How to Enable Zero Trust Model by Implementing Azure Active Directory
According to the 2020 Zero Trust Progress Report, 72% of surveyed organizations put forward plans for implementing Zero Trust capabilities at least to some extent in 2020. What makes a Zero Trust security model so appealing to organizations? Should your company consider this approach as well? Let us strategize together.
What is a Zero Trust Model? Trust Nothing, Verify Everything
Zero Trust Network or Zero Trust Architecture is not a new technical concept per se. Originally proposed by John Kindervag, a principal analyst at Forrester at that time, the premises of this concept were simple:
Later on, the model underwent several iterations and expanded into an array of technical implementations, plus secure network and infrastructure architectures. The baseline principles remained the same: organizations develop cybersecurity plans using the idea that all access requests (internal or external) are non-safe by default. Thus, every request originating from any source should be provided with the least privilege for access before it is authenticated, authorized, and reviewed.
On the surface, such a level of “suspicion” may seem excessive. However, the latest cybersecurity statistics and events prove otherwise:
- 59% of EY survey respondents said their organization had experienced a minor or significant cybersecurity incident in the past 12 months.
- Accenture reports that on average, cybersecurity programs safeguard only 60% of the company’s ecosystem. That is problematic since 40% of security breaches originate from indirect attacks through the ecosystem.
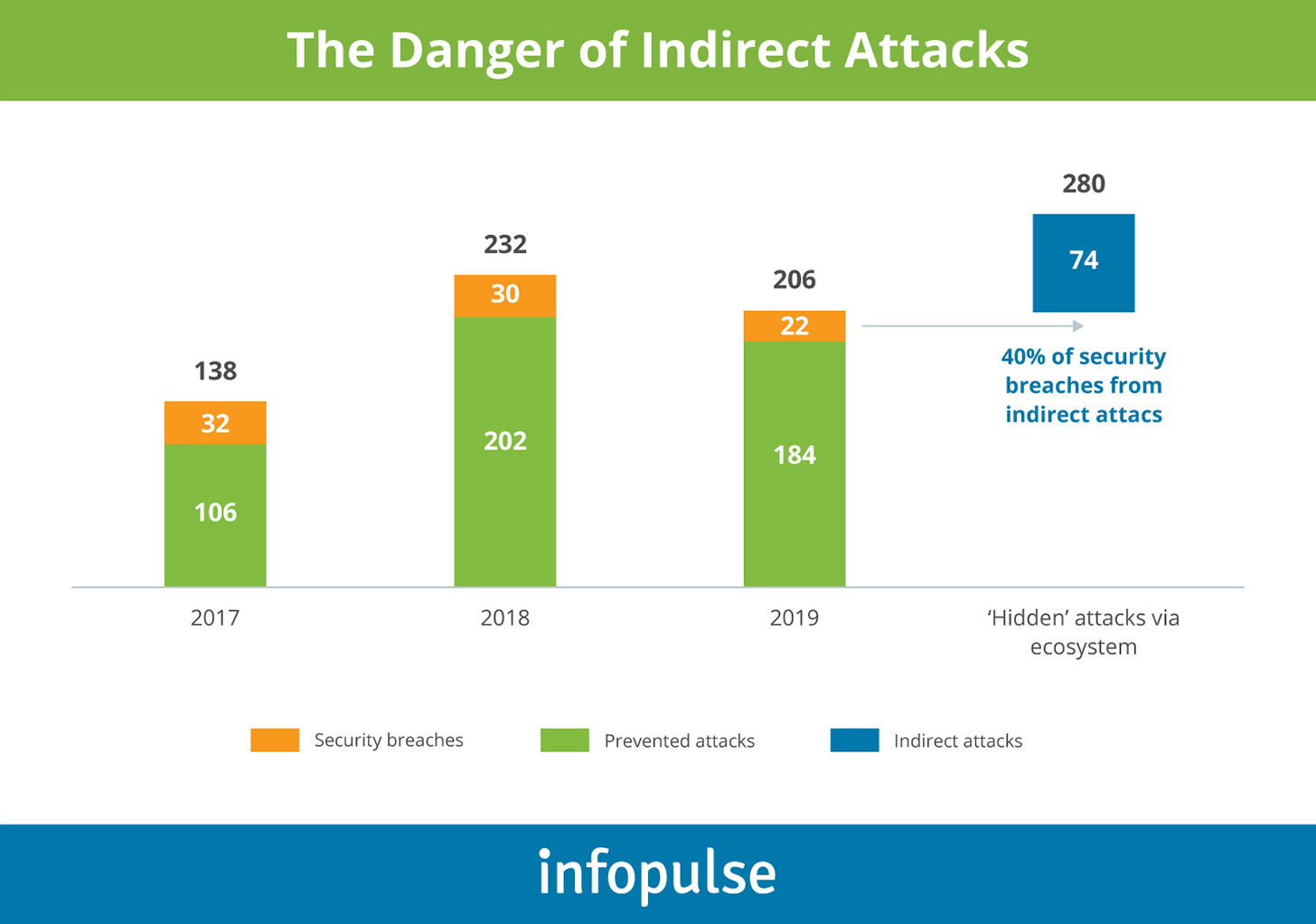
Indeed, many organizations today operate an ever-expanding digital footprint of globally distributed applications, hybrid cloud infrastructure, connected IoT and edge devices, and diverse users, connecting to the ecosystem via APIs, VPNs, and custom-built integrations.
With such ubiquity of ecosystem participants, organizations need to carefully balance the need for secure, seamless connectivity to company resources with staunch protection against diverse threats.
In the current cyber threat environment, perimeter-based network defenses with multiple layers of disjointed security technologies have proven insufficient to meet cybersecurity needs. The corporate infrastructure needs to be secured in a unified yet more granular way. Zero Trust security model and supporting tools such as Azure Active Directory (AD), Azure Security Center, and Azure Sentinel among others help set up full-proof protection against sophisticated threats.
Benefits of Zero Trust Security Model
- Modern, flexible approach to cybersecurity
- Enhanced data protection
- Data breaches protection and prevention
- Greater protection for IoT devices
- Lower complexity (and cost) of cybersecurity stack
- Flexible, remote work, and multi-cloud compatible security
- Does not undermine user experience
Three Main Principles of Zero Trust Approach
The Zero Trust model advocates cybersecurity professionals to treat any asset — connection request, data transmission, app, user, or device — as “guilty unless proved otherwise”.
Think of Zero Trust in the following manner: you do not invite a stranger to your home unless you learn something about them first, e.g. their name, purpose of visit, background, etc. Zero Trust encourages you to do the same — learn as much as you can about the request origin before granting access to your ecosystem. This is done using the next three principles:
- Explicit user credential verification. Authenticate and authorize users based on multiple data points — location, IP, device, credentials, etc. — using strong security methods such as MFA, SSO, or biometrics. After granting access, also verify that the user does not abuse the provided privilege and does only what is intended.
- Grant the least amount of privilege first. Reveal information progressively to the users. Create access hierarchies and scoped roles for accessing different types of data. Entrust the user with the least amount of privilege they need to do their job. “Idle curiosity” is a common reason for accidental disclosures and internal breaches. For instance, last year two Shopify support team members abused their rights for accessing customer transaction records, which resulted in a data breach involving 200 merchants on the platform.
- Assume a breach. Network traffic visibility is the focus of the Zero Trust security model. By implementing automated inspection and logging, using end-to-end encryption and security analysis, you should continuously strive to expand the boundaries of your threat detection capabilities.
The above three principles are applied in a modern setting automatically in a matter of moments.
6 Essential Components of the Zero Trust Model
While cybersecurity and Zero Trust are a top-of-mind corporate priority, 47% of cybersecurity teams indicate that they lack confidence in applying this model to their Secure Access architecture.
At a high level, Zero Trust assumes using micro-segmentation, granular security perimeter enforcement, and continuous security monitoring based on known data about the user, device, or application seeking access.
On a lower level, Zero Trust architectural implementations will vary depending on the security technology you are using. In our case, we will focus on the tech stack provided by Microsoft for Zero Trust and Azure Active Directory in particular.
If you plan to implement Zero Trust security model with Azure to protect cloud assets, infrastructure, and users, you will need protection plans for the following six elements:
- Identities. These include users, devices, and third-party services, accessing your ecosystem. In each case, you will need to establish an optimal identity management governance framework for determining authentication methods and levels of privilege.
- Endpoints. Every device requesting a connection should be properly identified and authorized. Moreover, the connected devices should be kept under continuous monitoring to detect and prevent any signs of being compromised.
- Applications. On-premises, hybrid, and cloud-native applications, alongside APIs, should be granted the necessary access controls and be protected via secure configurations. Implementing traffic monitoring and usage analytics also makes sense for applications processing sensitive data.
- Data. Business and customer data security is critical for both regulatory compliance and business reasons. Data breaches trigger a cascading effect of direct and indirect costs with the average cost hovering at $3.86 million. Thus, ensure that you have the proper facets for protecting stored, exchanged and analyzed data.
- Infrastructure. Cloud security remains a hot-button issue as companies continue with asset migration. Aging legacy infrastructure also poses significant risks. Access control, usage monitoring, end-point protection, and anomaly detection are among the crucial security tasks.
- Networks. Network security, threat detection, and security monitoring are the three areas with the sharpest increase in security costs. That makes sense given that business leaders now need to support a larger array of remote devices and a growing volume of data exchanges. This results in a growing need for end-to-end encryption, traffic monitoring, and analysis.
Azure AD — the Cornerstone Element of Zero Trust
Microsoft Azure Active Directory is the company’s dedicated solution for creating a secure identity management infrastructure, including one governed by Zero Trust principles. In particular, Azure AD enables:
User privilege verification and management:
- Strong authentication for all users (MFA, SSO, Passwordless Sign-in).
- Introduce greater control over user devices with Azure AD Hybrid Join or Azure AD Join — a tool designed to allow a secure rich client access to data from company-supported devices.
- Microsoft Intune helps collect data about the user’s mobile devices to determine whether they can be trusted or not.
Grant lowest privilege first:
- Robust and flexible functionality for privilege identity management.
- Conditional access capabilities — an intelligent engine auto-verifies all access requests based on user identity, device risk, environment, etc.
- Centralized view into all the applications users can access and why/when the access was granted. Azure AD Premium P2 users can also exercise entitlement management and grant the user an access package — a bundle of permissions and privileges they need based on their role or to work on a specific project for a limited time.
- User consent to application management and restrictions to prevent unauthorized access to corporate data by various applications.
- Automatic creation, management, and termination of user identities in your SaaS applications based on business and security rules. Such automatic provisioning helps you rapidly scale your identity management system without undermining security.
Assume a breach:
- Passwords present a security nuance. You can use the Azure AD Password Protection service to enforce a user-friendly, yet robust password policy across your organization. The tool covers both cloud and on-premises users.
- Leverage identity protection (Azure AD Premium 2 feature). This tool automatically detects identity-based risks, pitches remediation passes and performs ongoing monitoring of risks using the available data. The service can be handy for protecting users with the highest level of privileges and access to the most sensitive data. Intel obtained from this tool can be passed over to other Microsoft services, such as Conditional Access, to adjust rules policy or to be fed to a SIEM solution.
- Configure restricted sessions. You can allow low-risk users to access only certain functionality from an unknown device, but prevent them from meddling with more critical applications or data without further authentication.
Other Microsoft security products you may consider using include Microsoft Cloud App Security (MCAS) and Microsoft Defender for Identity.
The following half an hour video further explains how to implement Zero Trust security with Azure AD:
To Conclude
Cybersecurity has become an intricate task for digitally mature organizations with diverse assets due for protection. Zero Trust model helps set a multi-checkpoint security system, focused on minimizing the risks of accidental or intentional security compromises or misbehaviors.
While rigid on the surface level, in reality, Zero Trust helps create a flexible security perimeter, conducive to remote work, multi-cloud and hybrid infrastructure, edge deployments, and mobile connectivity, especially if you are using Azure Active Directory and other Microsoft products.
Infopulse has been a Microsoft Certified Partner since 2004. We have significant breadth and depth product knowledge, as well as domain experience in cybersecurity. Contact us to receive a preliminary consultation on securing your infrastructure.

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


