6 Symptomatic Signs Your Enterprise Needs SOC
Previously we explained the role of the Security Operations Center (SOC) and the main responsibilities this unit handles. We also mentioned that SOC establishment may not be the optimal move for companies at lower levels of cybersecurity maturity.
However, if you have already implemented certain security practices and feel pressure to evolve your protection further, the signs below should help you determine if SOC is the next logical step for your cybersecurity program.
1. You Have Mission-Critical Dependence on IT Services
Nearly every business heavily relies on IT technologies to power its operations. However, for some organizations, several seconds of operational system downtime (due to a security incident or another occurrence) can lead to significant losses.
According to an ITIC 2020 survey, 40% of enterprises admit that an hour of downtime can chirp away $1-$5 million in direct and indirect costs, plus lead to hefty legal fines and penalties.
Industries with critical dependence on the quality, efficiency, and security of IT systems include:
- Finance
- Telecom
- Healthcare
- Automotive
- Manufacturing
- And online retail among others
Additionally, these industries also experience scrutiny from regulators and consumers alike when it comes to data security. Respectively, even a hint of a possible data leak or breach can cause major operational havoc and reputation damage.
For instance, earlier this year Audi and Volkswagen had to perform damage control after one of their vendor systems was hacked. Over 90,000 of the company’s customers and prospects had their personal information exposed — including driver’s license numbers, tax IDs, and more. The Volkswagen Auto Group extended a free credit monitoring service, $1 million of insurance, and assistance in case of identity theft to all affected parties. The security incident understandably left a strain on the company’s reputation, however.
Given that it is not just the “household name” companies that are under cyber-attack today, investment in SOC services could help prevent avoidable downtime, improve security perimeter, and ensure fast response to early signs of a breach.
2. You Don’t Have a Dedicated Security Operations Officer
A security operations officer is responsible for developing company-wide security policies and standard operating procedures (SOPs) for ensuring top-most protection of corporate assets.
Essentially, they formalize and implement the following types of security processes:
- Incident management
- Incident response
- Data governance and security
- Threat investigation and intelligence
- Threat hunting and prevention
- Disaster recovery and business continuity
In smaller organizations (under 500 people), such a role is not typically present and is mostly allocated towards CISO or Head of IT. Likewise, companies at lower levels of SOC maturity may not have a separate person to drive, oversee, and report on the progress in cybersecurity program implementation.
Opting for a SOC as a service or SOC managed services in such a case could help you obtain the expertise and technical know-how you need to introduce proper security facets. Plus ensure optimal staffing levels without setting up an in-house division.
3. You are Bound by Compliance
Most digital security standards include specific requirements for IT operations, infrastructure, and data processing security. For example:
- PCI-DSS standard stipulates multiple provisions for implementing effective log monitoring.
- HIPAA also has an extensive list of security requirements, spanning technical system configuration, organizational and operational policies, and risk management.
Separately, a host of ISO standards were specifically designed to promote standardization of security practices in regulated industries.
4. Your Security Team is Overloaded
It is no secret that the cyber talent gap is tremendous across all markets. It follows that many in-house security teams are understaffed and operate at maximum capacity. Over 30% of cybersecurity professionals reported an overwhelming workload last year and 35% were confronted by extra projects, started by other IT departments without any security oversight.
The rapidly growing technical estate enterprises now operate also leaves IT security teams with a larger number of incidents and alerts to handle. To a point where 49% of professionals admit that they have to turn off high-volume alerting features when they already have too many alerts in the processing queue.
How come alert fatigue happens so often when we now have stellar SOC technology such as SIEM and SOAR solutions? In most cases, alert fatigue happens due to:
- Outdated or over-sensitive heuristic policies, resulting in low-fidelity alerts.
- Lack of downstream visibility into the root cause issues and consolidated alert reporting.
- Suboptimal security technology configurations leading to a high volume of false positives.
- A growing number of users and IT systems, producing a high volume of incidents and alerts, especially post-transition to remote work.
In such a case, SOC managed security services providers can not only augment your in-house team performance but also assist with the implementation of better SOPs and security tools configurations for incident management and security monitoring.
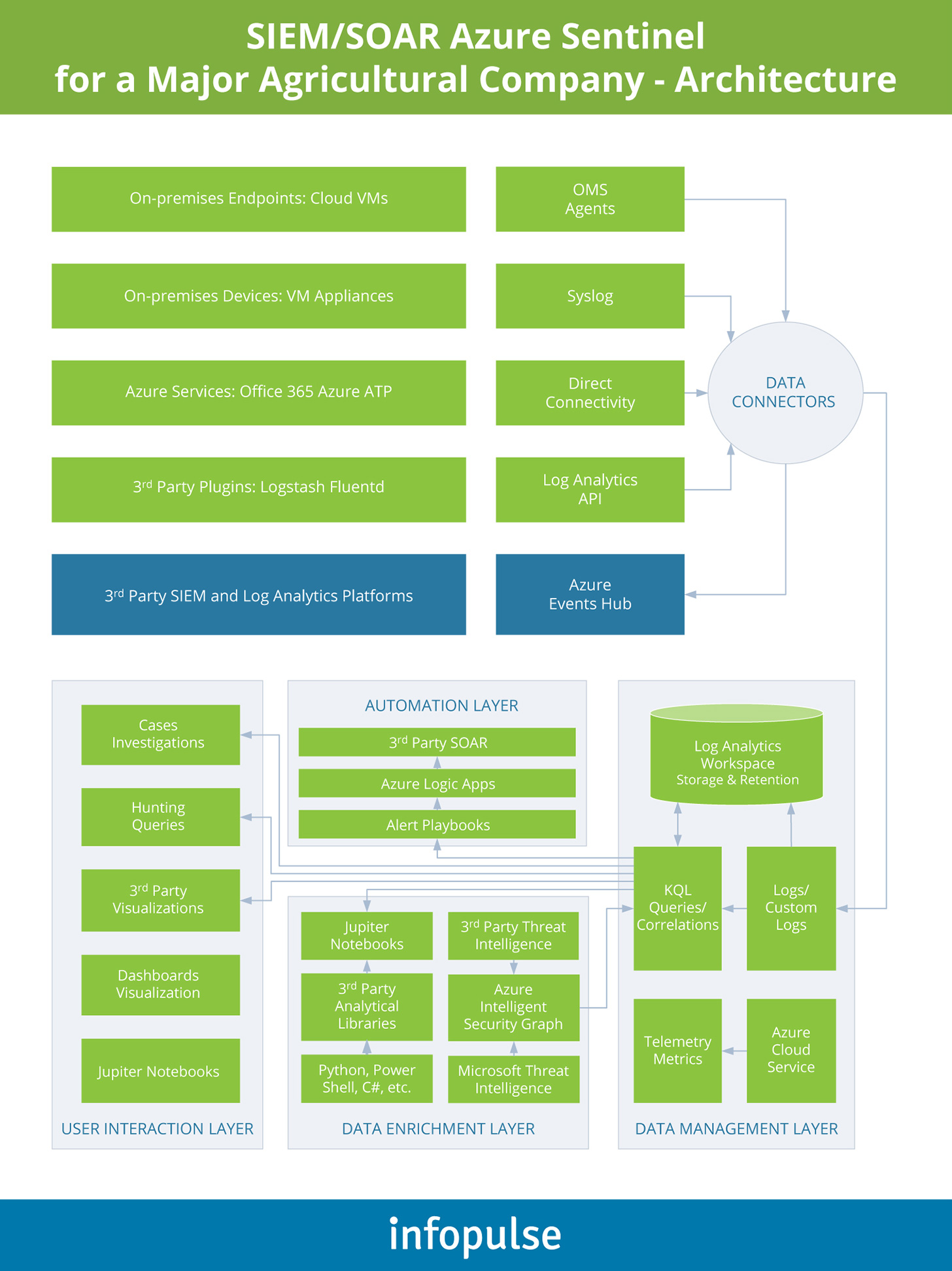
Case in point: Infopulse recently conducted a security assessment for an agricultural enterprise, sizing up a better SIEM/SOAR architecture. We directed the client towards Azure Sentinel and helped them re-configure the technology to gain the most value from it. Our team implemented routine security process automation, consolidated and centralized alerts to a single console, and established a seamless integration with the ITSM system and corporate business applications.
5. You are Entering a New Digital Growth Stage
Nearly every industry has found a strong footing in digital channels over the past year. Many now seek further ambitious business model transformations and digital product line expansions. However, going from offline to online operations also opens your business to new security risks.
Let’s take retail as an example. Verizon reports that in 2021 so far “system intrusion”, “social engineering”, and “basic web application attacks” represented 77% of breaches. DoS attacks were the primary cause of such incidents with pretexting and phishing coming close behind. Retailers, shifting to online operations without a strong security backbone, are the prime targets and easiest prey to such attacks.
On the other hand, the digital transformation process likely has most of your IT resources tied in other operational areas. Thus, cybersecurity is often treated as an after-thought. At least until a security incident occurs.
Delegating SOC as part of a wider digital transformation process to an experienced vendor allows you to focus on your core business operations. In this case, you benefit from their expertise and assistance in:
- Restructuring the internal operational processes in line with the latest security best practices.
- Right-sizing and configuring new cybersecurity tools investments.
- Ensuring ongoing support and reporting on the state of your system’s security and proactive recommendations on further improvements.
Furthermore, if you are expanding to a new market, where cyber concerns are high, the adoption of SOC can give you a competitive advantage. Not only do you “communicate” a certain degree of maturity to regulators and business partners, but also attain a positive sentiment from consumers. After all, 63% of consumers believe that the company is always responsible for protecting their data (even if they fail to follow baseline security practices such as not sharing sensitive data over an unencrypted Wi-Fi connection).
6. You are Looking to Optimize Operational Expenses
One of the major reasons why companies postpone SOC establishment are the operational costs. Ponemon Institute estimated that the average enterprise cost of staffing and maintaining an enterprise-level SOC is $2.86 million. However, those units rated as “highly effective” had a price tag of $3.5 million per year.
The largest budget line for SOC was staff salaries, going north of $100,000 annually for a security analyst in the US and further projected to increase by 29% this year. Given that many enterprises need 24/7 SOC with people on call 365 days per year, the personnel costs can become inhibitive.
Tools and supporting technology investments constitute another major line. However, due to suboptimal configurations, many organizations end up paying more in licensing costs than necessary. Likewise, the lack of automation capabilities further increases both the technology and people costs.
Managed SOC, and specifically the shared SOC model, can drastically reduce the costs of running a SOC. Under a shared model, you obtain the required security roles for the hours you need to cover. However, these people are on rotation with other vendors when not engaged in your projects and respectively cost less to retain.
To Conclude: How to Evaluate a SOC Provider
Outsourcing SOC operations helps speed up the adoption. Instead of spending time on cultivating the security expertise internally, you can obtain professionals, technologies, and operational best practices, required to run a high-performing unit in under 6 months. Not to mention the reduced adoption and maintenance costs through competitive “as a service” or “managed” SOC service models.
However, outsourcing should be a well-considered decision requiring a certain degree of readiness and confidence in the selected partner. To understand whether your current SOC vendor or potential new partner can deliver optimal service levels, analyze whether they:
- Provide comprehensive coverage of security events and timely reporting.
- Propose customizable policies and SOPs, rather than apply a one-fit-it-all approach for all customers.
- Have metrics-driven service levels agreements (SLAs) and deliver on the spelled out obligations.


![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)





![Multi-Cloud Governance: Policies [thumbnail]](/uploads/media/thumbnail-280x222-multi-cloud- governance-policies-and-procedures.webp)
![Security Operations vs Security Development [thumbnail]](/uploads/media/thumbnail-280x222-how-to-strike-a-balance-between-security-operations.webp)