIP technology. We can assume that today the figure has hardly gone any lower.
Lack of standardization among IP phone manufacturers and PBX device providers have made the job of protecting individual systems harder for businesses. For telecom providers, the security challenges of VoIP are further amplified by the over-reliance on two dominating VoIP protocols – SIP (Session Initiation Protocol) and SCCP (Skinny Client Control Protocol).
In this new installment of our Definitive Guide to Telecom Security, we’ll discuss how to identify and prevent SIP hacking in VoIP.
The Common Types of VoIP Attacks To Watch Out For
VoIP technology is as robust and secure as traditional telephony and is arguably more secure than a traditional cellular connection. However, every network needs to be properly configured and strengthened to be fully hacker-proof.
Most VoIP cyber attacks originate from the fact that administrators fail to put proper protective measures in place:
- Set up isolated VoIP networks with open physical access, weak VPNs, or MPLS.
- Over-reliance on automation tools for setting the defense perimeter, and thus, miss certain vulnerabilities.
- Fail to set proper protection against network-based attacks such as DOS, DDoS, phishing, surveillance and spying, VAS services abuses.
- Fail to configure the VoIP devices properly – rely on weak passwords, use legacy software, and leverage vulnerable protocols.
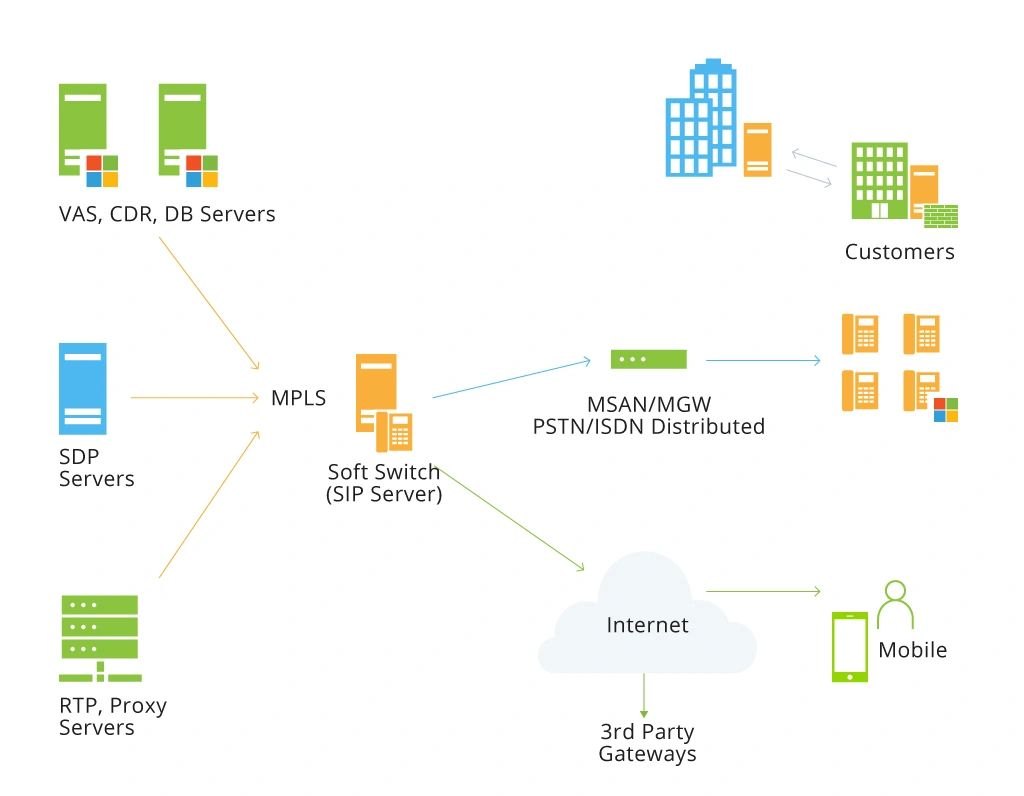
All of the above often leads to the following VoIP security attacks and SIP hacking in particular. After all, SIP servers are positioned in the heart of both internal IP telephony and commercial services as pictured:
Distributed Denial of Service Tests
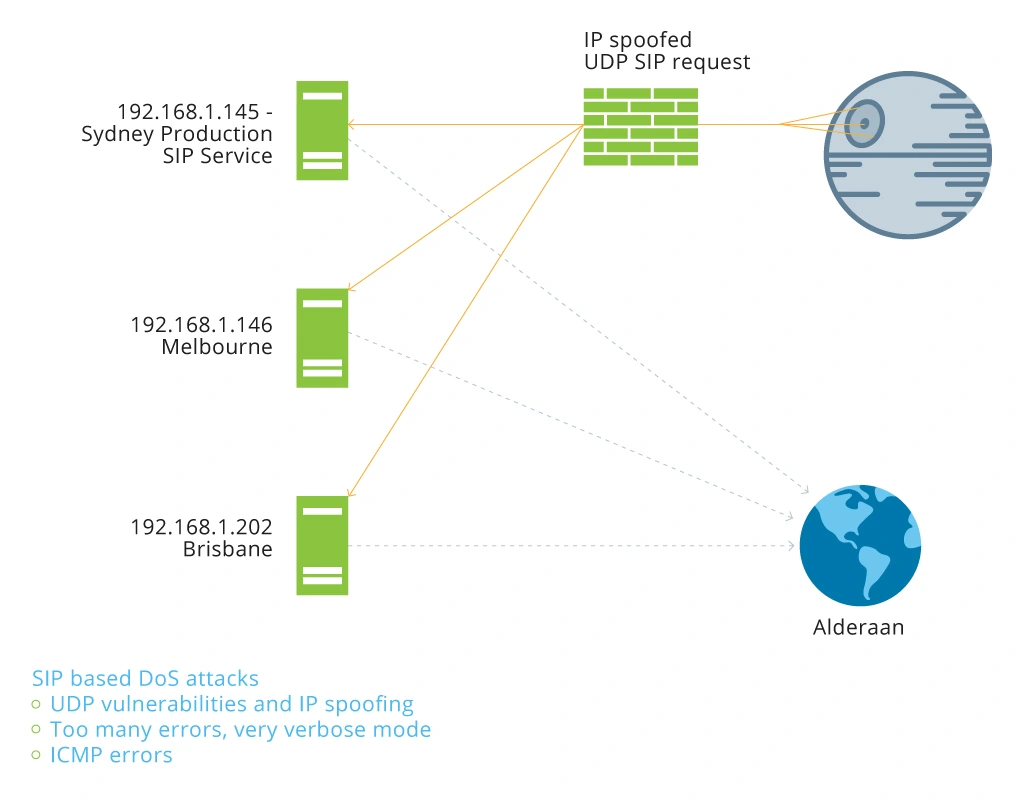
This is the reason why protecting your SIP servers is mission-critical. Below are four types of SIP hacks that have gained popularity in the telecom industry over the past several years:
DDoS – SIP Amplification Attack
SIP hacking remains one of the most pervasive security threats in the telecom domain as this protocol has become commonly used in VoIP systems. A SIP amplification attack usually assumes the following scenario:
A hacker stages a mass application layer attack on the SIP protocol using DDoS aiming to destabilize the system. For instance, the attacker may compromise the SIP servers to send multiple (10+) errors, so that they could transmit IP Spoofed packets and multiple Responses to the victim.
SIP Services: Commercial
Hacking SIP Trust Relationships
SIP gateways use SIP Trunks for a trusted call initiation and CDR/invoice management which makes them attractive targets for VoIP attacks. Beyond that, SIP trunks often have no passwords or IP-based filters used for trunk authentication. Most SIP trunks also have Direct INVITE privilege without REGISTER, again becoming a good avenue for attacks.
A typical SIP trust relationship hack will involve the following steps:
- A hacker locates Trusted SIP Networks;
- They send IP Spoofed Requests from each combination IP: Port;
- Specifically, they’ll target calls that contain IP: Port in “From” section;
- Once they have a call, they’ll capture the Trusted SIP Gateway IP and Port and use it to initiate unauthorized calls.
Spoofed INVITE Requests
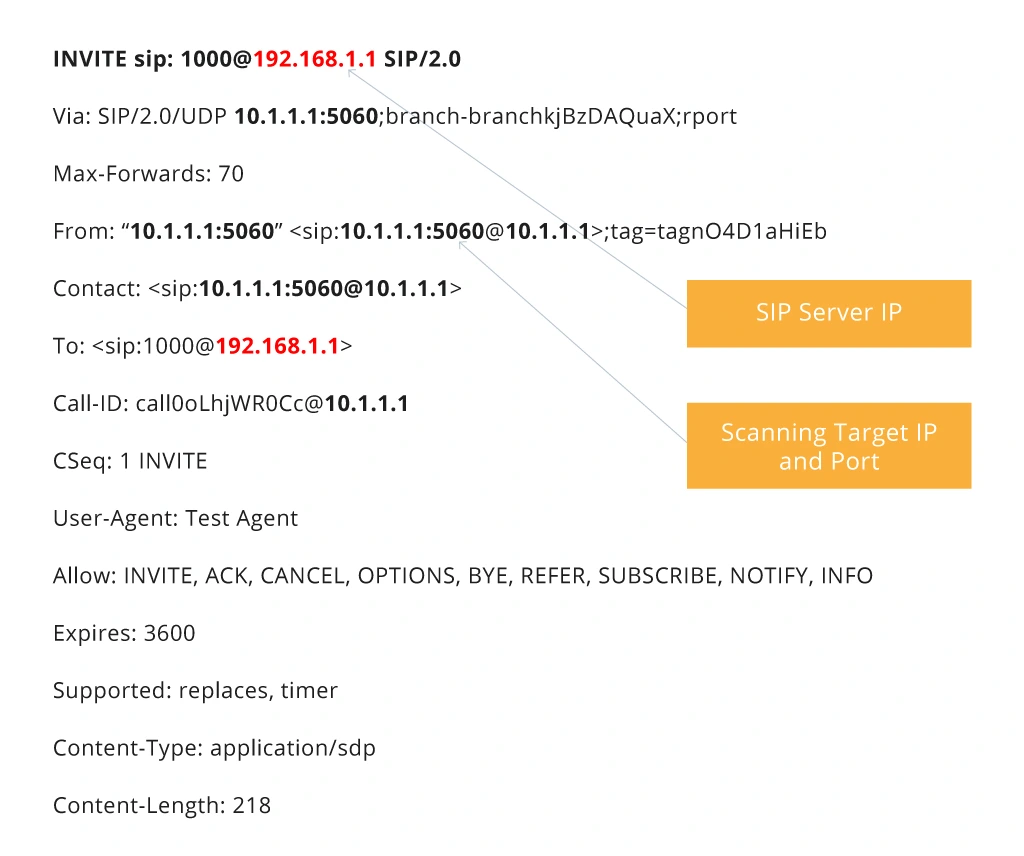
SIP Authentication Attacks
SIP 2.0 relies on the MD5 message-digest algorithm for hashing the UAC password to add an extra layer of protection to VoIP systems.
The problem with such an authentication approach is that it isn’t fully secure either. Here’s why: when UAC wants to authenticate with a UAS, the latter generates and dispatches a digest challenge to the UAC. The simplest authentication challenge contains:
- a Realm – necessary to identify credentials within a SIP message;
- a Nonce – a unique MD5 string generated by the UAC for each registration request. A Nonce has a timestamp and a secret non-reusable phrase that guarantees a limited lifetime.
WWW-Authenticate: Digest algorithm=MD5, realm=”asterisk”, nonce=”3cf75870”
After the UAC gets the digest challenge and the user provides their credentials, the client will then use the Nonce to generate a digest response and dispatch it back to the server:
Authorization: Digest username=”1234”realm=”asterisk”,nonce=”3cf75870”, uri=”sip:1000@192.168.101.105”,response=”cf89107228a444c1e8b761dfb6e669e4”, algorithm=MD5
The UAS will then execute the same process to generate its own MD5 hash. If it matches the one received from the UAC, UAS will authenticate the UAC with a “200 OK” message.
However, hashed passwords no longer suffice to protect VoIP systems against elaborate authentication attacks. Hackers can now crack MD5 cash and gain access to a SIP authentication header with a Network Analyzer or perform a brute-force attack.
Spoofing Caller ID
Caller ID doesn’t have enough protection in SIP and hackers have plenty of tools for changing the SIP INVITE Request Message from the header to perform the spoof. In particular, this is a common method of voice fraud used to compromise PBX systems. Thus, if you want to avoid roaming fraud or call hijacking, you need to protect that endpoint too.
How Telecoms Can Protect Their VoIP Services
Mitigating attacks in VoIP environments requires a systematic approach. Build your protection from the bottom up starting with IP phones and ending with comprehensive network security testing and occasional penetration tests.
IP Phones Protection
IP phones present a physical pathway to deeper network penetration. Do not underestimate the importance of basic precautions, such as:
- Protection against unauthorized usage and calls.
- Mandatory usage of extra security codes when dialing international or toll numbers.
- Addition of regularly updated security codes for regular usage.
- Implementation of geo-fencing for general users.
- Regular firmware updates on all phones.
On a network level, you should also consider implementing the following solutions against VoIP attacks:
- Voice packet encryption to/from any VoIP phone. You can configure your device to add SIPS instead of SIP at the start of address by default to auto-execute call encryption using Transport Layer Security (TLS). Alternatively, you can consider setting up a virtual private network (VPN) or virtual LAN (VLAN) to protect your connection further.
- Segregate voice on a separate voice VLAN. Doing so can help you further protect all the voice traffic.
- Set up a SIP-capable firewall to sift through message contents and capture malware, along with other types of spoofing.
- Regularly evaluate your VLAN configuration, user authentication mechanisms, and the security of configuring and signaling methods. As you do so, also verify that you are compliant with HIPAA, SOX, or PCI recommendations if those apply to you.
IP PBXs Security
Most IP PBXs rely on Linux-based or Windows-based servers that can be hacked into by a malicious party unless there are certain precautions in place. Specifically, you’ll need to ensure that:
- Your servers have the latest antivirus, software firewalls, and malware protection software installed.
- Regular data backups are configured.
Some IP PBXs systems may rely on router-type appliances, rather than servers, that should also be hardened following these best practices:
- Use strong passwords.
- Enable encrypted management communication.
- Create access lists for blocking malicious IP address ranges and Transport Layer ports.
- Revoke access to any services that are not in regular use.
SIP Trunks Safeguarding
As mentioned already, SIP trunks can be a weak security link for hacking since voice packets can be overtaken as they travel between two SIP endpoints. To protect that connection, look beyond the standard hashed password encryption. Some of the key measures to consider are as follows:
- Verify that encryption is applied to both the voice portion of the communication and the SIP signaling and control packets.
- Limit the number of devices that can establish contact with your SIP trunk.
- Set a secure protocol and session validity that cover SIP port settings, SIP protocol inspection and termination, registration, and authentication methods.
- Implement privacy control mechanisms for all SIP trunk sessions. Properly configure SIP privacy headers, enable SIP normalization, protect against digit manipulation, and add extra encryption methods for the signaling and the media streams, such as TLS, IPSec tunnel, or VPNs on the IP connections.
Regular Network Testing
Last, but not least – conduct regular security audits and tests of your VoIP systems. We recommend using the SIPVicious OSS toolkit for SIP audits and the Viproy penetration testing kit, designed specifically for VoIP systems. Beyond that, you can also explore the newer generation of AI-based network security and monitoring solutions that are emerging on the market.
Being proactive when it comes to your network security pays off manifolds as you handle potential vulnerabilities in advance instead of throwing emergency resources into dealing with the complex (and costly) aftermath of compromised VoIP devices or part of your network.
To Conclude
VoIP security is a matter every business should address. While SIP hacks are popular, most of them can be effectively mitigated with the essential device and networking best practices we described in this post. The key is being diligent and systematic when it comes to endpoint protection and proactive in terms of network security audits and testing.
Infopulse telecom security team would be delighted to further assist you with securing your VoIP services. A trusted partner to leading telecom providers, our team can help you build an advanced security perimeter for your operations, protecting you against existing and emerging threats. Contact us!



![CX with Virtual Assistants in Telecom [thumbnail]](/uploads/media/280x222-how-to-improve-cx-in-telecom-with-virtual-assistants.webp)
![Power Apps Licensing Guide [thumbnail]](/uploads/media/thumbnail-280x222-power-apps-licensing-guide.webp)
![Expanding NOC into Service Monitoring [thumbnail]](/uploads/media/280x222-best-practices-of-expanding-telecom-noc.webp)
![Cloud-Native for Banking [thumbnail]](/uploads/media/cloud-native-solutions-for-banking_280x222.webp)
![Generative AI and Power BI [thumbnail]](/uploads/media/thumbnail-280x222-generative-AI-and-Power-BI-a-powerful.webp)
![Data Governance in Healthcare [thumbnail]](/uploads/media/blog-post-data-governance-in-healthcare_280x222.webp)
![Super Apps Review [thumbnail]](/uploads/media/thumbnail-280x222-introducing-Super-App-a-Better-Approach-to-All-in-One-Experience.webp)
![SAP Service Insight [thumbnail]](/uploads/media/Service Insight-Infopulse-SAP-Vendor-280x222.webp)
