Corporate Data Protection Based on Microsoft Defender for Endpoint
The omnipresence of data makes it increasingly prone to security risks. Endpoints, such as PCs, mobile phones, laptops, routers, or servers, are often identified as the weakest areas of an organization. Cyber attackers exploit their vulnerabilities to corrupt or steal valuable information. Likewise, it’s a common practice for employees to inadvertently jeopardize data using weak passwords or by downloading unsafe content.
Combine it with the hybrid work model, the BYOD adoption, and the widespread popularity of cloud-first environments, and you get an overwhelming challenge in controlling and securing endpoints while preventing data loss. Moreover, manual processes and legacy tools make managing endpoints and remediating vulnerabilities nearly impossible.
As a result, there have been multiple cases of devastating data breaches, 45% of which occurred in the cloud between 2021 and 2022. These breaches inflicted a global average total cost of USD 4.35 million on corporations around the world in the last year.
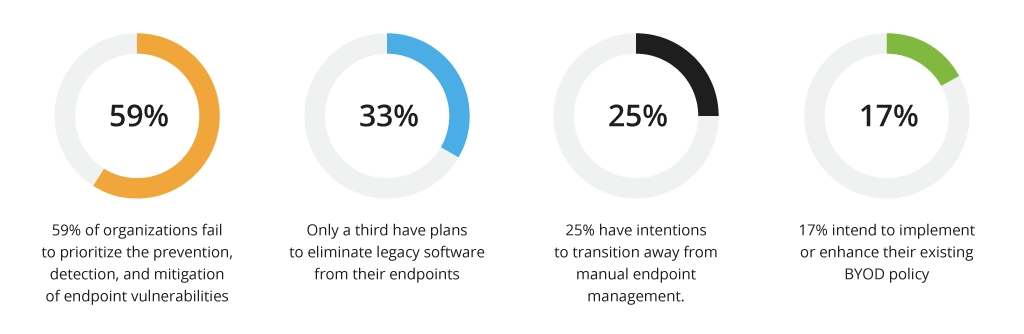
Given all these factors, it is reasonable to assume that endpoint security and management should be among the highest priorities. However, a recent study conducted across the USA, Canada, Europe, and other regions has revealed that this is not the case:
These findings are deeply concerning, as many organizations are placing themselves at high risk of falling victim to severe cyberattacks.
One of the reasons behind this negligence towards endpoint and data protection is the lack of knowledge on how to develop a new security approach and where to initiate the process. To address this issue, it’s recommended to start by identifying proper threats and risks relevant to your data and endpoints. Then you should implement a comprehensive data loss prevention (DLP) solution like Microsoft Purview and endpoint security solution like Defender for Endpoint, which can significantly strengthen each other while safeguarding corporate data and devices.
DLPs offer complete transparency by monitoring how data is utilized and transferred within the organization. They also provide control over various types of sensitive corporate information, including emails, messages in different communication channels, files stored in cloud services, and records in databases located both in the cloud and on servers.
What Is Microsoft Defender for Endpoint?
The data loss prevention approach within an organization can be reinforced by implementing Microsoft Defender for Endpoint as a DLP agent. This enterprise solution acts as a local agent that exerts control over data, enforces corporate policies, and oversees the enforcement of those policies.
The solution focuses on safeguarding endpoints within an organization's network to proactively prevent, detect, investigate, and respond to sophisticated threats directed toward Windows, macOS, Android, iOS, and Linux.
Microsoft Defender for Endpoint employs the following capabilities to ensure the full protection of an organization's endpoints:
- Threat and Vulnerability Management — a risk-based approach that streamlines the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations in real time.
- Attack Surface Reduction — a prevention technology designed to minimize the areas where a company might be susceptible to threats and attacks.
- Next-generation Antivirus (NGAV) — a solution that proactively identifies and blocks attacks before they can inflict damage to corporate data.
- Endpoint Detection and Response — a robust technology that uncovers and identifies threats hidden in an organization’s endpoints.
- Auto Investigation & Remediation — a tool that empowers security teams to swiftly transition from alert notifications to efficient remediation actions on a large scale.
- Microsoft Threat Experts — targeted notifications and an on-demand service of experts to provide technical consultations.
- Unified Security Management & APIs — an ability to integrate with other solutions.
A case in point: Infopulse implemented Microsoft Defender for Endpoint for one of the largest retail chains, which resulted in enhanced cyber resilience and effective protection of more than 1500 corporate and BYOD endpoints.
Which Defender for Endpoint Plan Should You Choose?
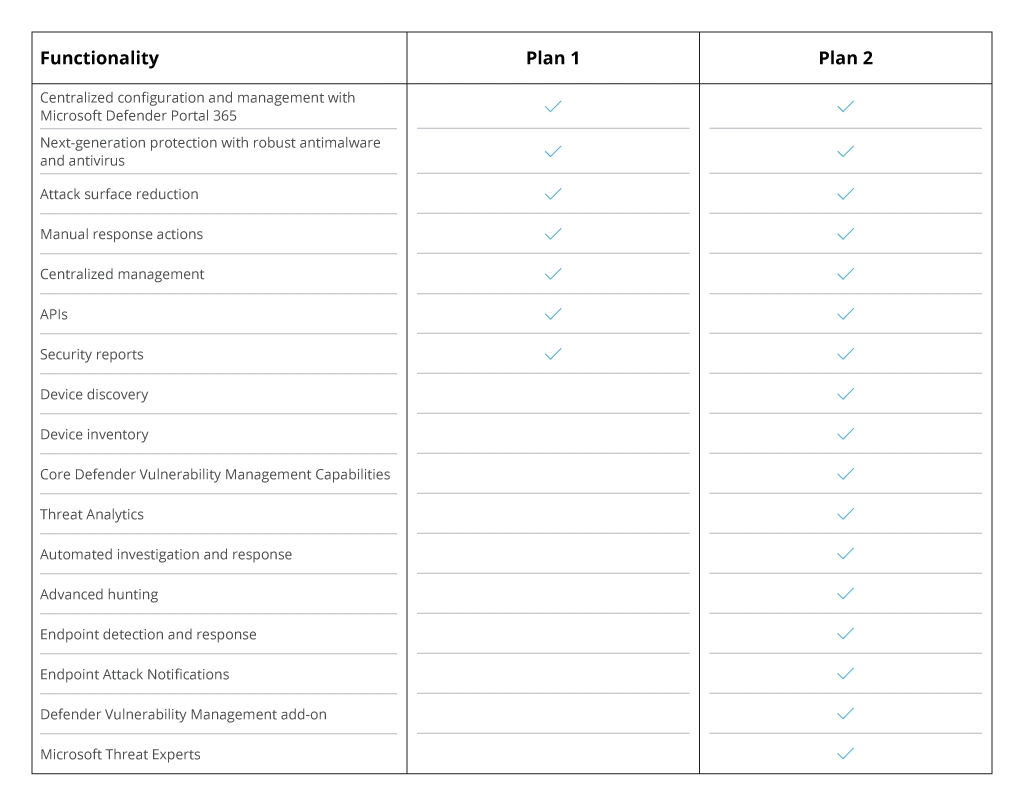
Some time ago, Microsoft Defender for Endpoint was a single solution, but now the company offers two plans for device protection — Plan 1 and Plan 2. Why was there a split, and how do these two options differ?
Defender for Endpoint was originally designed to meet large enterprises' most demanding cybersecurity needs. Due to this, small and medium-sized companies could not justify the purchase of the software because they did not need all the features. In fact, by breaking down the product into two plans, with Plan 1, Microsoft makes it more accessible to more companies, especially SMBs.
Plan 2 is suitable for large enterprises as it includes many more features. For instance, Threat and Vulnerability Management will be useful for corporations with separate teams accountable for threat detection and response.
Both plans support Windows, macOS, iOS, and Android operating systems. However, Plan 2 also offers support for Linux.
Also, there are two other solutions that are optimized solely for small and medium-sized businesses: Microsoft Defender for Business and Microsoft 365 Business Premium that provide similar capabilities. However, if you decide to opt for Microsoft Defender for Endpoint, here is the comparison table that will help you see what plan and features can suit your needs.
The experience Infopulse obtains suggests that companies can undergo a few stages before implementing data protection based on Microsoft solutions. In the following sections, we will provide a more detailed description of those stages.
Assessment Stage
Data protection is not solely a technical solution; it is a comprehensive business process encompassing various organizational approaches and processes.
To begin with, the company needs to have a clear understanding of its data assets. This involves identifying and determining which types of data are most valuable. Naturally, certain information may be publicly available and, therefore, does not require protection. However, for other types of information, the company must establish appropriate protective measures, rules, and policies for their usage and dissemination. Here's how Infopulse increased its level of asset protection with a consistent security strategy.
Thus, before implementing DLP, it is crucial to analyze and assess the existing corporate information as well as compile a comprehensive list of all data assets within the company. Ideally, the organization can create profiles specifically for critical and important information.
A case in point: Infopulse used Microsoft Defender for Endpoint for in-depth asset monitoring and data collection in one of the largest telecom companies in Central Asia. This has resulted in a few benefits for the company:
- reduced data breaches and cyber threats,
- boosted corporate assets security,
- secure access to the company resources outside the office, etc.
Labeling Stage
Once the initial stage of data analysis and assessment is completed, the company can proceed with the labeling process. This involves assigning specific sensitivity labels with the help of Microsoft Purview to each sample data, enabling the system to determine which rules should be applied to the labeled data, regardless of its type of processing or storage mode (be it a file, email, database record, or message in a corporate communication channel).
Simply speaking, sensitivity labels enable the classification and protection of business-sensitive content. By utilizing them, users can encrypt all types of information, mark the labeled content with headers, footers, and watermarks, apply labels automatically, and prompt others to do the same.
Implementing this entire labeling process requires fostering a culture of data assessment within the company and establishing relevant policies.
Process Automation Stage
After completing the assessment and labeling stages, the company can proceed to the process automation stage. During this stage, the organization will require the following solutions:
- Microsoft Azure
- Defender for Endpoint Plan 2
- Data Protection
- Data Compliance
Microsoft Azure, Microsoft Defender for Endpoint, data protection, and compliance, when used together, can automate data loss prevention processes by taking advantage of their integrated features and capabilities. For instance, Azure’s Purview Information Protection discovers and protects data at rest and when it travels. With its help, Microsoft Defender for Endpoint can automate data protection actions. For example, when Defender for Endpoint detects a potential data breach, it can trigger preventative actions to protect disclosure attempt automatically.
Deployment of Microsoft Defender for Endpoint
Before deploying Microsoft Defender for Endpoint, an organization must identify its enterprise architecture and select an appropriate deployment method. For instance, if the company's endpoints primarily run on Android, Microsoft Intune would be the most suitable choice. Then the company should configure Defender for Endpoint's security features to maximize its robust protection. The entire deployment method of Microsoft Defender for Endpoint includes three phases:
- Preparation phase
- Setup phase
- Onboarding phase
Preparation Phase
During this phase, the company needs to identify and involve all relevant stakeholders who will need to approve, review, or stay informed about the project. Some roles may be temporarily applied and removed once the deployment has been completed. The next step after identifying all stakeholders is to conduct an inventory management process to understand how many endpoints will be onboarded.
Setup Phase
The setup phase focuses on meeting the network requirements and mitigating possible communication issues between the devices in the company's environment. All devices should contact the respective endpoints of Microsoft Defender for Endpoint.
Onboarding Phase
The next step is to onboard all the devices to Microsoft Defender for Endpoint. This involves configuring and integrating the devices with the endpoint protection system.
However, the implementation of Microsoft Defender for Endpoint is not an easy task and has its pitfalls and complications. Infopulse, as an experienced Microsoft solutions provider, can help you overcome all of them and successfully deploy the solution to serve your security objectives.
Wrapping Up
Given that data is essential to every business, it becomes a prime target for cyberattacks, making it crucial for companies to prioritize protecting their corporate data. One widely adopted strategy for data protection is the use of data loss prevention (DLP) solutions and implementing Microsoft Defender for Endpoint. The latter can significantly enhance the organization's data loss prevention strategy.
![Defender for Endpoint [main banner]](https://www.infopulse.com/uploads/media/banner-1920x528-defender-for-endpoint.webp)



![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![Security Guide for Cloud Migration [thumbnail]](/uploads/media/thumbnail-280x222-security-when-migrating-apps-to-the-cloud.webp)
![AWS Security Hub Integrations [thumbnail]](/uploads/media/top-security-solutions-to-integrate-with-aws-security-hub-for-soc-280x222.webp)
![Building AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-enterprise-guide-to-building-your-aws-security-hub.webp)
![Why Use AWS Security Hub [thumbnail]](/uploads/media/thumbnail-280x222-why-use-aws-security-hub.webp)
![How to Centralize Enterprise Security System [thumbnail]](/uploads/media/thumbnail-280x222-how-to-centralize-enterprise-security-system.webp)


