How to Ensure IoT and OT Security with Microsoft Defender for IoT
Why OT/IoT Landscape Needs Staunch Protection
Operational technology (OT) is a collection of devices organizations rely upon to monitor and manage industrial equipment, processes, and events. Internet of Things (IoT) are mostly consumer-grade, internet-connected devices. Currently, over 16.7 billion active OT/IoT endpoints are now present globally.
Modern OT devices are internet-connected through a variety of networks (wire connection, Wi-Fi, cellular, Bluetooth, etc.). Moreover, most are assigned to govern mission-critical processes, ranging from streamlined office space management to automated chemical sampling.
Therefore, attacks targeted at OT and IoT devices can carry substantial risks for organizations. What makes the issue more acute is that OT/IoT attacks can be staged on two levels: hardware and software, with either being used as a leverage to penetrate the security perimeter.
In November 2021, the Cybersecurity & Infrastructure Security Agency (CISA) found that
IntelliBridge EC 40 and EC 80 Hub devices, manufactured by Phillips, contained critical vulnerabilities, which allowed hackers to access patient data and launch distributed denial of service (DDoS) attacks. The company had to rapidly roll out a new patch, however, its reputation was tarnished.
IoT and OT exploits were also behind the February 2022 cyberattack on Viasat, which caused a malfunction of some 5,800 Enercon wind turbines; March 2022 Samsung data breach, April 2022 malware attack on Ukraine’s energy infrastructure, May 2022 cyber offense against the Port of London, and countless other events of different scale.
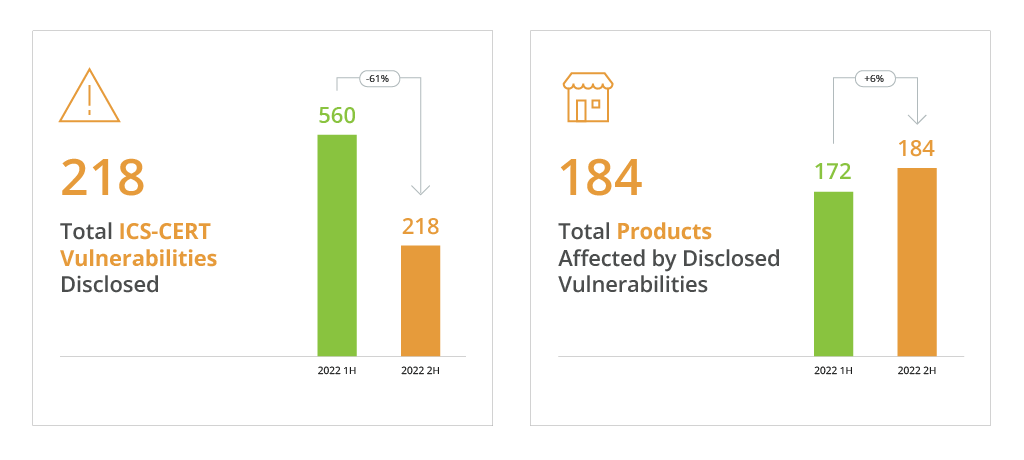
Overall, the ICS-CERT advisories for industrial control systems, published by CISA, disclosed 560 new vulnerabilities in the first half of 2022 and another 218 — in the second half of 2022.
Critical manufacturing was the prime sector for attacks, followed by the energy industry, water and wastewater companies, transportation systems, and healthcare.
Common Types of Vulnerabilities in OT and IoT Devices
The “cost” of greater connectivity is an increased attack surface. A breach of OT components might have critical impact on organization, presenting an attractive target for hackers. A breach of one device could instantly provide access to a wider system. This fact is significantly multiplied considering some OT devices are Internet-connected and/or interlinked with other business systems. The reasons why “IoT hacking” remains in the news headlines are poor awareness of security risks, paired with weak security practices within the organizations, and low visibility into different assets. These factors are often behind the most common IoT device vulnerabilities such as:
- Unsecured network services
- Unauthorized changes to the device’s configuration
- Unsecured ecosystem interfaces
- Missing secure update mechanisms
- Usage of outdated components
- Insufficient privacy protection
- Insecure data transfer and storage
- Lack of centralized device management
- Usage of default manufacturer settings
- Lack of physical device hardening
As Andrea Carcano, chief product officer and co-founder of Nozomi Networks, explained in an EE Interview:
How to Protect IoT and OT Networks with Microsoft Defender for IoT
The challenges of protecting IoT and OT networks stem from the growing size of networks. From smart video conferencing systems and connected printers to smart meters and connected controls for managing manufacturing jobs, the usage of IoT/OT devices across enterprises proliferates. In Europe, over 48% of large enterprises use IoT devices in some capacity.
With an increasing number of endpoints, security features, configuration requirements per device, and user identities, organizations increasingly struggle to have full visibility (and therefore — control) over their OT estate.
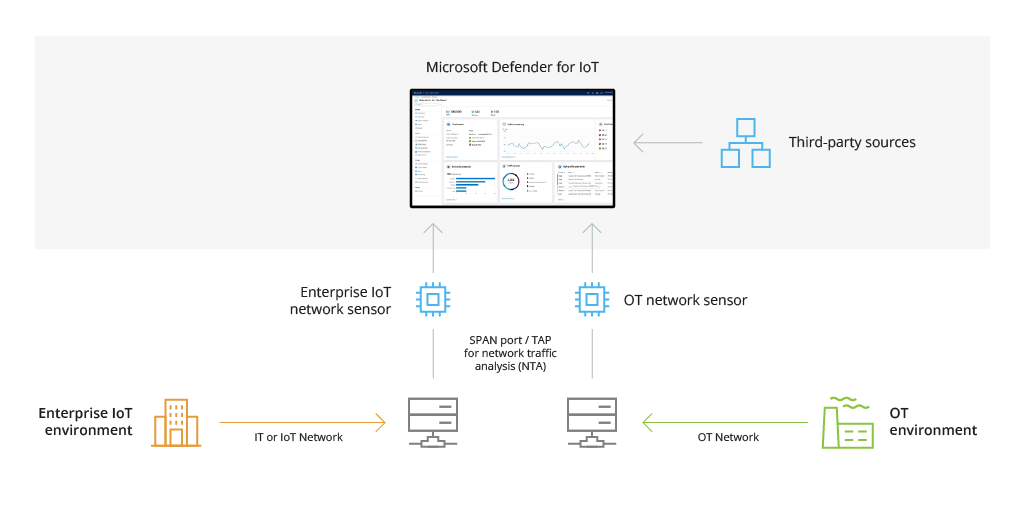
Microsoft Defender for IoT (formerly Azure Defender for IoT) is a network detection and response (NDR) solution for collecting security telemetry across diverse IoT, OT, and industrial control system (ICS) devices for subsequent analysis.
Deployable on-premises, in the cloud, or in a hybrid fashion, Microsoft Defender for IoT can be effectively scaled to achieve full visibility into the company’s IoT/OT environment, detect security threats and facilitate vulnerability management.
Note: Microsoft Defender for IoT is not a standalone security solution. It provides network layer monitoring and enables data exchanges between connected devices and auxiliary security systems such as Microsoft Sentinel or third-party SIEM/SOAR tools.
Effectively, the role of Microsoft Defender for IoT is to continuously monitor network traffic across your network of OT and IT devices. It can be configured to monitor the following types of sensors:
- OT/IoT network sensors, which connect to a SPAN port or network TAP
- OT/IoT network sensors, which use analytics engines and Layer-6 Deep Packet Inspection (DPI)
In each case, data collection, analysis, and alerting happen directly on the sensor, which reduces both bandwidth and latency. On-premises or Azure-based dashboards receive only security telemetry and insights for security management.
Microsoft Defender for IoT: Key Capabilities
Microsoft Defender for IoT was purpose-built to identify threats and vulnerabilities within IoT and OT environments.
Since a number of IoT and OT devices don’t have any embedded security agents, capable of sending security telemetry data to connected tools, they may remain invisible to cybersecurity teams and therefore — unpatched and/or misconfigured.
With Microsoft Defender for IoT in place, enterprises can:
- Instantly discover new IoT/OT devices on their networks. Gather equipment details, extra data from network sensors, and other relevant sources.
- Receive alerts about common types of risks in real time (e.g., missing patches, open ports, unauthorized changes to device configurations, controller logic, or firmware).
- Benefit from recommendations for vulnerability management, based on behavioral analytics and machine learning algorithms.
- Model advanced threat scenarios such as zero-day exploits or living-off-the-land tactics.
- Scale the deployment across cloud, on-premises, and hybrid IoT/OT networks to achieve full visibility.
- Extend monitoring to devices with custom, or non-standard protocols, using Horizon Open Development Environment (ODE) SDK.
Microsoft Defender for IoT: Implementation Best Practices
Microsoft Defender for IoT enables continuous monitoring of all OT/IoT devices through data centralization, plus provides Security Operation Center (SOC) unit with better controls for doing their best work — ensuring unquestionable protection of your company’s operation.
Microsoft Defender for IoT users get access to the following out-of-the-box components:
- An Azure-based portal for cloud management and integrations with other Microsoft security services.
- IoT/ OT sensor console for device detection and subsequent Defender deployment on either the device itself or a virtual machine. You can select between configuring cloud-connected sensors, or fully on-premises locally managed sensors.
- On-premises management console for centralized OT sensor management and monitoring of local, air-gapped environments.
To ensure that you are getting the most out of the offered solutions, we recommend following a set of configuration best practices for Microsoft Defender for IoT.
1. Decide on the Set of SOC Use Cases
A SOC use case is a modeled security detection and response plan your organization designs for the detection, reporting, and mitigation of a specific security threat. In essence, you create a registry of prioritized threats, compliance requirements, and industry needs you’d like to transform into a SOC alert — an event that requires an investigation and orchestrated response from your security team.
Since Microsoft Defender for IoT can collect and process vast amounts of data, you will have to define parameters for alerting (i.e., what sort of behavioral deviation of a device should be considered as an anomaly and further investigated).
For example, creating alerts for SCADA device configuration changes made by the admin or privileged users may be redundant. However, setting up an alert for device change by an unknown or unauthorized use is critical. Based on the incident type, your SOC team would then develop a specific playbook for its investigation and remediation. In the case of the example above, it could be an automatic dispatch of a PLC stop command.
2. Design Rules for SIEM
Security information and event management (SIEM) is the practice of consolidating security information and event management for enabling a faster response to security vulnerabilities and threats. The goal of SIEM — detect and addresses incidents at early stages before they can hinder business operations.
Based on the identified SOC use cases for OT/IoT, your team should design analytical rules, such that help generate descriptive alerts for a specific incident type. Then set up step-by-step workflows for analysing the alert received and implementing applicable remediation steps.
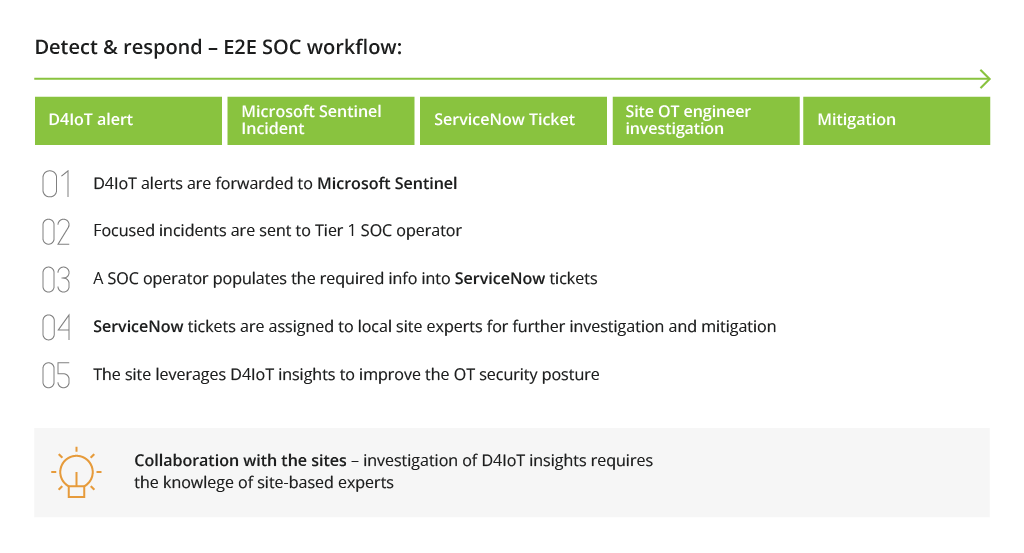
3. Automate SOC Workflows with Microsoft Defender and Microsoft Sentinel Integration
Microsoft Sentinel is the company’s converged SIEM/SOAR tool. Apart from facilitating security information and event management, Microsoft Sentinel also provides robust tools for security orchestration, automation, and response (SOAR).
By integrating Microsoft Defender for IoT into Microsoft Sentinel, SOC teams can benefit from the predefined rule sets available with Sentinel, which help identify IoT/OT events, as well as pre-made playbooks for automating incident investigation and response. Moreover, SOC teams can implement smart filters for incident filtering by specific IoT issues and generate detailed reports on the business impact of an incident for other stakeholders.
Sentinel’s playbooks significantly help SOC teams to implement better alert triage, raise alerts to device owners/operators, weed out false positives, and begin a sweeping investigation faster.
Reducing OT and IoT Security Risks with Microsoft Defender
OT security requires a consolidated response from network operations centers (NOCs), security operations centers (SOCs), device management systems (DMSs), and application management systems. To achieve unity and standardization among these entities organizations require a centralized, yet flexible security system.
Solutions like Microsoft Defender for IoT, combined with Microsoft Sentinel, enable companies to integrate all assets in their IoT/OT environment; monitor and manage them from a centralized console. Such a consolidated approach significantly reduces cyber risks by providing extra security insights and opportunities for proactive incident mitigation, rather than retroactive remediation.



![Defender for Endpoint [thumbnail]](/uploads/media/thumbnail-280x222-defender-for-endpoint.webp)
![Security Stack [thumbnail]](/uploads/media/THUMBN~1.WEB)
![AWS Security Hub Integrations [thumbnail]](/uploads/media/top-security-solutions-to-integrate-with-aws-security-hub-for-soc-280x222.webp)
![Building AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-enterprise-guide-to-building-your-aws-security-hub.webp)
![Microsoft Sentinel Adoption Guide [thumbnail]](/uploads/media/azure-sentinel-how-to-ensure-seamless-integration-and-optimize-your-soc-licensing-costs-280x222.webp)



