How to Strike a Balance Between Security Operations and New Solutions Implementations
In response, organizations continue to ramp up their investments in the cybersecurity function. Gartner expects corporate spending on security and risk management to increase by 14% YoY and reach $215 billion globally. Cybersecurity services, a segment that includes consulting, IT outsourcing, implementation, and hardware support, will account for 42% of all spending.
Clearly, businesses are bullish on improving their cybersecurity programs. However, in doing so, some leaders tend to underestimate the importance (and capacity needs) of maintaining effective security operations. Effective cyber teams maintain a dual focus on security operations and security development — implementation of new policies, practices, playbooks, and technology solutions for ensuring higher levels of corporate protection.
An imbalanced distribution of resources between these two processes can fold back, rather than propel forward, your cybersecurity efforts.
What Is Security Operations (SecOps)?
SecOps, short for Security Operations, is the collection of processes and practices, aimed at ensuring effective identification, response, and protection against security threats and ability. In simpler terms, it’s all the work junior SOC team members (L1 professionals) perform to ensure proactive threat mitigation and rapid incident response.
The common security operation processes include:
- Security monitoring and analysis
- Incident response
- Vulnerability management
- Access and identity management (IAM)
- Incident management
- Security Information and Event Management (SIEM)
- Threat intelligence collection and analysis
- Network and endpoint security
Effectively, security operation professionals keep watch over all the digital infrastructure that needs to be protected (e.g., individual applications, databases, servers, cloud computing services, network endpoints, etc). Their job is to process the incoming intel — investigate alerts, perform routine maintenance tasks (e.g., patching and firewall updates), and assist with vulnerability assessments.
What Is Security Development?
Security development is the process of implementing new policies, practices, and technological solutions to improve the company’s security posture. While security operations professionals ensure that all the current bases are covered, senior security analysis assesses how the current processes can be improved further and what extra solutions may be required to further improve the company’s posture (for example, an upgrade from a legacy on-premises WAF to a cloud-based solution).
Typically, senior L2 professionals and L3 specialists spend more of their time strategizing new structures and processing for controlling cybersecurity operations and responding to changes in the cyber-risk landscape.
The common security development processes include:
- Policies and playbook creations
- Cybersecurity software implementation
- Incident simulation and red teaming
- User training and awareness
- Business continuity and disaster recovery planning
- Security tools development and customization
In other words: Security development is more focused on implementing new best practices and solutions that are based on the intel, discovered by the analyst, and obtained during pen tests. L3 professionals also help develop new incident response plans, which define the processes, roles, and responsibilities in the event of a threat, plus set the metrics for measuring the success of the incident response activities.
Also, senior professionals often work closely with the CTO/CISO to determine the next cybersecurity technology acquisitions and create plans for their implementation.
How to Strike a Balance Between Security Operations and New Solutions Development
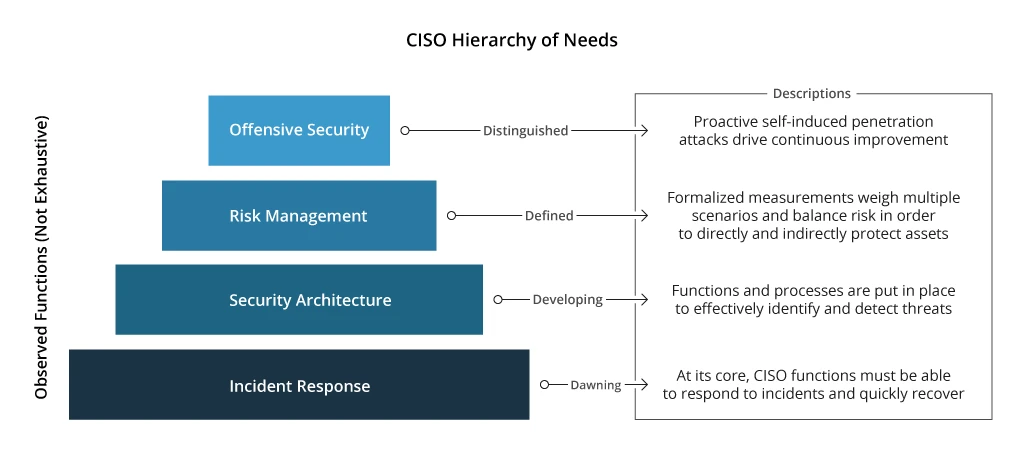
Cybersecurity teams have a three-tier, pyramid-like structure, reflecting the wider scope of the organizations’ needs.
The above needs can be conflicting, however. For example, you may decide to switch more people towards implementing new controls for better risk management at the expense of having fewer people to deal with alert investigations.
When your organization is overly focused on implementing new cybersecurity solutions (e.g., all hands are on deck to secure newly acquired data storage locations one after another), you may overlook vulnerabilities in other areas (e.g., an outdated OS version on a local server, which attackers can use as an entry point).
Think of it this way: if you’re saving all your money to buy a new car and neglect servicing your current one, chances are it will go bust before you get the new model. The same goes for cybersecurity: when you overly focus on implementing new solutions, you should never do so at the “expense” of ongoing maintenance and monitoring. Otherwise, you risk having a security function that’s constantly fighting fires — aka switching between conflicting priorities on the implementation and maintenance sides.
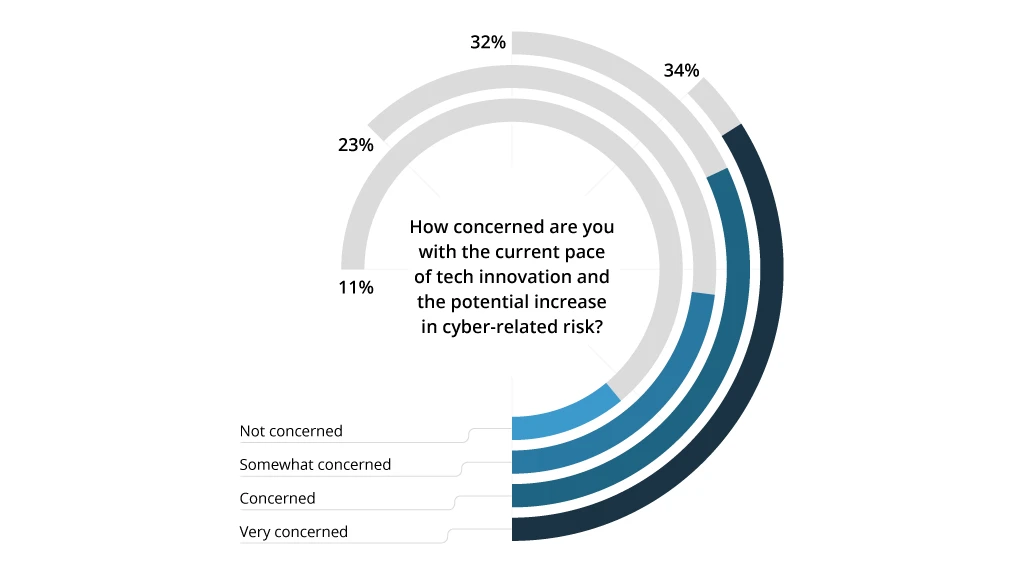
On the other hand, a strong focus on operations alone means that you can be potentially blind-sighted by new risks. Almost 90% of technical leaders feel that the current pace of technological innovation increases cyber-security risks. Yet, only 47% have implemented defense strategies against AI-powered attacks. When you’re only investing resources in maintaining the cyber-security function, rather than evolving it, your risk exposure increases.
To maintain the optimal balance between different security areas, we recommend the following best practices.
1. Conduct a Security Assessment
Your first goal is to scope the issue — that is understand where and why the disparity in resource allocation occurs. Our recommendation is to go with a security assessment first to:
- Create an up-to-date IT asset inventory with priority levels assigned to different types of assets.
- Document all the indemnified vulnerabilities and process gaps in the current cybersecurity program.
Based on the assessment findings, you can formalize a list of ongoing operational tasks, requiring a fixed number of human resources, and one-off projects — areas for evolving your program.
2. Determine Critical Areas of Improvement
Changes in cybersecurity programs are often triggered by external events:
- Recent massive cyber attacks or even a breach
- Compliance with new regulatory requirements
- Updates to customer SLAs
All of these result in extra workload for your security teams — a workload they don’t have time to handle. Given that 68% of organizations face cybersecurity skills shortages, you will have to evaluate carefully the feasibility of undertaking the planned project,
In such cases, it may be tempting to switch some of your Ops specialists into the development mode. However, doing so could increase your risk exposure (since there would not be enough people to man the virtual defense perimeter).
There are two viable solutions to the above:
- Increasing the SOC team hand-count to support the new initiative(s) and help with ongoing security tasks. This way you get more hands on deck eventually. However, this option won’t suit projects with tight timelines due to the prolonged time-to-hire for cybersecurity rules.
- Partnership with a cybersecurity security services provider, which allows you to delegate either ongoing threat monitoring tasks or get proactive support with implementing new strategic initiatives.
To be fully candid, you also have the third option: Divert existing resources towards the new project, while accepting higher risk exposure. More often than not, such a gamble will likely backfire.
3. Consider an Iterative Approach
New cybersecurity programs do not have to follow a “big bang” approach. On the contrary, a much more sustainable and impactful option is to implement new changes in increments. This way you can better allocate your resources and maintain realistic timelines while delivering consistent security posture improvements and justifying the value to project stakeholders.
You can divide the planned initiatives into several milestone projects. For example, your main initiative is implementing AWS Security Hub.
Your first milestone in enabling security logs collection for a prioritized use case. Once your senior team completes the solution implementation and develops the new runbooks, you can hand over this workload to the operations teams.
Next, collect the teams’ feedback with the new system. Do they receive too many alerts? Are there any critical integrations missing? Document all of these findings and address them in a new interaction.
Your goal here is to progressively improve different areas of your cyber-protection by first implementing a new process. Then fine-tuning and/or automating some aspects of it to reduce the load on L1/L2 specialists. In this way, you can evolve your cybersecurity function without creating new "fires" for the operational team to deal with.
The only possible problem with this approach is that priorities often change. Your senior staff may be asked to prioritize the security of a new system, due for deployment to production, instead of addressing existing security concerns. In such cases, it may pay to hold off a new deployment until the security team greenlights it. Otherwise, your newest asset may end up being your biggest vulnerability.
Conclusion: Deciding When to Rebalance Your Security Processes
High-performing SOC teams focus on threat monitoring, prevention, and detection in almost equal parts. Yet, it may be tough to spot if that equilibrium is always in place. From our experience, cybersecurity workloads should be better managed and distributed when:
- Security issues stall new product development or application deployments. This likely means that your teams are more focused on implementing new solutions and policies, rather than maintaining the security of existing environments.
- Recent exposure to a cyber event (unsuccessful or otherwise) is a strong sign that not enough attention was given to critical security processes.
- Your L1 security teams are over-stretched, constantly battle alert storms, run many processes manually, and haven’t received any new playbooks in response to escalated issues. In this case, your senior staff is not contributing enough to the development side.
By recognizing and addressing the above issues at the onset, you can avoid unnecessary risk exposure and ensure more productive SOC operations.
![Security Operations vs Security Development [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-how-to-strike-a-balance-between-security-operations.webp)



![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


