How to Build AWS Security Hub for Enterprise
AWS Security Hub is the natural choice for companies with significant IT infrastructure hosted in the AWS cloud environment. This guide explains how to set up and configure AWS Security Hub to maximize its value.
How to Set Up Your AWS Security Hub
As the name indicates, AWS Security Hub is an “umbrella” solution for collecting and managing security telemetry data — from emails, endpoints, servers, clouds, and networks — in a centralized manner.
That said: AWS Security Hub also offers a great level of granularity. You can choose which sub-tools and -services to integrate based on your technical estate size and security needs. In other words: You can create a purpose-built solution for your SOC team instead of opting for an out-of-the-box set of features.
Customization is definitely an advantage as it allows you to establish cost- and resource-efficient SOAR workflows. However, the scope of setup possibilities also leaves many business leaders confused about the exact implementation process.
This section breaks down the key steps of the AWS Security Hub setup that Infopulse cybersecurity team relies upon.
Define Business Needs for AWS Security Hub Adoption
Adopting any type of technology for its own sake never brings tangible returns. To gain measurable ROI from your AWS Security Hub investments, you need to define your goals first.
As we previously wrote, there are many benefits to using AWS Security Hub:
- Centralization of security data, which improves your incident detection capabilities
- Higher security workforce productivity with intelligent workflow automation
- Streamlined compliance checks with existing security rules of threat prevention
- More in-depth and timely-data for proactive vulnerability detection and prevention.
Overall, AWS Security Hub is a robust solution for security data aggregation, automation of routine security checks, and intelligence alerting across large technology portfolios.
However, the quantifiable impacts of such benefits will differ depending on the company’s cybersecurity maturity levels. To benefit from this solution, you should have respective information security processes and practices in place such as:
- Internet traffic protection systems
- Network and wireless security protocols
- Identity and access management tools
- Rules for protecting remote access
- IT infrastructure monitoring solutions.
Essentially, AWS Security Hub works best for organizations with established SOC teams or those who are proactively preparing for SOC adoption.
Create a Set of Specific Use Cases
Your wider business needs should be further formalized as specific use cases — a list of business risks and security vulnerabilities you want to protect your business from. Based on the above, you then determine which data streams and tools you will need in place to effectively identify, mitigate, and resolve the said issues.
As part of our IT Security Assessments, we usually ask clients: What types of events would you like to detect? For example, get alerted to upcoming security certificate expiration or abnormal user behaviors such as multiple password reset updates. Based on the above, we determine where you can locate the security log data.
Security logs originate from multiple places — Web Application Firewall (WAF), identity and access management solutions, and individual applications. The advantage of AWS Security Hub is that this service can consolidate log data from all across the AWS ecosystem and external SIEM/SOAR tools.
Data availability, however, can be a double-edged sword. Just because certain security logs are available, it does not mean your organization needs to collect them.
Remember AWS Security Hub bills users for both ingested data and performed security checks. Your bill can grow significantly if you haphazardly ingest log data without any prior filtering. At the same time, you do not gain any additional security improvements if the ingested data is irrelevant.
Our recommendation: Start with the minimum required intel to fulfil your use cases. Later on, you can always enable extra collection if your needs change or new cyber threats emerge.
Codify the above principle into a set of specific rules for alerting and alert prioritization, plus use the underlying use cases to develop issue response scenarios for your SOC team.
Much of the SOC team’s value comes from the playbooks and runbooks they use.
Both are designed specifically for your organization by the SOC team and are a key element of high performance.
Build a Solution Architecture
With use cases defined, you are ready to develop reference architecture. Remember: AWS Security Hub is not a standalone SIEM tool, but rather a platform for aggregating and managing data from multiple security tools from Amazon and other vendors. Its primary purpose: Supply you with a consolidated view into your infrastructure and centralize security workflows.
Therefore, it is your task to decide which assets should be monitored; how the log data will be collected and transmitted to the cloud.
Once again, you have options here. You can use:
- Native Amazon security tools
- Third-party tools via AWS Marketplace
- Custom integrations with other products.
Below, we provide an overview of each option with several reference examples.
Native Integrations
Naturally, AWS Security Hub integrates with all other AWS security tools including:
- AWS Identity and Access Management Access Analyzer
- Amazon Inspector
- Amazon Macie
- AWS Systems Manager Patch Manager
- AWS Audit Manager
- Amazon Detective
- AWS Systems Manager Explorer and OpsCenter
- AWS Trusted Advisor
As mentioned earlier, you will probably not need all of these tools (which also come with separate licensing costs). The selected use cases will determine which types of tools and integrations you will need.
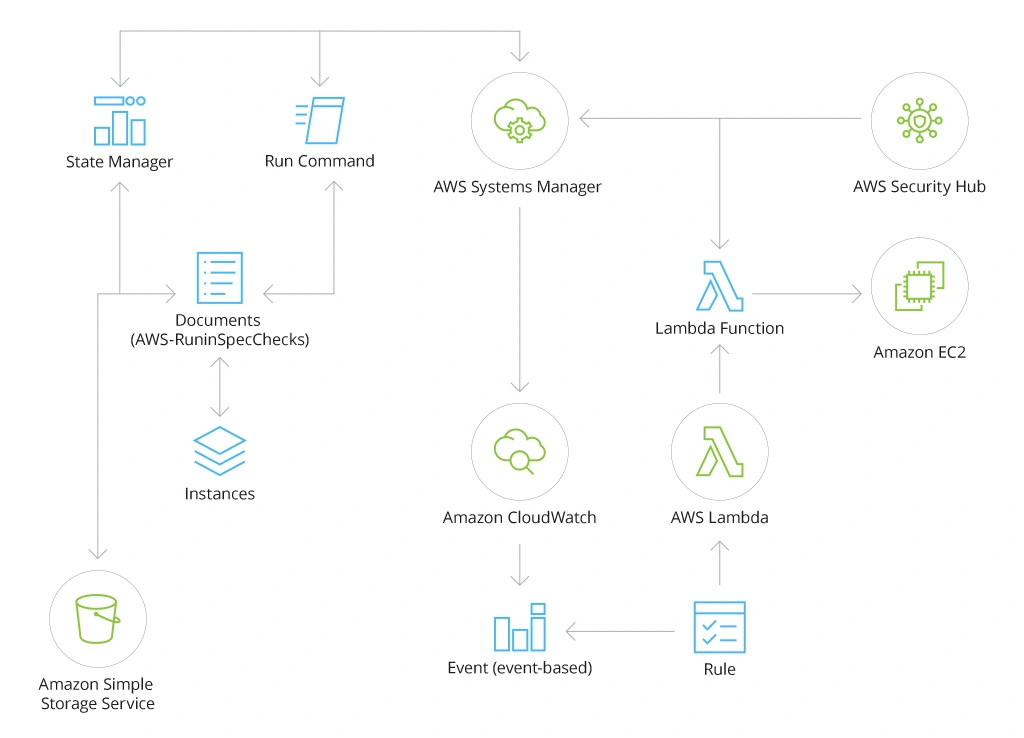
Let’s say, you want to improve your compliance monitoring for Amazon EC2 instances. Your security team spelled out specific requirements and you want to automatically verify their adherence across all instances and get alerted about any deviations.
To implement this use case, you can rely primarily on AWS Systems Manager — an operational data aggregator that collects information from multiple AWS services.
Here is how a reference architecture looks like for such scenario:
AWS Marketplace Integrations
AWS Marketplace is a database of all pre-made integrations and connectors available for third-party services. Among them, you will find integrations with over 2600 security tools.
Marketplace integrations offer a fast and easy way to integrate more tools into your AWS Security Hub to collect extra data. For example, you can add CyberArk to detect behavior anomalies among privileged user accounts and receive high-fidelity intel for threat mitigation and prevention.
Custom Integrations
Finally, you can build custom data ingestion pipelines for AWS Security Hub to integrate log data from applications directly. For such use cases, you will have to rely on connector APIs and AWS CloudTrail tools.
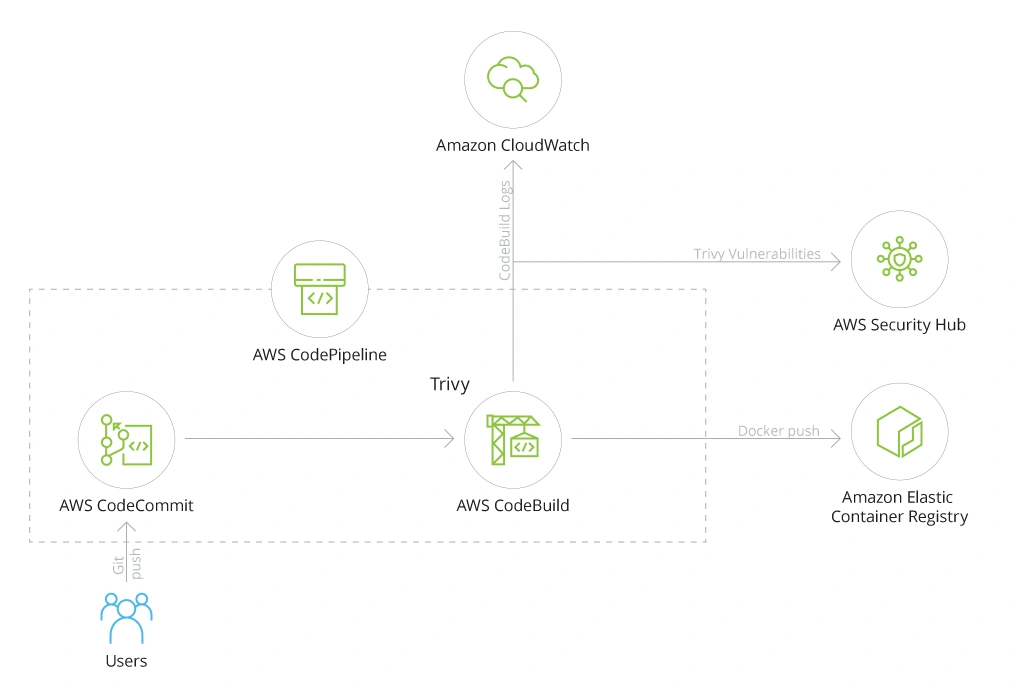
Let’s take a look at several scenarios. For example, you want to implement security-by-design principles to harden your custom application(s). For that purpose, you want to add automated container vulnerability scanning to your continuous integration and continuous delivery (CI/CD) pipeline — and have the collected data sent to AWS Security Hub.
In this case, the architecture will be as follows:
In short, you configure an open-source container vulnerability scanner, Trivy, to auto-send relevant logs to Amazon CloudWatch service and vulnerability scans to AWS Security Hub. Based on predefined rules, AWS Security Hub will auto-assess the scans and alert you of potential issues (if any) before the container gets deployed to the Amazon Elastic Container Registry. This is an effective checkbox mechanic for improving the security of shipped software.
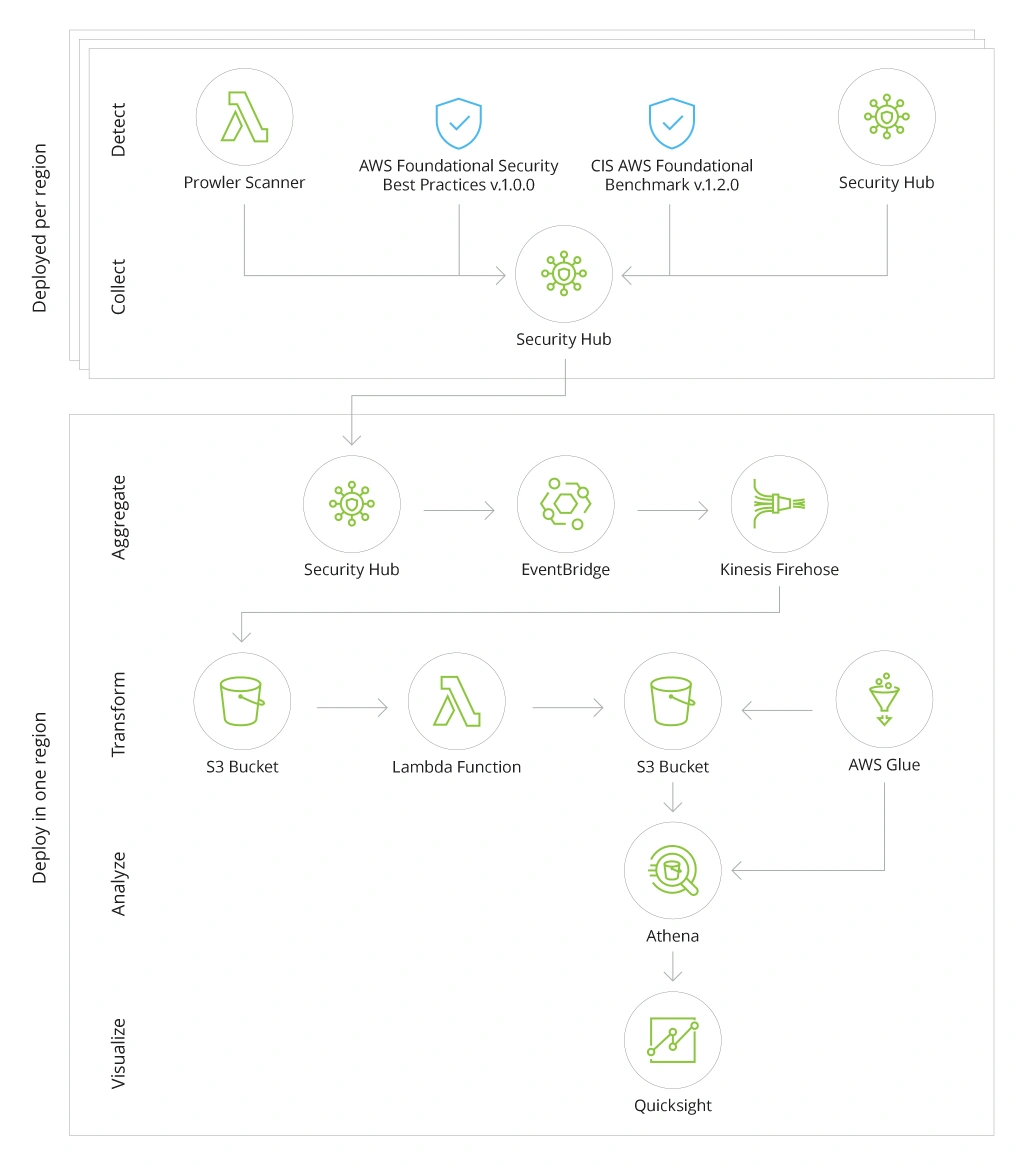
A more complex scenario would be building a multi-region AWS Security Hub analytic pipeline to get fused insights from across all assets. You can also visualize this data into real-time reports using Amazon QuickSight — a BI service from Amazon.
Here is a high-level architecture reference for this case:
To enable this use case, you will first have to deploy the infrastructure for detecting, ingesting, and transforming the required data. AWS Cloud Development Kit (AWS CDK) provides you with all the tools you need.
Afterwards, you can determine which data sources you want to use:
- Built-in security standards in AWS Security Hub
- Other AWS security services
- Third-party partner products
To ensure proper processing, use the cross-region aggregation feature within Security Hub. For data transmissions, you will have to rely on Amazon EventBridge and Amazon Kinesis Data Firehose.
Note: The ingested data will then have to be transformed to become compatible with Amazon Athena (a data querying tool) and stored into a respective Amazon S3 bucket. Once it is in the right format, you can feed it to Amazon QuickSight for advanced analytics.
Final Thoughts
AWS Security Hub helps you create a “single source of truth” for all security information, aggregated across the entire infrastructure — and then effectively operationalize it using built-in, native, and third-party security tools.
Apart from improving the coverage and efficiency of your security checks, AWS Security Hub also helps you ensure company-wide compliance with baseline security policies. Given that 82% of data breaches involve some degree of human error (including non-compliance with standing policies), AWS Security Hub can help your security professionals identify and resolve those minor issues before they turn into a major incident.
![Building AWS Security Hub [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-enterprise-guide-to-building-your-aws-security-hub.webp)

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


