A Guide to Setting Up Essential Security Reporting and Key Metrics
Regardless of an organization's size and the tools it employs, the critical factor lies in establishing the right metrics to assess the health and strength of one's security posture. Tailored and coherent security reports play a central role in providing the necessary insights to support the enterprise’s critical functions, such as risk management, compliance, resource allocation, incident response, strategic planning, continuous improvement, vendor relationships, and stakeholder confidence.
Let’s explore reasons and factors you need to consider when selecting metrics for your business’s security reporting and why it’s more significant than you might initially realize.
Why Do You Need Security Reporting?
First things first, why do we make a big deal out of security reporting and assign it a high-priority status?
Effective security reporting is a vital component of any organization's cybersecurity strategy. It's indispensable for risk management, as it allows organizations to identify vulnerabilities, potential threats, and risks, enabling proactive measures to minimize the chances of security breaches. This, in turn, helps prevent financial losses and damage to an organization's reputation.
The importance of robust security reporting becomes even more evident when considering the alarming statistics highlighted in the IBM Cost of a Data Breach Report. The global average cost of a data breach in 2023 reached a staggering $4.45 million, marking a 15% increase compared to 2020. In the financial industry, the stakes are even higher, with firms facing an average loss of approximately $5.9 million per data breach.
Nonetheless, an equally scary factor that can undermine the cybersecurity fortress of your enterprise from within is a sneaky phenomenon known as “alarm burnout”. Imagine managing an IT support center, where your inbox is flooded with a ceaseless torrent of tickets. Throughout the course of your workday, these requests range from urgent "server meltdown" alerts to less critical "reset my password" messages, all competing for your team's precious time and focus. Now, layer in a flood of requests, and you're on the precipice of support team burnout, risking the oversight of critical issues amidst the digital deluge.
The concept of “alert fatigue” is real. A study commissioned by IBM uncovered that SOC team members review only half of the alerts within a typical workday, resulting in a 50% blind spot. Moreover, the same study reveals that most security analysts spend approximately one-third of their typical workday investigating incidents that turn out to be non-events, with the majority of threats falling into the categories of low-priority or false positives.
By leveraging the right security reporting metrics and technology's assistance, you can ensure that vital threats aren't overlooked amidst the data tsunami and that your response efforts remain aligned with the real emergency "911 calls" of your IT landscape. Now, let’s delve into the process of selecting and setting up the appropriate security indicators.
Just as individuals monitor health metrics to lead healthier lives, organizations choose security metrics to enhance their cybersecurity resilience. Effective metrics adhere to the SMART criteria, being Specific, Measurable, Attainable, Repeatable, and Time-Dependent. To create your set of security metrics, consider these seven guiding principles:
- Purpose: Always start by defining the specific aspects of security that you need to measure or improve. Are you focusing on vulnerability management, incident response, compliance, or another area?
- Controllability: Choose controllable processes that your organization can influence directly, such as patch management or access control policies. Because, while you can anticipate, you can never manage something uncontrollable like emerging threats or supply chain risks.
- Meaningful Context: Understand why you are collecting a particular metric and how it relates to your security objectives. If you are tracking the number of firewall rule changes, consider why this matters in the context of security. Is it to reduce the risk of misconfigurations or unauthorized changes?
- Best Practices: Leverage industry best practices and standards when selecting security metrics. Organizations can benefit from established frameworks like the NIST Cybersecurity Framework, CIS Critical security Controls, or ISO 27001.
- Quantitative Data: Whenever possible, opt for quantitative metrics over qualitative ones. For example, measuring the average time it takes to patch critical vulnerabilities in days is more informative than using qualitative descriptions like "slow" or "fast."
- Data Quality: Ensure that the data sources you're relying on are trustworthy and up-to-date. For that matter, consider investing in data quality assurance processes, including data validation, monitoring, and governance.
- Ease of Collection and Analysis: Metrics should be feasible to gather without excessive manual effort or cost. Automation is a key factor in the ease of collecting and analyzing metrics. Don’t forget visualization tools and dashboards that aid in conveying complex data simply.
Once you've identified the indicators that align with the specific security aspects tailored to your organization's goals, it's time to shift your attention towards universal security reporting metrics. Essential for evaluating the health and strength of your security posture, these metrics encompass key measurements and industry-recognized standards.
Consider These Crucial Security Reporting Metrics
To ensure the functional viability of the security perimeter, organizations should establish various types of KPIs within their SOC and broader cybersecurity efforts. These metrics will provide a detailed assessment of your security systems' performance and its network complexity, as well as facilitate efficient allocation of human and financial resources.
Technical Metrics
- Incident Count: The number of security incidents detected and responded to by the SOC provides insights into the threat landscape's intensity and the SOC's workload.
- Data Volume: Measuring the amount of data received and processed by the SOC helps assess data traffic and potential anomalies.
- Analytics Hours: Tracking the time spent by analysts on security analytics tasks indicates resource allocation and work efficiency.
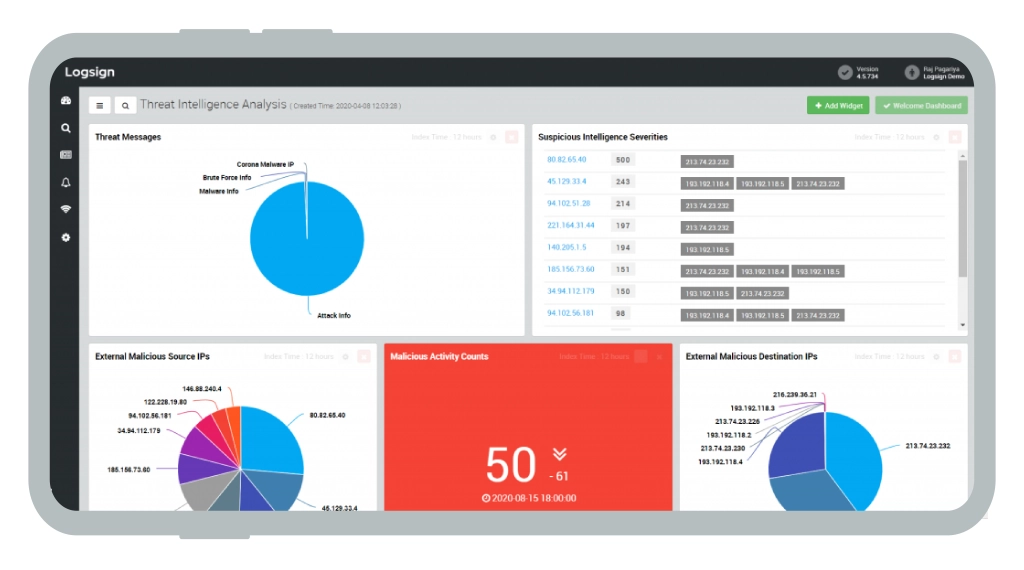
SIEM Solution Dashboards
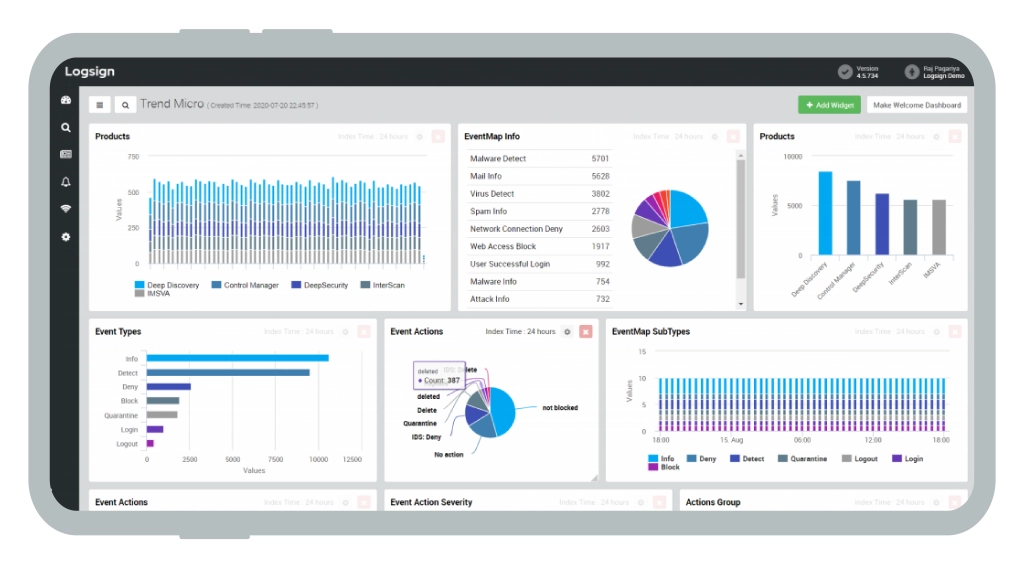
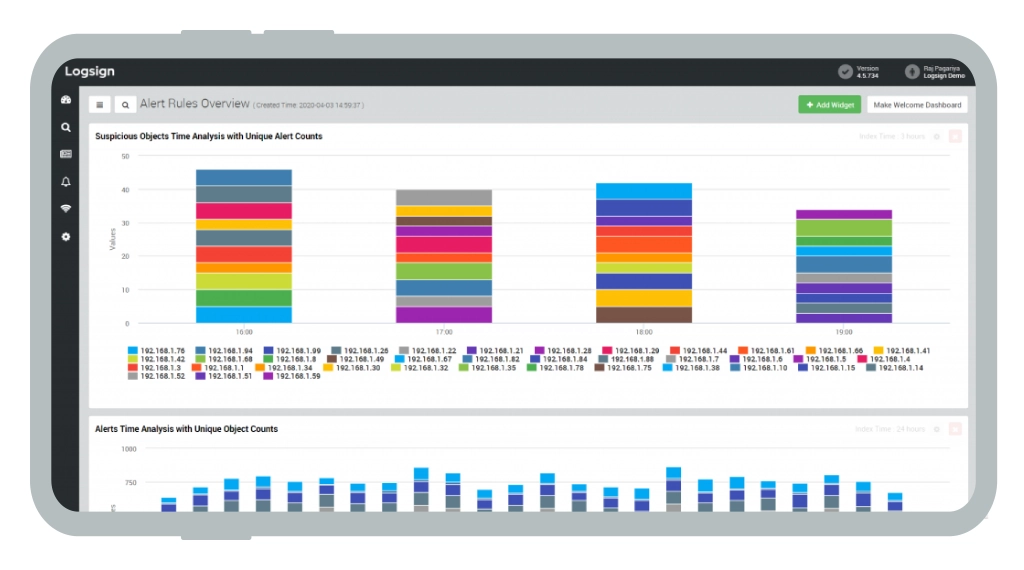
Organizational Metrics
- Employee Count: Knowing the number of employees provides context for user accounts and potential attack vectors.
- User Accounts: Monitoring user accounts helps detect unauthorized access or suspicious activity. Consider the alarming surge of phishing attacks, which saw a staggering 48% increase in 2022 resulting in a substantial financial toll of $12.3 million for businesses.
- Workstations: Tracking the number of workstations and devices assists in identifying potential endpoints vulnerable to attacks.
- Servers: Counting servers helps assess the attack surface and the criticality of server security.
- Connected Objects: Measuring the number of connected objects to the SOC, such as servers and data repositories, helps in managing network complexity and potential threat vectors.
- Data Collection Rate: Assessing the volume of data collected per day is essential, not only for understanding traffic but also for budgeting as it may impact the cost of security solutions.
Security System Health
- Health Metrics: Monitoring the health of security systems, such as firewalls, intrusion detection systems, and antivirus software, ensures their proper functioning and timely updates.
- Vulnerability Metrics: Categorizing vulnerabilities based on severity and potential impact helps prioritize patching and remediation efforts.
- Retention Policies: Evaluating data retention policies ensures that data is retained as required for compliance and investigation purposes without exposing the organization to unnecessary risks.
Assess These Critical Factors for In-House Security Management
For many organizations, maintaining security in-house is a strategic decision, but with this choice comes the challenge of ensuring comprehensive protection and centralizing your cybersecurity system. Here are five areas to focus on when managing your security internally:
1. Identity Monitoring
Measure User Activity: Continuously monitor user activities to detect unusual behavior. Sudden location shifts, like traveling from Ireland to Australia in a matter of hours, could be a sign of compromise. Pay attention to where users log in from, the frequency of logins, and the time spent online.
2. Antivirus and Endpoint Protection
Protect Machines: Implement antivirus and endpoint protection solutions to shield your organization's machines from malware and threats. Regularly update these solutions to stay ahead of evolving risks.
3. Alarm and Incident Monitoring
Monitor Alarms: Keep a close eye on the number and types of security alarms generated. Investigate incidents promptly to determine their origins and impacts. If you notice a high volume of spam incidents, it's a red flag for your email gateway defense. Consider tuning your defenses to counter this threat effectively.
4. Compliance Policy
Define Compliance: Clearly outline your compliance policy, specifying requirements that must be met by all machines and users. Recent findings revealing that a majority of companies identified over 1,000 files accessible to all employees highlight the critical need for compliance measures. This includes ensuring that:
- Operating Systems are up to date
- Antivirus signatures are no older than three days
- Machines do not run software from blacklisted sources
- All required security solutions are installed
- Information security policies are adhered to.
5. Intune and Compliance Reports
Utilize Microsoft Intune: Leverage Microsoft Intune to manage device compliance. Define compliance requirements and regularly generate compliance reports to gauge the status of your machines. These reports are invaluable in assessing your organization's adherence to security policies.
Final Thoughts
Establishing crucial security reporting metrics is vital for modern organizations to navigate the complex landscape of cybersecurity. They provide the visibility, data, and insights necessary to protect valuable assets, comply with regulations, allocate resources effectively, respond to incidents swiftly, and ensure the long-term security and success of the organization.
Whether you are looking for point solutions or a comprehensive assessment of your security posture, Infopulse offers a broad spectrum of cybersecurity services and solutions, from penetration testing to managed SOC, SIEM/SOAR deployment, cloud security, and more.




![Data Storage Security [thumbnail]](/uploads/media/thumbnail-280x222-data-storage-security.webp)
![Building AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-enterprise-guide-to-building-your-aws-security-hub.webp)
![Why Use AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-why-use-aws-security-hub.webp)
![Introduction to DevSecOps [thumbnail]](/uploads/media/introduction-to-DevSecOps-280x222.webp)






