Three Ways to Introduce SOC to Your Organization and How to Find the Best One for Your Business
Most leaders already recognize the benefits of the Security Operations Center (SOC) establishment, but they also acknowledge the challenges of operating one. According to a 2022 SOC survey by Chronicle, companies with in-house SOC operations struggle to maximize the unit’s value due to:
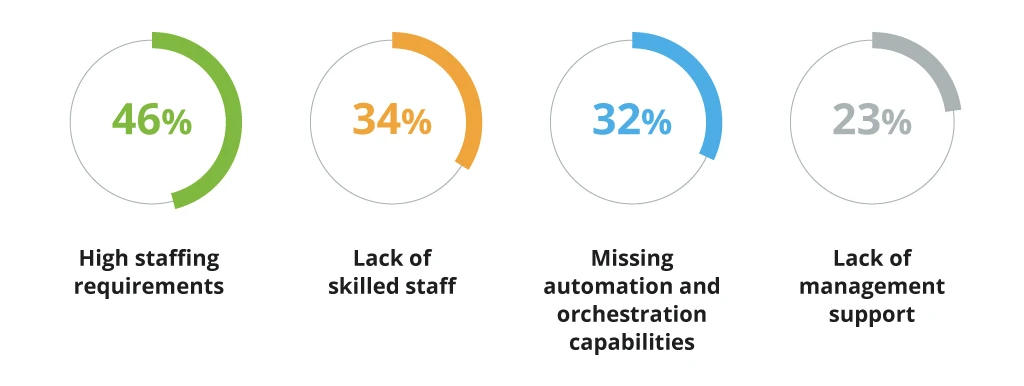
Organizations who are just considering SOC adoption, in turn, are often deterred by high in-house SOC operating costs, as well as the lofty “groundwork”, required for SOC pre-implementation.
That said, an in-house model is not the only way to introduce SOC to your organization. In this post, we offer a snapshot of alternative adoption scenarios.
3 SOC Service Models to Consider for Better Security Protection
Businesses are encouraged to invest in better security by their end customers. An astounding 87% of consumers will refuse to transact with a company if they have concerns about its security practices.
Global data watchdogs and regulators also put extra pressure on businesses to level-up cybersecurity and consumer data protection mechanisms. In response to recent hacker attacks, US officials issued a new “National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems”. Updated security guides from NIST and DHS are soon to follow. EU member state officials are also leading discussions on establishing a national cybersecurity strategy at the pan-European level.
The above macro-market changes drive growth on lower levels. An evolving market of independent cybersecurity solutions providers (CSSPs) has emerged in response to the growing demand for cybersecurity expertise.
- The global cybersecurity market was worth $139.77 billion in 2021 and is set to grow at a 13.4% CAGR until 2029.
- The global SOC as a Service market is worth $6.1 billion in 2022 and is expected to grow at a 10.5% CAGR until 2027.
New (and established) providers commoditized access to different security services and SOC adoption in particular.
Guided SOC Operations Establishment and Maintenance
Under this service model, you partner up with cybersecurity consultants whose primary job is to build a necessary “technical” mortar for SOC adoption. Then help your company maintain the created IT infrastructure an in-house SOC unit would use.
As part of such collaboration, you receive:
- An in-depth security assessment of your current infrastructure, processes, compliance status, and risk radar.
- Recommendations for necessary process changes, infrastructure updates, and cybersecurity technology investments.
- Reference SIEM/SOAR architecture development and tooling selection with subsequent implementation.
- Operational assistance with SOC service functions, processes, playbooks, and procedures developed for the staff.
- Assistance with hiring for the main roles to fully staff your SOC.
- Ongoing consultancy and support with implementing ITIL service management standards for the new unit.
A real-world example: A telecom company approached Infopulse for SOC advisory. As part of its SIEM system, the client selected Azure Sentinel – a dual SIEM/SOAR solution. Infopulse assessed the client’s current infrastructure and licenses to map unbillable (Microsoft) and billable (third-party) systems and solutions. Then proceeded with implementing five test case scenarios.
With our guidance, the client field-tested Azure Sentinel capabilities to understand the scope and efficacy of automated threat detection and monitoring. Additionally, they received a more accurate budget estimate of usage costs and recommendations on the next SOC implementation steps.
At a glance
- The main benefits of guided SOC adoption and subsequent in-house unit establishment are risk minimization and faster time-to-value (thanks to proactive support from a CSSP).
- The main downsides are that this approach is more cost-intensive and only suited for cyber-mature organizations. Your company must have well-defined ITIL security processes, reactive cybersecurity measures, and XDR telemetry collection in place. Also, when comparing in-house management vs. outsourced SOC costs, the former is more expensive. For enterprises, in-house SOC maintenance costs $10.3 million on average.
Managed SOC Services
Outsourcing SOC function to a CSSP makes sense when your organization struggles to hire cybersecurity talent locally or cannot afford to maintain 24/7 L2/L3 support.
In this case, the selected managed SOC service provider takes over:
- SIEM/SOAR solutions deployment
- IT infrastructure security proofing
- A specified number of SOC processes
A managed SOC unit can cover some of the following security tasks:
- 24x7 L2/L3 support
- Threat intelligence mining
- Anomaly detection and investigation
- Network security monitoring
- Threat response and containment
- Log management and log analysis
In such an arrangement, your provider commits to covering a fixed number of use cases (or security functions) according to SLAs. SOC specialists remain on the vendor’s end and “tune in” on a retainer basis.
Going with the SOC managed services model makes sense when you need to rapidly scale up your team to cover a larger technological estate (for example, new cloud infrastructure). Managed SOC services also make sense for covering one-off jobs to be done such as implementing security automation across a set of processes or setting up a better threat intelligence collection system.
Sample client scenario: A financial company decided to launch a spin-off mobile banking product in a new region. The company has sufficient L1/L2/L3 coverage for the domestic market and can maintain an 8/7 days schedule. In-house security analysts are primarily focused on monitoring in-house core banking systems and private cloud-based extensions.
The new region has a more complex cybersecurity threat landscape. The bank requires more proactive threat-hunting capabilities and 24/7 L2/L3 monitoring to minimize the risks of breaches due to direct attacks. They also need assistance with local security compliance.
A managed SOC provider could step in to cover regional L2/L3 support and a number of use cases around threat monitoring, investigation, and mitigation. On the technology side, the vendor can help reconfigure their SIEM/SOAR architecture in line with local requirements and perhaps implement an extended detection and response (XDR) solution as an extra precaution.
At a glance
- The main benefit of a managed SOC model is rapid access to required expertise and unconstrained team scalability. You can progressively switch other use cases to your team or get more people on board as your technology portfolio grows larger at a competitive cost.
- The main downside is the need to right-size the scope of managed SOC services to your company’s needs. You will need to select the optimal number of cases for delegation. Then ensure that the ROI of outsourcing these would be in the positive territory. The current state of cybersecurity automation already permits maintaining a strong security posture without having highly-skilled security analysts on call 24/7.
Managed SOC as a Service
SOC as a service is an “extended” version of managed SOC services, where you receive the better of the two previous service models:
- Pre-adoption assessment, guidance, and SOC establishment
- SLA-backed SOC services delegation of various security jobs
- Ongoing cybersecurity recommendations and reporting
“As a service” part indicates that such an offering is distributed as a fixed-price subscription with clear-cut terms and scoped deliverables. The price depends on the variables such as the number of users/locations to cover, support availability, and the number of SOC use cases among others.
Unlike managed SOC, SOC as a service adoption scenario is better suited for companies with lower levels of cybersecurity maturity. As part of the “subscription”, you first receive an in-depth security assessment and managed security architecture setup and tooling configuration. Then a SOC team takes over monitoring, threat detection, and investigation.
A real-world example: An agricultural company approached Infopulse, looking for improvements to their current Azure Sentinel configuration. The client’s goal was to improve the solution’s efficiency and introduce a greater degree of security automation.
Our cybersecurity consultants helped the company validate four SIEM/SOAR test cases. A greater degree of automation has allowed them to extend security coverage across more corporate applications and maximize the productivity of human staff. As a next step, the business is now considering an extended integration of Azure Sentinel into its IT infrastructure – with subsequent SOC adoption.
At a glance
- The main benefits of SOC as a service are predictable pricing and comprehensive security coverage. You do not have to engage separate CSSPs for security assessment and further SOC management. Instead, you can first tackle standard high-priority security tasks – and then explore out-of-the-box security scenarios together with your partner.
- The main challenges concern people and technology. To benefit from SOC as a service you need to first establish high IT infrastructure visibility to draw the security defense perimeter. This will take extra time. On the people side, you need to build a clear communication channel with your SOC provider. The optimal scenario is appointing one responsible person with decision-making powers to facilitate collaboration.
Starting Out with SOC Services
When considering SOC adoption, it is easy to get caught up in the immediate intricacies and costs. Switch your gaze to the bigger picture: a strong cybersecurity posture has become a driving force for business continuity and a competitive advantage.
Companies with higher customer data protection standards not only benefit from easier compliance, but also secure bigger market share thanks to higher customer trust and loyalty. Stronger security policies encourage consumers to share more data — which in turn can be leveraged to make your products or services more competitive. These are the indirect benefits of SOC worth taking into account as you prepare your business case for its adoption.
Contact Infopulse to receive personalized consultation on different SOC service models and adoption scenarios.
![SOC Adoption Scenarios [banner]](https://www.infopulse.com/uploads/media/three-ways-to-introduce-SOC-to-your-organization-1920x528.webp)


![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


