How to Prevent Ransomware Attacks on Your Enterprise
Among the most common mistakes leading to breaches are misconfigurations, human errors, and the exploitation of a known vulnerability. The situation is aggravated by the fact that 51% of companies do not even have a formal ransomware plan to respond to such attacks.
What is ransomware, why it is so difficult to address, what types are the most dangerous, and what you can do to prevent its negative impact? As a top-tier cybersecurity service provider, we are here to cover the ins and outs.
What Is Ransomware?
Ransomware is a type of malware that encrypts key files at the endpoint and blocks access to enterprise systems until a ransom is paid. Without payment to the hackers, there is a threat the data will be erased or made public and all the systems will be blocked, costing the company millions or even billions of dollars. To wit, the NotPetya malware that made its first attacks in 2017 has now caused about $10 billion in damage worldwide. The pharmaceuticals giant Merck lost $1.4 billion and spent months recovering from this ransomware — after its 40,000 computers had been hacked. The NotPetya attack on TNT Express cost FedEx $300 million, and Mondelez experienced significant damage to its network and infrastructure, losing about $100 million.
Types of Ransomware
Depending on who the key actors are and how they demand payment, there are different types of ransomware attacks. Locker and crypto are the traditional ones, followed by double extortion and ransomware as a service (RaaS) that are gaining traction right now.
Locker ransomware blocks access to enterprise systems and computers, and attackers demand payment to give the access back. Until the ransom is paid, users can only view the blocked screen with a deadline timer and interact with the ransom demand through the partially enabled mouse and keyboard. In this case, the data is only blocked, not destroyed. This breach commonly affects the system through malicious email attachments or fake updates.
Crypto ransomware encrypts data and files on the victim’s device, with attackers requiring payment for a decryption key. Users can even view the data, but do not have the permission to interact with it. If the cyber criminal is not rewarded within the deadline, there is the risk of all the encrypted data being permanently deleted. Due to such an attack, the American publisher Macmillan was forced to close its virtual and physical offices in New York, causing disruption and delays in book shipments.
Double extortion presupposes a double ransom demand: the first one — for decrypting data; the second one — for not making sensitive information public. Such a double threat makes the attack even more dangerous in terms of reputation and financial loss. Appearing in 2020, the DarkSide group, infamous for using the double extortion technique, organized a successful high-profile attack on the Colonial Pipeline, a major U.S. fuel supplier.
Ransomware as a service (RaaS) occurs when threat actors employ a SaaS-like model to carry out the attack. Cybercriminals with low technical skills subscribe to an affiliate RaaS network that launches the attack for them for a percentage of the ransom payment. This model has become popular among attackers because the coding knowledge barrier is removed. Egregor, Sodinokibi, Conti — these are all examples of this ransomware model. In 2020, the Egregor ransomware attacked Barnes & Noble, one of most popular book chains in the U.S., leading to an outage. Sodinokibi got over $200 million in ransom payments since its start, breaching the networks of UnitingCare Queensland, JBS S.A., and more.
Ransomware Vectors
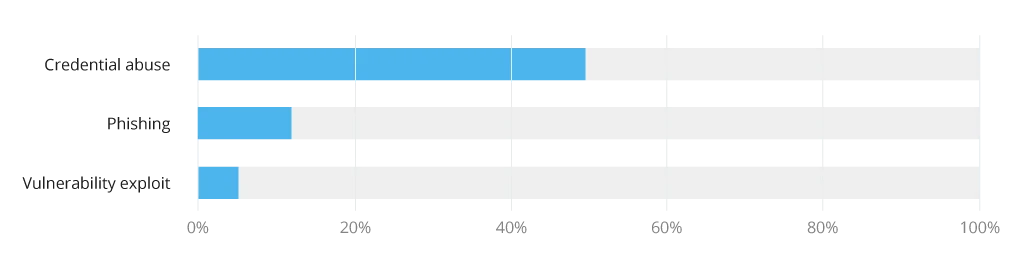
While malware agents are always on the lookout for a new way to enter corporate networks, they still mostly turn to one of the three common infiltration vectors: phishing, Remote Desktop Protocol (RDP) & credential abuse, and exploitable vulnerabilities.
Phishing, which includes embedding malware in an email, is one of the most popular ransomware attacks, with 3.4 billion spam emails sent every day. Cybercriminals make such emails more and more sophisticated, spoofing the sender identity in ways even the savviest users might follow the damaging link.
Attackers also inject malicious software through an RDP, a Microsoft proprietary protocol that provides secure remote access to desktops and servers. When this environment is left without protection, hackers get illegitimate access to information and resources through credential stuffing. Among the most well-known cases is SamSam, an attack that brought about roughly $6 million in total damage, hitting 67 different targets, including the city of Atlanta and the Colorado Department of Transportation.
Poor patching practices significantly increase an organization’s exposure to threats, making its systems bait for a ransomware attack. Malicious actors look for vulnerabilities that they can exploit and insert malware into corporate websites, complex software environments, and more.
Enterprise Ransomware Prevention: Best Practices
Ransomware is dangerous, but you can effectively deal with it by establishing a rock-solid cybersecurity environment. Alongside some traditional and on-the-surface methods like conducting a regular security assessment, we will share other key steps to prevent ransomware attacks.
Employ Layered Security
One of the ways to limit the negative impact of ransomware is to leverage a layered approach that aligns with the National Institute of Standards and Technology (NIST) Cybersecurity Framework. This includes implementing multiple security controls to protect data and resources at various levels.
Levels of Enterprise Security
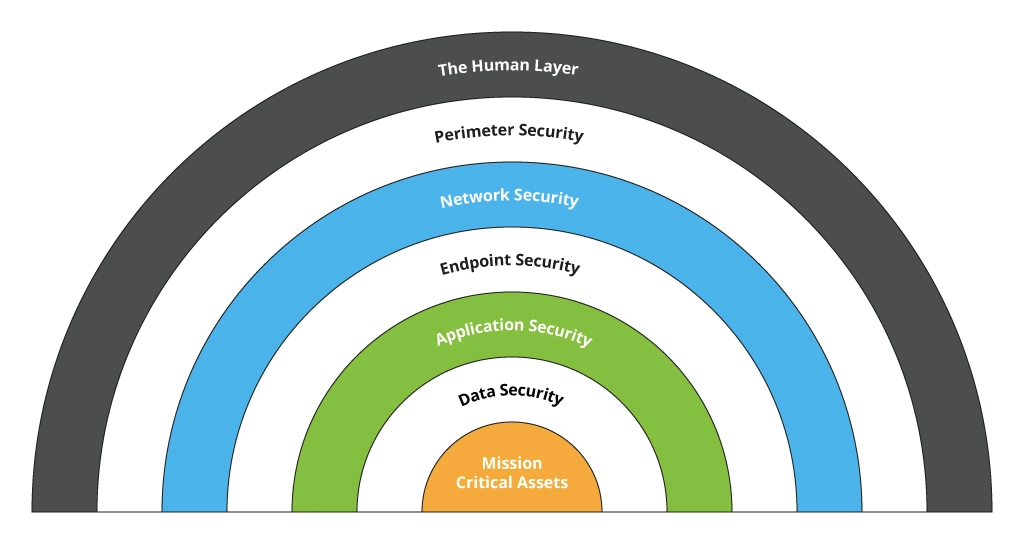
There are multiple security components you can use to increase your enterprise security. It is better to use a combination of these tools so that if one of them fails, there are other options to alert the security team.
- Firewalls monitor incoming and outgoing network transmissions based on a particular set of rules — to decide whether to allow or block specific traffic.
- Patching includes applying updates to software and firmware to close possible security gaps.
- Multi-factor authentication increases security by requiring multiple forms of verification to access a corporate network (password, biometrics, OTPs, SMS/email codes, tokens).
- Email filtering comprises real-time email processing and categorization to spot suspicious content.
- Antivirus software helps to monitor your enterprise systems to detect and eradicate malware as quickly as possible.
- Data backup serves as a guarantee that whatever happens you don’t lose you data – either all of it, or the critical data you selected for backup.
- Cloud data loss prevention presupposes leveraging a range of techniques like sophisticated identity & access management, threat intelligence, and security managed services.
- Incident response plans define responsibilities, communications, and procedures in case of a cyber attack.
- Physical security — such as door locks, surveillance, and access control systems — further enables protecting your on-premise infrastructure and spaces.
- Network segmentation through internal firewalls, Access Control List and Virtual Local Area Network configurations on networking equipment, as well as the software-defined access technology.
To make it easier to manage an array of systems under monitoring, you can opt for SIEM/SOAR solutions. This practice enhances alert management processes, accelerates threat discovery, decreases time to resolution — all in an automated manner. Underpinned by a robust Security Operation Center (SOC), such an approach can bring about even better results, including a higher degree of business continuity, faster issue investigation, improved compliance, and undisrupted service levels.
A case in point: Infopulse helped a leading Swiss manufacturer improve their security posture by implementing a SOC and Microsoft Sentinel as a SIEM/SOAR platform. As a result, the client managed to notably reduce the risk of cyberattacks, detected and resolved over 500 security incidents in one month, enabled 24/7 monitoring and vulnerability scanning across their multiple branches, and fine-tuned their internal security practices.
Make Frequent Backups and Software Updates
A report by ServiceNow states that 60% of victims said they had faced a breach due to an unpatched known vulnerability, and 62% did not know their organizations were vulnerable before the breach occurred. This means that if you do not regularly update your enterprise-grade systems, you give attackers easy pickings.
According to the Multi-State Information Sharing and Analysis Center (MS-ISAC), backing up all mission-critical data is one of the most efficient ways to recover from a ransomware infection. When malicious software encrypts your resources, you can leverage backups to rapidly restore the access without interacting with the attacker. However, mind the fact that you might be brought to the point where you already had the exploited vulnerability, so your ransomware recovery plan should include the remediation of the incident root cause.
Backup should be created and implemented thoughtfully, and here are some additional recommendations we can share: strongly protect your backup files and store them out-of-band, while continuously testing your backups for efficacy. Furthermore, cloud services could also help you get back to an unencrypted version, mitigating the infection.
Introduce Company-Wide Security Policies
According to a report by SlashNext, phishing attacks increased by 61% in 2022, and the Anti-Phishing Working Group spotted a total of 3 million phishing attacks in the third quarter of that year, which is the worst ever observed by the body.
These stats show that security awareness is a must-have piece of the enterprise ransomware prevention puzzle. Introduce a company-wide security policy within your company. Train your employees, partners, and stakeholders on how to create highly secure passwords, use VPNs, spot suspicious communications and attachments, identify phishing attacks, reinforce confidentiality, and more.
Use a Zero-Trust Approach
A security report by Verizon says 74% of breaches include a human element, namely misuse, errors, or social engineering. This means particular attention should be paid to access control in your organization. We recommend adopting a zero-trust approach.
Also called “least privilege”, such a method presupposes maintaining strict access controls even for users and devices inside the network perimeter. The access is granted to a minimal set of resources and only depending on user identity and the context. The zero-trust model continuously inspects and re-authenticates users and devices to revoke the network and application access as soon as an infection is detected, making it difficult for ransomware to escalate its privileges and get control over the network.
Other zero-trust best practices include securing access behind a proxy-based brokered exchange to make users and resources invisible to the internet as well as minimizing data exposure through micro-segmentation techniques. To keep it truly zero-trust, it is important to regularly reevaluate that users have the right level of permission, since it can fluctuate over time.
A case in point: Infopulse assisted a large media holding in Ukraine to reinforce security. Underpinned by Microsoft cloud technologies, the service provider introduced a unified IT ecosystem for all the subsidiaries — enabling hybrid identity based on Azure AD and simple multi-factor authentication for end users.
Implement Endpoint Security
Endpoints like laptops, computers, tablets, and smartphones might be less guarded due to their use outside corporate networks, thus representing an accessible target to attackers. Among common threat vectors here are vulnerability exploits, social engineering attacks, compromised USB devices, threats from shared files, and unsecured software usage.
In 2020, 68% of companies experienced an endpoint attack that resulted in compromised data or IT infrastructure. The market for endpoints security tools is also booming, with predicted spending reaching $25.7 billion by 2030. Considering such alarming stats, we recommend reinforcing your security strategy with endpoint security practices. This can be done through:
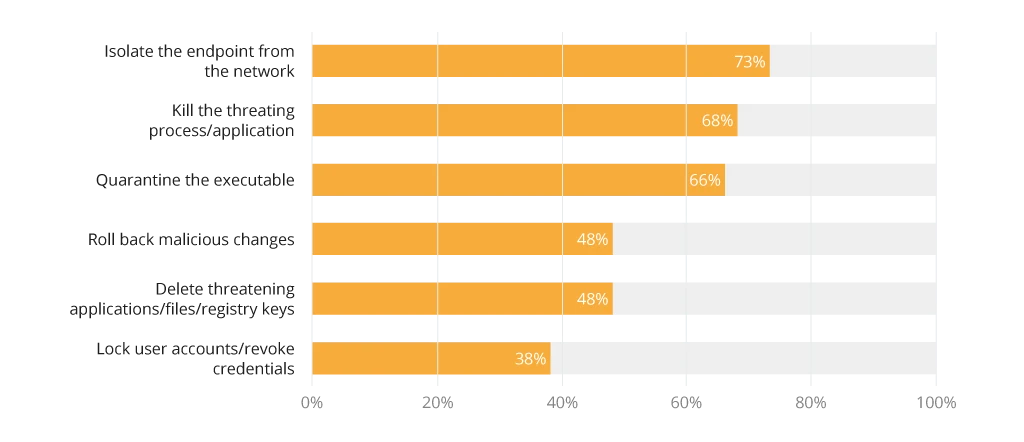
- Anti-malware software automatically detects the virus, alerts the central server or the IT team, tries to delete or uninstall the malicious files, or quarantines the infected devices to prevent lateral movement. According to Cybersecurity Insider, organizations prefer isolating the infected endpoint from the network, followed by killing the application.
- Application control. This technique allows IT administrators to decide which software employees can install on endpoints, minimizing the risk of installing attacker-compromised software by mistake or with malicious intent.
- Encryption. By encrypting data on an endpoint device, you protect it if the device is compromised or physically stolen. Hard disk encryption is another simple practice that helps minimize the risk of unauthorized parties breaching sensitive data.
A case in point: Infopulse implemented Microsoft Defender for a large retail operator to enable 24/7 protection of 1,500+ corporate and BYOD endpoints against any cyber attacks, automated incident investigation and response, and ML-fueled user behavior analytics for precise anomaly detection.
What’s Next?
We have given you some effective recommendations on how to prevent enterprise ransomware attacks. However, using them sporadically or unevenly without a prior IT infrastructure analysis and cohesive security plan creation will not provide you with an optimal outcome. To make things work, partner with a seasoned cybersecurity expert like Infopulse. We provide a wide range of security services, including threat detection, governance, risk & compliance, backup & disaster recovery, incident response, and digital forensics.
![How to Prevent Ransomware Attacks [banner]](https://www.infopulse.com/uploads/media/banner-1920x528-how-to-prevent-ransomware-attacks-on-your-enterprise.webp)



![Security Levels [thumbnail]](/uploads/media/thumbnail-280x222-levels-of-enterprise.webp)
![SOC Use Cases [thumbnail]](/uploads/media/thumbnail-280x222-soc-use-cases-definition-and-implementation-best-practices.webp)

![Measuring BCDR Effectiveness [Thumbnail]](/uploads/media/thumbnail-280x222-measuring-bcdr-effectiveness.webp)
![Deepfake Detection [Thumbnail]](/uploads/media/thumbnail-280x222-what-is-deepfake-detection-in-banking-and-its-role-in-anti-money-laundering.webp)
![Robocall Mitigation Solutions [thumbnail]](/uploads/media/thumbnail-280x222-caller-line-identification-spoofing-and-robocall-4-mitigation-solutions.webp)
![How to Choose MFA [thumbnail]](/uploads/media/thumbnail-280x222-how-to-choose-the-right-mfa-approach-for-your company.webp)


