Top Security Solutions to Integrate with AWS Security Hub for SOC
As the scope of cybersecurity priorities widens, more leaders are looking for tools that could provide better infrastructure observability and consolidated threat intelligence. AWS Security Hub is a security product, designed to meet these needs.
AWS Security Hub can be enabled in minutes and the service helps your teams answer fundamental security questions you may have on a daily basis: Which misconfigurations can become a source for exploit? What actions cause security accidents? How well are we protected against various threats?
In this post, we discuss how SOC teams can obtain more in-depth AWS Security Hub insights using the available integrations with native and third-party products.
AWS Security Hub Setup: Best Practices for Adoption
AWS brands Security Hub as a “cloud security posture management service” with robust automation capabilities. Indeed, one of the main reasons why organizations adopt AWS Security is its sweeping monitoring capabilities and data aggregation across the entire IT portfolio.
Apart from monitoring AWS infrastructure, AWS Security Hub can be also used to procure data from on-premises applications, as well as infrastructure, hosted in other cloud environments.
That said, AWS Security Hub’s robust data aggregation capabilities can also become a hindrance without proper configuration. Organizations risk racking up a substantial bill if they collect too much data or use redundant third-party security tools.
To ensure the optimal usage of AWS Security Hub, we suggest the following best practices.
Decide on the Optimal Data Sources
Prior to adoption, you have to decide which type of security telemetry you need to collect, based on the selected SOC use cases, to avoid overspending. Though AWS bills only $0.0010 per check/account/region/month, the cents can quickly add up.
Our recommendation is to shortlist data sources based on your security goals, e.g., improved threat monitoring, vulnerability scanning, or compliance checks.
Next, map business-critical services that need to be monitored. These can include core financial systems, digital workplace solutions, or ERP applications. For each asset, decide on the exact type of parameters you need to monitor. For example, new access requests, failed login attempts, new IP connections, etc.
When evaluating use cases, pay attention to the cost- and resource-efficiency of collecting security logs. Without proper diligence, you may end up paying exorbitant cloud storage costs for accessing hardly useful information.
Decide On the Optimal Security Toolkit
As the name implies, AWS Security Hub acts as a linchpin, which enables security data collection, analysis, and insight distribution and full-stack observability.
Organizations have an array of native and third-party services to build out the optimal AWS Security Hub architecture. In short, you can select between:
- Native Amazon security tools and infrastructure monitoring services such as Amazon Inspector, AWS Audit Manager, AWS Trusted Advisor, etc.
- Third-party partner product integrations, listed on the AWS Marketplace, such as Palo Alto Networks security solutions or Fortinet products.
- Custom integrations with other solutions, which do not have a pre-made API connector available on the AWS marketplace.
When you evaluate custom integrations to AWS security, investigate if the products support AWS Finding Format (ASFF) for data. If the tool does not support ASFF, you will have to configure an additional data processing layer for converting incoming logs into ASFF. Then send the information to AWS Security Hub.
Set Up Standard Operating Workflows
SOC helps you proactively discover possible vulnerabilities, instances of non-compliance, and gaps in cybersecurity policies. The information must then be effectively shared with other departments that will apply remediation.
To ensure timely action, we recommend setting up an automated data export process to your corporate ticketing system (e.g., Jira or ServiceNow). This way you can monitor issue resolution and ensure that all AWS security hub insights receive proper attention.
Alternatively, organizations can use Change Manager, a feature of AWS Systems Manager, which allows you to set up customizable workflows for requesting, approving, implementing, and reporting changes to your IT infrastructure configurations. Change Manager also comes in handy for compliance monitoring.
3 AWS Security Hub Integration Scenarios for SOC
AWS Security Hub is a versatile and cost-effective solution, equally suited for organizations at different stages of SOC function maturity.
The “composite” nature of AWS Security Hub allows you to assemble a purpose-built toolkit, tailored to your selected use case and business needs. You can establish monitoring across your entire AWS infrastructure, as well as on-premises resources (using custom or third-party tools).
AWS Security Hub also integrates well with Microsoft Sentinel — a flagship security information and event management (SIEM) product, which is convenient for organizations, pursuing a multi-cloud strategy.
To help you better navigate the AWS Security Hub adoption process, our cybersecurity team has created three reference scenarios, describing the types of tools and processes you will need to have in place in order to get the maximum value from this service.
Three Scenarios for AWS Security Hub Adoption
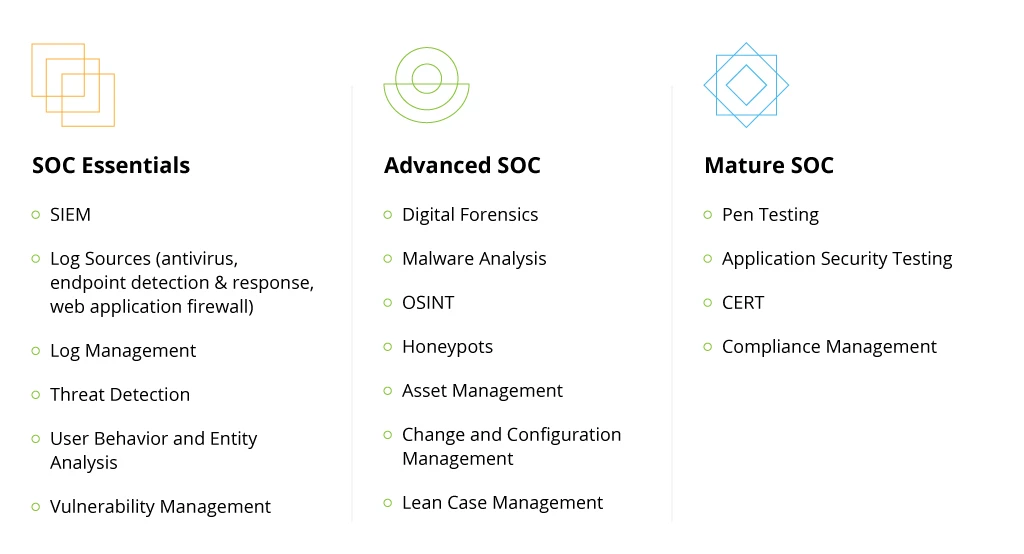
SOC Essentials
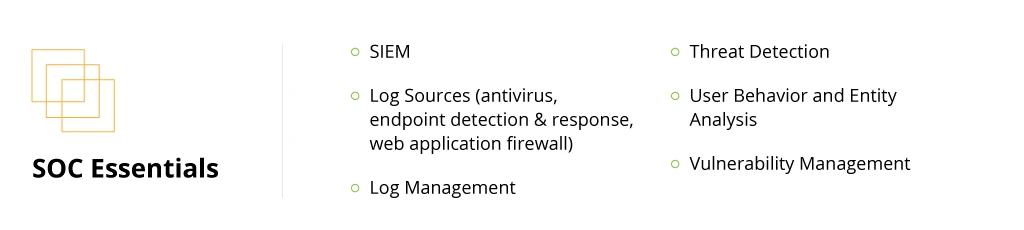
Companies that are just introducing SOC to their organizations have to create a staunch “‘tech mortar” for the team’s effective operations. The first step in this process is to establish a dynamic process for collecting security data.
AWS Security Hub is not a standalone SIEM product, but rather a processing engine for consolidating and analyzing incoming data. Its primary job is to correlate Security Hub findings with each other and other log sources such as antivirus software, endpoint detection and response (EDR) systems, web application firewalls, and other data sources. Additionally, you can feed in external log sources such as database logs, application logs, or third-party security tooling logs into Security Hub to improve your visibility.
Therefore, we always advise our customers to first formalize the selected SOC use cases. Then work backward to locate data sources, which provide the necessary information for fulfilling them. To ensure optimized processing, we recommend implementing a log management solution such as Centralized Logging by AWS.
The next step is to select the optimal tool for threat detection. AWS Guard Duty is the native service for threat intelligence. The solution also provides user and entity behavior analytics (UEBA), meaning you do not have to pay for additional tools to cover this scenario. Other options like FortiGuard or CrowdStrike Falcon are available as marketplace integrations to enable advanced threat detection.
Finally, you should add a vulnerability management (VM) tool, which would allow you to identify unintended risk exposure across all the standard workloads. Amazon Inspector is a native VM service. You can also utilize other options available on the marketplace, such as Tenable.io, Qualys Virtual Scanner Appliance, or IBM Security X-Force Red VMS.
The above integrations create the optimal SOC workflow for incident response, threat hunting, and rapid remediation.
Advanced SOC Capability

Larger organizations, entering a new digital growth stage, or industries bound by tighter compliance requirements (such as finance or telecom) may require more advanced SOC capabilities.
Apart from baseline threat monitoring and incident response, you may also want to implement digital forensics and malware analysis workflows. In this case, we recommend adding extra processes and integrations to your AWS Security Hub architecture. These include:
- Open-source intelligence (OSINT) data sources, which can be collected and ingested into AWS Security Hub for extra contextual insights.
- Honeypots — faux attack targets, designed to lure cybercriminals away from legitimate assets.
- Asset management solutions allow you to collect metadata from across your infrastructure and then analyze it to determine if all the configurations meet your cybersecurity policy.
- Change and configuration management solutions further help you audit configurations and evaluate relationships of your AWS resources to identify gaps or inconsistencies.
To ensure timely issue resolution, we also recommend creating a lean case management workflow, where all identified security findings are forwarded to the right people, responsible for ITSM/ITOM.
Mature SOC Operations

Enterprises, required to maintain the top-most level of security, may also want to explore additional use cases such as:
- Pen testing, done by external security consultants or an internal ethical hacking group. This way you can test how well your current AWS Security Hub configuration supports your organization and evaluate the efficiency of the current workflows (e.g., in terms of incident detection time or incident response time).
- Application security testing (AST) is another proactive cybersecurity technique for evaluating the response of individual applications to direct attacks. AST helps locate vulnerabilities and implement better security-by-design principles.
- Computer emergency response team (CERT) is a dedicated task force, assembled to solve all the incident reports and security tickets for the selected case.
As part of our SOC services, we also help our clients ensure greater compliance with industry-specific and internal compliance requirements and security policies. To conduct an in-depth audit, we rely on AWS Systems Manager Compliance — a native service for analyzing compliance and configuration inconsistencies in the monitored infrastructure, as well as apply third-party services on an as-needed basis.
Conclusion
Cybersecurity has become everyone's responsibility as IT portfolios have grown in size. AWS Security Hub allows organizations to go through their infrastructure with the finest toothcomb to identify vulnerabilities, misconfigurations, or oversights in cyber defense mechanisms.
With Security Hubs, SOC teams get a centralized control panel for reviewing alerts, analyzing security findings from multiple sources, and issuing suggestions for further infrastructure hardening. Integrations with other AWS services and third-party solutions also minimize cybersecurity technology fragmentation within your organization and help you maintain cost efficiency.
![AWS Security Hub Integrations [banner]](https://www.infopulse.com/uploads/media/top-security-solutions-to-integrate-with-aws-security-hub-for-soc-1920x528.webp)

![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


